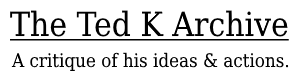Perspectives on Terrorism; Volume IX, Issue 6
A Journal of the Terrorism Research Initiative
Radical Groups’ Social Pressure Towards Defectors: The Case of Right-Wing Extremist Groups
Future Behaviour towards Group
Group Reaction Differentiation According to Defector Type
How Groups Arrive at a Strategy
Discussion of Findings and Future Directions for Research
Group Decision Making Processes
Annex: Brief Case Descriptions
Religion, Democracy and Terrorism
The Democracy-Terrorism Debate
Religion and Variations in Terrorist Targeting
Religious Security and Terrorism
20 Years Later: A Look Back at the Unabomber Manifesto
Attracting, Maintaining, and Molding Followers
Securing Adoption of the Ideology by the Larger Structure
Reacting to Resistance from the Larger Structure
“Rhetorical Problems” and “Rhetorical Strategies”
Appendix: Sections of Theodore Kaczynski’s “Industrial Society and its Future”
Re-Examining the Involvement of Converts in Islamist Terrorism: A Comparison of the U.S. and U.K.
Appendix 1. List of American converts included in the sample
Appendix 2. List of British converts included in the sample
Terrorist Practices: Sketching a New Research Agenda
Unsolved Puzzles and Questionable Assumptions
Social Practice and Terrorist Society
Leveraging Practice Disaggregation: The Case of Religious Culture
Research and Policy Implications
Interview Protocols and Sample Description (n = 13)
Motivations and the Positive Benefits for Those Joining IS
Process of Indoctrination by Charismatic Trainers
Military Training, Weapons, & Battle Field Practices
Warnings to those Westerners Who Might be Attracted to IS
Bibliography: Homegrown Terrorism and Radicalisation
Bibliographies and other Resources
Journal Articles and Book Chapters
Counterterrorism Bookshelf: 40 Books on Terrorism & Counter-Terrorism-Related Subjects
A Word of Appreciation for Our External Peer Reviewers
TRI Award for Best PhD Thesis 2015: Call for Submissions
TRI National/Regional TRI Networks (Partial) Inventory of Ph.D. Theses in the Making
Expected date of completion: December 2016.
Job Announcement: Open Rank Faculty Search at CTSS, UMass Lowell
[Front Matter]
Table of Contents
Welcome from the Editor
I. Articles
The Evolution of Al Qaeda’s Global Network and Al Qaeda Core’s Position Within it: A Network Analysis
by Victoria Barber
Radical Groups’ Social Pressure Towards Defectors: The Case of Right-Wing Extremist Groups
by Daniel Koehler
Religion, Democracy and Terrorism
by Nilay Saiya
20 Years Later: A Look Back at the Unabomber Manifesto
by Brett A. Barnett
II. Research Notes
Re-Examining the Involvement of Converts in Islamist Terrorism: A Comparison of the U.S. and U.K
by Sam Mullins
Terrorist Practices: Sketching a New Research Agenda
by Joel Day
Eyewitness Accounts from Recent Defectors from Islamic State: Why They Joined, What They Saw, Why They Quit
by Anne Speckhard and Ahmet S. Yayla
III. Resources
Bibliography: Homegrown Terrorism and Radicalisation
Compiled and selected by Judith Tinnes
IV. Book Reviews
Counterterrorism Bookshelf: 40 Books on Terrorism & Counter-Terrorism-Related Subjects
Reviewed by Joshua Sinai
<strong>V. Notes from the Editor
A Word of Appreciation for Our External Peer Reviewers
from the Editorial Team
TRI Award for Best PhD Thesis 2015: Call for Submissions
TRI National/Regional TRI Networks (Partial) Inventory of Ph.D. Theses in the Making
by Alex P. Schmid (Network Coordinator)
Job Announcement: Open Rank Faculty Search at CTSS, UMass Lowell
About <em>Perspectives on Terrorism
Welcome from the Editor
Dear Reader,
We are pleased to announce the release of Volume IX, Issue 6 (December 2015) of Perspectives on Terrorism at www.terrorismanalysts.com. Our free online journal is a joint publication of the Terrorism Research Initiative (TRI), headquartered in Vienna (Austria), and the Center for Terrorism and Security Studies (CTSS), headquartered at the Lowell Campus of the University of Massachusetts (United States).
Now completing its ninth year, Perspectives on Terrorism has over 5,800 regular subscribers and many more occasional readers and visitors worldwide. The Articles of its six annual issues are fully peer-reviewed by external referees while its Research Notes, Policy Notes and other content are subject to internal editorial review.
This issue begins with analysis by Victoria Barber on the relationship between al Qaeda core and other identifiable groups within the so-called “global jihadist movement.” She finds that many groups’ ideological affinity seems to give way to more worldly concerns, and globalization to regional concerns, indicating limited evidence of a truly cohesive global network. Then Dan Koehler looks at how right-wing extremist groups react - emotionally and strategically - when individuals defect from the group. In the next article, Nilay Saiya describes how states that provide religious security for their citizens undercut the ideological narratives disseminated by religious militants (that their faith is under attack), and thus dampening the resonance of their appeal for violent action. Finally, Brett Barnett examines how and why the manifesto of “Unabomber” Theodore Kaczynski has resonated with some radical environmentalists.
Our Research Notes section begins with a piece by Sam Mullins examining how religious converts compare with non-converts in the U.S. and U.K. with regard to involvement in terrorist activities 1980-2013. Next, Joel Day proposes an innovative mixed methods approach to the study of terrorist cultural, ritual and community practices. And in the final piece of this section, Anne Speckhard and Ahmet Yayla provide some preliminary results of their Islamic State Interviews Project, based here on a sample of thirteen Syrian IS defectors who spoke about life inside the “Islamic State” and now warn others not to join what they gradually came to see as a totally disappointing, ruthless and un-Islamic organization.
The Resources section features an extensive bibliography by Judith Tinnes on homegrown terrorism and radicalization, and 40 short book reviews by Joshua Sinai. And the issue concludes with a sincere word of thanks to our external peer reviewers; an announcement for the annual TRI Award for Best Thesis; an inventory of Ph.D. theses underway by members of the TRI National/Regional Networks; and a faculty job announcement from the CTSS at UMass Lowell.
This issue of the journal was prepared by the co-editor of Perspectives on Terrorism, Prof. James Forest at the University of Massachusetts Lowell, who offers a special thank you to our new Editorial Assistant Jared Mello and to CTSS Co-Op Scholar Danielle Thibodeau for their considerable assistance. The next issue (February 2016) will be prepared in the European offices of the Terrorism Research Initiative (TRI) by Prof. em. Alex P. Schmid.
I. Articles
The Evolution of Al Qaeda’s Global Network and Al Qaeda Core’s Position Within it: A Network Analysis
by Victoria Barber
Abstract
There has been much discussion in recent decades regarding the nature of the threat posed by terrorism. In doing so, many have cited the existence of a vast and amorphous global terrorist network, with Al Qaeda at the helm. But is that model a truly accurate one? By using social network analysis to map and track Al Qaeda’s global network from 1996 to 2013, this article seeks to determine whether the global movement is as cohesive and ideologically-driven as it has been made out to be. Ultimately, it finds that not only is that model no longer reflective of Al Qaeda’s global network, it likely never was. In the end, ideological affinity seems to give way to more worldly concerns, and globalization to regional concerns, leaving the idea of a global movement lacking.
Keywords: Al-Qaeda; networks; influence
Introduction
There has been much debate in recent years over the nature of the threat posed by terrorism in the 21st century. A prominent question within this debate concerns how the terrorist threat is structured: Is it within traditional groups and their affiliates or individuals taking their own initiative, rendering the traditional group structure irrelevant?[1] The impact of this answer will dictate strategies for intervention. For example, should the threat lie in individual self-motivated actors, the often-used strategy of decapitation is of limited use. While there are certainly arguments to be made for the threat posed by the rise of lone wolves[2] and their origins in more familiar movements within the counter-terrorism field,[3] this article will focus on established groups, as its primary concern is in relationships between them.
Such relationships have changed in recent decades, as advances in technology and more affordable travel have made communication and coordination much easier.[4] This has given rise to transnational terrorist movements and allowed these established groups to move beyond the national and regional struggles they had engaged in before.[5] As part of this transition, many groups moved from the traditional hierarchical organization observed in non-state armed groups in the past and toward a more horizontal structure,[6] leading researchers to study terrorist organizations as networks.[7] There is much debate over the relative merits of these organizational structures. On the one hand, size can be a limiting factor for a networked structure, as large networks can be difficult to control and coordinate.[8] However, becoming networked can make a group more resilient to intervention and can therefore be an attractive choice for clandestine organizations.[9]
The rise of Al Qaeda provides an excellent example of this transition and the globalization of the terrorist threat.[10] Arguably the group with the greatest reach and influence in the last several decades, Al Qaeda Core began as a small and highly selective group that arose out of the Soviet-Afghan War.[11] They maintained this status throughout the 1990s, quietly influencing uprisings throughout the Middle East and biding their time until they entered the world stage with the September 11th attacks.[12] By September 12th, 2001, Al Qaeda and Osama bin Laden were household names, and Al Qaeda Core was in the position to foster other militant groups on a much broader scale. It was seen as the hallmark of a new kind of terrorist threat, one that was no longer confined to a specific conflict or geographic area and could pose a legitimate threat to even the most powerful states.[13]
The most common contemporary image of Al Qaeda is that of a global movement with Al Qaeda Core as the vanguard for a network of affiliated groups that could be utilized within the movement, but did not require the same maintenance and control as a hierarchical organization.[14] This affiliation could be anything from sending members to Al Qaeda affiliated training camps or publishing statements in support of Al Qaeda to formally pledging one’s group to Al Qaeda Core. What emerged was a structure that could loosely be described as a set of concentric circles, with Al Qaeda Core at the center, immediately surrounded by the lucky few groups that were allowed to call themselves its regional branches, followed by affiliate groups who benefitted from Al Qaeda in some way, and finally the independent cells or individuals, who were inspired by Al Qaeda, but lacked any tangible connection to the Core.[15]
There is much debate over the nature and genesis of this structure.[16] Some scholars argue that the networked approach was adopted consciously, with key members of the organization advocating for the early versions of the structure even before 9/11.[17] Others argue that much effort was placed on maintaining a strict hierarchy within the group, which made it less able to combat more networked organizations, such as ISIS.[18] On this side of the debate, the structure emerged in response to counter-terrorism efforts, rather than as a conscious choice by the leadership.[19]
Regardless of where one falls in these discussions, Al Qaeda as an organization evolved into being part of a larger network that spanned the globe, though whether it maintains a position as a member or leader of that network remains to be seen. But is the idea of a sustained global terrorist network an accurate one or is that image overblown or out-of-date? The remainder of this article will attempt to address this concern by looking at what makes groups cooperate and where Al Qaeda Core lies within the network.
There are many schools of thought surrounding the best way to measure the strength of a network, be it density of connections, leadership roles, or number and independence of sub-groups.[20] However, while these could certainly be useful when evaluating an organization as a whole, this research approaches the idea of the network in a slightly different way. Rather than looking at Al Qaeda Core’s network in terms of strength and weakness, the purpose of this research is to determine whether this image of a sustained, cohesive global movement with Al Qaeda Core at the center was an accurate one.[21] To answer this question, Al Qaeda Core’s leadership role within the network and whether those actors with which it cooperates are in line with its ideology serve as key variables. As an ideologically based organization, it follows that working with groups that have similar objectives would denote the maintenance of its image and that of a global movement. As with any coalition, agreement on objectives is central to the maintenance of a multi-actor campaign. As such, within the context of this research, Al Qaeda Core’s global network is considered “strong” when it maintains a clear leadership role and engages largely with actors that are in line with its objectives.
The discussion that follows will track trends in cooperation and competition in Al Qaeda’s global network as it grows and Al Qaeda Core’s place within it to determine the validity of this global network model. Ultimately, the argument is made that we can use these variables to determine whether the image of a cohesive global network is an accurate one.
Methodology
The primary analytical approach used within this article is network analysis. A networked dataset was created largely from the data supplied by the Mapping Militants Project (MMP),[22] run by Professor Martha Crenshaw of Stanford University, and the Global Terrorism Database (GTD).[23] To create the dataset, this project began with the list of groups and the links between them that were included within the Al Qaeda Global Network portion of the MMP. From there, all of the incidents that involved two or more groups were pulled from the GTD, provided that at least one group was in the original list from the MMP. The research was restricted to these two sources in an effort to contain the scope of this project. This restriction does give rise to some limitations in the research, which are elaborated upon in more detail later in this article. However, future research could expand the source material in order to further test the conclusions found here.
This methodology was chosen to highlight the connections between these groups and the character of those connections. In the interest of showing the development of relations over time, the analysis was broken into four time periods, each of which spans roughly five years. In the diagrams and analyses that follow, a tie between two groups represents one or more incidents that involved those two groups during that time period. In the instances where there were multiple incidents involving two groups that occurred in the same time period, those incidents were aggregated according to an averaging method that will be elaborated upon in the sections that follow.
Ultimately, this methodology allows the researcher to track the evolution and devolution of relationships between groups within the larger Al Qaeda network, as ties are not cumulative between time periods. As ties appear between groups, it indicates that there were incidents involving those two groups within the time block in question. As they disappear between time periods, the lack of tie indicates that there was not an additional incident within the more recent time block present in either the MMP or GTD datasets. In doing so, this analysis reveals changes in cooperative behavior between groups within the network, as well as patterns within the network as a whole.
Groups
In this analysis, all groups that were included within MMP or the subset of the GTD previously mentioned were considered, regardless of their status as terrorist organizations, level of affiliation with Al Qaeda Core, etc. An assortment of demographic information was collected on each one in an effort to determine whether there was a pattern or change in the nature of groups admitted into the Al Qaeda network over time. These included: country of origin/primary activity, level of Al Qaeda affiliation, primary target(s), organizational objective(s), umbrella organization(s), and a series of yes/no features that are described in more detail below. Ultimately, a total of 56 organizations were considered, all of which are listed below in alphabetical order.[24]
-
313 Brigade
-
Abu Sayyaf Group (ASG)
-
Adan Abyan Islamic Army (AAIA)
-
Ahlu-sunah Wal-jamea (Somalia)
-
Ahrar al-Sham
-
Al Jama’a Al-Islamiya
-
Al Qaeda Core (AQ)
-
Al Qaeda in the Arabian Peninsula (AQAP)
-
Al Qaeda in the Islamic Maghreb (AQIM)
-
Al Qaeda in Yemen (AQY)
-
Al Shabab
-
Al Mua’qi’oon Biddam Brigade (Those who Sign with Blood)
-
Al Qaeda Kurdish Battalions
-
Al Tawhid Islamic Front (TIF)
-
Ansar al-Islam (AI)
-
Asif Raza Commandos
-
Baloch Liberation Front (BLF)
-
Bangsamoro Islamic Freedom Movement (BIFM)
-
Black Banner Brigade
-
Boko Haram
-
Egyptian Islamic Jihad
-
Free Aceh Movement (GAM)
-
Free Syrian Army
-
Hamas (Islamic Resistance Movement)
-
Haqqani Network
-
Harkat-ul-Jihad al-Islami (HuJI)
-
Harkat-ul-Mujahedeen
-
Hizb-I-Islami
-
Hizbul al Islam (Somalia)
-
Hizbul Mujahideen (HM)
-
Indian Mujahideen
-
Islamic Army in Iraq
-
Islamic Movement of Uzbekistan (IMU)
-
Islamic State (IS)
-
Jabhat al-Nusra
-
Jaish-e-Mohammad (JeM)
-
Jamaat-E-Islami (India/Pakistan)
-
Jamiat ul-Mujahedin (JuM)
-
Jemaah Islamiyah (JI)
-
Jundallah
-
Lashkar-e-Jhangvi (LeJ)
-
Lashkar-e-Jhangvi Al-Alami
-
Lashkar-e-Taiba (LeT)
-
Lashkar-e-Zil
-
Liwa al-Islam
-
Moro Islamic Liberation Front (MILF)
-
Moroccan Islamic Combatant Group (GICM)
-
Movement for Oneness and Jihad in West Africa (MUJAO)
-
Mujahideen Army (MA)
-
Mutassim Bellah Brigade
-
Ogaden National Liberation Front (ONLF)
-
Rajah Solaiman Revolutionary Movement
-
Second Soran Unit (SSU)
-
Sipah-I-Mohammed
-
Taliban
-
Tehreek-e-Taliban Pakistan (TTP)
The following analysis focuses mainly on whether or not a group’s organizational objectives are in line with the stated objectives of the Core, its country of origin/primary activity, and the level of affiliation each group has with Al Qaeda Core. Further discussion of the data collection methods for those three features can be found below, though it is worth noting that the variables collected on the groups were treated as static. In other words, attribute data were not collected separately for each time period. A full explanation of the data that were collected but not addressed in this paper can be found in Appendix I.
Organizational Objective(s)
For coding purposes, each of the publicized organizational objectives, as specified in the MMP dataset and supplemental source material, were recorded without any limitation on the number of objectives ascribed to each group. The list of organizational objectives used in coding are as follows; few of the groups had only one of them, while many have expressed a combination of any number of these as primary objectives:
-
Government Overthrow[25]
-
Establish Islamic Government
-
Wahhabi
-
Anti-Shia
-
Anti-Western
-
Incorporation of Kashmir into Pakistan
-
Nationalist
In the analysis, the primary focus was on whether or not groups aligned with the publicized organizational objectives of Al Qaeda Core—namely a combination of Anti-Shia, Anti-Western, and Establishing an Islamic Government objectives.[26] As such, any organization with at least two of Al Qaeda Core’s organizational objectives was treated as being ideologically aligned with Al Qaeda Core’s goals. For the purposes of this analysis, a new binary variable was created to denote whether a group matched the above description or not.
Region
In an effort to determine whether geography was a factor in the admission of groups into the network, the countries in which organizations originated—or, in the cases in which the leadership was forced to relocate, primarily operate—were recorded. For the sake of more efficient analysis, the countries were divided into regions, which were then used as the primary geographical identifiers for groups. The list of such countries, divided by region, is as follows.
-
South Asia
-
Afghanistan
-
India
-
Pakistan
-
Pacific
-
Indonesia
-
Malaysia
-
Philippines
-
Singapore
-
Middle East
-
Iran
-
Iraq
-
Iraq (Kurdistan)
-
Israel
-
Palestine
-
Saudi Arabia
-
Syria
-
Turkey
-
Yemen
Northern Africa
-
Algeria
-
Egypt
-
Morocco
East Africa
-
Ethiopia
-
Somalia
West Africa
-
Mali
Nigeria
Level of Al Qaeda Affiliation
The first four levels of Al Qaeda affiliation were drawn from Hoffman and Reinares’s definitions of the four types of affiliation with Al Qaeda Core.[27] There was, however, a need for two more categories within the dataset, in addition to a category for groups with no apparent relationship with Al Qaeda Core. The first, Anti-AQI (Al Qaeda in Iraq), though limited to groups in Iraq, did not easily fit into any of the four categories. These groups generally work against AQI, now the Islamic State (IS), though have occasionally worked with it. In both instances, their interactions with the group earned them places within the network and, by extension, an additional category. The second addition, “Many members were veterans of the Soviet- Afghan War”, describes groups that have no obvious Al Qaeda affiliation, other than the fact that their members served in the Soviet Afghan war with the original Al Qaeda Core members. They could potentially be categorized within the fourth category, Independent Cell (Inspired by AQ), but the fact that the fourth category specifies that Al Qaeda provided inspiration to the groups or individuals within it make that argument problematic, as many of them were founded before or contemporaneously with Al Qaeda Core. As such, they were given their own category of affiliation. Those groups with no apparent relationship with Al Qaeda Core were coded as “no affiliation”. The full list of levels of affiliation is outlined below.
-
AQ Central / Core
-
AQ-Directed Branch / Territorial Extension
-
Autonomous Affiliate
-
Independent Cell (Inspired by AQ)
-
Anti-AQI (though occasional ally)
-
Many members were veterans of the Soviet-Afghan War
-
No affiliation
Links
To achieve a more nuanced view of the network, the links between the groups were also coded. The two features of particular concern, other than which groups were involved in each incident and when it happened, were the type of link and where that type fell on a scale of what level of commitment that action represented on the part of the groups involved. More detail on both of those features is provided in the sections below.
Type of Link
The type of link denotes the nature of the relationship between the two groups for that data point. Each link describes an incident in which two groups were involved. As such, the links between the groups describe a wide variety of actions that one group can take with or against another. All links described within the MMP dataset were included in this analysis, regardless of the relationship’s nature, relative importance, or ultimate outcome. Likewise, the only requirements for GTD incidents to be included in this analysis were that at least one of the groups from the MMP was involved, and collaborative action was at least suspected. In other words, if the incident was recorded within the GTD as having two groups involved because it was listed as potentially being committed by either one organization or the other, rather than it being the product of joint effort, it was excluded from this study. The 20 types of links between groups identified within the dataset are listed below:
-
Documented Alliance
-
Joint Operation
-
Training
-
Host Leader
-
Material Aid
-
Shared Leader (i.e. the leader of one organization belonged to the other at some point)
-
Establishes Contact
-
Parent-Child Organizations
-
Public Statement of Support
-
Oath of Allegiance
-
Merger
-
Humanitarian Aid
-
Split
-
Personal Friendship Between Leaders
-
Documented Rivalry
-
Sanctuary (i.e. one group provided sanctuary to a number of members of the other during a time of persecution)
-
Public Statement of Condemnation
-
Armed Conflict
-
Rejected Merger
-
Training/Financial Aid
Link Level
To aid in analysis, the types of link were further categorized into six groups, based on two main criteria: positive or negative (which describes whether the link between the two organizations was cooperative or competitive, respectively), and high, medium, or low (which denoted the strength of the connection). The distinction between positive and negative links is fairly straightforward, but the demarcation between high, medium, and low level links is more subjective and, therefore, warrants further description.
The category “Low” was limited to those links that were either primarily based on public statements or individual relationships. These are considered low-level links because they involve relatively less effort on the part of the group (or even individual) or involve taking one group “out of the game” (e.g. hiding members of another group during a time of persecution).
Medium-level links describe either relationships documented from an outside source (e.g. a government report describing two groups as allies) or the provision of some sort of aid without one group taking the extra step of performing a joint operation with the other. Again, this is a higher level of commitment than the low- level category in that there are additional steps taken (e.g. providing funds to support another group, rather than simply praising them in public), but this relationship falls short of physically acting together.
Finally, high-level links are reserved for events that either change or establish organizational structures (e.g. merging organizations, pledging allegiance, or splitting) or involve the groups actively working with or against each other. These links denote the highest level of commitment, as they involve either the fundamental structures of the groups or placing “boots on the ground” for an operation or conflict. As such, they were awarded the highest weight.
A detailed breakdown of where each type of link was placed within this framework can be found in Table 1:
Table 1: Types of Links Between Organizations
| Low | Medium | High | |
| Positive |
Public Statement Hosting Leader Shared Leader Establishing Contact Personal Friendships Sanctuary |
Documented Alliance Training/Financial Aid Humanitarian Aid Material Aid |
Oath of Allegiance Merger Parent-Child Organizations Joint Operation |
| Negative | Public Statement | Documented Rivalry |
Armed Conflict Split Rejected Merger |
Analysis
In an effort to examine the changes within the network before and after the 9/11 attacks, the analysis here is limited to the period between 1996 and 2013, when the MMP dataset ends. Moreover, the data is separated into four intervals of time in order to both show the progression in the network over time and have enough data in each interval of time to be meaningful.
Within the discussion of each interval, there is a network map to illustrate the structure of the network and the types of links found between the groups that were active within that time period. Also included is a series of network measures to assess Al Qaeda’s role within the network and trends in the groups with which it chooses to interact.
The two measures this research focuses on are centrality and cohesion. Centrality denotes the role of an individual actor within the network. There are several measures to determine centrality, each with its own implications. For these purposes, three have been selected: betweenness, eigenvector, and closeness. For comparison, each interval discussion includes the top three groups for each measure. Before discussing these measures in the context of this research, it is worth defining each in order to ensure clarity in their implications.
Betweenness denotes the number of paths between groups. Actors with high betweenness scores are couriers of information. They connect groups to each other and can act as both bottlenecks and facilitators.[28] Within the context of this research, one would expect Al Qaeda Core to have a high betweenness score for each time interval, if it is truly the “mastermind” of the network.
Eigenvector centrality measures the level of connection to other well-connected nodes. Those with high eigenvector scores are informal leaders, who have influence over more overt power players.[29] As with betweenness, one would expect Al Qaeda Core to have a very high score for eigenvector centrality, meaning that it is pulling the strings behind the regional clusters of groups.
Closeness determines how many steps are required for each group to reach every other group within the network. Groups with low closeness scores have fewer steps to get to the others in the network. Within the context of this research, this is the number of other groups one actor would have to work through to reach every other actor. Again, one would expect Al Qaeda Core to have a low closeness score in each time block. This implies that AQC has relatively few steps to go through to get to each of its affiliates, as compared to the rest of the network, which would have to go through AQC to reach another affiliate.
To assess the cohesion of the network, or how often groups tend to work with other groups that are similar to them in some respect, this analysis uses an E-I Index. This measure reports on a scale of -1.00 to 1.00 how often a group (or all groups within the network as a whole) interacts with another group with whom it shares a given characteristic. A score of -1.00 denotes that a group only works with groups that are like it and 1.00 describes an actor that only works with groups that are unlike it. A characteristic used within this analysis is region of primary activity. If the E-I Index is taken for a group based in the region of primary activity for actors within the network, then the score a group receives describes how likely that group is to work with other groups from its region. If an actor scores a -1.00, that means that it interacts entirely with other actors from the same region.
For the purposes of this analysis, an E-I Index for both Al Qaeda Core and the network as a whole are included, with the “in-group” defined in four different ways:
1. Those who are considered in line with Al Qaeda Core’s objectives, as defined in the Methodology section of this article
2. Those that originate from or primarily operate in a given region
3. Those who fall into the category of being Al Qaeda Core, a Regional Branch, or an Autonomous Affiliate (i.e. have an established and tangible relationship with Al Qaeda Core)
4. Those who are either Al Qaeda Core or a Regional Branch.
These categories were chosen to examine whether Al Qaeda Core is more likely to interact with groups that are ideologically or organizationally similar to it, as demonstrated by similar objectives or an established relationship, respectively.
Combined, these measures speak to the strength of Al Qaeda Core’s position within the network. With high centrality measures, AQC is in a position of power within the network, with that power defined by both controlling the flow of information and affiliation (with Betweenness and Closeness) and maintaining connections to other well-connected actors (with Eigenvector centrality). Cohesion speaks to the idea that Al Qaeda Core is maintaining control over its message and goals within the network by maintaining ties to groups that are ideologically similar to itself.
One important note in the centrality and cohesion measures is that, unlike network maps, only positive links were included. In other words, the cohesion score represents how likely Al Qaeda Core is to work together with another group, not how likely the two groups are to simply interact. This was done to prevent the negative ties from skewing the measures toward actors that often clash with others, as this research is chiefly concerned with Al Qaeda’s positive control over its network.
The following sections include an analysis of Al Qaeda Core’s network at four time intervals, including a network map, centrality measures to determine Al Qaeda’s position within that network, and cohesion measures to quantify the features of groups that make Al Qaeda Core more or less likely to work with them.
1996-2000
This block represents the period leading up to the September 11th attacks. This was when the network was in its infancy, as Al Qaeda Core was planning the attack under the watchful eye of Khalid Sheikh Mohammed. It was also during this period that the networked structure and “homegrown” jihad movement were developed. [30] At this point, Al Qaeda Core certainly had ties to other groups, as evidenced below. However, the familiar concentric circle model has yet to take shape. In Figure 1 below, the colors represent the average commitment level between those groups during this time period, a method that will carry forward for every subsequent diagram within this paper. To obtain this average, each link level was given a weight (i.e. Negative, High = 1, Negative, Medium = 2, up to Positive, High = 6) and an average level was taken based on the number of links between the groups.
In the map above, the network has a hub-and-spoke structure, with Al Qaeda Core at the center, not unlike the star network proposed by Arquilla, which requires information and planning to flow through the hub. [31] This is especially interesting to observe, given the previously mentioned debates surrounding when and why Al Qaeda adopted a networked approach to its activities. Regardless of whether it was done intentionally before counter-terrorism measures put pressure on the organization after 2001, it does appear that Al Qaeda Core had been developing a network among its associates before that time. Al Qaeda Core tends to enjoy strong positive links (i.e. Positive High and Medium), while the rest of the network is defined by weaker positive and even negative links. In short, Al Qaeda is securely positioned at the center of a network that is defined by its relationships.
It is worth noting that much care was taken to code each tie independently of external factors to maintain both the integrity of the dataset and the ability to observe the network as it evolved. For example, a reader who is familiar with the case may view the positive-low link weight between Al Qaeda Core and the Haqqani Network as reductive of the relationship between the two groups. However, in the interest of consistency,
every instance of one group hosting the leadership of another, or providing safe-haven for that group, is coded as a low-positive tie, regardless of the long-term implications of that tie. Additional relations that, admittedly, likely grew out of the affiliation cemented during this period will be coded and analyzed separately in subsequent sections as they arise.
Centrality
Unsurprisingly, Al Qaeda is a strong frontrunner in all three measures of centrality, as shown in Table 2, below. To reiterate, a high betweenness measure indicates that Al Qaeda Core is the path through which information and planning flows. Having the highest eigenvector measure indicates that Al Qaeda Core is the most strongly connected to other well-connected groups. Finally, having the lowest closeness score means that Al Qaeda Core can connect with other groups within the network by going through the lowest number of other groups, (i.e. has the least degree of separation from other actors). In combination, leading each of these categories denotes that Al Qaeda Core has a firm grasp on the network.
Table 2: Analysis of Data on Centrality, 1996-2000
| First | Second | Third | |
| Betweenness | Al Qaeda Core (62.000) | Laskar-e-Jhangvi (40.000) | Jaish-e-Mohammad (36.000) |
| Eigenvector | Al Qaeda Core (0.453) | Laskar-e-Jhangvi (0.380) | Haqqani Network (0.362) |
| Closeness | Al Qaeda Core (26.000) | Laskar-e-Jhangvi (28.000) | Jaish-e-Mohammad (32.000) |
Not only does it control the flow of information between the groups with its high betweenness measure, but it also enjoys a position that is both well connected to other well-connected groups, such as they are in a network like this, and requires very few steps to reach any other group. This implies that there is little that gets done involving multiple actors within network without Al Qaeda Core’s involvement.
Cohesion
Once again, cohesion measures indicate a group’s likelihood to work with another that shares some characteristic with it. This analysis also included cohesion measures along each parameter for a variety of datasets, including two different ways to consolidate multiple ties within a time interval and subsequently eliminate negative ties.
Thus far, this analysis has focused on the average commitment level between groups for a given time interval. However, to thoroughly test the aggregation methods, cohesion measures were also taken using the highest level of commitment between two groups, rather than the average. For example, if two groups had two ties, one with a strength of 1 and the other with a strength of 4, they would average to 2.5, which would be excluded from the average-based analysis, as it would round to a level 3 tie, which corresponds to a Negative Low score. However, in running the measures for the highest tie between groups, this relationship would be included, as the highest commitment level between them is 4, a Positive Low score.
In addition, not only were cohesion measures run for all positive ties, but they were also run for only the highest levels of commitment. In other words, cohesion measures were determined both for a network of all positive ties between groups (i.e. low, medium, and high), and for only the Positive High ties.
As a result, the EI index was taken for each interval in four different ways:
1. Taking the average commitment level between two groups and eliminating all negative ties (i.e. Weights of 1-3 are eliminated, leaving only positive commitment levels)
2. Taking the highest commitment level between two groups and eliminating all negative ties (i.e. Weights of 1-3 are eliminated, leaving only positive commitment levels)
3. Taking the average commitment level between two groups and eliminating all but the Positive High (6) commitment (i.e. Weights of 1-5 are eliminated, leaving only Positive High commitment levels)
4. Taking the highest commitment level between two groups and eliminating all but the Positive High (6) commitment (i.e. Weights of 1-5 are eliminated, leaving only Positive High commitment levels)
This was done in order to determine whether the choice of analyzing only positive average commitment levels obscured other results, which may have come to light in using another method of consolidating the data. However, the results for all methodologies were comparable, and therefore all cohesion measures within the body of this article will be average positive ties going forward. A table of all cohesion results can be found in Appendix II.
The cohesion measures for our four key characteristics for the average positive commitment level between 1996 and 2000 are displayed in Table 3 below. Once again, the EI Index used for this analysis is on a -1.00 to 1.00 scale, with groups scoring a -1.00 interacting exclusively with those who are the same as they are. In other words, if a group should score a -1.00 for the “Same Region” category, it means that said group interacts exclusively with other groups from its region.
Table 3: Analysis of Data on Cohesion, 1996-2000
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.231 | 0.231 | -0.692 | 0.692 |
| Whole Network | -0.405 | -0.568 | -0.189 | -0.405 |
Interestingly enough, even in these early stages, Al Qaeda Core is slightly more likely to interact with groups that are not in line with their objectives. There is a stronger tendency within the network for groups that are in-line with AQC’s objectives to work with each other and those who are not to work together. However, the tendency is not very strong, implying that links are not necessarily ideologically motivated. One possible explanation is that ideologically dissimilar groups are brought into the network in an effort to indoctrinate them. However, it is impossible to prove that thesis definitively within the context of this project.
There is also a slight tendency for Al Qaeda Core to work with groups that are not focused within its region, which is expected given its global agenda. There is also a moderate tendency for groups to work with others within their region, which is, again, expected as the global network is still developing.
There is a fairly strong tendency for AQC to work primarily with those with whom it has an established relationship, at least when affiliates are included. However, that tendency reverses when affiliates are not included in the “in-group”, which is to be expected given the timing, as many of the regional branches had yet to take shape within the network.
2001-2005
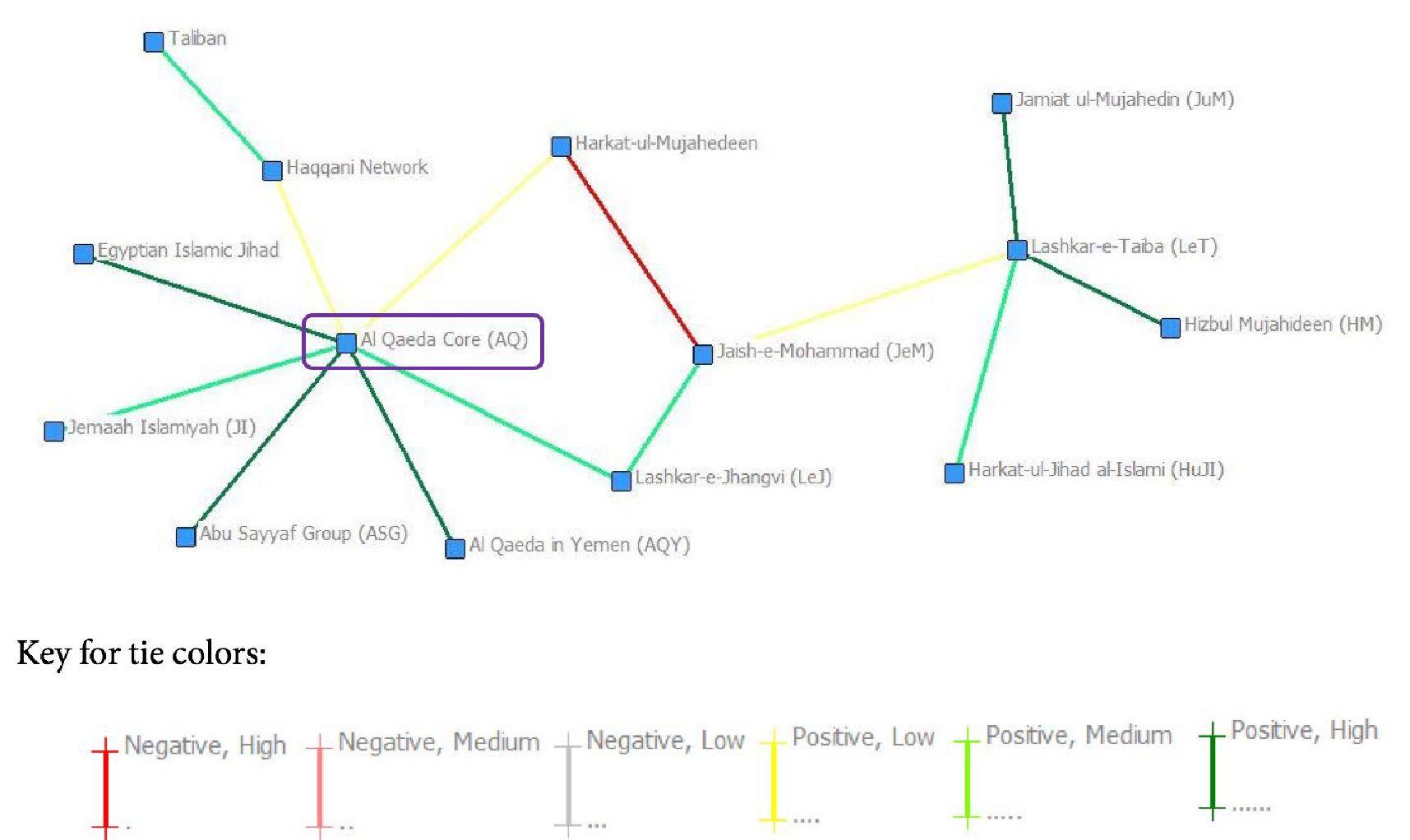
The period including and following the September 11th attacks was one of expansion in the network.
Suddenly, groups were clamoring to be affiliated with the Al Qaeda brand,[32] which is reflected in Figure 2 below.
Once again, one can see a hub-and-spoke structure with Al Qaeda Core at the center and roughly the same breakdown of the level of direct ties between AQC and others.[33] However, there is a significant development that was not present in the previous time period. In the 2001-2005 period, we begin to see not only affiliate groups connecting with each other on a large scale, but strong positive links between those groups. In particular, the network begins to display small groups of two or three that are typically connected to Al Qaeda Core through one member of the cohort, for example the cohort of Second Soran Unit (SSU) Al Tawhid Islamic Front (TIF) and Ansar al Islam (AI), who are connected to the Core through AI. This development is significant in that it denotes the decentralization of power within the network. Al Qaeda Core still enjoys its place as the hub, connecting a vast array of spokes, but other hubs are beginning to emerge among the groups in its network.
Centrality
Once again, there is little surprise in the centrality measures, as displayed in Table 3 below. Al Qaeda Core maintains its place at the top of every centrality measure, with Ansar al-Islam often staking out second place. Despite the expansion of the network and the increasing connections between affiliates, AQC is still the main source of direction and information within the network.
Table 4: Analysis of Data on Centrality, 2001-2005
| First | Second | Third | |
| Betweenness | Al Qaeda Core (349.000) | Ansar al-Islam (107.000) | Lashkar-e-Jhangvi (103.000) |
| Eigenvector | Al Qaeda Core (0.616) | Abu Sayyaf Group and Jemaah Islamiyah (0.254) | Ansar al-Islam (0.253) |
| Closeness | Al Qaeda Core (49.000) | Ansar al-Islam (65.000) | Lashkar-e-Jhangvi and the Islamic State (69.000) |
Cohesion
The EI Index for the four characteristics of interest during the 2001-2005 time interval are displayed in Table 5. The results are very similar to those of the previous interval, with most of the patterns established remaining largely unchanged.
Table 5: Analysis of Data on Cohesion, 2001-2005
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.231 | 0.231 | -0.692 | 0.692 |
| Whole Network | -0.368 | -0.579 | -0.158 | -0.368 |
The paradoxically inclusive nature of Al Qaeda Core continues into this period, as there is a slight tendency for AQC to interact with groups that are not in line with their objectives, as compared to the slight tendency of the rest of the network to stay within their “in-group”, with regards to AQC’s ideology, though that effect appears to be weakening compared to the previous time period. Moreover, while AQC’s tendency to seek out groups outside of its region has continued, the regional focus of the network has only increased.
Likewise, there is still a strong tendency for Al Qaeda Core to interact with those groups, with which they have an established connection. However, the tendency reverses when independent affiliates are removed from the “in-group”, implying that Al Qaeda Core is largely limiting its activities to its independent affiliates, as many of the regional branches are still forming.
In short, Al Qaeda Core remains the main hub of activity in a growing network. It is the key connection between smaller networks of groups that share similar ideology and regional focus, without pigeon-holing itself by excluding connections based on ideology or region. While this inclusion may or may not have been a strategic decision, it reveals that even in the early stages, the Global Al Qaeda network does not meet the characterization of strength in a global movement as provided within this research.
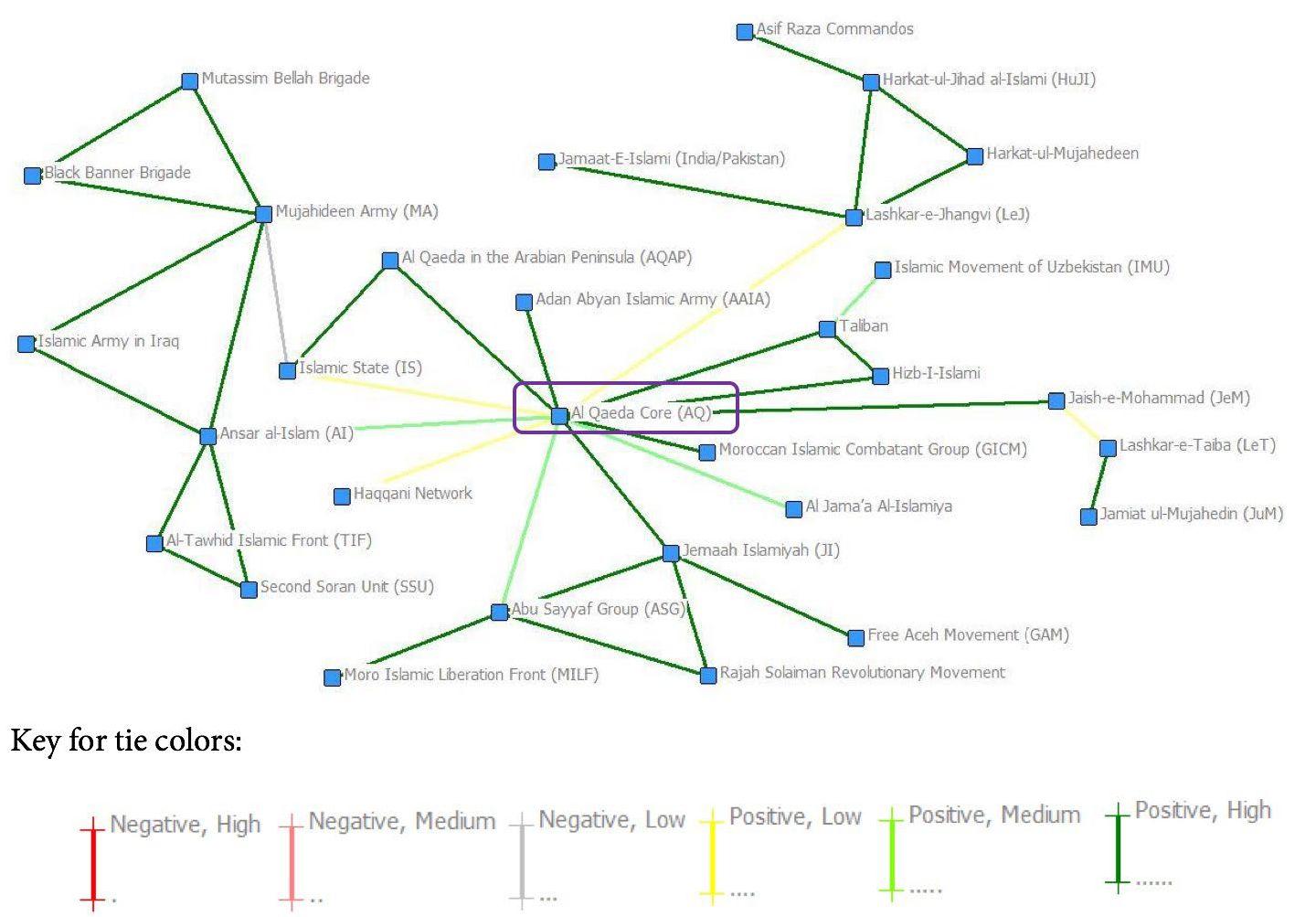
2006-2010
The 2006-2010 time block shows a flurry of activity within the network. Not only have several new actors emerged, but the structure of the network has changed dramatically, as displayed in Figure 3.
Once again, the number and breakdown of ties directly to Al Qaeda Core remained relatively constant. However, the ties between affiliates with little interaction with AQC has increased exponentially, with both a high proportion of strong positive ties and the highest number of negative ties that have appeared thus far.
Most significantly, while there is still a hub and spoke structure surrounding Al Qaeda Core, it no longer has the monopoly on that structure. Figure 3 reveals the development of Al Shabab and Tehreek-e-Taliban Pakistan as hubs in their own rights. This is where one may begin to believe that the network may have overextended itself. For more empirical data to that effect, this analysis will turn to centrality and cohesion measures.
Centrality
While Al Qaeda Core managed to hold onto the top centrality scores, maintaining its position as a broker of information, TTP is hot on its heels, as shown in Table 6.
Table 6: Analysis of Data on Centrality, 2006-2010
| First | Second | Third | |
| Betweenness | Al Qaeda Core (80.500) | Tehreek-e-Taliban Pakistan (45.000) | Al Shabab (27.000) |
| Eigenvector | Al Qaeda Core (0.535) | Tehreek-e-Taliban Pakistan (0.509) | Taliban (0.355) |
| Closeness | Al Qaeda Core (214.000) | Tehreek-e-Taliban Pakistan (218.000) | Taliban (222.000) |
In previous time intervals, there was rarely such consistency in the second and third positions in each measure. A group may have one or two of the second-place spots. However, having a “clean sweep” of second place and such little variety in third implies the solidification of other centers of power that are well- positioned to challenge that of Al Qaeda Core.
Cohesion
In Al Qaeda Core we can observe near perfect external cohesion, perfect internal cohesion, and perfect indifference, as evidenced in Table 7. Within the 2006-2010 time period, Al Qaeda almost exclusively interacted with groups that were not in line with its organizational objectives, but with whom it had an established relationship. However, it appeared that autonomous affiliates were still the preferred groups. It also appeared to lose its preference for groups that were not part of its region, as it displays no preference either way.
Table 7: Analysis of Data on Cohesion, 2006-2010
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.75 | 0 | -1 | 0.25 |
| Whole Network | -0.403 | -0.583 | -0.667 | -0.417 |
This implies that the ideology of the groups with which it interacted did not matter, so long as they were a known ally. Moreover, it demonstrates the disconnect between the objectives of the affiliates and branches AQC chose to foster in this period of expansion and the ideology of Al Qaeda Core itself. Although AQC has displayed a pattern of being slightly biased toward bringing in groups that have different ideologies, there has previously been a stronger base of those groups that are in line with its objectives to balance it out. In this latest time period, it would seem that as the network has expanded, Al Qaeda Core has lost some measure of control of its message via its affiliates.
Interestingly enough, groups in the rest of the network have displayed a moderate to strong preference for those of with the same features that they do. In other words, groups with objectives in line with Al Qaeda tend to work with each other, as do groups that operate within the same region, or have the same or similar levels of affiliation with Al Qaeda. This implies that even as Al Qaeda’s control over the network begins to wane, its influence on the groups within it has remained. Still, while it has maintained one aspect of strength, as defined within this context,[34] it seems to have abandoned the pursuit of the other.[35]
2011-2013
The shift in the network from the 2006-2010 time period to this one is clear in Figure 4. The number of links has been dramatically reduced, as has the number of groups within the network.[36] Part of that reduction may have been a function of the limitation of the MMP and GTD datasets, which only included links up to 2013, two years short of the full five-year interval that the other time periods were allotted. Another possible explanation is the death of Osama bin Laden in 2011. One of Al Qaeda Core’s greatest strengths was the cult of personality around its leadership[37] and the loss of Osama bin Laden was a significant blow to the organization, which may have translated into a period of inactivity within the network as the power void was filled.
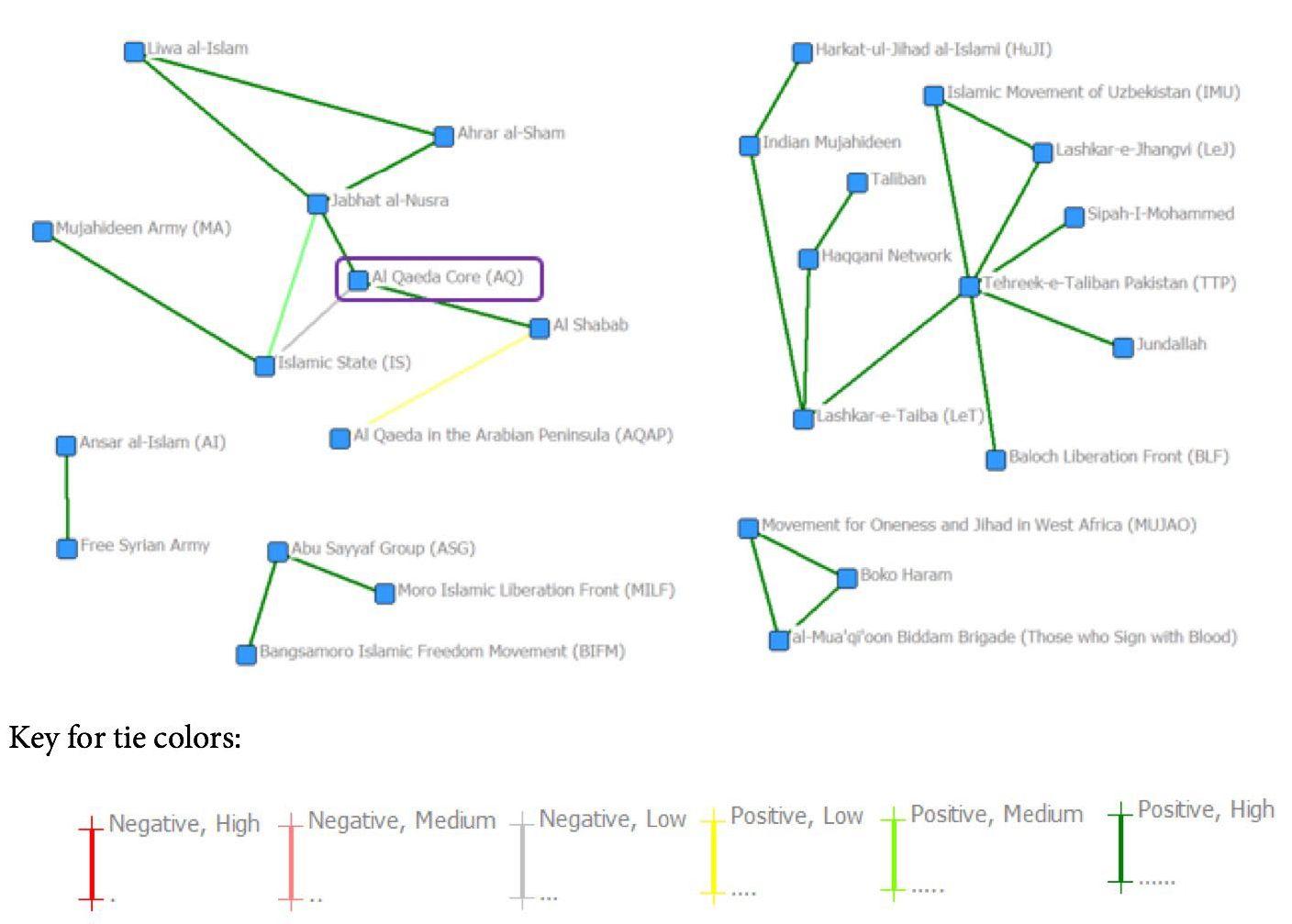
The period is significant, however, as it includes the first negative tie between Al Qaeda Core and one of its affiliates, the Islamic State. Up until now, direct connections between Al Qaeda Core and its affiliates have been fairly predictable - a roughly equal mix of positive high, medium, and low ties. Now, however, it only has two Positive High ties and one Negative Low. It would appear that Al Qaeda Core is becoming more selective with its links, only allowing for open affiliation in occasions of high commitment or public censure for its affiliates stepping out of bounds (i.e. the Islamic State).
Centrality
This interval brings a change in centrality as well, as Al Qaeda Core is no longer the top score in each centrality measure, displayed in Table 8. Indeed, it is not even in the top three for any of the measures.
Table 8: Analysis of Data on Centrality, 2011-2013
| First | Second | Third | |
| Betweenness | Tehreek-e-Taliban Pakistan (34.000) | Lashkar-e-Taiba (28.000) | Jabhat al-Nusra (16.000) |
| Eigenvector | Tehreek-e-Taliban Pakistan (0.642) | Islamic Movement of Uzbekistan and Lashkar-e-Jhangvi (0.366) | Lashkar-e-Taiba (0.335) |
| Closeness | Tehreek-e- Taliban Pakistan (448.000) | Lashkar-e-Taiba (449.000) | Islamic Movement of Uzbekistan, Lashkar- e-Jhangvi, Indian Mujahideen, and Haqqani Network (456.000) |
As was foreshadowed in the 2006-2010 interval, Tehreek-e-Taliban Pakistan has taken over as the best- connected group in the network.[38] This is likely at least in part because of the larger size of the sub-network in which it is central. Indeed, the network structure of the 2011-2013 interval implies the breakdown of the global network into smaller, more easily managed groups that share some characteristic that binds them together. Just what that characteristic is will be the subject of the subsequent section of this discussion.
Cohesion
The pattern for Al Qaeda Core in the 2011-2013 interval is one of extremes, as displayed in Table 9. It exclusively works with groups that are not in line with its organizational objective, are from a different region, and with which it has some type of established relationship. However, it does not have a preference between regional branches and non-regional branches.
Table 9: Analysis of Data on Cohesion, 2011-2013
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 1 | 1 | -1 | 0 |
| Whole Network | -0.12 | -0.68 | -0.44 | -0.6 |
Even more compelling are the results from the rest of the network. The pattern established in the previous interval has held, in that groups still tend to work with those that are similar. The preference for groups to work with those who match their alignment (or lack thereof) with Al Qaeda’s objectives has almost disappeared, but the regional preference has increased to be the strongest factor in interaction between groups, followed by whether the group is a regional branch of Al Qaeda. However, the strong preference for working with groups that match one’s own status as a regional branch of Al Qaeda is likely skewed by the small number of regional branches included within the 2011-2013 interval. The regional affinity of the network is especially apparent in Figure 5, which displays the same network map as Figure 4, but with the groups coded by region. There is clearly a division along regional lines within the larger network.
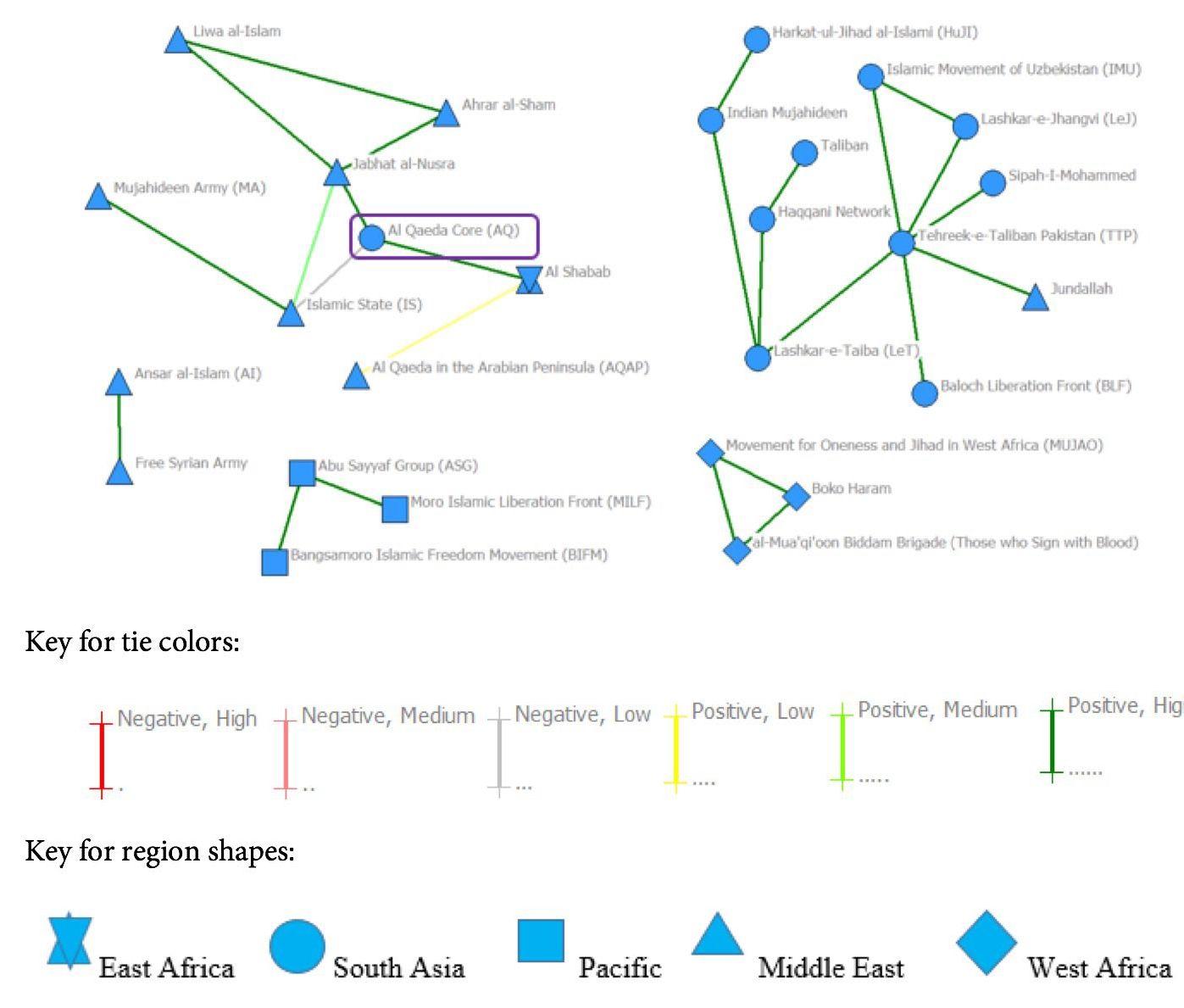
Clearly, the network has lost any semblance of strength as a global AQC-led movement, as it does not meet either criteria required for strength within the context of this project. Rather, the network appears to have taken on a life of its own and returned to the regional focus that was the norm before Al Qaeda’s rise.
Conclusion
While Al Qaeda Core’s network of affiliates has certainly grown over time, the data do not support the doomsday image of a vast and amorphous enemy that its reach implies. Rather, the network ultimately appears to have overextended itself for Al Qaeda Core’s purposes, and the group has gradually lost control.
The period leading up to the 9/11 attacks saw a small, but stable network. Al Qaeda Core was well-positioned as a power-player within a hub-and-spoke network. It did have a mix of groups that were in line with its organizational objectives and those that were not, so it did not meet that aspect of strength. However, the presence of both implies the maintenance of its ideological base, while logistical or doctrinal motivations may account for the presence of dissimilar groups. All in all, it is the organized, tight-knit network that one fears in the image of a Global Al Qaeda.
The five years following 9/11 did not see major changes in the nature of the network, as outlined above. Al Qaeda Core still enjoyed its status as a hub and maintained a mix of ideologically similar and dissimilar affiliates. However, this period saw an expansion in the network as groups flocked to AQC’s banner. More importantly, those groups began to form connections with each other. So while groups maintained their connections with Al Qaeda Core, they no longer relied on it as their sole source of information or direction - they began to rely on each other.
The true breakdown in Al Qaeda Core’s control came during the 2006-2010 interval, where it was not yet ousted as the sole source of information and direction within the network, but its affiliates were clearly poised to take active leadership roles. Even more damaging, it abandoned efforts to maintain ties with ideologically similar groups altogether. There could be any number of logistical or tactical motivations for this, but the ultimate implication is that the ideology of the group is not as important. For an ideologically motivated organization like Al Qaeda, this represents a dangerous departure from its rhetoric and the loss of control over its overall message.
The final interval, although incomplete, is important in that it represents both the increasing regionalization of the network, and the introduction of competition between Al Qaeda Core and its regional branch. Al Qaeda Core had previously been insulated from such negative ties, implying that this new period marks the end of Al Qaeda’s unquestioned leadership. It also seems to point to the end of a global network, as groups increasingly focus on regional conflicts and objectives. The ultimate function of Al Qaeda Core was to inspire the rise of militant organizations and then connect them to each other. As the network grew and Al Qaeda Core’s power waned, rather than prop up its creator, the movement fractured into regional networks. Given the ongoing regionally focused conflicts in which many of these groups operate today, the trend towards regionalism is unlikely to change. However, without additional data, it would be unwise to draw firm conclusions from this interval.
The use of only two datasets, particularly ones that only include data up to 2013 has certainly limited the number and types of links available for this research. In the interests of maintaining data integrity, only data points included within the MMP and GTD datasets were considered. Moreover, links between groups were only included when and how they were presented in the dataset. For example, Al Qaeda Core and Lashkar- e-Jhangvi had a close relationship beginning in the 1990s and continuing through the early 2000s. However, there were only two specific links listed between them in the MMP dataset and none in the GTD - one in 1998 and another in 2001. To preserve consistency in coding, additional ties were not extrapolated from this implied ongoing relationship and therefore these were the only ties between the two groups included within this dataset. However, this methodology does have a trade-off in leaving the dataset open to some gaps. Some of the more prominent omissions have been denoted in the footnotes of this paper for reference, though they are not exhaustive.
In addition, the methods of aggregation—i.e. condensing multiple incidents involving groups into a single tie within a given time period—did not take into account the relative importance of those events. In other words, if there was a public statement of support that went largely unmarked and a joint operation with far reaching consequences for the relationship between two groups, they were weighted the same within the average (i.e. the tie would be weighted 5, as the joint operation is weighted 6 and the public statement 4). Relative importance of ties was partially addressed in the weights themselves, however they do not address specific instances in which a given event that may have a low score within this framework because of its type, but has far reaching consequences on the relationship. This could lead to students of this network noting ties that are weighted higher or lower than they would expect within the network maps. Some notable examples have been highlighted in the text and footnotes, but these are also not exhaustive.
The inclusion of additional links or the expansion of the timeline could certainly alter or strengthen these conclusions. In particular, recent developments with the Islamic State would have likely given the network map in the 2011-2013 time block a very different shape, had it extended to present day. Moreover, as the GTD is almost exclusively a database of terrorist attacks, all incidents taken from it were coded as the highest level of either positive or negative commitment. This has the potential for biasing any results toward a higher level of commitment than might otherwise be observed with access to a greater number of medium and low level incidents.
Finally, the use of a single coder, who is also the researcher, opens the dataset to questions of subjectivity. As such, those interested in continuing research on the topic should do so using more rigorous coding methods, as well as a more expansive dataset.
Ultimately, the image of a vast and tightly controlled network of organizations with Al Qaeda Core pulling all the strings does not seem to be realistic. While that may have been the case on a smaller scale, during the group’s time “under the radar”, its leap to infamy with the September 11th attacks appears to have marked the end of that structure. Indeed, it never fully met the requirements of a strong network, as defined within this project. Rather, we have a large, increasingly regionalized network that, while at least inspired and sometimes aided by Al Qaeda, does not maintain the idea of a unified, globalized movement. In the end, with great networks comes a great lack of control.
About the Author: Victoria Barber is a second-year Master’s student at the Fletcher School of Law and Diplomacy, concentrating on International Security Studies. In her research, she utilizes social network analysis to study inter- and intra-group networks of non-state armed groups.
Bibliography
Abdoulaye, Ibbo Daddy, Jason Hanna, and Pierre Meilhan. “Report: Islamist Militants Claim 2 Deadly Attacks in Niger.” CNN: Africa. CNN, 23 May 2013. Web. 9 June 2015.
“Aden Abyan Islamic Army (AAIA).” Terrorist Organization Profile - Aden Abyan Islamic Army (AAIA). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
“al-Badr.” Terrorist Organization Profile - al-Badr. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
“al-Mansoorain.” Terrorist Organization Profile - al-Mansoorain. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Atwan, Abdel Bari . The Secret History of Al-Qa’ida, London: Saqi Books, 2006, p.265-66.
“Asif Raza Commandos.” Asif Raza Commandos. Terrorism Research and Analysis Consortium. Web. 9 June 2015.
“Asif Reza Commando Force.” Asif Reza Commando Force. South Asia Terrorism Portal. Web. 9 June 2015.
“Baloch Liberation Front (BLF).” Terrorist Organization Profile - Baloch Liberation Front (BLF). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Berger, J.M.. “ISIS/The Islamic State.” Lecture at the Fletcher School of Law and Diplomacy, Medford, MA, February 17, 2015.
Brams, J. Steven, Mutlu Hande, and S. Ling Ramirez, “Influence in Terrorist Networks: From Undirected to Directed Graphs,” Studies in Conflict & Terrorism 29, 2006, p.703-718.
Carley, M. Kathleen, Diesner Jana, Reminga Jeffrey and Tsvetovat Maksim, “Toward an Interoperable Dynamic Network Analysis Toolkit,” Decision Support System, 43, 2006, p.1324-1347
Carley, M. Kathleen, Ju-Sung, Lee and Krackhardt, David, “Destabilizing Network,” Connections 24 (3), 2002, p.79-92.
Chalk, Peter. “The Bangsamoro Islamic Freedom Fighters: The Newest Obstacles to Peace in the Southern Philippines?” Combating Terrorism Center at West Point, 26 Nov. 2013. Web. 9 June 2015.
“Chapter 6. Foreign Terrorist Organizations.” U.S. Department of State, n.d. Web. 12 Nov. 2014.
Cozzens, Jeffery B. and Magnus Ranstorp, “The Enduring Al Qaeda Threat: A Network Perspective,” in Contemporary Debates on Terrorism, ed. Richard Jackson and Samuel Justin Sinclair, London: Routledge, 2012, 90-97.
Cozzens, Jeffrey B.. “Approaching Al-Qaeda’s Warfare: Function, Culture and Grand Strategy,” in Mapping Terrorism Research: State of the Art, Gaps and Future Directions, ed. Magnus Ranstorp, London: Routledge, 2007, p.127-64, 132
Crenshaw, Martha. “Abu Sayyaf.” Mapping Militant Organizations. Stanford University, 20 July 2015. Web. 4 March 2015.
Crenshaw, Martha. “Al Qaeda in the Arabian Peninsula.” Mapping Militant Organizations. Stanford University, 12 May 2015. Web. 4 March 2015.
Crenshaw, Martha. “Al Qaeda in the Islamic Maghreb.” Mapping Militant Organizations. Stanford University, 20 Jan. 2013. Web. 4 March 2015.
Crenshaw, Martha. “Al Qaeda in Yemen.” Mapping Militant Organizations. Stanford University, 18 July 2015. Web. 4 March 2015.
Crenshaw, Martha. “Al Qaeda Kurdish Battalions.” Mapping Militant Organizations. Stanford University, 9 Aug 2012. Web. 4 March 2015.
Crenshaw, Martha. “Al Qaeda.” Mapping Militant Organizations. Stanford University, 28 Nov 2012. Web. 4 March 2015.
Crenshaw, Martha. “Al Shabab.” Mapping Militant Organizations. Stanford University, 30 Sep 2013. Web. 4 March 2015.
Crenshaw, Martha. “Al-Tawhid Islamic Front.” Mapping Militant Organizations. Stanford University, 23 July 2015. Web. 4 March 2015.
Crenshaw, Martha. “Ansar al-Islam.” Mapping Militant Organizations. Stanford University, 14 Aug 2014. Web. 4 March 2015.
Crenshaw, Martha. “Boko Haram.” Mapping Militant Organizations. Stanford University, 20 Feb 2015. Web. 4 March 2015.
Crenshaw, Martha. “Egyptian Islamic Jihad.” Mapping Militant Organizations. Stanford University, 9 Aug 2012. Web. 4 March 2015.
Crenshaw, Martha. “Global Al-Qaeda.” Mapping Militant Organizations. Stanford University, n.d. Web. 4 March 2015.
Crenshaw, Martha. “Haqqani Network.” Mapping Militant Organizations. Stanford University, 15 May 2015.
Web. 4 March 2015.
Crenshaw, Martha. “Harkat-ul-Jihadi al-Islami.” Mapping Militant Organizations. Stanford University, 28 Nov 2012. Web. 4 March 2015.
Crenshaw, Martha. “Harkat-ul-Mujahedeen.” Mapping Militant Organizations. Stanford University, 28 Nov 2012. Web. 4 March 2015.
Crenshaw, Martha. “Hizbul Islam.” Mapping Militant Organizations. Stanford University, 10 July 2013. Web.
9 June 2015.
Crenshaw, Martha. “Islamic Army in Iraq.” Mapping Militant Organizations. Stanford University, 23 July 2014. Web. 4 March 2015.
Crenshaw, Martha. “Jabhat al-Nusra.” Mapping Militant Organizations. Stanford University, 12 Nov 2014.
Web. 4 March 2015.
Crenshaw, Martha. “Jaish-e-Mohammad.” Mapping Militant Organizations. Stanford University, 25 June 2015. Web. 4 March 2015.
Crenshaw, Martha. “Jemaah Islamiyah.” Mapping Militant Organizations. Stanford University, 8 July 2015.
Web. 4 March 2015.
Crenshaw, Martha. “Lashkar-e-Jhangvi.” Mapping Militant Organizations. Stanford University, 7 July 2015.
Web. 4 March 2015.
Crenshaw, Martha. “Lashkar-e-Taiba.” Mapping Militant Organizations. Stanford University, 3 Aug 2012.
Web. 4 March 2015.
Crenshaw, Martha. “Lashkar-e-Zil.” Mapping Militant Organizations. Stanford University, 25 Aug 2012. Web. 4 March 2015.
Crenshaw, Martha. “Jaish al-Islam” Mapping Militant Organizations. Stanford University, 5 Nov 2014. Web. 9
June 2015.
Crenshaw, Martha. “Moro Islamic Liberation Front.” Mapping Militant Organizations. Stanford University, 18 July 2013. Web. 9 June 2015.
Crenshaw, Martha. “Moroccan Islamic Combatant Group.” Mapping Militant Organizations. Stanford
University, 6 Aug 2012. Web. 4 March 2015.
Crenshaw, Martha. “Mujahideen Army.” Mapping Militant Organizations. Stanford University, 11 Aug 2014.
Web. 4 March 2015.
Crenshaw, Martha. “Second Soran Unit.” Mapping Militant Organizations. Stanford University, 11 Aug 2014.
Web. 4 March 2015.
Crenshaw, Martha. “Tehreek-e-Taliban Pakistan.” Mapping Militant Organizations. Stanford University, 7 Aug 2012. Web. 4 March 2015.
Crenshaw, Martha. “The Islamic State.” Mapping Militant Organizations. Stanford University, 15 May 2015.
Web. 4 March 2015.
Crenshaw, Martha. “The Taliban” Mapping Militant Organizations. Stanford University, 2 July 2013. Web. 4 March 2015.
Cronin, Audrey Kurth. “Cyber Mobilization: The New Levee en Masse,” Parameters 36(2), 2006 p.77-87.
“Free Aceh Movement (GAM)” Terrorist Organization Profile - Free Aceh Movement (GAM). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
“Free Syrian Army Founded by Seven Officers to Fight the Syrian Army.” Syria Comment RSS. Syria Comment, 29 July 2011. Web. 9 June 2015.
Gunaratna, Rohan, “Al Qaeda’s Trajectory During and After Bin Laden,” in Terrorism and Counterterrorism, Howard and Hoffman (eds.) Terrorism, p. 206-237.
“Hamas.”Terrorist Organization Profile - Hamas. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Hamzawy, Amr, and Sarah Gebowski. “From Violence to Moderation: Al-Jama’a Al-Islamiya and Al- Jihad.” Carnegie Papers 20 (2010). Print.
Helfstein, Scott and Wright, Dominic. “Covert or Convenient? Evolution of Terror Attack Networks,” Journal of Conflict Resolution, October 2011, pp. 785-813
“Hizb-I-Islami.” Terrorist Organization Profile - Hizb-I-Islami. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
“Hizbul Mujahideen (HM).” Terrorist Organization Profile-Hizbul Mujahideen (HM). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Hoffman, Bruce, “Al Qaeda, Trends in Terrorism, and Future Potentialities: An Assessment,” Studies in Conflict & Terrorism, 26, 2003, p.429-442.
Hoffman, Bruce. “The Myth of Grass-Roots Terrorism,” Foreign Affairs 87(3), 2008, p.133-138.
Hoffman, Bruce. Inside Terrorism. Rev. and expanded ed. New York: Columbia University Press, 2006. 63-71
Hoffman, Bruce and Fernando Reinares, “Conclusion,” in The Evolution of the Global Terrorist Threat, p. 618639
Holzer, Georg-Sebastian. “Somalia’s New Religious War.” Digital Library. International Relations and Security Network, 31 July 2009. Web. 9 June 2015.
“Islamic Great Eastern Raiders Front (IBDA-C).” Terrorist Organization Profile: Islamic Great Eastern Raiders Front (IBDA-C). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
“Jamaat-e-Islami.” Military. Global Security.org. Web. 9 June 2015.
“Jamiat ul-Mujahedin (JuM).” Terrorist Organization Profile - Jamiat ul-Mujahedin (JuM).
National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Jenkins, Brian Michael. “Statement on Terrorism: Current and Long-Term Threats”, Senate Armed Services Committee on Emerging Threats, November 15,2001. RAND Testimony Series. 2001.
Krebs, E. Valdis, “Mapping Networks of Terrorist Cells,” Connections 24 (3), 2002, p.43-52.
Koschade, Stuart, “A Social Network Analysis of Jemaah Islamiyah: The Applications to Counterterrorism and Intelligence,” Studies in Conflict & Terrorism 29 (6), 2006, p.559-575.
Laszlo-Barabasi, Albert, and Eric Bonabeau, “Scale-Free Networks.” Scientific American 288(5), 2003, p.60-69.
“Mahdi Army.” Terrorist Organization Profile - Mahdi Army. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Mayntz, R, “Hierarchy or network? On the Organizational Forms of Terrorism,” Berliner Journal fur Soziologie 14 (2), 2004, p.251.
“Mutassim Bellah Brigade.” Mutassim Bellah Brigade. Terrorism Research and Analysis Consortium. Web. 9 June 2015.
“Ogaden National Liberation Front (ONLF).” Terrorist Organization Profile - Ogaden National Liberation Front (ONLF). National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Pedahzur, Ami and Perliger, Arie, “The Changing Nature of Suicide Attacks: A Social Network Perspective.” Social Forces 94 (4), 2006.
Pedahzur, Ami and Perliger, Arie, Jewish Terrorism in Israel, New York: Columbia University Press (2009).
Perliger, Arie and Pedahzur, Ami, “Social Network Analysis in the Study of Terrorism and Political Violence,” Political Science and Politics, 44(1), 2011, p.45-50.
Perlinger, Arie. “Terrorist Networks’ Productivity and Durability: A Comparative Multi-Level Analysis.”
Perspectives on Terrorism, 8(4), 2014. http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/359/712.
Picarelli, John T. “The Future of Terrorism.” NIJ Journal, no. 264 (n.d.). https://www.ncjrs.gov/pdffiles1/ nij/228387.pdf.
“Rajah Solaiman Movement.” Rajah Solaiman Movement. United National Multilingual Terminology Database. Web. 9 June 2015.
“Rajah Solaiman Revolutionary Movement.” Terrorist Organization Profile - Rajah Solaiman Revolutionary Movement. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Raufer, Xavier, “Al Qaeda: A Different Diagnosis,” Studies in Conflict & Terrorism, 26 (2003): 391-398.
Rana, Amir. “Vengeance, Frictions Reviving LJ and Sipah-e-Muhammad.” Daily Times Archives. Daily Times, 7 Apr. 2004. Web. 9 June 2015.
Reynolds, Paul. “Iraq Strategy Tough to Enforce.” BBC News. BBC, 4 Oct. 2004. Web. 9 June 2015.
Ryan, Michael W. S. Decoding Al-Qaeda’s Strategy ; the Deep Battle against America. Columbia Studies in Terrorism and Irregular Warfare. New York: Columbia University Press, 2013, p. 227-229.
Sageman, Marc, Understanding Terror Networks. Philadelphia: University of Pennsylvania Press 2004.
Sageman, Marc. Leaderless Jihad: Terror Networks in the Twenty-First Century. Philadelphia: University of Pennsylvania Press, 2008.
Sahimi, Muhammad. “Who Supports Jundallah?” PBS. PBS, 20 Oct. 2009. Web. 9 June 2015.
Sakhuja, Vijay. “Terrorism or Freedom Struggle: The Free Aceh Movement by Vijay Sakhuja.” TerrorismArticles. Institute of Peace & Conflict Studies, 1 Dec. 2002. Web. 9 June 2015.
Sciolino, Elaine and Eric Schmitt, “A Not Very Private Feud over Terrorism,” New York Times, June 8, 2008.
“Signers in Blood Battalion.” Signers in Blood Battalion. Terrorism Research and Analysis Consortium. Web. 9 June 2015.
“Sirri Powz.” Sirri Powz. Terrorism Research and Analysis Consortium. Web. 9 June 2015.
“The Daily Star Web Edition Vol. 4 Num 338.” The Daily Star Web Edition Vol. 4 Num 338.
The Daily Star, 13 May 2004. Web. 9 June 2015.
“The Holders of the Black Banner.” Terrorist Organization Profile - The Holders of the Black Banner. National Consortium for the Study of Terrorism and Responses to Terrorism (START). Web. 9 June 2015.
Thomas, Timothy L.. “Al Qaeda and the Internet: The Danger of Cyberplanning,” Parameters 23(1) 2003, p.112-123.
Tunnard, Christopher, “Consulting Firm-Analyzing.” Lecture at the Fletcher School of Law and
Diplomacy, Medford, MA, 30 September 2014.
Vennesson, Pascal. “Globalization and al Qaeda’s Challenge to American Unipolarity,” in Recalling September 11th: Is Everything Different Now?, ed. James Burk, New York: Cambridge University Press, 2013, p232-61, 242.
Vidino, Lorenzo, “The Evolution of the Post-9/11 Threat to the U.S. Homeland,” in The Evolution of the Global Terrorist Threat, p. 3-28
Zurutuza, Karlos. “’We Are Suffering Genocide at the Hands of Pakistan’: An Interview with BLF Commander Allah Nazar | VICE News.” VICE News RSS. Vice News, 15 Apr. 2015. Web. 9 June 2015.
Other Coded Data for Groups
Analysis of these features of the dataset was eliminated for the sake of time and space within the article. However, future research could certainly delve more deeply into how these features of the groups relate to patterns of interactions within the network, as well as the longevity of the groups themselves.
Primary Target(s)
In an effort to determine where groups focused their operations, the dataset included the primary targets of each group. The number of primary targets each group could have was not restricted, but rather all of those identified within the Stanford project and other sources were recorded. This allowed for analysis on the combination of targets, (e.g. groups that target primarily western institutions and foreign combatants would likely be more sympathetic to the domestic population than those who target civilians and domestic combatants). The primary target groups identified were as follows:
-
Civilians
-
Foreign Combatants
-
Domestic Combatants
-
Political Figures
-
Western Institutions
Umbrella Organization
In recent years, there have been several “umbrella organizations” that have emerged within the larger global Al Qaeda network, primarily in Iraq.[39] These three organizations are listed below, however, the vast majority of groups within the dataset do not belong to any of them.
-
None
-
Jihad and Reform Front
-
The Political Council for the Iraqi Resistance
-
United Jihad Council
Yes-No Attributes
Finally, a series of yes/no demographics for each group were recorded, which can be found in the list below. These features were identified as potential factors that could either strengthen or weaken an organization’s position within the global context and were recorded to determine if the there was any sort of pattern in whether Al Qaeda Core interacted with groups that met such criteria. In coding them, a simple 1=true, 0=false system was used.
-
Is State Sponsored
-
Uses Criminal Fundraising
-
Is Funded by Other Terrorist Organizations
Is Officially Designated Terrorist Organization
Targets Combatants
Full Cohesion Measures
| 1996-2000 | ||||
| Positive Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.231 | 0.231 | -0.692 | 0.692 |
| Whole Network | -0.405 | -0.568 | -0.189 | -0.405 |
| Positive Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0 | 0.333 | -0.667 | 0.333 |
| Whole Network | -0.167 | -0.333 | -0.333 | -0.333 |
| Positive High Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | -0.333 | 1 | -1 | -0.333 |
| Whole Network | -0.6 | -0.2 | -0.6 | -0.6 |
| Positive High Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0 | 1 | -1 | 0 |
| Whole Network | -0.429 | 0.143 | -0.429 | -0.429 |
| 2001-2005 | ||||
| Positive Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.231 | 0.231 | -0.692 | 0.692 |
| Whole Network | -0.368 | -0.579 | -0.158 | -0.368 |
| Positive Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.333 | 0.333 | -0.667 | 0.667 |
| Whole Network | -0.389 | -0.556 | -0.167 | -0.444 |
| Positive High Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.429 | 0.143 | -0.429 | 0.714 |
| Whole Network | -0.448 | -0.724 | -0.034 | -0.586 |
| Positive High Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.429 | 0.143 | -0.429 | 0.714 |
| Whole Network | -0.484 | -0.724 | -0.032 | -0.613 |
| 2006-2010 | ||||
| Positive Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.75 | 0 | -1 | 0.25 |
| Whole Network | -0.403 | -0.583 | -0.667 | -0.417 |
| Positive Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.75 | 0 | -1 | 0.25 |
| Whole Network | -0.403 | -0.583 | -0.667 | -0.417 |
| Positive High Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.5 | 0.5 | -1 | 0 |
| Whole Network | -0.25 | -0.625 | -0.5 | -0.625 |
| Positive High Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 0.667 | 0 | -1 | 0.333 |
| Whole Network | -0.158 | -0.684 | -0.579 | -0.474 |
| 2011-2013 | ||||
| Positive Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 1 | 1 | -1 | 0 |
| Whole Network | -0.12 | -0.68 | -0.44 | -0.6 |
| Positive Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 1 | 1 | -1 | 0 |
| Whole Network | -0.12 | -0.68 | -0.44 | -0.6 |
| Positive High Only Cohesion (Average) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 1 | 1 | -1 | 0 |
| Whole Network | -0.217 | -0.739 | -0.391 | -0.652 |
| Positive High Only Cohesion (Highest) | ||||
| Similar Objectives | Same Region | Core/Regional Branch/ Independent Affiliate | Core/Regional Branch Only | |
| Al Qaeda Core | 1 | 1 | -1 | 0 |
| Whole Network | -0.167 | -0.75 | -0.417 | -0.667 |
Radical Groups’ Social Pressure Towards Defectors: The Case of Right-Wing Extremist Groups
by Daniel Koehler
Abstract
Research on deradicalization and disengagement from terrorist groups has produced insights into factors motivating to turn to violent milieus as well as reasons for turning away from them. Less exploration has focused on the group dynamics involved when individuals leave the group. In particular, the social pressure component, including the use of retaliatory violence, has not been adequately addressed. Testing Levine and Moreland’s theoretic model of group reaction to disloyalty, this article illustrates how extremist groups determine the type of social pressure, using five problem-centred interviews with former German neo-Nazis, as well as 12 cases of violent social pressure on defectors in Germany and the United States. The main argument of this article is that a group’s internal negotiation process regarding the pressure is typically segmented into two phases: one emotionally-based, immediately after the defection and a second, more rational and strategic response phase later on. Important factors determining the group’s reaction are: the in-group status of the defector, group specific ideology, in-group future prospects and strategies, group structure, prevention of further defection, in-group behavioural learning processes, the defection process itself, and pressure on the group from the government.
Keywords: Germany; right-wing extremism; deradicalization; defection; disloyalty; social pressure
Introduction
In November 2011, German police discovered that a right-wing extremist terrorist cell which called itself the “National Socialist Underground (NSU),” had killed at least 10 people, was responsible for two bombings, and had committed more than a dozen bank robberies over a period of more than 14 years.[40]
The trial against the only surviving member of the cell, Beate Zschape, and several alleged supporters started in May 2013 and included witness statements of former right-wing activists. In one statement, a defendant told the court that during his time in the movement “deviant” behaviour, such as eating non-German food, was heavily punished. In his case he had to do push ups while being whipped[41]. This severe form of social pressure only scratches the surface of what might happen to group members who consider leaving the group and its ideology behind. In fact, numerous cases of murdering defectors are publicly known.
Although violent reactions and social pressure by right-wing groups towards potential and successful defectors are well-known within deradicalization research, no systematic study about the mechanisms and factors determining the types of social pressure inflicted by these groups exists at present. Most of the literature on this issue focuses on the micro-social level and has established a number of important individual motivations for joining and leaving such groups. A significant gap, however, can be found at the meso-social level, as it is almost unknown which mechanisms and determining factors lead to specific forms of social pressure which aim to either prevent individual defection or retaliate against those former group members who have left the group. The present study therefore addresses the question: what are the mechanisms and determining factors for social pressure to be directed at potential and successful defectors within extreme right-wing groups? In addition, this article looks at the types of pressure typically used and the benefit envisioned by the group.
Methods and Sources
This article is based on five problem-centred interviews[42] with former members from the German rightwing extremist scene. These interviews focused on two biographical phases-active time and post-defectionasking about the respondents’ experiences with social pressure when the group was confronted with defections during their active involvement, and how the group they belonged to reacted after the departure of those interviewed. The interviews applied a semi-structured questionnaire. All interviews were recorded, transcribed and qualitatively analysed, using MAXQDA software in several parallel coding and re-coding phases. The interviews were conducted with the full consent of the respondents, within a safe environment (e.g. the researcher’s office or a place of choice selected by the interviewee), and in full accordance with the APA ethical standards. Quotes have been translated into English by the author. The sample consisted of four male and one female interviewees. The respondents age ranged from 23 to 37 years (average being 32.6), reflecting the fact that all of the former extremists had relatively long careers in the German neo-Nazi movement and left after occupying high ranking positions. In order to protect the interviewees’ identities all have been given alias names when quoted.
In addition, twelve cases of publicly known violent retaliations executed by extreme right-wing groups in Germany and the United States were analyzed, using information that was in the public domain (press reports, court documents, and published interviews with perpetrators or victims). A list of these cases is provided in the Annex. These two countries (USA and GFR)) were chosen because they provide a high number of well-documented incidents.
Literature Review
Deradicalization Research
Research about deradicalization and disengagement processes from radical social movements and terrorist groups has produced very important insights into individual motivations to join and leave these milieus. So called ‘push’ and ‘pull’ factors have been identified, which together determine individual decisions to leave extremist groups. ‘Push’ factors include, but are not limited to, sanctions by the government, loss of faith in the group’s cause, disillusionment, lack of faith, burnout, decline in personal status, as well as conflicts within the group or discontent with the group’s strategy[43]. ‘Pull’ factors typically consist of individual efforts to return to a “normal” life, changes in family situations, new goals for future developments, getting older, and finding new friends or develop intimate relationships[44]. Leaving a radical or terrorist group is not a irreversible but a highly complex process. It involves many risks for the potential defector, including inhibiting factors such as positive aspects of life within the group, lack of future perspectives outside the group, losing protection against enemies as well as potential judicial sanctions[45]. Group sanctions are among the strongest reasons for some defectors to abstain from leaving, although some groups appear not to react with violence against defectors. Tore Bj0rgo[46] has noted that, should former members leave middle- or upper cadre levels in the group’s hierarchy and should they provide information to extreme left-wing groups, police or media, group reactions my include disappointment, observation, death threats, physical attacks, harassment, verbal threats and expression of contempt, but only rarely killings.This has also been reported by Horgan[47] and Aho regarding contact with the media [48].
In other cases, reports about special arrangements between defectors and the group have surfaced, e.g. the practice of ‘separation contracts’ by al-Qaeda, as described by John Horgan[49], vacation breaks for IRA members[50] or severe death threats for potential defectors in case of the Ulster Defence Forces (UDA)[51]. Other groups have relied on blackmailing potential and successful defectors, either by making public information about crimes committed by the defector in the past or by threatening to disclose signed vows of loyalty to the ideology from the defectors[52].
Although the literature on deradicalization and disengagement does not provide much in terms of evidence to substantiate such observations, scholars have identified at least two categories of group reactions which are strongly dependent on the defector’s former status, time spent within the group and his/her post-defection behaviour regarding groups hostile to the former one [53]: (i) a ‘quiet’ exit without any sanction or pressure and, (ii) some form of verbal and/or physical aggression. If radical groups resort to violence, it is usually very severe. Cases of defectors being crucified by their former group, arson attacks against their homes, home invasions, and targeted robberies have been described in interview studies with former extremists [54]. As a very common first reaction, the complete social and physical banishment of the defector was described[55].
In addition, studies of deradicalization programs in a prison context have shown that sometimes a competition between radical groups over the membership of potential defectors can lead to more positive forms of social pressure (i.e. incentives) to prevent members from leaving, for example in Israeli prisons[56].
Terrorism Studies
In other related academic fields, such as terrorism studies or social psychology, potential violent reactions of groups confronted with defections are generally known, but rarely qualified or analysed as such. Researching the community context of terrorism for example, Bates[57] briefly touches on the issue by stating that terrorists groups, which are “normative coercive,”[58] rely on “sustaining loyalty” as a “significant priority” and develop “elaborate strategies to preserve morale and membership” including “more formal controls”[59]. When confronted with individual defection, these groups might even use deadly violence as the highest level of social pressure:
Terror or enforcing squads are used to retaliate against defectors. (...) While a great loss of status seldom results from a single act, serious or persistent deviations may lead to loss of status, one’s reputation as a trusted member, or even one’s life within the terrorist movement.[60].
Social Psychology
Examining other areas of social psychology that discuss social processes on the meso-social level, typically either internal group dynamics[61] or group formation related topics[62] are extensively discussed and analysed. However, the specific mechanisms behind the application of social pressure on the defector, including processes of decision making and factors determining the potential options and behaviour when confronted with individual defection and disloyalty, have not received any attention from social psychologists or related academic fields. The only known exception is the model by Levine and Moreland[63], which lays out a theoretical framework of potential group reactions when confronted with individual disloyalty (in nonradical contexts). This present article attempts to empirically test Levine and Moreland’s theoretical concept in the area of radical social movements (i.e. the extreme right) using the interviews and case studies to validate and further develop their model.
On the one hand, Levine and Moreland collect known possible group reactions in cases of disloyalty: “the punishments associated with disloyalty are often quite negative, including public condemnation, imprisonment, and death“[64]. According to Levine and Moreland the reasons for these negative sanctions are rooted within the competition between groups and the subsequent loss or gain of advantage through defectors[65]. In general, the authors distinguish four types of defectors: “reliable defector (current and future orientation toward the group positive), unreliable defector (current positive, future likely negative), unreliable spies (current negative, future positive), reliable spies (current negative, future negative)“[66]. This typology reflects the previously explained role of defectors’ behaviour against the former group (e.g. giving information to police, to left-wing groups, or to the media) in the field of right-wing extremism. Levine and Moreland name the defector’s status within the group, his/her motivation to leave, time spent in the group, knowledge about the group, personal relationships within the group, and the group’s general character (groups under high “pressure” are likely to react more harshly when confronted with disloyalty) as the most important factors determining the specific course of action undertaken by the group[67].
Accordingly, Levine and Moreland’s model predicts that groups facing strong competition will react harshly and negatively towards those defectors whom they perceive to create a disadvantage for the group as well as positively attempting to win back those who have not totally broken with the group’s collective identity or narrative. This is supported by literature on organizational turnover, which might have serious negative impacts on organizations in terms of operational costs and demoralization of organizational membership[68]. Thus, sanctions against defection or positive rewards to avoid it can be expected.
Summary
In summation, the literature on deradicalization and disengagement processes has not addressed the question of how radical groups form defection-inhibiting social pressure. Nevertheless, this literature suggests several types of social pressure (i.e. violence, threats, blackmailing, condemnation and slander) They are typically determined (most importantly) by the length of time spent in the group and the behaviour towards it after the defection (i.e. information given to the police, media, anti-racists). However, these claims have yet to be validated by empirical studies focusing on this aspect.
Findings
Types of Defectors
One of the first observations in the literature refers to the fact that groups appear to differentiate between various types of defectors, based on their expected future behaviour regarding the group. Levine and Moreland’s model predicts negative group sanctions for at least two types: current negative/future positive and current positive/future negative. Translated to the radical social movements, this classification would relate to the question of individual motivation to defect, i.e. the degree to which the group’s ideology is questioned or whether more personal reasons affected the decision. In addition the future behaviour towards the group was stated by Levine and Moreland as critical. This was strongly supported by most of the interviewees. Interviewee ‘John’ instantly could identify three types of defectors requiring different reactions from the group. He differentiated between defectors who merely ‘retire’ without questioning the group’s ideology (type A, called “dropouts”), persons who leave the group and ideology behind but do not speak out against the former group (type B “renegades”), and those who leave behind both the group and its ideology and become publically active against the former group (type C “traitors”). Two points were central for this group-internal classification: the remaining degree of adherence to the ideology and the level of counteractivism against the former group.
Future Behaviour towards Group
The element of ‘betrayal’ in the form of passing on information towards police, anti-fascists or the press was seen as one the most important criteria to assign the above mentioned categories, which also directly supports Levine and Moreland’s model. The main logic behind this process was the fear of incriminating knowledge ending up with enemies of the group. In one case a very brutal reaction followed after a short period of shock within the group:
“This was indeed a very extreme group reaction, because he did conspire with the political enemy. How it would have been, if he wouldn’t have been seen there I can’t say of course. But back then I found this very hard. Because he was a very close friend and one never expected that he would defect to the political enemy. It was like being paralysed with shock in the first moment; no one from the group did expect that he would do something like that.” (Transcript “Ted”)
‘Ted’ continued to describe how he and the group felt deeply betrayed by this defector, a feeling mostly fuelled by panic and fear of concrete information possibly revealed by the defector. ‘Ted’ himself left the movement quietly, which resulted in an almost complete absence of any reaction by the group, except for a few half-hearted attempts to contact him. ‘Ted’ explained this lack of backlash with the fact that the group did not know that he gave information to outsiders. It is especially noteworthy that ‘Ted’ describes that his former group regularly accepted also other defections, without much disturbance or reaction at all. This however was only the case with ‘type A’ defectors. Others were declared open targets.
Several of the case studies support this dynamic of right-wing groups resorting to violence after the defector had committed an ‘act of treason’. In 1984, for example, eight German right-wing extremists held ‘court’ and sentenced a former leading member of their ‘combat group’ to severe punishment due to treason. The group raided the victim’s home at night, read an indictment to him, and severely assaulted him. The victim was also water boarded and threatened with an weapon pointing at his head which turned out to be unloaded. After another round of beatings, the person was left in a forest to die, but luckily survived.[69] Another case happened on February 3rd, 1987. It led to the murder of the 17 year old German Gerd-Roger Bornemann by his former comrades after he had made witness statements to the police.[70] In yet another case, in March 1996 the 26 year old former German neo-Nazi Martin Kemming was shot and killed by a former comrade[71].
Sometimes even the attempt to leave the group is seen as sufficient to use violence. James A. Aho [72] reported that in 1988 two persons in his sample were physically attacked and massively threatened once their decision to leave the right-wing milieu became known. In several other cases, the act of defection itself was the only reason for the violent reaction, indicating that, as postulated by Levine and Moreland, the group’s general character by itself plays a very important role. One female defector who left a skinhead group did not recall any differentiation regarding type of defectors, as her former group routinely employing violence in reaction to defection. When asked how she saw defectors during her active time ‘Maria’ replied: “They were traitors, they were subhuman people, and they were free to be shot.” In this case the act of defection was automatically equated with treason. From this it would appear that some groups simply could not muster the necessary reflective and intellectual skills to distinguish between different types of defectors and different forms of social pressure.
Forms of Social Pressure
Previous studies as well as Levine and Moreland’s model suggest that groups use a variety of forms of social pressure ranging from public condemnation, monetary fines, verbal abuse, ostracism all the way to torture to death.[73] In regard to right-wing groups, it was suggested that if the groups react at all, it would typical result in threats, verbal abuse, blackmailing, slander but rarely lead to lethal violence.[74] However, the interview sample and the case studies (see Annex) suggest that (severe) forms of violence are much more common than suggested by the Levine and Moreland’s model as well as other authors. One risk is that groups might not take the time or have the skills to differentiate between various types of defectors. It could also be that the group was simply not willing to take the risk, and as a consequence almost all interviewees reported immediate resort to violence. ‘Maria’s’ group deployed a very specific method to deal with defections. In this case, the group generally came together and formed something the interviewee called “Skinhead Control Commandos”, a small group of selected executors for the punishment, which consisted of arson attacks and heavy beatings. Like a task force, this ‘commando’ met prior to the attack and planned the form of retaliation: “Well we sat together and then it started: We drive there. What do we do, what do we take with us? A baseball bat, Molotov cocktails, brass knuckles, self-made things and so forth.” (Transcript “Maria”)
This form of direct retaliatory violence was, however, an exception rather than the rule. Typically the groups tried to find an appropriate strategy to deal with the situation; rarely did it resorted to long-lasting strategic violence. One example of this would be the case of the former high ranking German neo-Nazi leader Ingo Hasselbach. He received a fully functional mail-bomb in 1993, only good luck prevented it from exploding [75].
Group Reaction Differentiation According to Defector Type
Interviewee “John” described how his group deployed different form of reactions depending on the defector type, thereby confirming Levine and Moreland’s claim of group reaction differentiation according to defector types. ‘Type A’ defections usually caused great disappointment and feelings of betrayal because friendship, according to John, could never be understood alone without the political cause. However, other than distancing and the expression of disappointment, the group did not attempt to do anything else. ‘Type B’ defectors were usually seen as blinded through other social forces (e.g. family) or interests. Sometimes the group first responded positively by trying to win the former member back.
‘Type C’ defectors received the harshest group treatment. Verbal intimidation, physical violence and arson attacks on the defector’s home were variations of response. In this case, it was important for the group to add specific information about the punishment’s origin:
“The other option would have been, and that was planned (...) to visit him at his residence and afflict physical violence upon him. This was to be done in specific combined with a clear message, so not only physical violence, which indeed has a symbolic value, but we wanted to give a name to the whole thing. He had to know where this is coming from. Also for the outside, for others who might decide to leave, we wanted to set an example.” (Transcript “John”)
In all cases, the group was very careful to make in advance a detailed ‘cost-benefit’ analysis, so as to balance the potential negative reactions and expected beneficial effects. Another interviewee reported that his former group systematically kept defectors under surveillance and interrogated them as soon as a specific ‘hostile’ behaviour was noted. In several cases, group members attempted to break in the defectors’ homes, drag the persons out and punish them, because they had “spoken with the political enemy”.
“Peter”, another interviewee who left a well-structured neo-Nazi organization, described how his former group planned “campaigns” against defectors, and how he actively participated in two of those campaigns against former members while he was an active neo-Nazi. He threatened them via phone calls and helped to create something he called “scenarios of intimidation”. He also took part in several group meetings that discussed revenge operations against defectors. One operation against a defector, who allegedly had provided information to the police, even targeted the defector’s mother - suggesting that she be murdered. Peter described how leading group members spurred others against the defectors, prodding lower ranking members of the group to execute the punishment more or less on their own.
Stirring up other members of the right-wing movement beyond those in one’s own group to act against the defector was reported in all cases and included tactics ranging from ostracism to slander campaigns. In such cases, names, addresses and slanderous allegations were typically published online. All former extremists interviewed reported online campaigns against them. Typically these campaigns aimed to “prove” that the former member was corrupt, a paedophile, mentally unstable, a drug addict, police informant, weak and worthless.
Another tactic is to turn up at any public place the defector might be found and make a ‘show of force’. Frequent phone calls, letters, and specifically targeted propaganda (i.e. stickers and flyers left only in the mailbox of the defector) aimed to create ‘scenarios of intimidation’, which, at times could have fatal consequences. In 1980, for example, a former US-American neo-Nazi died of a heart attack after a series of death threats and bomb and arson attacks on his home[76]. In ‘Maria’s’ case, such intimidation campaigns came in waves-the result of a revived interest triggered by certain events that brought her back into the group’s memory.
How Groups Arrive at a Strategy
In all cases of the sample, the former groups had some sort of mechanism to determine the course of action and selected the form of social pressure to be applied - something going beyond the options contained in the Levine and Moreland’s model. This ranged from very formal meetings, called ‘courts’, where highly strategic discussions took place in an attempt to assess the cost-benefit ratio of any damage control tactic. Many groups feared that violent retaliation could create “blowback” for the group and tried to develop longterm forms of social pressure, e.g. in the form of online defamation campaigns. As stated by one interviewee, the actual situation of the group and its level of information regarding the case under consideration were most important factors influencing the selected course of action. Seeking revenge for treason and for the disclosure of group secrets, were described by all respondents as main drivers behind exercising pressure on defectors. Many interviewees described a first phase of emotional shock caused by the defection, followed by a subsequent phase of more rational planning. ‘John’ described how every defection from the movement caused a general eclat. News about recent defections travels fast and often result in pressure from other extremist groups to offer an explanation how this could be allowed to happen in the first place. Defections appear to be highly embarrassing for each group, and influences their standing negatively within the larger movement, promoting the notion that they are suffering from internal divisions and lack of resolution.
This supports Levine and Moreland’s theory the inter-group competition is the main reason for social pressure in the event of disloyalty. It is seen as a potential threat within the right-wing movement when defections could lead to the collapse of smaller groups. Rarely, however, are defections seen as a form of purification. All interviewees reported that defections had the long-term effect of treating newcomers with a higher degree of suspicion which led to more aggressive demands that they quick integrate into the group and obey its collective norms.
Discussion of Findings and Future Directions for Research
Looking at these findings, previous research as well as Levine and Moreland’s model, many of the suggested forms of social pressure have been confirmed by the interviews and by case studies. Verbal threats, ostracism campaigns and (albeit to a higher degree than postulated in the literature) violence were the most common forms of social pressure. As suspected by Levine and Moreland, (internal) group competition is one major driving force behind some of these actions. In addition, there is the fear of incriminating information being passed on to the group’s enemies. Although right-wing groups appear to distinguish between various types of defections, the differentiation is not as detailed and complex as Levine and Moreland assumed. In general, such groups distinguish mainly on the basis of an assessment whether or not the defector abandons the group’s ideology or not, and whether his or her future behaviour might involve cooperating with the group’s enemies. Several groups did not want to take any risk and resorted directly to the use of violence as punishment, seeing the defection as equal to betraying the group’s ideology, which, in this author’s view, is a noteworthy and important finding since the role of commitment to the ideology as a factor determining the group reaction has not been mentioned at all in previous research. So far only doubts about the group’s ideology have been identified as cause for individual disengagement.[77] Several major factors determining violent forms of social pressure suggested in the existing literature and by Levine and Moreland have, on the other hand, been strongly confirmed - in particular the importance of the length of time spent in the group, the status of the defector, his or her possession of incriminating information, and the role of motivation behind the decision to leave the group. In addition, positive attempts to win back defectors—one of our findings— have only rarely been reported in the existing literature..
Group Decision Making Processes
As for the processes and mechanisms behind the group’s decision to employ certain forms of social pressure, this study has produced some unique and novel insights. First, group reaction to defection influenced as much by group-related factors as by defector-related factors-something not foreseen by Levine and Moreland. Relevant factors are the group-specific ideology (especially in regard to the status of treason etc.), group affinity to violence, in-group future prospects, group structure and hierarchy (especially in regard to decision-making and strategic reflection about possible consequences), the danger of further defections, pressure on the group by the government, relative status of the group within the larger movement as well as the overall movement’s political position, and, finally the role of in-group behavioural learning processes. Furthermore, when confronted with defections, right-wing groups typically were found to go through two distinct phases of decision-making-something not mentioned by Levine and Moreland. At first, emotions (Phase I) dominate the group’s decision-making process. (Mis-)Guided by feelings of personal betrayal, shock, anger, and fear about secrets to be disclosed to the authorities or the public, violence in all its forms is considered as a gut reaction. If the defector amplifies these emotions through behaviour perceived as threat by the group, the group is most likely to respond with direct physical violence or at least with strong physical intimidation. After a certain period of ‘cooling down’ and getting accustomed to the fact that a defection has taken place, generally more mature strategic reflection and planning comes into play (Phase II). In this phase, the group calculates the costs and benefits of any retaliatory action, taking into account possible blowback against the group. Typically the methods chosen in this phase are large-scale defamation and ostracism campaigns, public outings, ‘scenes of intimidation’, and direct anonymous threats (by mail or phone) targeting the defector or his family. Carefully planned and complex violent operations such as assassinations and bombings do occur. However these are relatively rare, and are usually applied only when the group is not prepared to take the risk of information leakage or when the defector, by his former status, becomes a liability to the group (e.g. when s/he speaks out against it publically). Phase I can be ‘resumed’ even after a long period of time, Typically this is the case when group members meet the defector by accident or when certain events (e.g. media articles, court verdicts, group banning) are directly connected to the defector and revive the group’s initial emotional reaction.
All groups had more or less sophisticated decision-making processes, based on the group’s hierarchy and intellectual level. This is also a finding that goes beyond Levine and Moreland’s model. It turned out that even the more violent and non-intellectual skinhead type groups displayed surprising organizational skills to exercise social pressure (e.g. the ‘skinhead control commandos’). This took the form of online blogs, fanzines, and chat rooms containing pictures, addresses and family information of defectors. Followed by targeted propaganda distribution (e.g. leaflets with the defector’s name written on it), this all serves to create ‘scenes of intimidation’ based on the psychological fear of becoming a target of retaliation.
While these findings are limited due to the small sample of cases analysed, nevertheless new light is shed on some meso-social dynamics of social pressure against defectors from extremist right-wing groups. While many of the factors and mechanisms suggested by Levine and Moreland’s original model have been strongly supported, it has also been shown that group-related mechanisms regarding applying social pressure on defectors are much more complex which points to the need for more research. As an important future direction for research, the reaction of other extremist movements vis-a-vis defectors (e.g. defectors from jihadist groups) should be explored in order to better determine the role of specific ideologies in the selection of forms of punishment meted out against who have lost faith in extremist groups.
About the Author: Daniel Koehler is the Director of the German Institute on Radicalization and Deradicalization Studies (GIRDS) in Berlin, Germany since November 2015. He is also a Fellow at the George Washington University’s Center for Homeland and Cyber Security Program on Extremism. He has worked for over six years in the practical field of de-radicalization as case manager and has trained mentors as well as designed different tools and programs. He has done extensive research on various aspects related to terrorist rehabilitation and de-radicalization.
Annex: Brief Case Descriptions
1. 1980: a former US-American neo-Nazi died of a heart attack after repeated bomb and arson attacks
on his home and death threats.[78]
2. 1984 eight German right-wing extremists “held court” and sentenced a former leading member of
their “combat group” to severe punishment due to treason. The group broke into the victim’s home at night, read the indictment to him, and severely beat him. The victim was water boarded and “shot” with an unloaded weapon put to his head. After another round of beating up the person was brought to a forest to die but he luckily survived.[79]
3. 1987: the 17 year old German Gerd-Roger Bornemann was killed by his former comrades after he had
given witness statements to the police.[80]
4. 1987: a former Ku Klux Klan leader was crucified by other Klansmen in Sacramento.[81]
5. 1988: in California “a disenchanted female member of the Chicago Area Skinheads (CASH), had her
home broken into, her face maced, her body beaten limp, and a swastika painted on the wall with her own blood”.[82]
6. 1988: Aho [83] reports of two persons in his sample who were physically attacked and massively
threatened once their decision to leave the right-wing environment became known.
7. 1993: the former high ranking German neo-Nazi leader Ingo Hasselbach received a fully functional
mail-bomb which did not explode due to unforeseen circumstances.[84]
8. 1995: the former German neo-Nazi skinhead Sven Silbermann and his brother Michael were found
dead in Dresden. Sven Silbermann was outed as ‘traitor’ shortly before, and his brother had possible links to a right-wing terrorist group.[85]
9. 1996: the 26 year old former German neo-Nazi Martin Kemming was shot and killed by a former
comrade.[86] Kemming had left the right-wing movement and acted as a court witness against the person who would later kill him.
10. 2011: a youth court sentenced five German neo-Nazis to serve several years in prison due to their massive violent assault on a defector, whom they lured into a trap and severely beat him.[87]
11. 2011: a former German neo-Nazi (together with his girlfriend) met a former comrade by accident at a train station in Berlin. After he was recognized another 10 neo-Nazis were called into the train station and tried to attack the defector with his girlfriend, who sought protection with the train station personnel. The 11 right-wing activists split up and controlled the entry and exit doors of the train station until police arrived.[88]
12. 2014: five German neo-Nazis attacked a person and his girlfriend in Berlin and severely injured them. Although the person might not be seen as a full defector (as he still expressed sympathy for national socialist ideology online) he was the target of a long-lasting online defamation campaign, in which he was accused as ‘traitor’ who gave witness statements in court against former comrades.[89]
Bibliography
Aho, James A. “Out of Hate: A Sociology of Defection from Neo-Nazism.” Current Research on Peace and Violence 11, no. 4 (1988): 159-68.
Altier, Mary Beth, Christian N Thoroughgood, and John G Horgan. “Turning Away from Terrorism: Lessons from Psychology, Sociology, and Criminology.” Journal of Peace Research 51, no. 5 (September 1, 2014 2014): 647-61.
Barrelle, Kate. “Pro-Integration: Disengagement from and Life after Extremism.” Behavioral Sciences of Terrorism and Political Aggression 7, no. 2 (2014/12/21 2015): 129-42.
Bates, Rodger A. “Terrorism within the Community Context.” The Journal of Public and Professional Sociology 3, no. 1 (2010): 1-14.
Bj0rgo, Tore. “Processes of Disengagement from Violent Groups of the Extreme Right” In Leaving Terrorism Behind. Individual and Collective Disengagement, edited by Tore Bj0rgo and John Horgan, 30-48. New York: Routledge, 2009.
———. Racist and Right-Wing Violence in Scandinavia: Patterns, Perpetrators, and Responses. Oslo: Aschehoug, 1997.
Bj0rgo, Tore, and John Horgan. Leaving Terrorism Behind: Individual and Collective Disengagement. London/ New York: Routledge, 2009.
Boyd, Robert, Herbert Gintis, Samuel Bowles, and Peter J. Richerson. “The Evolution of Altruistic Punishment.” Proceedings of the National Academy of Sciences 100, no. 6 (March 18, 2003 2003): 3531-35.
Campbell, Donald Thomas. “Ethnocentric and Other Altruistic Motives.” In Nebraska Symposium on Motivation, edited by David Levine, 283-311. Lincoln: University of Nebraska Press, 1965.
Dalgaard-Nielsen, Anja. “Promoting Exit from Violent Extremism: Themes and Approaches.” Studies in Conflict & Terrorism 36, no. 2 (2013/10/27 2013): 99-115.
Demant, F., Marieke Slootman, F. J. Buijs, and Jean Tillie. “Decline and Disengagement-an Analysis of Processes of Deradicalisation.” In IMES Report Series. Amsterdam: Institute for Migration and Ethnic Studies (IMES), 2008.
Disley, Emma, Kristin Weed, Anais Reding, Lindsay Clutterbuck, and Richard Warnes. “Individual Disengagement from Al Qa’ida-Influenced Terrorist Groups: A Rapid Evidence Assessment to Inform Policy and Practice in Preventing Terrorism.” Cambridge: RAND Europe, 2011.
Fink, Chowdhury Naureen, and Ellie B. Haerne. “Beyond Terrorism: Deradicalization and Disengagement from Violent Extremism.” International Peace Insitute, 2008.
Ganor, Boaz, and Ophir Falk. “De-Radicalization in Israel’s Prison System.” Studies in Conflict & Terrorism 36, no. 2 (2014/11/18 2013): 116-31.
Garfinkel, Renee. “Personal Transformations. Moving from Violence to Peace.” In Special Report: United States Institute of Peace, 2007.
Gegenrede. “Berlin-Lichtenberg: Rechte Jagen Szene-Aussteiger.” In gegenrede. Informationsportal gegen Rechtsextremismus fur Demokratie., 2011.
Hart, Claire M., and Mark Van Vugt. “From Fault Line to Group Fission: Understanding Membership Changes in Small Groups.” Personality and Social Psychology Bulletin 32, no. 3 (March 1, 2006 2006): 392-404.
Hasselbach, Ingo, and Tom Reiss. Fuhrer-Ex : Memoirs of a Former Neo-Nazi. 1st ed. New York: Random House, 1996.
Horgan, John. Walking Away from Terrorism: Accounts of Disengagement from Radical and Extremist Movements. London/New York: Routledge, 2009.
Klufimann. “Explosives Klima.” http://www.spiegel.de/spiegel/print/d-8848666.html.
Kruglanski, Arie W., and Donna M. Webster. “Group Members’ Reactions to Opinion Deviates and Conformists at Varying Degrees of Proximity to Decision Deadline and of Environmental Noise.” Journal of Personality and Social Psychology 61, no. 2 (1991): 212-25.
Levine, John M., and Richard L. Moreland. “Group Reactions to Loyalty and Disloyalty.”. In Group Cohesion, Trust and Solidarity. Advances in Group Processes, edited by Shane R. Thye, 203-28: Elsevier Science/JAI Press, 2002.
Maegerle, A. “Rechtsextremistische Gewalt Und Terror” In Handbuch Rechtsradikalismus. Personen- Organisationen-Netzwerke Vom Neonazismus Bis in Die Mitte Der Gesellschaft, edited by Bernd Wagner and Thomas Grumke, 159-72. Opladen: Leske und Budrich, 2002.
Mauer, R. “Violence Plagued Ex-Aryan Ally.” Idaho Statesman, September 17 1980.
Noricks, Darcy M.E. “Disengagement and Deradicalization: Processes and Programs.” In Social Science for Counterterrorism. Putting the Pieces Together., edited by Paul K. Davis and Kim Cragin, 299-320. Santa Monica: Rand Corporation, 2009.
Peel, Quentin. “The Faces of Neo-Nazism.” http://www.ft.Com/cms/s/2/dfda3010-3438-11e2-9ae7- 00144feabdc0.html#axzz2K6JSUB7i.
Pidd, Helen. “How Could German Neo-Nazi Killers Have Evaded Police for 13 Years?” The Guardian, November 18 2011.
———. “Neo-Nazi Terror Scandal Grows in Germany.” The Guardian, November 16 2011.
Rhein-Zeitung. “Neonazi-Prozess: Funf Rechte Schlager Mussen Ins Gefangnis.” Rhein-Zeitung, October 30 2011.
Riehl-Heyse, Herbert. “Bilder Einer Schaurigen Traumwelt. Beobachtungen in Einem Prozess Gegen Junge Neonazis.”. In Rechtsextremismus in Der Bundesrepublik. Vorrausstetzungen, Zusammenhange, Wirkungen., edited by Wolfgang Benz, 295-98. Frankfurt am Main, 1984.
Rochford, E. Burke, Jr. “Factionalism, Group Defection, and Schism in the Hare Krishna Movement.” Journal for the Scientific Study of Religion 28, no. 2 (1989): 162-79.
Sani, Fabio. “When Subgroups Secede: Extending and Refining the Social Psychological Model of Schism in Groups.” Personality and Social Psychology Bulletin 31, no. 8 (August 1, 2005 2005): 1074-86.
Sani, Fabio, and John Todman. “Should We Stay or Should We Go? A Social Psychological Model of Schisms in Groups.” Personality and Social Psychology Bulletin 28, no. 12 (December 1, 2002 2002): 1647-55.
Schneider, Theo. “Blutiger Szenestreit in Berlin.” In Stoerungsmelder. Berlin: ZeitOnline, 2014.
Spiegel. “The Brown Army Faction: A Disturbing New Dimension of Far-Right Terror.” SpiegelOnline, http:// www.spiegel.de/international/germany/the-brown-army-faction-a-disturbing-new-dimension-of-far-right- terror-a-797569-4.html.
———. “Ei Im Nest.” Der Spiegel, 1983, 67-68.
———. “Neo-Nazi Killings: Terror Trio’s Network May Have Been Bigger.” Der Spiegel, March 25 2013.
-------- . “Sachsen: Mogliche Nsu-Verbindung Zu Ungeklartem Doppelmord.” Der Spiegel, June 6 2014.
———. “Verrater Verfallen Der Feme.” Der Spiegel, May 13 1996.
Staw, Barry M. “The Consequences of Turnover.” Journal of occupational Behaviour (1980): 253-73.
Sundermann, Tom. “Wer Doner Afi, Wurde Ausgepeitscht.” Die Zeit, June 18 2013.
UPI. “Ex-Kkk and Neo-Nazi Leader Found Nailed to Board.” Los Angeles Times, August 11 1987.
van der Valk, Ineke, and Willem Wagenaar. “The Extreme Right: Entry and Exit.” In Racism & Extremism Monitor. Leiden: Anne Frank House/Leiden University, 2010.
Witzel, Andreas, and Herwig Reiter. The Problem-Centered Interview. 2000. Vol. 1, New York: Sage, 2012.
Religion, Democracy and Terrorism
by Nilay Saiya
Abstract
One of the most important policy-relevant questions terrorism researchers have attempted to address is the relationship between democracy and terrorism. Some extol the virtues of democracy in combating or discouraging terrorism. Others claim that the vulnerabilities inherent in democracy make terrorist activity easier to carry out. This essay suggests that both schools of thought may be correct: democracies suffer disproportionately from certain manifestations of terrorism but not others. Specifically, I show that religious terrorists - those who prescribe for themselves religious aims and identities-are more likely to target authoritarian states, while non-religious terrorists tend to attack liberal democracies. The reason for this is two-fold: (i) religious terrorists are not as deterred by systemic repression as their secular counterparts and (ii) authoritarian countries breed religious extremism by radicalizing religious actors, weakening moderates and increasing support for extremism by making religion a point of cohesion against the state. States that provide religious security for their citizens, on the other hand - the common understanding that religious identity (including beliefs and practices) of groups and individuals in society is inviolable-undercut the narrative propounded by religious militants that their faith is under attack, thus dampening the impetus towards violence. Religiously secure countries also allow for the development of cross-cutting cleavages other than those rooted in religion. For this reason, secular terrorism is more likely to occur in liberal countries than in repressive ones.
Keywords: Terrorism; religion; democracy
The Democracy-Terrorism Debate
Scholars of terrorism have been studying the connections between democracy and terrorism for decades.
Yet the literature on democracy and terrorism has not reached a conclusive verdict. On one side are those who argue that democracy mitigates terrorism. These studies reveal an inverse relationship between political freedom and the likelihood of terrorism. The logic here is straightforward: the availability of political representation found in democracies and not present in repressive states affords groups and individuals the ability to select their leaders, pursue their political ambitions, and air their grievances through political channels rather than resorting to terrorism. In this same vein, some scholars have found that the democratic commitment to civil liberties also lessens the risk of terrorism and other forms of political violence.[90] Thus democracies are believed to be “accessible systems” that naturally undercut the motivations for terrorist activity by providing legitimate, non-violent avenues for political dissent.[91] Contrariwise, authoritarian regimes that choke nonviolent avenues of dissent, ban participation in political decisionmaking and curb freedom of expression incentivize terrorist activity in that they leave violence as the only way by which aggrieved persons can try to change the system.[92] Such systems also serve to delegitimize the state, alienate citizens, and increase popular grievances, thus providing terrorists with a steady supply of support from among ordinary citizens.[93] Furthermore, when these kinds of regimes harshly crack down on more peaceful forms of dissent such as protests, they invite retaliatory violence against governmental brutality.[94]
Democracies also make superior counter-terrorists, according to this school of thought. Max Abrahms, James I. Walsh and James A. Piazza, for example, have all argued that a commitment to civil liberties restrains democracies from overreacting to terrorism-the precise thing that terrorists want them to do. For countries to violate their liberal values in combating terror risks losing the support of the very constituencies- moderates, the international community, and their own publics-required for success. On the other hand, by goading states into using excessive force, terrorists can actually engender support from those would otherwise be sympathetic towards the state.[95]
On the debate’s other side are those who claim that instead of diffusing terrorism, democracy actually enables it.[96] This school of thought holds that the qualities inherent in democracies serve to facilitate attacks by militants. For instance, the democratic commitment to the rule of law, limits on the executive, and respect for individual rights (especially freedoms of movement, speech, and association) enable terrorist activity by providing militants with an open space to attract sympathizers, recruit members and plot attacks.[97] Furthermore the presence of a free media makes it easier for terrorists to spew propaganda, communicate which each other and claim responsibility for terrorist strikes, thus making violence easier for terrorists in democracies.[98]
Democracies are also believed to be inferior in terms of responding to terrorism by making the detention and prosecution of suspected terrorists more cumbersome due to restrictions on policing, a commitment to due process, and the presence of an independent judiciary.[99] By contrast, authoritarian states are less susceptible to terrorism precisely because they have greater capacities to monitor society, more restraints on movement, more media restrictions, and fewer constraints on surveillance and interrogation practices, thus raising the costs of participating in terrorist activity.[100] In short, according to this school, non-democracies experience less terrorism than democracies because they increase the costs of engaging in violence by making terrorism difficult and dangerous, whereas the openness of society in democratic states decreases those costs. [101]
Looking at both terrorism and communal conflict more generally, a final set of studies finds an inverted U-shaped relationship between democracy and domestic violence. According to this logic, both highly repressive states and highly democratic ones experience low levels of civil conflict. In the former case, the costs of engaging in violence are prohibitive; in the latter, other means exist whereby groups in society can affect political change. So-called “anocracies”—countries transitioning either toward democracy or authoritarianism—experience the worst of both worlds. They do not yet have the institutions and political channels for citizens to peacefully express their dissatisfaction with the political status quo; at the same time, they do not have or choose not to use the tools of repression to undercut terrorist group formation and violence a priori. Anocratic countries in the transition period between democracy and autocracy, countries exhibiting enduring semi-democracy and new democracies tend to suffer higher levels of civil conflict including terrorism.[102]
Religion and Variations in Terrorist Targeting
The connection, then, between democracy and terrorism is inconclusive. Why is the literature so mixed? A large reason is that the historical record itself points in both directions. Some long-standing democracies like those in Scandinavia and Canada have been relatively free of terrorism; others like India, Greece and Israel have suffered hundreds of attacks. In examining the relationship between democracy and terrorism, scholars have attempted to disaggregate different dimensions of democratic governance and their effect on terrorism, thus accounting for the variation. Such studies have looked at the importance of multi-party competition, [103] rule of law, [104] democratic participation, [105] different representation systems, [106] and regime strength.[107] Thus, both regime type and specific regime characteristics need to be taken into account when considering the structural determinants of terrorism.
While many studies on democracy and terrorism examine different components of democracy, most do not attempt to disaggregate terrorism with respect to ideology, motivations, or tactics in the same way. The majority of these studies tend to lump terrorist groups together without taking into account the guiding ideologies of different terrorist organizations. “Terrorism,” however, runs the risk of being an overly- aggregate dependent variable. Perhaps democracies/autocracies give rise to some manifestations of terrorism but not to others. Thus a disaggregated approach is more promising for understanding the structural conditions that encourage particular forms of terrorist violence, thus explaining some of the observed variation in the studies discussed above. It might, therefore, be more useful to classify terrorist incidents based on who the perpetrators are and their long-term objectives.
One possible way of distinguishing terrorist groups is on the basis of religion. Religious terrorists-those who prescribe for themselves religious identities and aims-are fundamentally different from their secular counterparts in important ways.[108] Religious terrorists look to their faith as a source of inspiration, legitimation and worldview, resulting in a totally different incentive structure than exists for their secular counterparts.[109] Accordingly, religious terrorist groups are also more lethal and long-lived than nonreligious organizations.[110] Such groups have been implicated in a rising number of suicide missions in recent years, while suicide attacks by secular groups have declined.[111] To be sure, religious terrorist organizations can pursue vastly different goals, ranging from apocalyptic notions to the establishment of a religious state in the here and now. Yet because religious militants often understand their endeavors as part of a larger-than-life spiritual struggle, the constraints that normally limit secular terrorist groups seem to have little bearing on groups and individuals who commit violence in God’s name.
It stands to reason, then, that the structural conditions that enable religious terrorists might not have the same effect on non-religious terrorists and vice versa. Religious terrorist groups, for example, may be willing to carry out attacks in the same conditions of pervasive authoritarianism that might otherwise discourage non-religious terrorists who are not motivated by transcendent concerns. Indeed, analyzing terrorist attacks by group ideology and regime type reveals a striking dissimilarity between religious and non-religious terrorist groups. Non-democracies are far more likely to birth religious terrorists, while democracies are more likely to experience attacks by groups motivated by non-religious concerns.
The charts below examine the average annual number of both religious and non-religious domestic terrorist attacks according to countries’ level of freedom. The freedom scores are taken from Freedom House, a widely used index to assess the democratic status of countries worldwide.[112] Coding of religious and nonreligious terrorist incidents was done by analyzing terrorist attacks that were included in the University of Maryland’s Global Terrorism Database from 1991-2012. Only attacks by groups that are driven by an explicit and professed religious ideology rooted in supernatural assumptions are considered “religious” attacks.[113] Focusing on beliefs and practices rooted in supernatural assumptions has the benefit of allowing for the differentiation of religious from secular ideologies and avoiding debates as to whether ideologies like Marxism or nationalism constitute religion. Another benefit is that it allows for the separation of groups driven by a professed religious ideology from groups that may coalesce around a common religious identity but do not have overtly religious goals or motivations as in the cases of the Tamil Tigers, the Irish Republican Army, and the Greek Orthodox EOKA.[114]
The charts reveal a marked difference in the countries most susceptible to religious or non-religious terrorist attacks. The first chart shows that 74 percent of religious attacks transpired in countries that were “not free” by Freedom House’s standards. 23 percent of attacks occurred in “partly free” countries.
Only 3 percent of attacks took place in liberal democracies. By contrast, only 10 percent of non-religious attacks took place in authoritarian, unfree countries. Two-thirds of these attacks occurred in partly-free countries. Yet nearly a quarter of attacks, 23 percent, transpired in liberal democracies. Simply put, religious terrorists appear not to be deterred by the same structural conditions that apparently deter their secular counterparts. Conversely, non-religious terrorists are far more likely to attack partly-free or free countries; 90 percent of these attacks occurred in moderately free or fully free countries.
These percentages show important differences in the logics of both kinds of terrorism. Even if repression generally raises the costs for engaging in terrorism, this rule does not seem to apply to terrorists motivated by religion. Put differently, the same structural context that makes terrorism a suboptimal tactic for political dissidents trying to secure concessions from their adversaries actually enables terrorism by those motivated by an ideology that downplays the strategic calculus of purely political rebel groups. Religious terrorists see value in engaging in violence in authoritarian settings, despite the risks of doing so. This does not mean that religious terrorists are irrational, but rather that they operate according to a different type of cost-benefit analysis than non-religious terrorists.
Religious Security and Terrorism
How can we account for these differences in the targeting preferences of religious and non-religious groups? One possibility is that religious terrorist attacks are concentrated in countries that have high levels of religiosity to begin with. While this might be true in certain cases, this rationale does not account for the fact that in a fair number of authoritarian countries plagued by religious terrorism, levels of religiosity are actually quite low as in China and Burma. Conversely, some highly religious countries like Ghana and Romania witness very few terrorist incidents. Another possibility is that religious terrorism occurs with higher frequency in authoritarian states because the majority of Islamic countries are authoritarian and most religious terrorist groups claim an Islamic mantle. This rationale falls short for three reasons. First, certain Islamic countries like Bangladesh and Pakistan are equally or more likely to experience non-religious forms of terrorism as they are to suffer from Islamist terrorism. Second, slightly more than one-third of Islamic countries actually experienced no terrorism during the timeframe being analyzed, and more than two-thirds witnessed fewer than 10 attacks. The evidence indicates that Islamic countries are not more likely to suffer from religious terrorism when compared to non-Muslim countries. Third, about the same number of Islamic countries are “free” as those that are “not free.” Like the rest of the world, most fall in the “partially free” category.
Insights derived from the sociological theory of post-materialism first developed in the 1970s can be useful in developing a theory for understanding why religious terrorism tends to occur in authoritarian settings, while non-religious terrorism occurs in largely democratic countries. University of Michigan Political Scientist Ronald Inglehart has long argued that rising levels of wealth free people from a fixation on materialistic values like economic or physical security, and allow them to emphasize a different set of values—“post- material” ones—that stress autonomy and self-expression.[115] Thus rising prosperity creates a perceived widespread sense of existential security, which gradually liberates those living in rich countries from occupation with basic materialistic needs, allowing them to pursue other goals such as belonging, esteem and intellectual satisfaction.[116] In contrast, in countries marked by abject poverty and the uncertainty of survival, individuals vulnerable to physical, societal and personal risks tend to be preoccupied with materialistic values (i.e., basic healthcare, access to clean water, etc.) because survival cannot be taken for granted as it can in prosperous countries.
The theory of post-materialism can be adapted to help understand variations in religious and secular terrorism across time and space. Just as Inglehart argued that survival values predominate when material sustenance and physical security are scarce, the tendency for religion to turn violent exists when religious security is in short supply. While the most obvious way in which religious security can become compromised involves government restrictions on religious practice in the forms of unfavorable laws, violent state suppression, or cooptation of religious institutions, religious insecurity can result from several other factors including domestic or international conflict, religiously-based social hostilities and persecution, bellicose religious doctrines, and so forth. For this reason, religious security is a much more expansive concept than conventional notions about religious freedom. When religion becomes embattled for any of these reasons, it serves to radicalize political theologies and give more credence to the narrative espoused by religious extremists that their faith is under attack, either by the state or society at large. Because legitimate institutional vehicles are not available to voice grievances, certain religious groups feel compelled to take matters into their own hands.
The key problem with respect to religiously insecure states is that they isolate and radicalize religious identity in society and increase the possibility that religious groups and individuals feel aggrieved enough to take up arms against a state or group that is perceived to be attacking that religious identity. For example, when governmental institutions act in a discriminatory manner and block channels for political and cultural engagement, they create conditions ripe for the development of bellicose political theologies where people of faith perceive their religious beliefs are being attacked and are in need of defense. [117] This dynamic can be seen in places like Algeria, Egypt, and China. Religious security can also become compromised at the society level. Inter-group hostilities rooted in religion often result in tit-for-tat retaliations by targeted groups, leading to violent conflict spirals. [118] In the western Rakhine state of Burma, communal violence, including widespread rioting and clashes, between Rohingya Muslims and Buddhists has resulted in thousands of deaths and hundreds of thousands of people being internally displaced. Finally, as seen most vividly in Iraq and Syria, civil wars and the collapse of the state often creates a power vacuum which is exploited by extremist groups which threaten the religious security of all who do not unswervingly abide by their radical ideology. These are just three examples of the myriad ways in which religious insecurity and violence are connected, and these conditions are far less likely to be present in liberal democracies.
Unlike in Inglehart’s argument, religious security does not come about through the generation of wealth, but rather by through respect for the rights of religious groups and individuals—a quality inherent in liberal democracies. When people of faith are free to believe whatever they want and practice their religion however they see fit, a transformation of individual values ensues. As countries transition toward greater religious tolerance and inclusivity, the subsequent strengthening of religious security reduces the necessity of violence on the part of religious adherents. No longer do individuals have to fight to earn basic religious rights; instead these rights are guaranteed and indeed taken for granted in highly secure countries. The full recognition of religious rights allows individuals to gradually shift their attention to non-religious goals.
In states that are religiously secure, religion does not cease to be an important value-just as Inglehart’s concept of existential security never stops being fundamental-but rather, concerns over religion are not overwhelmingly predominant, often leading to attention being given to other or new issues and the formation of cross-cutting cleavages in which religious and other forms of identity are given more equal weight. Prolonged periods of religious security encourage the spread of these non-religious concerns, while the declination of religious security has the opposite effect. People raised in times of religious security will turn their attention to “post-religious” concerns. These concerns permit an entirely different set of grievances to emerge that has little to do with religion-secular nationalism, environmentalism, animal rights activism, racial supremacism, etc.-for which terrorists may take up the gun.
Terrorism of this variety often occurs when groups believe they are too small or marginalized to work through the system or the state refuses to negotiate on issues of importance. Religious terrorism may well occur in religiously secure countries, but it tends to be intermittent and carried out by “lone wolf” militants. This logic might help us understand how a country like the United States can remain highly religious and multicultural, yet at the same time face few problems when it comes to religious violence.[119] This also means, though, that secular violence becomes more common in religiously secure states. In short, in religiously-secure countries, the religious and political rights of religious groups and individuals are basic, allowing for other kinds of cleavages to rise to importance. Because people of faith in these states can practice their faith as they see fit and work through democratic channels in order to achieve their political goals, the likelihood for religious violence is diminished because the right to religion is essentially unquestioned.
As the literature shows, religious terrorism has been on the rise over the past 30 years and especially after the attacks of September 11, 2001.[120] This can be attributed to two key factors. The first involves the global resurgence of religion in response to the perceived destruction of religious values by corrupt and self-serving secular political orders.[121] The religious resurgence has been exacerbated by forces like modernization and globalization. Yet this increase in religion’s prominence comes at the precise time that religion has come under unprecedented assault from governmental religious restrictions, communal hostilities involving religion, and religiously-based civil wars-the withering of religious security.[122] The confluence of these trends helps to both explain the rise of religiously-motivated terrorism and predict its continuation and intensification well into the future.
Conclusion
This article has made the case that religious terrorism tends to occur in authoritarian settings because faithbased terrorists are not as likely to be deterred by repression and such settings make religion a point of cohesion and contention. By contrast, in religiously secure places, people are less likely to take the claims of militants that their faith is under attack seriously and will be less willing to support or join religious terrorist organizations. People in these countries may, however, subscribe to a different militant narrative-a secular one-that supports the use of violence.
This study reinforces the notion that there is heterogeneity in terrorism, arguing that different structural contexts have the potential to breed different kinds of terrorist groups. The disaggregated approach used here cautions against making blanket judgments about the causes of “terrorism” in general, as much of the existing literature does. Contemporary terrorism has diverse roots, and this reality becomes even clearer when comparing the contexts that give rise to religious and non-religious forms of terrorism. This further means that making universal policy recommendations is difficult as the findings suggest that there is no single “silver bullet” for defeating terrorism. Approaches designed to combat secular terrorism need not necessarily apply to religious terrorism and vice versa.
Instead of adopting blanket approaches to terrorism, states would be best advised to take into account the specific nature of the threats they face. For example, this article suggests that if states struggling with religious terrorism take steps towards introducing a modicum of religious security, then this will have a mitigating effect on that particular form of terrorism, even though the threat of religious terrorism can never be completely eradicated. But the case has also been made that liberal democracies are far more likely to experience nonreligious forms of terrorism. Fortunately, though, it has been shown that dealing with non-religious terrorism is a more manageable task and can be handled through methods like policing and intelligence. These counterterrorism tactics, which tend to be ineffective against religious terrorism, often succeed when used against non-religious terrorist groups.
While this article has revealed marked divergences in terrorist targeting against certain kinds of regimes based on group ideology and while it offered a possible explanation for this finding, it has not attempted to robustly test this relationship or rule out alternative explanations. Future research, therefore, can expand upon the arguments put forward in this article in two ways. First, statistical analysis should be used to examine the robustness of the relationship between religious insecurity and violence, while accounting for other variables that may have an effect on variations on terrorist targeting. Second, case studies at both the country and group level would provide increased leverage in determining how and why violence arises.
About the Author: Dr. Nilay Saiya is Assistant Professor of Political Science and Director of International Studies at the State University of New York, Brockport. His research interests include the study of religion and global politics, American foreign policy, and terrorism. He earned his Ph.D. from the University of Notre Dame in 2013.
20 Years Later: A Look Back at the Unabomber Manifesto
by Brett A. Barnett
Abstract
On September 19, 1995, The New York Times and The Washington Post submitted to “Unabomber” Theodore Kaczynski’s demand to publish his manifesto, a treatise that would come to be known as the “Unabomber Manifesto.” While Kaczynski has been serving a life sentence for the letter-bombing campaign that he perpetrated between 1979 and 1995, the radical environmentalist rhetoric contained within his manifesto has become available to an even wider audience of current and would-be environmental extremists than when it was first published. Given its availability online, the Unabomber Manifesto has become one of the most well-known rhetorical artifacts endorsing environmental extremism. Using Herbert Simons’ “rhetorical requirements” approach, this study demonstrates that the Unabomber Manifesto represents Kaczynski’s rhetorical efforts to animate like-minded environmental extremists. The article concludes by discussing how the Unabomber Manifesto resonated with some radical environmentalists and may have even served as a catalyst for later acts committed by U.S.-based environmental extremists. By utilizing a framework for examining the rhetoric of violent revolutionary social movements, this study provides further insight into what motivates environmental extremists of today.
Keywords: Unabomber Manifesto; eco-terrorism; environmental extremists; radical environmentalists; rhetorical analysis
Introduction
Between 1979 and 1995, Theodore “Ted” Kaczynski perpetrated a letter-bombing campaign that took the lives of three individuals and seriously injured 23 others.[123] Nicknamed the “Unabomber” by the FBI because his early bombing victims were connected to universities or airlines[124], Kaczynski eluded authorities for almost 18 years.[125] During his crime spree, Kaczynski sent letter bombs to various computer scientists, industry leaders, and other individuals whom he believed promoted technology to the detriment of the natural environment in the United States. Feeling that his murderous rampage had failed to sufficiently heighten the public’s awareness of the negative consequences of technology, in June of 1995, Kaczynski demanded that The New York Times and The Washington Post publish “Industrial Society and Its Future.”[126] Indeed, Kaczynski threatened to continue his killing spree if the Times and the Post refused to publish his 34,390-word, 56-page typewritten manifesto, a treatise in which he articulated his anti-technology, proenvironment worldview.[127]
On September 19, 1995, both papers submitted to Kaczynski’s demands and ran 3,000-word excerpts from the treatise[128], now better known as the “Unabomber Manifesto.” While publication of the manifesto garnered the Unabomber national headlines, it was also Kaczynski’s undoing. After reading the manifesto, a social worker from Schenectady, New York, noticed remarkable similarities in the language use and writing style of the Unabomber to those of his brother, Theodore Kaczynski, and notified authorities.[129] On April 3, 1996, FBI officials arrested Kaczynski at his cabin in Montana, effectively ending the Unabomber’s campaign of eco-terrorism.[130] As part of a plea bargain, Kaczynski was sentenced to life in prison without the possibility of parole.[131] However, Kaczynski’s imprisonment did not serve to silence his anti-technology, pro-environment message. Given its availability online, Kaczynski’s radical environmentalist rhetoric has become available to an even wider audience than when it was first published. Moreover, certain elements of the Unabomber Manifesto, a rhetorical artifact endorsing the destruction of the man-made world and the promotion of the natural environment, are reflected in the ideology and actions of many of today’s environmental extremists.
Given the covert and autonomous manner in which he perpetrated his eco-terrorism campaign, Kaczynski was the ultimate embodiment of a lone wolf environmental extremist. In discussing individuals who operate independently of a larger organizational structure, “lone wolf” describes an individual perpetrator, “lone wolves” describes a group of two or more perpetrators, and “lone wolfing” describes the acts committed by these perpetrators. Other terms commonly used by researchers and law enforcement for “lone wolf,” “lone wolves,” and “lone wolfing,” are “leaderless resistor,” “leaderless resistors,” and “leaderless resistance,” respectively. A concept developed and popularized by White supremacist Louis Beam in the hope of stimulating numerous acts of violence from far right extremists, leaderless resistance is an oppositional strategy allowing for, and encouraging, individuals, or small “cells” of lone actors, to perpetrate acts of violence independently of any leadership hierarchy or support network.[132] However, since its conception, leaderless resistance has also been embraced by individuals adhering to various ideologies (e.g. antigovernment, anti-abortion, animal liberation), including radical environmentalism. Similar to Louis Beam’s attempts to stimulate acts of violence from White supremacists, the Unabomber Manifesto represents Kaczynski’s attempt to animate like-minded environmental extremists.
Utilizing a framework for examining the rhetoric of violent revolutionary social movements, this study examines the rhetoric contained in the Unabomber Manifesto and demonstrates that the manifesto represents Kaczynski’s rhetorical efforts to animate like-minded environmental extremists. The essay demonstrates how Kaczynski rhetorically navigated the wide range of competing worldviews that exist within the larger radical environmentalist movement. The essay concludes by discussing how Kaczynski’s manifesto resonated with some radical environmentalists and may have even served as a catalyst for later acts committed by U.S.-based environmental extremists.
Rhetorical Analysis
The full text of the Unabomber Manifesto with the original section titles (see Appendix) and numbering scheme was retrieved from The Washington Post website.[133] The author’s examination of the manifesto is instructed by Herbert Simons’ “rhetorical requirements” approach which appears in his oft-cited essay, “Requirements, Problems, and Strategies: A Theory of Persuasion for Social Movements.”[134] Simons’ “rhetorical requirements” approach provides a useful framework for examining the rhetoric of violent revolutionary social movements, the sort of movement Kaczynski advocated in his manifesto and the sort embraced by like-minded environmental extremists. Simons argues that social movements, just like more formal entities such as political parties and governments, must fulfill functional requirements.
Simons further explains that the functional needs of a movement create “rhetorical requirements” for the movement’s leaders. Simons identifies three rhetorical requirements that leaders of social movements must fulfill: (1) attracting, maintaining, and molding followers into an efficiently organized unit; (2) securing adoption of their ideology by the larger structure (i.e. the established order); and (3) reacting to resistance generated by the larger structure. Simons also points out that inherent conflicts among these requirements result in “rhetorical problems” that must be resolved strategically. He describes these rhetorical strategies as ranging along a continuum from moderate to intermediate to militant, each with its own suitable styles and tactics.
Given Kaczynski’s anti-collectivist sentiment and his history of lone wolfing, it is doubtful that Kaczynski was intentionally seeking to lead a large social movement when he drafted his treatise; it is more plausible that Kaczynski was hoping to animate like-minded environmental extremists. But, regardless of Kaczynski’s intentions, he nevertheless fulfilled the rhetorical requirements of a movement leader when his antitechnology, pro-environment treatise was published. In using Simons’ framework to examine the Unabomber Manifesto, the author demonstrates how Kaczynski attempted to animate like-minded environmental extremists and, consequently, why it is conceivable that like-minded environmental extremists might have been, or could still be, energized by his rhetoric. The author’s analysis shows how Kaczynski fulfilled the rhetorical requirements that were created by the functional needs of a radical environmentalist movement, the problems he faced, and the strategies he adopted to solve these dilemmas.
Attracting, Maintaining, and Molding Followers
Kaczynski was of the opinion that technology and nature were dichotomous, with technological development representing a social ill and environmental preservation representing the cure. This point is exemplified by the following statement Kaczynski made in the manifesto:
“Nature makes a perfect counter-ideal to technology for several reasons. Nature (that which is outside the power of the system) is the opposite of technology (which seeks to expand indefinitely the power of the system). Most people will agree that nature is beautiful; certainly it has tremendous popular appeal. The radical environmentalists ALREADY hold an ideology that exalts nature and opposes technology To relieve the pressure on nature it is not necessary to create a special kind of social
system, it is only necessary to get rid of industrial society........... It will relieve the worst of the pressure
on nature so that the scars can begin to heal.”[135]
Thus, for Kaczynski, open opposition to technology was as beneficial to the preservation of the environment as environmentalism itself. What is more, these statements reveal that Kaczynski’s goal in drafting the manifesto was not to create an anti-technology, pro-environment movement, but rather to energize likeminded individuals from within the larger radical environmentalist movement.
Like Simons, Kaczynski realized that the survival and effectiveness of any movement is dependent on followers. Throughout his manifesto, Kaczynski made extensive use of both emotional and rational appeals. In an obvious attempt to garner support for his radical environmentalist agenda, Kaczynski made issue- oriented appeals that he knew would likely strike an emotional chord with readers, such as fears about the loss of basic freedoms and the well-being of future generations, particularly their own children. On the issue of freedom, Kaczynski discussed how technological development was increasingly forcing people to function “as parts of an immense social machine” [136] that resulted in a loss of individual autonomy and basic freedoms, including privacy and speech rights. The importance that Kaczynski placed on “autonomy” and being “autonomous” was apparent; at several points within his treatise, he capitalized the words.[137]
To support claims regarding the loss of personal autonomy and freedoms, Kaczynski offered a variety of evidence that had become all too familiar to Americans by 1995: (1) the prevalence of hidden cameras and other surveillance techniques in society, (2) the ease of access to personal information contained in computer data banks, (3) the conglomeration of media resulting in fewer speech opportunities, and (4) the concentration of corporations into fewer and fewer hands resulting in less choice for consumers. Clearly, Kaczynski’s strategy was to begin with a series of emotional appeals, playing to fears and concerns that he believed readers held, then try to substantiate those emotions with a series of rational appeals, offering verifiable evidence of the seemingly negative effects that technology had imposed on society.
Kaczynski used a similar approach when discussing the well-being of future generations. Commenting on the effects that technology would have on humans, he wrote, “The Industrial Revolution and its consequences have been a disaster for the human race”[138] and “threats to the modern individual tend to be MAN- MADE.”[139] To support such assertions, Kaczynski once again offered a variety of verifiable evidence, such as “ozone depletion,” “greenhouse effect,” and “nuclear proliferation.”[140]
In an apparent attempt to create a sense of shared identity between himself and other like-minded environmental extremists, Kaczynski made frequent use of the terms “we,” “us,” and “our” when referring to individuals who opposed technology and the environmental devastation it caused.[141] Alternatively, Kaczynski frequently used the term “they” when referring to persons with an opposite worldview in which technology is embraced. When referring to adherents to his radical environmentalist agenda, Kaczynski also frequently used “FC,” letters which authorities would later learn were an acronym for “Freedom Club.”[142] At one point, Kaczynski even suggested that adherents to his radical environmentalist ideology were more intelligent than non-adherents, a further attempt to create a sense of shared identity in “us-versus-them” terms.
In an effort to organize FC into an efficient unit, Kaczynski first established what form of action he believed the movement needed to embrace. Early in the manifesto Kaczynski wrote, “We . . . advocate a revolution against the industrial system.”[143] Kaczynski did not view technological reform as a possibility; he viewed revolution as the only alternative. What is more, Kaczynski contended that the longer this revolution was delayed “the more disastrous the results.”[144] Thus, Kaczynski attempted to instill a sense of urgency in those readers who may have lent credence to his revolutionary rhetoric.
In a further effort to define FC’s agenda, Kaczynski wrote, “we do outline in a very general way the measures that those who hate the industrial system should take in order to prepare the way for a revolution against that form of society.”[145] Kaczynski also established that FC’s goal was “not to be a POLITICAL revolution,” that its objective was “to overthrow not governments but the economic and technological basis of the present society.”[146] However, Kaczynski was not opposed to insurrection against governments, per se; Kaczynski did endorse a decision to target governments to the extent that those governments supported the “industrial- technological system.”[147]
Securing Adoption of the Ideology by the Larger Structure
Simons points out that the “product of any movement is its ideology, particularly its program for change,” and the revolutionary rhetorician will insist that a significant renewal of values by the larger structure is necessary to provide harmony and stability.[148] In his manifesto, Kaczynski provided like-minded environmental extremists with a strategy for securing adoption of FC’s radical environmentalist ideology by the larger structure. Perhaps the most important strategy Kaczynski developed for FC is revealed in the following statement:
“[T]wo tasks confront those who hate the servitude to which the industrial system is reducing the human race. First, we must work to heighten the social stresses within the system so as to increase the likelihood that it will break down or be weakened sufficiently so that a revolution against it becomes possible. Second, it is necessary to develop and propagate an ideology that opposes technology and the industrial society if and when the system becomes sufficiently weakened.”[149]
Kaczynski believed continual attacks on the industrial-technological system were vital for an environmental revolution. Assuming a radical environmentalist movement was successful in the initial task of sufficiently weakening the industrial-technological system, the success of the revolution would then only hinge on the movement’s ability to propagate an anti-technology, pro-environment ideology that might be adopted by the larger structure.
In discussing how FC should go about getting others to accept its worldview, Kaczynski wrote, “an ideology, in order to gain enthusiastic support . . . must be FOR something as well as AGAINST something. The positive ideal we propose is Nature.”[150] Kaczynski later stated, “the ideology should be propagated in a simplified form that will enable the unthinking majority to see the conflict of technology vs. nature in unambiguous terms.”[151] Thus, Kaczynski indicated that FC’s ability to articulate its ideology with complete clarity was essential for securing adoption of its radical environmentalist ideology by the larger structure.
Kaczynski also discussed what sort of adherents he believed FC should focus attention on while spreading its radical ideology, when he wrote:
“The revolutionary ideology should therefore be developed on two levels.......... the ideology should
address itself to people who are intelligent, thoughtful and rational. The object should be to create a core of people who will be opposed to the industrial system on a rational, thought-out basis, with full appreciation of the problems and ambiguities involved, and of the price that has to be paid for getting rid of the system.”[152]
Next, Kaczynski suggested that the effectiveness of FC’s efforts to secure adoption of its radical environmentalist ideology by the larger structure should not be measured strictly in terms of how many people were motivated to act out in support of its cause. While FC’s ability to advance its revolution ultimately hinged on compelling at least some individuals to commit physical acts, Kaczynski conceded that the majority of people only needed to be aware of its radial environmentalist ideology. Following from earlier statements, Kaczynski wrote:
“Until the time comes for the final push toward revolution . . . the task of revolutionaries will be less to win the shallow support of the majority than to build a small core of deeply committed people. As for the majority, it will be enough to make them aware of the existence of the new ideology and remind them of it frequently . . .”[153]
Thus, Kaczynski believed that FC would be more effective in securing adoption of its radical ideology by the larger structure by simply spreading its message to a majority of people. Of course, Kaczynski’s demands for the Times and the Post to publish his manifesto represented his own efforts to spread a radical environmentalist message to the general public, a goal he achieved quite successfully when considering the readership of the two papers and the widespread online availability of the treatise.[154]
Reacting to Resistance from the Larger Structure
Simons points out that the larger structure may respond to a movement in one of two ways. On one hand, the larger structure may be “too kind” to a movement by appointing an entity to “investigate the issue,” disarming the movement by accurately predicting its demands and acting on some of them, or some other seemingly positive response that produces little, if any, progress for the movement.[155] On the other hand, the larger structure may be too restrictive to a movement by, among other tactics, refusing to negotiate with the movement or carry its message in the mass media.[156] Believing that the larger structure would be too restrictive in its response to FC’s radical environmentalist efforts, Kaczynski drafted his treatise accordingly.
Kaczynski suggested, both implicitly and explicitly, that like-minded environmental extremists should react violently to any potential resistance from the larger structure. Implicit in Kaczynski’s writings is that FC should react to any potential resistance from the larger structure with enough violence to weaken the industrial-technological system, a strategy repeatedly referenced in the manifesto. Within his treatise, Kaczynski discussed “FC’s violent methods” and the history of violence in the United States and abroad. In many instances, Kaczynski suggested that violence was a justifiable response to oppressive conditions imposed by power-elites. For example, in discussing a fictional power struggle between a “weak” and a “strong” member of society, Kaczynski wrote, “The only sensible alternative for the weaker man is to kill the strong one while he has the chance. In the same way, while the industrial system is sick we must destroy it.”[157] Although he speculated that FC “may or may not make use of violence,”[158] Kaczynski believed that violent tactics were ultimately the most effective means to its success when opposed by the larger structure.
In other instances, Kaczynski explicitly stated this. For example, Kaczynski made explicit his belief that violence was more effective than non-violence when he wrote, “If we had never done anything violent and had submitted the present writings to a publisher, they probably would not have been accepted.”[159] In fact, Kaczynski went so far as to state that murder was an acceptable response to resistance by the larger structure when he later stated, “In order to get our message before the public with some chance of making a lasting impression, we’ve had to kill people.”[160] Of course, this is exactly what Kaczynski did during his bombing campaign, and why the Times and the Post gave in to his demands to publish his manifesto. After all, both papers, as well as other elements of the larger structure (e.g. law enforcement), were keenly aware that resistance to the Unabomber’s demands to publish his radical environmentalist ideology were likely to be met with more violence. What is more, the very publication of the Unabomber Manifesto in the Times and the Post demonstrated how effective the use of violence would be in getting a radical environmentalist message publicized to a mass audience.
“Rhetorical Problems” and “Rhetorical Strategies”
Simons points out that while the social movement leader needs to fulfill all three rhetorical requirements, inherent conflicts frequently exist among those requirements, creating “rhetorical problems” that need to be resolved by the leader.[161] Inherent conflicts among Kaczynski’s rhetorical requirements resulted in two “rhetorical problems” that complicated his attempts to guide FC’s radical environmentalist efforts: (1) how the movement was supposed to spread its message to a mass audience without using the very technologies the movement opposes and (2) how the movement was to avoid alienating the mass of potential followers who utilized the technologies the movement sought to eliminate.
Kaczynski made direct reference to the first inherent conflict when he wrote, “they [revolutionaries] will be tempted to use technology as a tool for reaching that other goal. If they give in to that temptation, they will fall right back into the technological trap.”[162] At the same time, however, Kaczynski realized that like-minded environmental extremists needed to use some technologies if they hoped to disseminate their message to a wide audience. Kaczynski attempted to resolve this inherent conflict when he later wrote:
“It would be hopeless for revolutionaries to try to attack the system without using SOME modern technology. If nothing else they must use the communications media to spread their message. But they should use modern technology for only ONE purpose: to attack the technological system.”[163]
Kaczynski’s resolution of this conflict was relatively simple. He indicated that technology use was a necessary evil that, if limited to the single purpose of harming the technological system, must be permitted if the radical environmentalist movement hoped to spread its message to a mass audience.
With regard to how FC was to avoid alienating prospective adherents who utilized the technologies the movement sought to eliminate, Kaczynski attempted to resolve it strategically by suggesting that the movement should focus its efforts only on those in control of the technology:
“As a matter of strategy one should generally avoid blaming the public.......... other conflicts tend to
distract attention from the important conflicts (between power-elite and ordinary people, between technology and nature) . . . Generally speaking, one should encourage only those social conflicts that can be fitted into the framework of the conflicts of power-elite vs. ordinary people, technology vs. nature.”[164]
Kaczynski suggested that FC should not direct its aggression toward ordinary citizens who used technology because that approach would have been counterproductive to the movement’s objectives. In Kaczynski’s view, FC would be more effectively served by stopping technological development at its “power-elite” source and allowing society to see the benefits created by a technology-free environment, rather than by attempting to convince “ordinary” people to do away with their technologies.
Simons points out that individuals seeking to lead social movements often find themselves having to navigate through an intricate web of conflicting rhetorical demands that must be resolved strategically.[165] The movement leader may employ a moderate, intermediate, or militant type of strategy.[166] The strategy of the moderate is one of peaceful persuasion, whereas the strategy of the militant is to use rhetoric as an expression, a tool, and an act of force.[167] Although his general rhetorical style was more militant, Kaczynski adopted an intermediate strategy that combined moderate and militant messages when faced with rhetorical dilemmas involving technology.
Individuals unaware of the conflicting demands imposed on movement leaders may well perceive the adoption of an intermediate rhetorical strategy by a person attempting to lead a radical environmentalist movement as oxymoronic, especially when considering the violence that Kaczynski perpetrated during his eco-terrorist bombing campaign. However, as Simons points out, contemporary social movements, when viewed broadly, all seem to require combinations of moderate and militant rhetorical strategies.[168]
Conclusion
In adopting an intermediate rhetorical strategy, Kaczynski’s rhetoric resonates with a wider universe of radical environmentalists. Bridging the myriad of ideological divides existing within the radical environmentalist movement has been a principal rhetorical problem facing the movement’s leaders. Given that Kaczynski managed to bridge this divide, if only partially, it certainly warrants examination. Using Herbert Simons’ “rhetorical requirements” approach for examining the rhetoric of violently revolutionary social movements, the author demonstrated how the Unabomber Manifesto represented a rhetorical effort by Ted Kaczynski to animate like-minded environmental extremists he referred to as FC, an acronym for Freedom Club. The examination demonstrated that Kaczynski fulfilled Simons’ three rhetorical requirements for social movement leaders by (1) attempting to attract/maintain/mold FC into an efficiently organized unit (e.g. emotional and logical appeals, sense of urgency, sense of shared identity, the revolutionary form of action needed); (2) instructing FC on how to secure adoption of their ideology by the larger structure (e.g. continual attacks on the industrial-technological system, a “for-and-against” ideology propagated in a simplified form); and (3) suggesting to FC that it should react violently to resistance generated by the larger structure. The examination also revealed how Kaczynski attempted to strategically resolve “rhetorical problems” that were created by these rhetorical requirements by adopting an intermediate strategy that combined moderate and militant messages.
Kaczynski’s manifesto clearly represented his rhetorical efforts to animate like-minded environmental extremists. Believing that he was in allegiance with other radical environmentalists, Kaczynski sought not only to fortify their convictions but also to guide their actions through his manifesto. Kaczynski’s rhetorical efforts were consistent with some of his earlier writings. Prior to his demands that the Times and the Post publish his manifesto, Kaczynski drafted letters to Earth First! and other radical environmentalist groups regarding his strategy for destroying the industrial-technological system.[169] During a search of Kaczynski’s cabin following his arrest, FBI investigators discovered carbon copies of letters Kaczynski had written to Earth First! in an overt attempt to enlist the group as an ally.[170] One of the letters discovered was entitled “Suggestions for Earth Firsters! from FC.”[171] Also, investigation revealed that Kaczynski drew upon radical environmentalist literature during his bombing campaign, even using it to select two of his victims.[172] This discovery as well as Kaczynski’s efforts to communicate with Earth First! indicate that the group’s radical environmentalist rhetoric struck a responsive chord with him.
Just as the rhetoric of Earth First! resonates with various radical environmentalists, including a lone wolf like Kaczynski, the rhetoric in Kaczynski’s manifesto has also resonated with various radical environmentalists. Because Kaczynski referenced ideals common to the larger radical environmentalist movement and utilized an intermediate rhetorical strategy, his manifesto likely resonated with a wider universe of radical environmentalists. Indeed, there is some evidence to support that Kaczynski’s revolutionary rhetoric resonated with environmental extremists in the United States.
Despite his deadly tactics, Kaczynski had, and perhaps still has, a number of sympathizers within the radical environmentalist movement.[173] In 1997, the year following Kaczynski’s apprehension, an anonymously- produced flyer reading “Free Ted Kaczynski” was distributed at the Earth First! Rendezvous by a long-term radical environmentalist movement participant.[174] The back side of the flyer read, in part, “It may be that the Unabomber will be looked upon ... as a kind of warrior-prophet ... Return to Wild Nature - Destroy the Worldwide Industrial System.”[175]
Some individuals within the radical environmentalist movement have even employed tactics that resemble those endorsed by Kaczynski in his manifesto. For example, after comparing Kaczynski’s revolutionary rhetoric with subsequent eco-terrorist acts committed by individuals linked with the Earth Liberation Front (ELF), several parallels exist. To begin, Kaczynski’s militant, pro-environment rhetoric is reflected in the violent eco-terrorist attacks committed by ELF cells in the United States. The year following the manifesto’s publication, ELF cells committed various large-scale acts of eco-terrorism, including multiple arsons and a variety of other destructive attacks against property, facilities, and housing developments.[176] What is more, the persistence of the eco-terrorist attacks perpetrated by individuals linked with the ELF is reflective of Kaczynski’s assertion that a radical environmentalist movement must wage continual attacks against the industrial-technological system in order to achieve its environmental objectives.
The views that Kaczynski espoused in his manifesto are also reflected in some targets of eco-terrorism perpetrated by ELF cells in the United States. Mirroring Kaczynski’s call to violence, ELF cells have committed attacks on construction sites, luxury retreats, developments in rural areas, facilities used for genetically engineering trees and crops, as well as equipment and/or properties used by a variety of corporations and government agencies that the group perceives to be environmentally-unfriendly. Moreover, the tactic of attacking large, costly facilities, including the upscale residences of individuals deemed to be assisting in environmental degradation, parallels Kaczynski’s strategy of perpetrating violence against powerelites, the entities he argued were most capable of supporting wide-scale environmentally-harmful activities.
Additionally, the guidelines Kaczynski established for propagating an ideology are reflected in how some ELF cells and sympathizers propagate radical environmentalist ideology. In some instances, ELF cells have attempted to propagate their ideology through the use of an unambiguous slogan (i.e. “If you build it, we will burn it.”), an approach that echoes Kaczynski’s recommendation that environmental extremists should propagate their ideology in a simplified form. ELF sympathizers have also attempted to spread a radical environmentalist message to a wider audience through the media of mass communication, particularly the Internet, an approach Kaczynski endorsed with the provision that it was done with the exclusive aim of harming the technological system.
In examining the rhetorical nature of the Unabomber Manifesto, the present article provides further insight into what motivates environmental extremists of today, and perhaps this study serves to assist society in guarding against future acts of eco-terrorism. Given its availability online, the radical environmentalist rhetoric contained within Kaczynski’s manifesto has become available to an even wider audience than when it was first published. If the manifesto’s anti-technology, pro-environment rhetoric resonated with environmental extremists in the past, like-minded individuals may view the essay as a guide for their eco-terrorist activities in the future. Future studies should examine the role that other rhetorical artifacts, especially those employing intermediate rhetorical strategies, may play in bringing radical environmentalists from various ideological perspectives together for a common cause. With environmental extremists and a host of other deeply committed issue-oriented extremists (e.g. anti-abortion, anti-globalization) actively operating in the United States and abroad, examinations of the rhetorical nature of extremist rhetoric are needed now more than ever.
About the Author: Brett A. Barnett is Associate Professor of Communication at Slippery Rock University of Pennsylvania. He examines the rhetoric of hate groups and other extremists. He is the author of “Untangling The Web Of Hate: Are Online ‘Hate Sites’ Deserving Of First Amendment Protection?”
Appendix: Sections of Theodore Kaczynski’s “Industrial Society and its Future”
1. “Introduction”
2. “The Psychology Of Modern Leftism”
3. “Feelings Of Inferiority”
4. “Oversocialization”
5. “The Power Process”
6. “Surrogate Activities”
7. “Autonomy”
8. “Sources Of Social Problems”
9. “Disruption Of The Power Process In Modern Society”
10. “How Some People Adjust”
11. “The Motives Of Scientists”
12. “The Nature Of Freedom”
13. “Some Principles Of History”
14. “Industrial-Technological Society Cannot Be Reformed”
15. “Restriction of Freedom Is Unavoidable In Industrial Society”
16. “The ‘Bad’ Parts Of Technology Cannot Be Separated From The ‘Good’ Parts”
17. “Technology Is A More Powerful Social Force Than The Aspiration for Freedom”
18. “Simpler Social Problems Have Proved Intractable”
19. “Revolution Is Easier Than Reform”
20. “Control Of Human Behavior”
21. “Human Race At A Crossroads”
22. “Human Suffering”
23. “The Future”
24. “Strategy”
25. “Two Kinds Of Technology”
26. “The Danger Of Leftism”
27. “Final Note”
28. “Notes”
II. Research Notes
Re-Examining the Involvement of Converts in Islamist Terrorism: A Comparison of the U.S. and U.K.
by Sam Mullins
Abstract
This article explores the role of converts in the ‘Global Salafi Jihad’ based on a sample of 75 American and 47 British converts who became involved in Islamist terrorism between 1980 and September 11th, 2013. Converts are compared to non-coverts on a variety of demographic, operational and investigative variables, and each sample is further divided into those who mobilized before and after 9/11 in order to allow assessment of changes over time. Contrary to previous research, results show that American converts in particular constitute a “jihadi underclass” that is markedly disadvantaged compared to the rest of the U.S. sample. They also present a generally less capable terrorism threat and are especially likely to be caught in sting operations. British converts, whilst also clearly disadvantaged and less capable, are much less distinct compared to non-converts in the U.K. Practical and theoretical implications of these findings are discussed.
Keywords: Islamist; terrorism; jihad; converts; United States; United Kingdom.
Introduction
From Richard Reid to Omar Hammami, the involvement of converts in Islamist terrorism has been a subject of much interest, yet there has been relatively little in the way of systematic research. A notable exception to this is the work of Robin Simcox and Emily Dyer, who found that American converts “were likely U.S.-born young men with a good education who had since found regular work” and were on a similar socioeconomic footing to the rest of their sample.[177] Utilizing a somewhat broader sampling frame, this paper re-examines the involvement of American converts in Islamist terrorism and compares them to British converts whilst also taking into account changes over time. Although there are broad similarities between the two bodies of research, the conclusion here is that American converts in particular constitute a highly marginalized “jihadi underclass” which is markedly worse off than the rest of the sample. This suggests a rather different reality than Simcox and Dyer depict, thus raising important questions about how and why converts are drawn to Islamist terrorist activity in the U.S. and what this means for counter-terrorism (CT). This is a critical issue in light of the recent increase in Islamist terrorist activity, combined with the fact that that converts make up for a significant percentage of such cases in the U.S.
Methodology
The Simcox and Dyer study included a total of 171 people (among them 40 converts) who were convicted of al-Qaeda related offences (AQROs) or were killed in suicide attacks within the U.S. between 1997 and 2011. The analysis presented here is based upon a U.S. sample of 365 individuals (75 converts, i.e. 21%) and a U.K. sample of 427 (including 47 converts, i.e. 11%) who mobilized in support of the al-Qaeda-led “Global Salafi Jihad” (GSJ) between 1980 and September 11th 2013 (see Appendices 1 and 2).[178] This included anyone from, living, or offending in the U.S. and U.K who:
-
Was convicted of a relevant offence (whether under terrorism legislation or otherwise);
-
Was killed during the course of terrorist activities, either at home and abroad;
-
Was facing legal allegations at the time the analysis was conducted;
-
Was subject to administrative or other sanctions in the absence of a conviction (detention,
deportation, financial asset freezing and British control orders);
-
Openly admitted their involvement in the GSJ, for example by way of appearing in a jihadi propaganda video;
-
Was publicly alleged to have been involved in GSJ-related terrorism but had not been subject to any legal action (including, for example, numerous individuals from Minnesota who are believed to have joined al-Shabaab).
In addition, each sample was divided into those who mobilized before and after 9/11 in order to evaluate changes over time.[179] Finally, while Simcox and Dyer examined 11 variables (7 relating to demographic backgrounds and 4 to operational behavior), the analysis here covers 14 (8 demographic, 5 operational and 1 relating to investigations).
Findings
The findings for demographic, operational and investigative variables before and after 9/11 are summarized in Tables 1 and 2 below. In the ensuing discussion of results, American converts vs. non-converts are compared first, followed by the equivalent comparison for the British sample.[180]
Table 1. Converts vs. non-converts involved in Islamist terrorism in the U.S. who mobilized before and after 9/11 (1980-September 11th 2013).[181]
| U.S. Pre-9/11 | U.S. Post-9/11 | |||
|
Converts 25n |
Non-converts 118n |
Converts 5 In |
Non-converts 172n |
|
| Criminal record | 24% | 11% | 57% | 20% |
| Mental health issues | 4% | 3% | 25% | 8% |
| Unemployed | 12% | 4% | 27% | 4% |
| Skilled occupation | 4% | 19% | 4% | 10% |
| Did not finish high school | 4% | 0 | 25% | 7% |
| University qualified | 28% | 23% | 10% | 17% |
| Female | 4% | 2% | 8% | 8% |
| Age | 27 | 27.8 | 27.7 | 28.1 |
| Foreign born | 8% | 76% | 16% | 71% |
| US born | 84% | 13% | 82% | 25% |
| US citizen/resident | 100% | 57% | 98% | 78% |
| Links to FTs | 68% | 78% | 22% | 46% |
| Training only | 20% | 23% | 2% | 9% |
| Jihadi fighting | 40% | 19% | 12% | 12% |
| Planning attack | 16% | 15% | 44% | 23% |
| Lone-actor | 0 | 2% | 16% | 8% |
| Undercovers used | 36% | 25% | 60% | 45% |
*FTs refers to foreign terrorists.
Table 2. Converts vs. non-converts involved in Islamist terrorism in the U.K. who mobilized before and after 9/11 (1980-September 11th 2013).
| U.K. Pre-9/11 | U.K. Post-9/11 | |||
|
Converts 13n |
Non-Converts 126n |
Converts 34n |
Non-converts 254n |
|
| Criminal record | 46% | 29% | 29% | 17% |
| Mental health issues | 8% | 7% | 9% | 6% |
| Unemployed | 8% | 14% | 31% | 16% |
| Skilled occupation | 0 | 8% | 3% | 3% |
| Did not finish high school | 0 | 3% | 3% | 1% |
| University qualified | 23% | 17% | 3% | 11% |
| Female | 0 | 0 | 9% | 4% |
| Age | 24.8 | 28 | 26.3 | 25.6 |
| Foreign born | 23% | 17% | 34% | 40% |
| UK born | 23% | 17% | 43% | 34% |
| UK citizen/resident | 69% | 56% | 83% | 74% |
| Links to FTs | 92% | 90% | 31% | 38% |
| Training only | 26% | 29% | 6% | 16% |
| Jihadi fighting | 46% | 20% | 0 | 10% |
| Planning attack | 23% | 26% | 20% | 23% |
| Lone-actor | 0 | 2% | 14% | 7% |
| Undercovers used | 0 | 0 | 14% | 5% |
*FTs refers to foreign terrorists.
Demographic Variables
More than 90% of all individuals in both the American and British samples, before and after 9/11 were male. Although the number of females becoming involved has increased over time, there is no obvious difference between converts and non-converts, or between the U.S. and U.K. While Simcox and Dyer found that American converts were significantly older than non-converts, this result was not replicated here and the average age in all groups was in the mid to late 20s. Nevertheless, in accordance with the previous study, American converts were found to be much more likely than non-converts to be born in the U.S. (more than 80% compared to 13% of non-converts before 9/11 and 25% after 9/11). Similarly, U.S. converts were more likely to be American citizens or permanent residents (almost 100% vs. 57% of non-converts in the pre-9/11 sample and 78% afterwards). By comparison, these differences were far less pronounced in the U.K. where, for example, 83% of converts were British citizens/permanent residents compared to 74% of non-converts after 9/11.
The remaining findings in relation to demographic variables are much more revealing. Simcox and Dyer found that overall, American converts did not differ greatly from non-converts in terms of education, although they were more likely to have obtained a college degree (20% vs. 8%). They further found that converts were more likely to be employed and in particular to be in skilled occupations (35% vs. 15%). In the present study, the figures are rather different. Among those who mobilized before 9/11, 28% of American converts had obtained a degree, compared to 23% of non-converts, yet they were more likely to be unemployed (12% vs. 4%) and less likely to be in skilled occupations (4% vs. 19%). During the same period, British converts did not appear to differ significantly from either the rest of the British sample or from American converts.
After 9/11, however, there are some quite dramatic differences. Just 10% of American converts had obtained a degree, compared to 17% of the rest of the U.S. sample. In addition, 25% of American converts had failed to complete high school, compared to just 7% of non-converts. They were also less likely to be in skilled occupations (4% vs. 10%) and much more likely to be unemployed (28% vs. 4%). Furthermore, American converts were more than twice as likely to have a previous criminal record (56% vs. 20%) and were three times as likely to have a documented history of mental health problems (25% vs. 8%).[182] By contrast, although British converts were also worse off than their compatriots, the differences were generally less. In terms of education, 3% of British converts had obtained a degree compared to 11% of the rest of the U.K. sample, but just 1 convert (3%) had failed to complete high school compared to 3 non-converts. Just 3% of individuals in either sub-sample were in skilled occupations; however, converts were much more likely to be unemployed (31% vs. 16%). British converts were also more likely to have a criminal record (29% vs. 17%) but there was little difference in terms of mental health issues (9% vs. 6%).
Operational Variables
Previously, Simcox and Dyer found that American converts were less likely to have received terrorist training (25% vs. 51% of non-converts), equally likely to have combat experience (18%) but more likely to have received training and then progressed to combat (54% vs. 33%). They further found that converts were less likely to be connected to designated terrorist organizations (DTOs) (38% vs. 63%) and seemingly less likely to be involved in terrorist plots against the U.S. (excluding plots involving undercover operatives).[183] Overall, these results suggest that converts are less of a terrorism threat, compared to non-converts. Although the findings from the present research generally confirm this, they also help to highlight important changes that have taken place over time as well as differences on either side of the Atlantic.
In terms of links to foreign terrorists (DTOs or otherwise), American converts are indeed less connected than non-converts (68% vs. 78% before 9/11 and 22% vs. 46% afterwards). Prior to 9/11, American converts were more likely to have trained and/or fought overseas (60% vs. 42%). After 9/11, however, the pattern has reversed - the respective figures being 12% vs. 22%. There has also been significant change in relation to planning of terrorist attacks.[184] Before 9/11, there was very little difference: 16% of American converts and 15% of non-converts were actively involved in planning attacks. Yet after 9/11, the percentage of converts rose to 44%, compared to 23% of non-converts. Finally, the number of lone-actor terrorists[185] has also increased, in particular for converts where the figures rose from 0 before 9/11 to 16% afterwards (compared to an increase from 2-8% for non-converts).
Although the changes that have occurred in the British sample have all been in the same direction, the differences between converts and non-converts are less. Before 9/11, 92% of British converts had links to foreign terrorists, compared to 90% of non-converts. After 9/11, the figures dropped to 31% and 38% respectively. The findings for participation in overseas terrorist training and/or combat are similar to the U.S: this applied to 72% of British converts and 49% of non-converts who mobilized before 9/11, then 6% vs. 26% after 9/11. Unlike in the U.S., however, there has been little difference in terms of planning attacks: 23% of British converts vs. 26% of non-converts were involved in attack planning prior to 9/11, compared to 20% and 23% respectively since then. Lastly, when it comes to lone actors, the results are again very similar to the American sample: among British converts, lone actors rose from 0-14%, compared to 2-7% among nonconverts.
Investigations
A final variable of interest for the purposes of this paper relates to the use of informants and/or undercover law-enforcement operatives within CT investigations. Here there are very substantial differences. Prior to 9/11, 36% of American converts, vs. 25% of non-converts were caught in such investigations. After 9/11, the respective percentages were 60% vs. 45%. Meanwhile, in the U.K., no converts and just 2% of non-converts who mobilized prior to 9/11 were caught in investigations using informants/undercover operatives. After 9/11, these figures rose to 14% vs. 5%.
Discussion
The above findings clearly suggest that American converts in particular are far more likely to be socially and economically marginalized on a variety of indicators compared to non-converts. They are also much less likely to have trained or fought overseas and more likely to act alone, as well as more likely to be involved in domestic attack plots and to be caught in sting operations. British converts also tend to be disadvantaged (notably with regards to unemployment and criminality) but otherwise appear to be slightly better off than their American counterparts and closer to the rest of the British sample. Similar to American converts, they are less likely to have trained or fought overseas and more likely to act alone, but otherwise there are no obvious, dramatic differences (bearing in mind that the number of British converts was smaller, meaning that percentages were easily skewed).
The disparity between these results and those of Simcox and Dyer comes down to methodology. By utilizing a wider sampling frame, the present study included a greater number of relevant cases, such as Jesse Morton (one of the founders of Revolution Muslim, later convicted of soliciting murder[186]), Ruben Shumpert (killed in a missile strike in Somalia in 2008[187]), Troy Kastigar (reportedly killed fighting for al-Shabaab in 2009[188]), and Naser Jason Abdo, who was charged in 2011 (and later convicted) of planning an attack on soldiers in the vicinity of Fort Hood.[189] Moreover, as the above results demonstrate, American converts involved in Islamist terrorist activity have shown a rapid decline in socioeconomic status after 9/11 and so it is equally important to measure changes over time.
Likewise, it is of course necessary to continually update analyses and this can obviously give quite different results. Notably, several American converts accused of Islamist terrorist activity in more recent years also appear to have been highly marginalized. These include Nicholas Teausant, who is believed to suffer from schizophrenia and stands accused of planning to join the ‘Islamic State’ (IS) following his arrest in March 2014[190]; Zale Thompson, who had been arrested multiple times and been evicted from his apartment before being killed in an attack on New York City police officers in October 2014[191]; Joshua Van Haften, an ex-convict described as a “mentally ill loner” who was arrested at Chicago airport in April 2015 on suspicion of attempting to join IS[192]; and Alexander Ciccolo, a young man with a long history of mental health and behavioral problems who was arrested on July 4, 2015 on suspicion of planning domestic attacks. [193] Although continued, systematic research will be required to confirm whether or not such cases are indeed part of a continuing trend, they nevertheless provide anecdotal support to the findings presented in this article, which suggest that American converts involved in Islamist terrorism tend to belong to a jihadi “underclass”.
Given that this is the case, American converts appear to conform, perhaps more than any other group, to the notion that people are drawn to Islamist terrorism as a result of being marginalized in society. Although this has become a rather stereotyped explanation for involvement in terrorism which tends to ignore the incredibly wide demographic profiles and diverse backgrounds of perpetrators, it at least appears to hold some truth for this category. Among the many thousands of people unable to achieve the ‘American dream’ who are left frustrated and resentful, a small number may thus find the answer in violent jihad as the ultimate counter-culture - one that promises belonging and acceptance, whilst simultaneously providing opportunities for excitement and fame and a chance to strike back against those who rejected them.[194] Putting aside debates about the nature of sting operations, this may help explain the greater willingness of American converts to attack their own country. It is also consistent with the suggestion that, for some, converting to Islam in the post-9/11 (now post-IS) world is an act of rebellion and this in turn helps us understand why there seems to have been such a dramatic shift in the average demographic profile of American converts involved in Islamist terrorism.
Why, then, would the situation be any different in the U.K.? Of course, neither population of ‘terrorist converts’ is entirely homogenous and so there is certainly overlap between the two. Nevertheless, there still appears to be a relative difference which is not easily explained. Part of the answer may lie in the fact that Islamist terrorism cases are far more geographically dispersed in the U.S., there are far fewer connections between cases on the domestic stage and the Internet appears to play a comparatively greater role in processes of radicalization[195] - meaning that violent jihadists in the U.S. often mobilize either by themselves or as part of relatively self-contained groups and there are few barriers to ‘membership’ in the movement.
By comparison, Islamist terrorism cases in the U.K. are confined within a much smaller area (dominated by four regional hotspots of activity) and there are many more connections between them.[196] This is indicative of socially ingrained jihadist subcultures within Britain, manifest by way of networks of likeminded individuals with varying degrees of involvement in extremist activism and terrorism-related activities. Presumably, these networks exert a certain level of natural control over who is able to join, which might therefore exclude people suffering from mental health disorders for instance. Moreover, the relative continuity of extremist networks in Britain may also have preserved the ‘quality’ of ideological understanding and expression in the sense that new recruits can often draw upon the knowledge and advice of more experienced individuals. By contrast, terror networks in the U.S. were largely dismantled during the 1990s and those who radicalize today are more likely to be essentially self-taught - thereby allowing wider participation and an apparently greater emphasis on specifically rebellious/counter-cultural elements over time.
The more established presence of extremist networks within Britain might help to explain another possible difference between these two countries. According to Simcox and Dyer, British converts (though fewer in number than Americans) seem to be proportionally over-represented within Islamist terrorism cases in the U.K., accounting for 15% of their sample of terrorists but only an estimated 4% of the U.K. Muslim population.[197] Meanwhile, they found that the number of American converts involved in Islamist terrorism was proportional to their place within the U.S. Muslim population (both 23%).[198] If true, the relatively high proportion of British converts might be due to the fact that they are more likely to come into contact with, and/or be deliberately targeted for recruitment by extremist networks (notwithstanding that 14% were classed as lone actors). However, there is no register of converts in either country and the overall numbers of Muslims are also approximations, meaning the above figures must be treated with caution.[199] Moreover, recent research has suggested that converts are also over-represented in Islamist terrorism cases in the U.S. Of 71 people arrested in America on ISIS-related charges since March 2014, Vidino and Hughes found that 40% were converts, compared to an estimated 23% for the Muslim population as a whole. [200] Although based on a relatively small sample, this suggests that the proportion of converts involved in Islamist terrorism in the U.S. has increased quite dramatically. Furthermore, the proportional difference is considerably greater than appears to be the case in the U.K. If indeed this is now the case, it seems likely that it is connected to
the increased significance of social media as a vehicle for terrorist propaganda and recruitment. Ultimately, however, the reality is still very much unclear and there are no currently definitive answers which explain the different profiles and rates of mobilization of British and American converts involved in Islamist terrorism.
Conclusion
The available data indicate that, contrary to previous research, American converts are in fact now worse off than non-converts on socioeconomic measures and although this also applies to British converts, the latter are much less distinct. Similar to previous research, the results here confirm that American converts in particular present a much less capable terrorism threat and are more likely to be acting alone. Nevertheless, they are also more likely to be involved in domestic attack plots within the U.S. and are more likely to be caught in sting operations.
Since converts make up a significant (and apparently growing) proportion of Islamist terrorism cases in the U.S., it is important to try and understand more about how and why such highly marginalized individuals are drawn to violent jihad. Ultimately, this may lead to more efficient ways of dealing with them. Indeed, the fact that American converts are especially likely to be caught in stings and often receive lengthy custodial sentences, makes them an added burden on law enforcement and society. Given that these individuals are socially and economically deprived and frequently suffering from mental health problems, intuitively it seems they might be more amenable to practical, “soft” interventions that emphasize social, financial and psychological support as opposed to more complex ideological “de-radicalization”. Of course such interventions will not always succeed, but amidst the current climate of strained budgets and increased mobilization to violent jihad, there is a clear need to look for alternative approaches to CT. Just as American converts seem to be especially vulnerable to radicalization and recruitment, they may present equally soft targets for CT or for countering violent extremism (CVE). Whether or not this is true -and whether it might also apply in Britain- will require further research.
Similarly, although British converts do not appear to be as distinct as those in the U.S., they exhibit relatively high rates of unemployment and criminality and (though small in number) may be proportionally overrepresented in Islamist terrorism cases. It is therefore necessary to examine them more closely in order to understand how and why they mobilize to violent jihad and just how different they are, both to non-converts in the U.K. and to converts in the U.S. More generally, there is also a need to compare ‘terrorist converts’ to non-violent converts in each country in order to establish whether the former are representative of the latter in terms of demographic characteristics. Finally, it is of course necessary to update this research in light of the significant increase in terrorist activity, largely inspired by events in Syria and Iraq, in which substantial numbers of converts continue to be involved.
About the author: Sam Mullins is a Professor of Counter-Terrorism at the George C. Marshall European Center for Security Studies, Germany, and an Honorary Principal Fellow at the University of Wollongong, Australia.
Appendix 1. List of American converts included in the sample
Converts included in the analysis are listed in chronological order according to when they began. Details include individual names, brief case description, offence period, and classifications (grounds for inclusion at the time the study was completed). Co-offenders are listed together.
Pre-9/11
1. Wadih El-Hage. AQ operative. 1982-1998. Prosecuted.
2. Ephron Gilmore. NY/NJ network, fought overseas. 1988-Unknown. Public allegations.
3. Daniel Patrick Boyd and Charles Boyd. Trained in Afghanistan. 1989-1991. Confession/Public allegations.
4. Christopher Paul. AQ links, planning attacks. 1990-2007. Prosecuted.
5. Abu Ubaidah Yahya. NY/NJ network. 1992-1993. Public allegations.
6. Kelvin E. Smith. NY/NJ network, provided training. 1993. Prosecuted (non-terror).
7. Earl Gant. NY/NJ network. 1993. Prosecuted (non-terror).
8. Clement Rodney Hampton-El and Victor Alvarez. NYC Landmarks plot. 1993-1993. Prosecuted.
9. Aukai Collins. Fought in jihadi conflicts abroad. 1993-1996. Confession.
10. Jason Pippin. Trained in Kashmir, involved with Tarek Mehanna. 1996-2003. Confession.
11. Abu Adam Jibreel al-Amriki. Killed in Kashmir. 1997-1998. KIA.
12. Adam Gadahn. AQ spokesman. 1997-Ongoing. Confession.
13. Jose Padilla. AQ operative. 1998-2002. Prosecuted.
14. Earnest James Ujaama. Oregon training camp. 1999-2001. Prosecuted.
15. Randall Todd Royer, Hammad Abdur-Raheem, Donald Thomas Surratt, Yong Ki Kwon. Virginia jihad group. 2000-2003. Prosecuted.
16. Hassan Abu Jihaad. Disclosed navy secrets. 2000-2001. Prosecuted (non-terror).
17. John Walker Lindh. American Taliban. 2000-2001. Prosecuted.
18. Jeffrey Leon Battle, Patrice Lumumba Ford and October Martinique Lewis. Portland jihad group.
2001-2002. Prosecuted/ Prosecuted (non-terror).
Post-9/11
19. Clifton L. Cousins. Threatened George W. Bush. 2001-2003. Prosecuted (non-terror).
20. Rafiq Abdus Sabir. Offered support for AQ. 2001-2005. Prosecuted.
21. Ryan Anderson. Tried to give military info to AQ. 2004. Prosecuted (non-terror).
22. Mark Robert Walker. Planned to join Somali jihadis. 2004. Prosecuted.
23. James Elshafay. NYC subway bomb sting. 2004. Prosecuted.
24. Kevin James, Levar Washington and Gregory Patterson. LA attack plot. 2004-2005. Prosecuted.
25. Justin Singleton. Discussed jihad online, lied to FBI. 2005. Prosecuted (non-terror).
26. . Paul Gene Rockwood Jr and Nadia Rockwood . Jihadi hit-list . 2006-2010. Prosecuted/Prosecuted (non-terror).
27. Mohammed Reza Taheri-Azar. North Carolina vehicle attack March 3, 2006. Prosecuted (nonterror).
28. Russell DeFreitas. JFK airport plot. 2006-2007. Prosecuted.
29. Ruben Luis Leon Shumpert. Joined al-Shabaab. 2006-2008. KIA.
30. Omar Shafik Hammami. Joined al-Shabaab. 2006-2013. Legal allegations/Confession/KIA.
31. Daniel Patrick Boyd. North Carolina jihadi plotters. 2006-2009. Prosecuted (repeat offender).
32. Carlos Eduardo Almonte. Conspiracy to join al-Shabaab. 2006-2010. Prosecuted.
33. Derrick Shareef. Mall attack sting. 2006. Prosecuted.
34. Daniel Joseph Maldonado. Joined al-Shabaab. 2006-2007. Prosecuted.
35. Bryant Neal Vinas. AQ operative. 2007-2008. Prosecuted.
36. James Cromitie, David Williams, Onta Williams and Laguerre Payen. NYC attack sting. 2008-2009. Prosecuted.
37. Barry Walter Bujol Jr. Conspiracy to join terrorists overseas. 2008-2010.
38. Troy Matthew Kastigar. Minnesota jihadi network. 2008-2009. KIA.
39. Colleen Renee LaRose and Jamie Paulin-Ramirez. Conspiracy to support terrorists overseas. 20082009.
40. Michael C. Finton. Springfield, Illinois attack sting. 2009. Prosecuted.
41. Abdulhakim Mujahid Muhammad. Little Rock shooting, June 1, 2009. Prosecuted (non-terror).
42. Zachary Adam Chesser and Jesse Curtis Morton. Online threats, attempt to join terrorists overseas.
2009-2010. Prosecuted/Prosecuted (non-terror).
43. Emerson Winfield Begolly. Promoting terrorism online. 2010. Prosecuted.
44. Antonio Benjamin Martinez. Baltimore attack sting. 2010. Prosecuted.
45. Randy Lamar Wilson. Planned to go to Mauritania for jihad. 2010-2012. Prosecuted.
46. Marcus Dwayne Robertson and Jonathan Paul Jiminez. Jihadi facilitation network. 2010-2011.
Prosecuted/Legal allegations/Prosecuted (non-terror).
47. Walli Mujahidh and Abu Khalid Abdul-Latif. Seattle military attack sting. 2011. Prosecuted.
48. Naser Jason Abdo. Planned attack near Fort Hood. 2011. Prosecuted.
49. Jose Pimentel. NYC attack sting. 2011. Legal allegations.
50. Craig Benedict Baxam. Attempted to join al-Shabaab. 2011. Legal allegations.
51. Arifeen David Gojali, Ralph Kenneth Deleon and Miguel Alejandro Santana Vidriales. Conspiracy to join AQ/Taliban. 2011-2012. Legal allegations.
52. Shelton Thomas Bell. Attempted to join jihadists in Yemen. 2012. Legal allegations.
53. Justin Kaliebe. Attempted to join jihadists in Yemen. 2013. Prosecuted.
54. Erwin Antonio Rios. Plan to commit armed robberies to fund jihad (sting). 2012-2013. Prosecuted (non-terror).
55. Matthew Aaron Llaneza. Oakland attack sting. 2012-2013. Legal allegations.
56. Nicole Lynn Mansfield. Killed fighting in Syria. 2012-2013. KIA.
57. Eric Harroun. Fought in Syria. 2013. Prosecuted (non-terror)/Confession.
Appendix 2. List of British converts included in the sample
Converts included in the analysis are listed in chronological order according to when they began. Details include individual names, brief case description, offence period, and classifications (grounds for inclusion at the time the study was completed). Co-offenders are listed together.
Pre-9/11
1. David Sinclair. Killed in Bosnia. 1993. KIA.
2. Xavier Jaffo. Killed in Chechnya, April 12, 2000. 1995-2000. KIA.
3. Andrew Rowe. International terrorist. 1995-2003. Prosecuted.
4. David Courtailler. FPM network. 1997-2000. Overseas conviction (France).
5. Jerome Courtailler. FPM network. 1997-2001. Overseas conviction (Netherlands).
6. Abdullah el-Faisal. Jihadi ideologue. 1998-2002. Prosecuted.
7. Abu Abdul Rahman Roland. Killed in Afghanistan. 1998-1999. KIA.
8. Richard Reid. Shoe-bomb plot. 1998-2001. Overseas conviction (US).
9. Dhiren Barot. US/UK attack plots (AQ). 2000-2004. Prosecuted (non-terror).
10. Martin John Mubanga. Alleged terrorist activity. 2000-2002. Gitmo detainee.
11. Feroz Abbasi. Alleged terrorist activity/FPM network. 2000-2001. Gitmo detainee/Confession.
12. Binyam Mohammed. Alleged terrorist activity. 2001-2002. Gitmo detainee.
13. Richard Dean Belmar. Alleged terrorist activity. 2001-2002. Gitmo detainee.
Post-9/11
14. Jamal Malik al-Harith. Alleged terrorist activity. 2001. Gitmo detainee.
15. . Abu Omar. Fought in Afghanistan . 2001-2002. Confession .
16. Jamal Abdullah Kiyemba. Alleged terrorist activity. 2001-2002. Gitmo detainee.
17. Anthony Garcia. Fertilizer bomb plot (Operation Crevice). 2003-2004. Prosecuted.
18. AP. Went to join jihadis in Somalia. 2004-2006. Control order.
19. Atilla Ahmet, Kibley da-Costa and Mohammed al-Figari. UK training camps. 2004-2006. Prosecuted.
20. Jermaine Lindsay. 7/7 bombings. 2004-2005. KIA.
21. Abu Izzadeen and Simon Keeler. Soliciting funds for terrorism (AM). 2004. Prosecuted.
22. Abdul Ishaq Raheem. Terror-supply network/Beheading plot. 2004-2007. Prosecuted.
23. Umar Islam. Aircraft liquid bomb plot (Operation Overt). 2005-2005. Prosecuted (non-terror).
24. Yeshiemebet Girma. 21/7 post-event assistance. 2005. Prosecuted.
25. Kevin Gardner. Army base attack plan. 2006-2007. Prosecuted.
26. Nicholas Roddis. Bomb hoax. 2007. Prosecuted.
27. Andrew Isa Ibrahim. Planned attack in Bristol. 2007-2008. Prosecuted.
28. Mohammad Abdulaziz Rashid Saeed-Alim. Attempted suicide bombing in Exeter, May 22, 2008. Prosecuted.
29. M1. Suspected terrorist activity. 2008-2009. Deported.
30. Matthew Ronald Newton. Manchester terrorism recruitment. 2008-2009. Prosecuted.
31. J1. London Somali jihad cell. 2009-2010. Detention/Deportation.
32. Abu Bakr and Mansoor Ahmed. Killed in Pakistan. 2009-2010. KIA.
33. Richard Dart. (Attempted) overseas training/Planning domestic attack. 2010-2012. Prosecuted.
34. Minh Quang Pham. Joined al-Qaeda in the Arabian Peninsula (AQAP). 2010-2011. Legal allegations (US).
35. Nicholas Roddis. Preparing for acts of terrorism. 2011-2012. Legal allegations (repeat offender).
36. Robert Baum and Christian David Erkart Heinze Emde. Possession offences. 2011. Prosecuted.
37. Samantha Lewthwaite and Jermaine Grant. Planning attacks (al-Shabaab). Legal allegations (Kenya).
38. Maryam. Joined jihad in Syria. 2013-Unknown. Confession.
39. Michael Adebolajo and Michael Oluwatobi Adebowale. Murder of Lee Rigby, May 22, 2013. Legal allegations (non-terror).
40. Royal Barnes and Rebekah Dawson. Encouraging acts of terrorism online. 2013. Legal allegations.
Terrorist Practices: Sketching a New Research Agenda
by Joel Day
Abstract
Contemporary approaches to the study of terrorism ignore the social practices that operate as ‘background noise’ in daily life. Research focusing on goal-seeking and the ‘aims’ of terrorist organizations leaves little room to analyze the performative, emotional, and ritual aspects of terrorism - key aspects of identity and disposition formation. Just as in other social cleavages, terrorist ritual and community practices forge actor preferences and passions. This note outlines puzzles which extant research agendas leave unanswered, proposes a ‘turn’ to cultural practice as an important new research area, and offers an example of how to conduct mixed method research on terrorist practices, looking specifically at how religious practice disaggregation predicts terror campaign duration. The research note concludes with academic and policy implications.
Keywords: terrorism; research; methodology; practice; culture; religion; duration; ideology; disaggregation
Introduction
Terrorism is widely understood as an organizational and strategic endeavor. Leading lights in the field argue that terrorism is a communication tactic, designed to produce political and social outcomes.[201] Even if terrorists engage in activities that are not supported by any rational cost-benefit analysis, their behavior is assumed to further organizational coherence strategies or ideological aims.[202] These mainstream approaches result in studies linking financing, weapons choices, training, doctrines-the “raw stuff” of what it takes to “do terrorism”-with terror outcomes like body count and target selection.[203] Such research designs leave little room to analyze the performative, emotional, and ritual aspects of terrorism - key aspects of identity and disposition formation. Terrorism studies thus reflects a trend that parallels Ted Hopf’s claim that academic international relations has virtually ignored what “most people do most of the time in their social lives.”[204] Essentially, contemporary approaches to the study of terrorism ignore the social practices that operate as “background noise” in daily life.
This Research Note presents an argument that a more fine-grained disaggregation of everyday life within terrorist groups is needed to help scholars understand differences within and between groups. Studying the actual activities and practical enactments of everyday terrorist life turns scholarly attention away from goals and ideas and towards social practice as the unit of analysis. Practice approaches are heterogeneous, but share a core commitment to understanding knowledge as social practice rather than ideology or goalseeking. Ultimately, “turning” terrorism studies toward practice accommodates many epistemological views and builds new ways of understanding terrorism.[205] The approach builds on a pioneering call by Thomas Hegghammer to study “jihad culture.”[206] Hegghammer’s idea is part of a larger orientation in international relations and security studies generally, joining other works on “practice” as a way to help scholars understand gendered dimensions of diplomacy,[207] political bargaining,[208] security communities,[209] deterrence,[210] and peacekeeping.[211]
The following four sections of this Research Note sketch what a practice turn in terrorism studies might look like as a research endeavor. Section one displays how current theories in terrorism studies leave unanswered puzzles and are based on unfounded assumptions of how human socialization functions. Section two outlines a theoretical foundation for prioritizing everyday practice as a way to understand extremist groups, and describes a potential mixed method approach for studying the identifiable practices of extremist groups. In section three, I offer a brief example of how to proceed within this research agenda. Here I disaggregate religious practices of terror groups, using a model that helps predict which terrorist groups have longer campaign durations. And the fourth section concludes by demonstrating the policy and research implications of this new approach to research in Terrorism Studies. In essence, there is clearly support for the argument that taking practices seriously will allow scholars to put aside “armchair analysis” and instead privilege observable social action on its own terms.[212]
Unsolved Puzzles and Questionable Assumptions
Current approaches in terrorism research result in at least three problematic themes. These include 1) the inability to answer puzzles about why terrorists often engage in aesthetic rather than strategic activities, 2) puzzles concerning disparate findings across the discipline, and 3) fundamentally misplacing emphasis on “thinking” as a principle social building-block and ignoring the more important role of “doing.”
First, there are many puzzles that current approaches simply cannot answer. What, for example, is the role of emotion in violent extremist organizations and how do emotive elements within everyday life frame passions and preferences of terrorists? Similarly, why do terrorists pursue art and aesthetics when such energy should rationally be used to hide, plan, train, and kill? For instance, the Sovereign Citizens’ practice of making artistically distinct forged documents is puzzling since many are intentionally poorly constructed, mocking rules of grammar and punctuation. If these domestic terrorist groups were trying to avoid authority interaction, why would they intentionally design forged documents to look suspicious and even comical, raising red flags and increased police oversight? Aesthetic inclinations are important because they reveal how elements of culture operate to shape and shove actors even without their overt mental processing. If terrorism isn’t just about pre-planned strategic actions, but the almost subconscious activities that are a result of the practices shaping day-to-day life, then current approaches to the study of terrorism are not doing justice to that reality.
Second, research that privileges exogenous social factors—institutions, financing, ideological affiliation, and politics—results in an inability to distinguish the difference among internal cultural characteristics of a group. The unfortunate result is evident in studies of religion and terrorism: A sizable portion of terrorism scholarship holds that religion is a secondary factor behind socio-political drivers like poverty.[213] However, other scholarship finds religious affiliation to be a principle explanation of extremist violence.[214] Such disparate findings indicate that over-aggregated measurements of religious affiliation (i.e. Muslim, Christian), and too much attention on exogenous variables result in inconclusive findings. Over-aggregated approaches also leave no ability to explain variation of activities within catch-all labels, such as why some Sufi groups produce ISIS recruits while others remain quietist. Over-aggregation of religious labels leave scholars with categories that lump actors like the Rainbow-Push Coalition and the KKK into the same analytical space because they are both “Christian.” Such labels do injustice to understanding obvious variations within and between groups.
Third, and perhaps most problematic, is the current literature’s assumption that meaning is created through propositional knowledge, or terrorist’s thinking through goals, organizational ties, or doctrine.[215] Accurate descriptions of goals or ideology requires a laborious amount of cognitive work for each and every actor in a violent environment, which most work in terrorism simply “assumes” into quantitative models. Recent work in this journal, for instance, has argued that differentiation between secular and religious terror groups is entirely based on ideologically informed and articulated goals.[216] I maintain that it is highly improbable that actors search through an ideological or strategic “blueprint” for each and every action they take. If we look further into terrorist action, my hunch is that some events are driven neither by ideals nor by goals, but by unintelligible and unspoken “background” dispositions. For example, in my research on post-war Sierra Leone, I came in a town in the district of Kono, where after the war, the only two buildings left standing were the church and the mosque. When I asked former rebels about why they failed to raze the buildings, they responded that nobody burned churches—it just wasn’t done. The justification given was about organizational dispositions—“that’s just what we did,” not from consulting any prescribed cognitive blueprint for action. Thus, to conceptualize goal-seeking behavior as a mere mental state takes out of consideration the way that physical training (say, in training camps) constitutes violence as a practice of terrorism a priori. [217] My argument joins Alasdair MacIntyre who maintains that most of what we see as goal-seeking behavior (after the fact) is actually carried on unformulated, improvised, and non-representational ways.[218] The processes of practice, alternatively, are where an actor taps into a “stock of unspoken know-how, learned in and through practice, and from which deliberation and intentional action become possible.”[219] Practice theory would instruct the methodologist to set aside research on ideas and goals, and instead start observing the concrete proceedings of daily life as the central object of meaning-making in the world.
Social Practice and Terrorist Society
Studying terrorist everyday practices points away from organizational dynamics, tactical choices, and static ideological ascription, and instead towards the background “noise” and aspects of society that are taken for granted. Practice theory goes as far back as Aristotle, when he wrote of “practical wisdom” as a form of knowledge.[220] Aristotle posited it is through practical wisdom that one does the “right thing” as part of her disposition, not merely due to belief or cost/benefit analysis. Practice theory turns our attention to this sort of “acting out” the “right thing” and instructs those interested in social outcomes, such as terrorism, to pay special attention to the embodied, dispositional manifestations of how one goes about performing in their day-to-day life.[221] The practice approach argues that “what we do together defines the question of who we are” together.[222] To state more precisely, a practice-oriented approach seeks to “do justice to the practical nature of action by rooting human activity in a nonrepresentational stratum,” meaning those activities that actors may not think through in order to perform.[223]
These aspects of practical knowledge involve one knowing how to perform in ways that are socially expected of them, whether in the practice of scripture reading, document forging, or taking a rest in the trenches. Even ISIS’s method of beheadings could be understood as informed by the preferences forged by textual- interpretive tradition, mimicking, ritual, and belonging. Further, it is doubtful that the colorful orange jumpsuits ISIS prisoners wear before beheading is something that the fighters “think through” every time they force a prisoner to put one on - it is just something that is done. The ultimate argument is that social practices—such as dress, textual interpretation, discussing dreams,[224] or naming one’s Kalashnikov, are areas that produce relational power, internalized into daily routine by a process of bodily “disciplining.” Ultimately, the practices of a group reveal the kinds of activities necessary for actors to be considered by the organization as socially competent and a co-identity member.[225] Identity formation via ritual builds on Whitehouse, who argues that everyday rituals “fuse” actors to their community so that group members are not perceived as mere cooperators; they are kin.[226]
While practice opens the door for terrorism scholars to consider new types of social phenomena within groups, it also directs the data-collection agenda towards observable, material manifestations of collective identity. Prior study of practice theory has examined ritual performances, training manuals and meeting minutes to observe how social expectations are internalized and perpetuated in group members. Like the method of process-tracing, tracing practices involves using evidence from within a case to make inferences about causal explanations within that case.[227] Yet, as Pouliot argues, while process tracing identifies a theoretically-informed causal chain “between an independent variable (or variables) and the outcome of the dependent variable,” practice-tracing is interested in how bundles of activities construct actors in particular ways.[228] Thus, the practice approach lends itself to both qualitative and quantitative investigations. First, case studies might consider singular local-level activities on a descriptive level, employing ethnographic methods, interviews, and (difficult for the study of terrorism) participant observations. This work would help us better understand particular groups, their processes of meaning-making, and social dispositions. Qualitative comparative cases might then compare, for example, how variation in Koranic interpretation between Hezbollah, Hamas, Islamic Jihad, and ISIS impact elite instrumentalization of particular verses. Likewise, veiling, purity of dress, dietary and fasting practices may vary within jihadi organizations, perhaps explaining the variation in how jihadi members interact with local populations with divergent daily rituals. Thus the job of the practice ethnographer is to find singular, local “causality” within a particular group that might then be used to construct broader comparative categories for larger-N studies. In many instances, ethnographic data may be readily available to construct datasets for comparing hundreds of groups over space and time. For example, the work of art and music ethnography, food culture, and fashion studies, have deep reservoirs of data on sub-national groups from which terrorist groups arise, but such data has never been systematically applied to understand the effects of culture on terrorist preferences, passions and outcomes. In sum, practice can be employed as a unit of analysis sequentially up the ladder of abstraction from micro-level specific contexts up to large-N statistical models.[229]
Leveraging Practice Disaggregation: The Case of Religious Culture[230]
Practices are actions embedded in institutional and organizational sinew, evident and observable in member performance. Religion is one area of human activity that requires one to not only profess, but practice that profession in a visible way. One’s identity as a believer is thus profoundly not propositional—as extant strategic, organizational, or ideological approaches assume—but a series of doings and sayings rooted in dispositional knowledge.[231] Propositional approaches are problematic because religious socialization and meaning-making may not necessarily be that which is deliberated, calculated, and operationalized. Rather, ethnographic research in practical theology has found that persons participate from a dispositional “urge” often explaining how “We don’t think about our rituals, we just do them,” or simply “It’s always been done that way.”[232]
A Model of Religious Practice Disaggregation
To illustrate the argument and method described here, I collected data on several hundred terror groups’ practices, disaggregating the practices of actors in Asal and Rethemeyer’s BAAD dataset.[233] I code a terrorist group memberships’ religious practices on several dimensions, adding them together in an index, which serves as an explanatory variable for the outcome of campaign duration, while controlling for GDP, regime type, religious difference, and ethnic, leftist, and territorial goals. The data are then analyzed using a logistic regression.
The explanatory practice index has two components.[234] First, there are eight dimensions of religious practice that are widely comparable and which vary considerably from group to group. These are not arbitrary categories, but are core ways of describing the practical theologies as played out by religious communities. Fortunately, and unique to the field of religious practice, the practices of religious communities have been recorded through extensive ethnographic work by religious sociologists.[235] Each element of practice is discussed in the most popularly cited texts on religious life, such as the Worldmark Encyclopedia of Religious Practice, which includes analysis on almost every religious community from 245 religious scholars.[236] From localized, ethnographic sources, one can compare religious communities along eight dimensions of practice: 1) orientations towards scripture, 2) defined leadership hierarchy, 3) practice and rituals concerning an afterlife, 4) demarcations of sacred space, 5) practices of diet, 6) dress habits, 7) rites of passage, and 8) prayer rituals. These dimensions are a kind of typology of religious practice and a cut at how scholars can observe religious actors in action, helping answer recent calls in international relations to take “thick” descriptive approaches to religion seriously.[237]
Second, each aforementioned dimension of practice is coded based on the level of exclusivity demarcating who is allowed to participate. Such an approach is based on the Durkheimian definition of religion as a separation of the sacred from the profane, as participating in ritualized life is fundamentally asserting difference between communities, lifestyles and worldviews. Ritualization is the production of differentiation between in-groups and out-groups, as practicing one’s religion is a way of acting in a particular way that establishes a contrast of privileged being. Thus, the way to correctly categorize groups like ISIS/ISIL is not “literalist” but rather “exclusivist” in that they appropriate their religion in a particular sort of way in conflict. [238] I also code each dimension of religious practice based on the exclusivity of that practice. I employ a 0/.5/1 exclusivity scale per eight categories, thus a group’s membership can score between 0-8 in the index. I code a practice as (0) when there is very little frequency, salience, or distribution of the practice within the members of a group. I code a group this way when there is definitive evidence that membership explicitly rejects the practice. For instance, many neo-Marxist groups explicitly prohibit public prayer. While some membership may still engage in prayer, the frequency, group-wide salience and distribution is negligible. In cases where I find mixed group practices I code the variable as (0.5). Instances in this category will have evidence of some members participating in the practice while others may not, or will have contending practices (i.e. Christian mixed with traditional religion). When specific percentiles are available, I code as “mixed” any membership levels from 10%-50% engaging in the practice. I code the variable as (1) when there is high frequency, salience, and distribution of a practice. Cases in this category include if there is definitive evidence that majority of membership practices, if the practice is explicitly talked about in-group memoranda, or if a group explicitly requires such orthopraxy as a condition of membership.
The outcome variable of interest is the duration of the terrorist campaign, from founding or first event to the end of the campaign through die out, losing, winning, or other termination type. This is a good test of the effect of exclusive practice on outcomes, since communities with dispositionally rigid practices are theoretically less likely to give up fighting, even at great loss. Toft, for example, holds that religious groups are likely to “lengthen time horizons” by factoring in the cosmic struggle of eternal good versus evil.[239] A practice approach concurs with this finding, but revises the central mechanism at work. Rather than a community propositionally thinking through violence with a cosmic cost-benefit analysis, practice posits that the discipline of exclusive practices frame everyday life (not just the conflict at hand) in terms of cosmic time. Rites of passage like baptism, for example, are mile-markers in a cosmic performance. Thus, extended time horizons are not necessarily rationalized by cost-benefit analysis, but are part of everyday social structure. Once conflict breaks out, those groups with more hardline dispositional realities are likely to bring extended time horizons with them, approaching a violent environment with skewed time-frames. Those with everyday practices that extend time horizons and set restrictions for who gains access to that afterlife are less likely to give up their fight.[240]
Results
Model 1 tests how a practice index contributes to how we can explain the duration of terror campaigns. This basic test refutes the null hypothesis. The results (shown in Table 1) indicate a positive and highly significant correlation between a terrorist group’s exclusive religious practices and terror campaigns with longer duration. Models 2, 3 and 4 include controls for ethnic, leftist, and territorial based conflicts, regime type, GDP per capita, and a dummy variable indicating differences in religious affiliation between the terrorist group and the state. When we control for these structural factors, secular goals, and difference in religious identity markers, practice remains a significant indicator: higher levels of exclusive religious practices are positively and significantly contributing to the duration of terror campaigns.[241]
Table 1: Effect of Exclusive Religious Practices on Terror Campaign Duration
| (1) Duration | (2) Duration | (3) Duration | (4) Duration | |
| GROUPIndex |
0.530*** (0.0729) |
0.533*** (0.0971) |
0.368*** (0.0914) |
0.366*** (0.0917) |
| Ethnic |
1.422 (0.763) |
1.610 (0.951) |
1.580 (0.965) |
|
| LeftAnarchist |
0.544 (0.548) |
0.903 (0.618) |
0.944 (0.613) |
|
| Territory |
1.469 (0.935) |
1.251 (1.148) |
1.252 (1.149) |
|
| LogGDP |
-0.456*** (0.0954) |
-0.459*** (0.0964) |
||
| PolityOnsetYear |
-0.0873* (0.0354) |
-0.0854* (0.0374) |
||
| Rel_Dif |
-0.111 (0.392) |
|||
| Constant |
0.636*** (0.145) |
-0.102 (0.534) |
4.590*** (1.133) |
4.653*** (1.172) |
|
Observations Pseudo R-squared |
560 0.249 |
560 0.298 |
560 0.361 |
560 0.361 |
Standard errors in parentheses * p<0.05, ** p<0.01, *** p<0.001
The results of Model 4 are used to examine the predictive marginal effects of terrorist group practice on the likelihood of conflict intensity, shown in Figure 1. For each index point change in terror group practice, we see a corresponding rise in the likelihood of longer campaign duration. The most exclusive practicing groups are about 20% more inclined to have longer campaign durations.
The findings suggest that categorizing religious conflicts as simply one group versus another (Christian versus Muslim, Sunni versus Shia), is an unhelpful variable to explain variation in campaign duration. Yet, when one disaggregates groups based upon their observable practices, one can better explain duration of terrorist campaigns.
Research and Policy Implications
There are important academic and policy implications for studying terrorist practices. On an academic level, the approach directs researchers away from the requirement to “get inside terrorists’ heads” in order to access information about their goals or ideology. One can then avoid assumptions about the effect of rhetoric or rationality on mobilizing persons towards extremism. This is preferable since in order for religious rhetoric to “work” on a population, there has to be some sort of framing device that triggers rhetorical and instrumental effectiveness. Practice gets closer to embedding the study of terrorism within the relational and embodied sites of society. Additionally, the choice to disaggregate groups based upon practices enables scholars to empirically examine “what people are doing on the ground” as the basis for categorizing religion and other social categories. Practice theory is thus better positioned to capture the activities of group membership, not simply the goals or doctrines promulgated by leaders. Since elements of religious practice exist even within groups that pursue secular goals, it is inappropriate to assume goals or ideology of elites are reflected in the daily life of group members. Simply categorizing groups based on their objectives fails to capture how ritual and practice frame dispositions of membership.
On a policy level, a practice approach argues that an understanding of violent groups should follow analysis of their “walk,” not just their “talk.” If jihadi, sovereign citizen, the Klan, or other extremist identities are forged less by propositional goals or beliefs and more through dispositional embodiment of social practice, then analyzing how terrorists live in their “everyday life” could offer data that helps researchers better understand group passions and preferences. Everyday practice offers a new, unexplored terrain for combating violent extremists. For instance, when not posting on social media about ISIS and jihad, do ISIS fans watch Friends and cat videos? Answering this question could offer routes of mainstream connections for radicals, who might prove moderated by meaning made in non-extremist practices. Finally, a practice approach offers the ability to map and track specific activities in particularly problematic “hot-spot” areas. For example, large-scale mapping of religious practice would predict areas of conflict that will experience longer campaign duration. Mapping could thus be a predictive tool for the intelligence community by indicating zones of culture where, say resource scarcity or refugee spillover (for example), would be amplified by particularly exclusivist religious practices. Similar models could be constructed for other types of social practices including disaggregation of identity labels like ethnicity and gender. This information could then be used by academics, decision makers, and intelligence officers alike, to better understand the social culture of terror groups.
A practice-oriented approach to the study of terrorism offers researchers an exciting new way to disaggregate terror groups and thus better understand variation within and between them. Practice theory opens the field of terrorism studies far beyond models that privilege representational goal-seeking or belief, and instead positions scholars to deeply consider how art, diet, poetry, dress, religious ritual, and other dispositionforging practices constitute terrorist identities, passions, and preferences.
About the Author: Joel Day is Assistant Professor, School of Criminology and Justice Studies, and Research Associate, Center for Terrorism and Security Studies at the University of Massachusetts Lowell.
Acknowledgments
This research was supported by the Office of University Programs Science and Technology Directorate of the U.S. Department of Homeland Security through the Center for the Study of Terrorism and Behavior (CSTAB - Center Lead) Grant made to the START Consortium (Grant # 2012-ST-61-CS0001). The views and conclusions contained in this document are those of the authors and should not be interpreted as necessarily representing the official policies, either expressed or implied, of the U.S. Department of Homeland Security, or START.
Eyewitness Accounts from Recent Defectors from Islamic State: Why They Joined, What They Saw, Why They Quit
by Anne Speckhard and Ahmet S. Yayla
Abstract
This Research Note reports on preliminary results of the Islamic State Interviews Project, based here on a sample of thirteen Syrian IS defectors who spoke on life inside the “Islamic State”(IS). A fuller and more systematic account will be published in early 2016 in book form. According to what we learned, all IS cadres undergo Shariah training in which they are imbued with a Takfiri ideology that allows them to deem all others, including Muslims, who disagree with IS’ extreme ideology, as apostates who should be killed. Despite this indoctrination, all of our informants (all Syrians) experienced their Shariah trainers as a positive influence since they allowed them to deepen their own religious understanding. In this sense, these disengaged defectors remained radicalized “true believers”. Following compulsory military training courses on weapons, explosives and physical fitness, they were sentto the front. Syrians who join IS are rewarded with salaried jobs which for young men translates into the ability to marry and for young women the money allows them to save their families from literal starvation. Foreign fighters receive additional rewards: wives, sexual slaves, and sometimes homes and cars. Daily life is punctuated by brutal practices - including floggings, torture and beheadings. Defections were the result of exposure to extreme brutality, disgust over the slave trade, observations of deep hypocrisy-a total mismatch between the words and deeds of IS. Charges of corruption and complaints about battlefield decisions that produced unnecessary deaths in their own ranks were also causes of disillusionment . Our informants all had come to hate IS and warn others not to join what they gradually came to see as a totally disappointing, ruthless and un-Islamic organization.
Introduction
The Islamic State (IS) is the most powerful, ruthless, horrific and well-funded terrorist group in recent history. Not only has IS managed to take and control a significant swathe of territory, it has become a de-facto state. Since their 2014 claim of establishing a Caliphate, IS has also unleashed an unprecedented and prolific social media recruiting drive that has enabled them to attract up to 30,000 foreign fighters from more than one hundred countries. A steady stream of fighters continues to enter Syria and Iraq on a daily basis - with some estimates placing their number at over one thousand new recruits per month.[242] In addition, IS has created a “brand” that has been exported to over twenty hotspots around the globe. As IS has arisen - seemingly out of nowhere - to become a powerful foe, the West has struggled to comprehend and understand how to effectively counter it.
While a political solution in the war-torn area of Syria and Iraq is a necessary precondition to the defeat of IS, discrediting the group’s ideology is also essential. Defectors from IS, who alongside the refugees pour out of IS-controlled territory, are among the most powerful first-hand voices to speak out against the group. Indeed, disillusioned cadres of those who can speak from experience and tell their authentic stories about life inside IS may be the most influential tool for preventing and dissuading others from joining IS.
This Research Note, based on preliminary findings of the International Center for the Study of Violent Extremism’s IS Defectors Interview Project, reports on findings from thirteen interviews with actual IS defectors currently hiding in Turkey. It throws light, in their own words on their experiences inside IS- including their motivations for joining; their ideological indoctrination, their weapons and military training, battleground experiences, gender (mis-)treatment, the social everyday life in IS-controlled territory, experiences with slavery and other forms of humiliation and cruelty. The interviews also highlight the factors that ultimately led to disillusionment and defections. These first-hand accounts offer a harrowing ‘inside account’ of how IS actually operates.
ISIS — A Brief Backgrounder
The border between Turkey and Syria, winding along Turkey’s southern flank, stretches out over five hundred fifty miles of contiguous territory [243]. On the Turkish side lies the land of Sanliurfa, sharing over one hundred thirty nine miles of border with Syria, one of the oldest settlements in the world, its history going back some 11,000 years. The largest province of southeastern Anatolia and the ninth largest in Turkey, its population numbers some two million people. Yet most important today is that it also shares what has, and continues to be, a highly porous border with Syria to the south-one that has allowed fighters against Bassar Assad’s regime-ranging from the Free Syrian Army, (al-Jaysh -Hurr, FSA), Jabhat al-Nusra (also known as al-Nusra Front, JN), Kurdistan Worker’s Party (PKK), the Kurdish Democratic Union Party (PYD) and, in recent years, IS cadres, to move freely across it. Indeed “Urfa” (short for: Sanliurfa) has often been referenced by IS cadres as a rest and relaxation point from the battles in Syria and Iraq, as well as a meeting place inside Turkey, for arriving foreign fighters before passing over the border into Syria. This Research Note is a report on our preliminary findings from interviews with former fighters who moved in the opposite directionactual IS defectors. Yet before we focus on them, here is some necessary background on IS.
The Islamic State in Iraq and Sham (IS) is formerly known as the Islamic State in Iraq and Sham (ISIS) or the Islamic State of Iraq and the Levant (ISIL), and is also known in Arabic as ad-Dawlah al-Islamiyah fi ‘--Iraq wa-sh-Sham, (i.e. Da’ish or Daesh). IS forces its subjects, i.e. the people under its control, to refer to it as ad- Dawlah (the State) and severely punishes people who uses other names, including Daesh or IS. IS arose as a proto-state during the Sunni rebel uprisings in Syria in 2013 but originates in Iraq, building on the legacy of Abu Musab al-Zarqawi, who, until his death in 2006, was al-Qaida’s emir in Iraq.
ISIS is led by and composed mainly of Arabs from Iraq and Syria, although it has also attracted 25 - 30,000 foreign fighters from around the globe. IS currently controls territory in both Syria and Iraq, about the size of the UK, area that until recently was occupied by up to ten million people. IS controls the Iraqi city of Mosul in Northern Iraq and is headquartered in Raqqa, Syria. Foreign intelligence estimates of the number of fighters in IS vary greatly, ranging from thirty-five thousand to seventy thousand. Fuad Hussein, the chief of staff for Kurdish President Barzani, argues that IS has at least two hundred thousand fighters, citing their ability to rapidly mobilize Arab young men inside their territory into a large field army [244]. Indeed our interviews tend to confirm such a high number.
ISIS claimed a worldwide caliphate on June 29, 2014 with Abu Bakr al-Baghdadi as its caliph. With a highly motivated and ruthless fighting force of tens of thousands, IS follows an apocalyptic vision of the future-its ideologues proclaim that the “end times” are near, and that its fighters are about to be engaged in a final cosmic battle to bring about a new world order. Many of the cadres are willing to die for the cause, believing that becoming Islamic ‘martyrs’ secures them a place in paradise.
Al-Qaeda (central) and Jabhat al-Nusra (the local branch in Syria of al Qaida) both rejected IS’s declaration of a caliphate and heavy fighting between the two factions continues to the present. While Jabhat al-Nusra is one of the leading forces among the Sunni rebels fighting against the Assad regime in Syria, IS has broader aims-to control territory in Syria, attract fighters from around the world, consolidate the self-proclaimed Islamic State and then to launch a full invasion of Iraq and to expand from there. While IS claims to represent true Islam, its cadres are in fact known for their ideologically twisted interpretation of Islam and ruthless treatment of fellow Muslims as well as subjugation of Christians and Yazidis.
The IS ‘caliphate’ has captured the imagination of many Muslims worldwide, resulting in a steady flow of some thousand foreign fighters streaming into Syria and Iraq each month from all around the globe, including five thousand or more foreign fighters coming from Muslim diasporas in Western Europe.[245] Women have also gone to join IS-becoming brides of IS fighters, recruitment agents and even Shariah enforcers in the form of morality police (hisbah).
ISIS is one of the most well-funded terrorist organization to date and relies on a steady stream of income from illicit trafficking in oil, bank theft, war booty, extortion and “tax collection” from the people inside its borders; kidnapping victims for ransom, female slave trade and from trafficking in stolen antiquities.[246]
As our interviews revealed, defections from IS territory and even from IS itself are not allowed. Those who escape must do so surreptitiously, risking their own lives and often also those of family members they leave behind. Fleeing fighters, and sometimes even ordinary citizens, caught while trying to escape the Islamic State are generally not subjected to a court proceeding. Instead they are brutally executed on the spot. For instance, one informant (Abu Nasir - not his real name) told us, “A European girl wanted to escape. Someone tried to help her to go back to Urfa [Sanliurfa, Turkey], to escape. But they caught him and killed him right there and took the girl back”. Stories of defectors who did not make it across the border to Turkey and were beheaded on the spot were common in the accounts of those we interviewed.
Interview Protocols and Sample Description (n = 13)
This Research Note is based on our first sampling of defectors who made it across the border. Our interlocutors were all Syrians-twelve men and one woman, ranging in age from fourteen to forty-five. They were all Arabs. Three originated from Tell Abyad, four Raqqa, two from Aleppo, and one each from Tishrin, al-Hasakah, el-Aziziye, and Deir ez-Zor. The men had all undergone Shariah indoctrination and military training with IS and had sworn an oath of allegiance (bay’ah) to IS before becoming fighters for the Islamic State. They spent between six and eighteen months as IS fighters and had defected within one year before the interview. Three had been in leadership positions as commanders, one of them as Chief of Security at a base in Raqqa and one of them was the Emir of a town under the control of ISIS before his defection. The rest were ordinary fighters, a prison guard, and the minor, a fourteen year-old child had been groomed to become a suicide bomber.
All of our subjects are now living in the Sanliurfa region of Turkey and all are in hiding, fearing the long arm of IS. They were all married except for the minor, and all of them except for the youngest adult (who had only married the week before the interview) had one or more young children. Our female informant was a mother and was married to a defected IS fighter. She was considered by IS as a member by virtue of her marriage to a fighter. Three of the males were college-educated, one was a law student in his last year, another an Arabic language teacher and the third an Arabic literature teacher. Three were high school graduates. The other adults we interviewed had not finished high school and one even had dropped out of primary school. They were farmers and small business owners. The minor had his middle school education interrupted by the conflict in Syria.
The interviews took place in the autumn of 2015 and are part of an ongoing effort by the researchers to interview IS defectors. They were carried out anonymously, with the first six interviews taking place with only the ‘fixer’ (i.e. the individual who arranged the interviews) being aware of the true identities of those we interviewed. Some of them knew the ‘fixer’ personally because he had been involved in their being smuggled across the border. For these interviews, the ‘fixer’ also insisted on sending along his own interpreter, known only to himself and the former cadres, to ensure that the interviews and the identities of those interviewed would not be leaked to IS intelligence and also to ensure his life from the hands of IS.
In the second group of seven interviews, we made use of one of the IS defectors as our fixer and interpreter, reducing the number of people involved and increasing anonymity and security for our informants. This change in research protocol was deemed necessary and took place after an active IS cadre-claiming also to be an IS defector-crossed into Turkey and won the trust of two journalist/activists (Ibrahim Abdul Qader and Fares Hamadi) [247] from the group Raqqa is Silently Being Slaughtered. Gaining access to their apartment, he murdered and beheaded them in the city of Sanilurfa.
Naturally, everyone who heard about this was terrified by this turn of events. At that point, our subjects were reluctant to participate, but were persuaded to do so after we made improvements in our security protocols to protect their identities. We began bringing them to interview locations alone rather than in groups-even in those cases where they knew each other. We changed the interview locations frequently, in order to protect them once we became aware that even with them living in Turkey, reprisals could occur.
We did not at any point inquire for names, nor record personal details of our interlocutors, in order to keep the interviews truly anonymous. To protect those we interviewed, we asked only about the violent acts of others, but not their own, so as not to involve them in incriminating themselves and to also avoid putting ourselves in a position of responsibility to report a criminal activity. The first six informants agreed to audio and written recording only. The second seven agreed to video recordings, but with their faces covered, and with the understanding that we would alter their voices before making any of these interviews public.
Our informants agreed to cooperate in order to share with the world how IS recruits and operates. They also volunteered to provide brief statements at the end of their interviews, directly addressing anyone considering joining IS in the hope that these would serve in preventing and dissuading others-including foreigners-from joining IS.
Complicating the sampling was the fact that the subjects feared IS intelligence and presence inside Turkey and reprisals from the group against themselves or their family members who were with them, or relatives back in Syria being killed as a result of their defections and participation in our interviews. They also feared Bassar Assad’s intelligence and the Syrian regime’s presence inside Turkey and possible similar reprisals. Given that there are over four hundred thousand Syrian refugees in Sanliurfa alone and that among them are IS and Syrian regime intelligence members collecting information about these people, alongside the recent murders of the two journalist/activists carried out by IS, these fears are not unfounded.[248]
Lastly they feared prosecution in Turkey for having been part of a terrorist group and were thus reticent to admit to any crimes they had committed while inside IS. Their fears of prosecution by Turkish authorities were heightened in October 2015, just after Ankara suffered a suicide attack (where 132 people died) attributed by Turkish authorities in part to IS. Needless to say, their fears of IS reprisals were greatly heightened by the recent double murders in Urfa, carried out by a claimed IS defector.
In this Research Note, we group some of the statements from the thirteen former IS fighters who granted us interviews in a thematic way under various headings. A more complete account will be provided in the form of a book to be published in early 2016.
ISIS Governance Tactics
A tactic applied by IS, as underscored by our informants, is to quickly gain control of all the economic and social infrastructures in an area-making it difficult to resist-thereby forcing the inhabitants to join in order to survive, even to literally obtain food. IS cadres are also extremely ruthless, immediately demanding that the local population bend to their rules.
“When Daesh took over they said, ‘You are either with us or not. They gave no food, no jobs except to people who joined them, so the people got so hungry. Daesh also began recruiting twelve to seventeen-year-old to become their soldiers. They provided well for them so they can feed their families. The [ISIS] shaikhs also pulled the youth in. When IS came to Raqqa, all the people suddenly don’t have work. Some join immediately for free food.” (Abu Walid).
Takfiri Practices
ISIS cadres claim to be following an authentic early version of Islam-following an extremist interpretation of Wahhabi and Salafi practices, observing what they claim were the original customs followed by the Prophet and his companions. IS cadres engage in takfiri (excommunication) practices-that is, they claim the right to label other Muslims, to whom they object, “unbelievers” and exterminate all those who do not adhere to their own extremist ideology. According to our informants, anyone who does not follow their extremist ideology is labeled murtad (a Muslim renegade), infidel, or kafir (unbelievers)-categories of people that, according to IS, can be killed with impunity.
One of our informants recalls that when IS moved into Raqqa, the local population were told that they needed to follow the “true Islam.” “In November 2013, when IS took Raqqa,” our informant recalls, “they told us, ‘You are not Muslim, you are kafir (an unbeliever/rejecter of Islam). You are infidels,’” (Abu Walid). As our informants told us, those who have sinned according to IS dogma and agree to live under IS rule are required to go through a process of tawbah (repentance), in which they openly have to declare sorrow over past sins and pledge never to repeat them. Tawbah takes place in front of a Shariah judge and is to be followed by announcing one’s allegiance to the Caliph. By this process the label of “kafir” can be shed and the person then can live under the rule of IS as a “true Muslim” IS-style.
Morality Rules
Infractions with any hint of sexual impropriety are harshly punished under IS rule. One informant told us: “A man in a small village went to visit his neighbor. He knocked on the door of a woman whose husband was not there. He was caught waiting inside the front yard of the home [inside the outer gate of the yard] when the husband was absent, so he was arrested. He was lashed forty times.” The lashing was so harsh that, “he could not use the toilet and had to stay in bed for twenty days. Afterwards he was forced to take the Shariah course for three weeks. The woman inside the house was lashed forty times as well because she opened the door to the yard for him” (Abu Walid).
Intelligence Gathering and Intimidation Practices
The means by which IS operates include the sending of spies and paying local informants before taking over territory, and then ruthlessly taking control, ruling by violent intimidation techniques-a page taken directly from the standard operating procedures of Saddam Hussein’s police state. This is a result of former
Iraqi Baathists intelligence officers having joined and lent their support and expertise to IS. Already before its establishment as a rogue state, IS had developed a very strong intelligence apparatus. It has now been revealed by Christopher Reuter in documents captured from an Iraqi national spy chief, Haji Bakr, that the security arm of IS was carefully organized, relying upon former Baathist experience with IS organized by and using the same secret intelligence gathering techniques as previously used by the Sadaam Hussein’s regime to instill fear in the targeted local populations.
According to documents captured at Haji Bakr’s residence, IS’ security division employed cadres sent out in advance of invasions to recruit local informants in order to collect and immediately apply intelligence to gain control the moment it decides to advance into new territory. This process includes: identifying the powerful families and individuals in a given area, finding their sources of income, identifying rebel brigades and their leaders by name, and learning about their Shariah violations so that on the basis of these they can be blackmailed if necessary.[249] Our informants provided many examples of how this security apparatus worked.
One informant, for example, explained how this IS strategy eased their entry into Raqqa: “When Daesh came to Raqqa, Jaysh al-Hur was in power, but Daesh took over for many reasons. First, Daesh sent small groups to establish themselves inside the city. Secondly, they sent suicide bombers of young boys, especially to the gates where Jaysh al-Hur had guards. This was very effective, as everyone feared the suicide bombers and it was very difficult to distinguish if an approaching child was a suicide bomber or not. Being unwilling to shoot a possibly innocent child, the sentries would run away and Daesh could enter. Lastly, Jaysh al-Hur began to realize it was too late to fight against Daesh-because they had established themselves by using cells already inside the city who began to explode things. So Jaysh al-Hur fighters left with hardly any fighting” (Abu Walid).
Talking about his personal experience, he recalled, “When they came to Raqqa they came to me and asked, ‘Why you don’t come with us? We work together to make an Islamic government. Why you don’t you help us?’ I answered, ‘Inshallah [God willing] after some time,’ but he won’t hear no. I knew if I said no, they will kill me, so instead I said, ‘Inshallah.’ Someone from IS comes and takes many photos of me. He writes reports of where I go and stay. They do this every one to three months” (Abu Walid).
Anyone can be subjected to mistreatment under IS. Indeed, the informants stated that if a fighter didn’t like a local person they could make a false accusation and order the person into Shariah court, or have them immediately punished, or even killed.
Torture
Having taken another page from Saddam Hussein’s manual of techniques of governance, torture is also a central part of the IS repertoire. One informant who had been part of Jabat al-Nusrah but who was hiding that fact recalls being put under interrogation when IS came to his region. “[They] took me by hand in iron cuffs, to torture me. They spread my arms wide and hung me by my forearms and wrists, held by the iron cuffs, from a steel bar. [i.e. he was hung there with his full body weight pulling down on him]. They left me there for around two hours. I had so much pain, and started to cry many times from the pain in my hands and my body. I cried and shouted. They did this again the next day and I cried and shouted again throughout the day and night” (Abu Walid). [This went on for thirteen days.]
Beheadings, crucifixions, torture and executions are such a common occurrence and well publicized in IS territory that everyone knows that life under IS is cheap and that not complying with their rules or wishes can bring a swift, harsh and dire result. Abu Walid recalled that during one of the days of being held and tortured, “I thought they want to cut my head, because the soldier who cuts throats came toward me. Then, I understood that I will die.” He continued, “The last day they took me again. This time they blindfolded me. They told me, ‘You know where we take you now.’ I answered, ‘No I don’t know!’ They said, ‘Now we take you out to kill you.’” Abu Walid was not killed however but intimidated into handing over his car, rifle and information they wanted from him. He was also coerced into joining IS’ Shariah training class and making his oaths of allegiance to IS.
Induction into IS
The process by which one is inducted into IS varies. However, according to our informants, everyone who joins is required to take a training course in Shariah law. These courses are organized for groups as large as fifty people, bringing together individuals with shared cultures and language (i.e. Syrians go to a different one than Westerners for instance). The Shariah courses vary in content and length, depending on the background and experience of students. Youth, for example, take a short ten-day course. Former fighters take a fifteenday course. From there, the prospective new IS members are put into military training which varies in length from two to four weeks, and is given in different languages depending on the composition of the group. Upon finishing each training session, the newcomers are invited (in fact heavily pressured) to make bay’ahs to IS.
Former Fighters
According to our informants, no one is forced to join IS as armed fighters—membership is voluntary. However, young men are heavily coerced by the circumstances they find themselves in. For instance, those who fought in militias other than IS, despite having a common enemy in the Assad regime, are immediately executed unless they find a way to show repentance. The few that are spared are invited to join the Islamic State but have to demonstrate loyalty and agree to renounce all past ties and swear their repentance for former “misdeeds”. This is done before a Shariah court referred to as tawbah after which they are issued a formal, written certificate of repentance.
One informant recalls being caught by IS and interrogated. They did not immediately realize he had been in Jabat al-Nusrah. He stated, “After a few days [following interrogation], they sent again for me [inside the prison] and asked, ‘Why you don’t come join ad-Dawlah [the State] with us and come for our training?’ I agreed because I know they will kill me if I don’t”. This young man, Abu Walid, took their Shariah course but did at first not enroll for military training. Instead he protested. “I have my family responsibilities, but I knew that eventually, if I didn’t work with them they would put me in a prison in Raqqa. I was afraid. After two months of them inviting me, I decided to escape. I know the area very well, so I took a motorcycle and came across the border to Turkey.”
Men coming from other militias were either killed or forced to go through a process of “forgiveness” or “repentance” in order to be eligible to join IS. One of them told us, “I was fighting for the Free Syrian Army before IS captured Tell Abyad [the Syrian town just across from the Turkish border city, Akçakale]. When they captured Tell Abyad, I fled to Turkey. [Later], I had people to talk to them and asked forgiveness so that I could go back to my village and family. They said they would forgive on the condition that I fight for them. When I went back, they detained me at the border, blindfolded my eyes and brought me before the Shariah judge for my trial, only then uncovering my eyes. The judge concluded, ‘You helped the infidels and because of this you are considered infidel as well. Now, ask forgiveness from Allah and promise us that you will never draw a weapon to the Muslims and pledge allegiance to the Caliph al-Baghdadi so that we can forgive you. Also, you have to help us whenever we need your assistance.’ I agreed and I was freed. However, this did not end there. They started to ask me to join the IS ideology classes [Shariah training]. I was forced to attend those classes for three months. This is their ideological preparation stage” (Abu Jamal).
Motivations and the Positive Benefits for Those Joining IS
Control of Resources
Because IS takes control of everything in a community they can be very good at incentivizing membership- particularly with young men who hope to be married. As one informant stated, “The IS guys speak with the youth about what they are doing to build an Islamic state. They tell them, ‘If you want to work we can help you and give you money. You can be married. We are the true Islam. We guarantee you. We are brothers, no problem.’ Like this they win trust and make many people to join them. They join for a loaf of bread.” Because of these factors, it was very easy for IS to recruit the youth inside Raqqa” (Abu Walid).
“If you do not fight for IS, you die from hunger as they would not feed or support you, or let you work. So, eventually, you either fight for them or die,” one informant stated. “I could stand six months before I was out of money and had to join them. If you fight for them, they pay two hundred US dollars per month, and also supply all your needs. So, you do not need to spend any money. Two hundred dollars is a lot more than a high-ranking judge can make in Syria today and equals to over sixty thousand Syrian pounds. When I joined, they told me I need to go to fight in Ramadi for a year and then I will be free to go anywhere in the Caliphate. They also give you a free house, furniture, all your needs in a house-even the money to purchase slave girls” (Abu Jamal).
Cash Rewards
According to our informants, IS is flushed with cash. One defector recalls one of the cadres involved in the oil sales tired of counting cash. He decided to weigh it instead to determine how much money he had taken in. Another showed us pictures on his phone of IS cadres lying around with bundles of cash strewn about. Cash payments were made as a reward to IS fighters for good “work”.
Learning About One’s Religion
Most of the IS defectors expressed gratitude for what they had learned in their Shariah training class-for finally learning more about Islam, after having been largely denied religious education under the Assad regime. “They taught us how to pray and taught us our religion. In Syria, the Sunni part of the country was not taught religion properly. We felt a vacuum filled. We hadn’t learned in school our real history and religion. Daesh filled an emptiness in us. We felt joy from this and anger at Assad” (Abu Walid). He added, “Many people under Assad don’t know how to pray properly. The people are very grateful to learn how to pray correctly.”
Embracing an Islamic Life
Our informants reminded us that as Sunni Arabs they were at first very pleased to be able to embrace a strict version of Islam. While none of them, looking back at their experience under IS, endorsed the violent enforcement techniques of IS, many expressed joy in embracing a strict Islamic course under IS. The minor in our sample said that he was so deeply brainwashed by the IS claims to be in possession of the “true Islam” that it took him a year after escaping to fully realize that they were misguided. He stated that he was first gratified when “They taught us how to pray, and how to perform zakat. They also stopped people from drinking and using drugs. That was all good.” He went on saying, “I liked the prayer and the fasting and the zakat [alms-giving] and the good things, that they didn’t let people drink, or take drugs or commit adultery and do blasphemous things. That made the country better. There were fewer people stealing” (Abu Shujaa).
Attaining Paradise
ISIS promotes the concept of sacrificing oneself and others in suicide missions as a form of “martyrdom” that they claim wins them all the rewards of Paradise. While Islam teaches the concept of forgiveness, belief alone does not guarantee salvation in the afterlife and Islam also promotes the concept of a horrific hell and damnation for anyone whose sins outweigh his or her good deeds on the Day of Judgment. Against this background, anyone who has sinned badly may be attracted to carrying out a “martyrdom” mission in order to gain eternal rewards. Our informants claim that the Shariah trainers are very good at selling the idea of “martyrdom” and that foreign fighters in particular often join IS to clean their slates. “Some people join IS in order to become ‘martyrs’ so that their past sins are forgiven. I spoke to one sheikh. He told me, ‘I am from Saudi Arabia. I was very rich and I had committed most of the sins. I thought that I had to do something big to be forgiven, so I left everything behind to fight here to cleanse my soul.’”
Fear of Worse Alternatives
A feeling of religious and cultural honor and a fear of life under the Assad regime as a worse alternative was also cited as an inducement to join by some of those we interviewed. Fearing that other groups would rape their women if they entered their territory, some of the strict IS practices concerning women were comforting at some level. As one informant answered our question, regarding why he joined IS? “They go talking to the people asking them, ‘How come you are living under Shia rule? This is degradation to live under the Shia.’ They taught us, ‘You consider yourselves as Muslims, but you do not practice and live it, so you are not Muslims. They taught us that all the others are murtads [infidels]. It was always, ‘You are either with us or not’, no grey areas. If you are not with them you cannot do business. They tell the guys, ‘If Assad’s army comes and you do not fight with us, they will take your car and rape your women. They will kill the men and rape your women.’ It’s true their soldiers did rape women so everyone is afraid and believes them. An older guy told us, Bassar’s soldiers came to a home, and told the father, ‘Send your daughter with us.’ Then they heard a gunshot. The father killed his own daughter, so they cannot rape her. Everyone knows that Bassar’s soldiers will rape anyone they find” (Abu Walid).
Process of Indoctrination by Charismatic Trainers
The Shariah training that IS provides serves to indoctrinate future cadres. Highly charismatic and knowledgeable IS teachers from Saudi Arabia and Jordan who are well trained in Islamic law, run the courses. Everyone in our sample reported that the trainers were kind, gentle, charismatic and very convincing.
Many stated that when they had doubts they always remembered what they had been taught in the Shariah class and how much they liked their trainer; that kept them going-despite serious doubts. Likewise many consulted their former trainers to discuss issues arising from contradictions between what IS said and IS did.
“ISIS preachers are well-educated and impressive. They persuaded me to be a ‘martyr’ in just three gatherings which lasted two hours each,” one informant stated (Abu Jamal - not his real name). It would appear that in terms of preparations for IS membership, the teachers inducted new IS cadres in ways similar to modern criminal gangs or as child soldiers are incorporated into paramilitary groups. One of those interviewed said that “At the third class, I declared that I was ready to be a suicide bomber as I was really affected by the preaching of the teacher, so that you can understand how well they choose their teachers. There were three hundred students like me. The classes lasted two hours per day. They usually lectured about the political problems Muslims are facing around the world and about how Muslims were assimilated and how their lands and wealth was imperialized. They spoke about how Bassar’s soldiers were raping our sisters and [that]we should be sending birth control pills to our sisters if we chose not to fight Bassar and others. Also of course they included ideological education, (Abu Jamal).
The first thing the Shariah instructors teach in their courses looks similar to first steps in cult practices - emphasizing the rule of “hear and obey”. They teach that under any circumstances, without any questioning, IS members must “hear and obey”. This is a must-members are obliged to obey and carry out the orders of all IS sheiks and emirs. This part of the process is presented as essential in ideology and the indoctrination process of “hearing and obeying” is presented as practicing holiness and keeping the order of Islam. Likewise failing to do so is taught to be threatening to authentic spirituality by claiming that not obeying the IS emirs is one of the greatest sins. Of course, added to this teaching are their sharp knives, they use to behead in public anyone who refuses to “hear and obey”.
In content, the IS Shariah training program generally follows the al-Qaida takfiri ideologies developed long before IS was created. It relies on the works of Ibn-i Tamiyyah, a thirteenth century scholar who was one of the founders of Salafist Islamic interpretations.[250] According to our informants, the trainers make use of a variety of Tamiyyah’s works, in addition to the book “Kitabu’t-Tevhid” which is presented as the main course book. Titled The book of the Unity and Unique Oneness of Allah, it was written by Muhammad-ibn-Abd-al- Wahhab, the eighteenth century Salafist scholar who stood at the cradle of present-day Wahhabism, the Saudi variant of Salafism.
Using these texts, trainers rely on twisted interpretations from the Holy Quran and from more or less well- known Hadiths, thereby making use of the cultural capital of Islam. Invoking in such a way values sacred to all participants, makes it difficult if not downright impossible for those undergoing such training to question what they are being taught by the trainers. The students’ belief in the inviolability of the Holy Quran, coupled with the powerful personalities of the teachers, makes them highly vulnerable to accepting the violent interpretations of Islam without questioning or challenging teachers and texts.
It is worth recalling that most Syrians, even university graduates, were never taught even the very basic features of Islam because the Assad regime controlled the educational systems. Therefore, for many of them, the knowledge they had about Islam before they came under the tutelage of IS was based upon deficient and incomplete narratives. This situation of spiritual emptiness, combined with a hunger to learn more about, and practice “true” Islam considerably eased the task of the IS Sheiks.
ISIS trainers instill in their students the idea that only IS possesses the “true Islam”, with everyone else being an apostate deserving death. “In the ten-day Shariah education course, they teach that all people not in IS are murtad [apostates]. All governments who do not support IS are murtad. They teach the students how to pray” (Abu Walid).
ISIS ideologues take a decidedly apocalyptic view of the future, teach their cadres that they are engaged in a cosmic battle where normal limits are shed as they are meant to defend and carry out the will of Allah. As one informant tells us, “Once I asked, why we don’t fight against Israel. The sheik told me that we have to first fight with the hypocrites and pretenders otherwise they will stab us in the back when we fight. He added that the last war will be in Halep Dabiq, once we win over the hypocrites” (Abu Jamal). This references Islamic apocalyptic prophesies of the End Times battle being fought in Dabiq, an area in Syria that IS has been sure to control.[251]
Following the practices of many cults, violent gangs and leaders of child soldiers, IS teachers require their students to carry out a barbaric act of violence against their enemies before graduating to become a fighter. Enemy prisoners are housed near the training sites for that very purpose. As one informant told us, “Graduation only happens when they feel a student is ready. At that point they demand that the student that is going to become a fighter cut off the head of a prisoner-to demonstrate that he is ready” (Abu Jamal).
Military Training, Weapons, & Battle Field Practices
“Everyone who becomes a fighter takes both Shariah and military training. It’s both military and Islamic training” (Abu Walid). These two courses—Shariah and military—are taught separately or combined into one (with the Shariah training happening after nightfall or during breaks in the daytime), depending on practicalities and the need of IS to move cadres forward into the battle space.
Military Training
As with Shariah training, IS cadres are organized and trained in military techniques in groups reflecting members’ nationalities and /or language. The military training can be as short as two weeks or take up to six weeks, depending on momentary needs for combat purposes.
“In military training, they teach them bombing and weapon tactics, fighting like an army and survival training” (Abu Walid). Particularly violence-prone individuals and those with psychopathic traits who take special pleasure in cruelty and infliction of pain are selected from among the trainees to become executioners. Others are chosen for intelligence work; they soon become feared by all the rest. The ‘Cubs of the Caliphate’; child soldiers have their own training camp and include boys as young as ten and eleven years of age. There the child boys receive military training. As many as they can persuade are talked into becoming suicide bombers, tasked with driving explosive-laden vehicles into enemy positions.
Weapons
A typical fighter is, according to our informants, equipped with, “one pistol-a Glock, a Colt, or a Smith and Wesson; one rifle-an M-16, or an AK-47; at least two hand grenades; a backpack with medical supplies, food and water; and at least five hundred bullets” (Abu Walid).
According to Abu Jamal, a former IS commander, “The weapons are coming from everywhere. But mostly we take our weapons from other groups and from the battles we win. We had obtained a lot of Bassar’s army warehouses as well. Bassar left all his weapons, including the tanks, to the PKK and PYD. We also took some of them.”
Some of our informants also claimed that IS receives, unlike any other groups in Syria or Iraq, new weapons arriving in wooden cases with nylon armor covers and slings. Abu Jamal claimed that he had seen unopened AK-47 cases full of brand new rifles, BKC (Bixi) machine guns, a variety of mortars, and even anti-tank and air missiles as IS cadres were unpacking and assembling the shipments, adding he did not know where they originated from.
Battlefield Practices
Local fighters who have families or wives live at home, except when engaged in fighting. They see their families frequently, according to those we talked to. Fighters leave the battlefield and go home every ten days to visit their families, we were told. “During the battle days he follows the orders of the leader. After fighting for ten days approximately he returns home for a week of rest with his family” (Abu Walid).
“The Daesh leaders are foreigners (non Syrian), [while] the soldiers are locals for the most part. There is no difference in how soldiers are treated between locals and foreigners. [But, the] Syrians do not like the foreign commanders” (Walid).
Nevertheless there is much loyalty to each other. “ISIS members support each other to death. The others are not like that” Abu Jamal stated. Likewise the fighters are not afraid of dying and in fact embrace “martyrdom” on the battlefield. As to IS’ military tactics, Abu Jamal told us “The strategy of IS before a battle is watching the group being targeted. “They would kill the top commander in an ambush before they attack in battle, so that the army or the group they are attacking would be without an experienced commander.” Executions are carried out on the battlefield. Unlike other IS operations that are based on Shariah practices, with investigations and with judges passing the final verdict, fighters bypass this. “Because they say they are at war, they do not need a trial—so they execute [their prisoners] instantly without waiting and consulting anyone” (Abu Jamal).
“During the Battle at the Al-Tabqa air base, the top commanders fled with a helicopter at night and afterwards. IS captured and killed almost seven hundred soldiers there. Almost all were killed via beheading,” an informant reported, showing us the videos of the beheadings he had still stored on his phone. “Two hundred fifty of them were taken to the cities to be executed in front of the people to spread fear, the rest were executed on the scene of the battle—during and afterward. The human blood from the executions ran like a river” (Abu Jamal).
ISIS cadres’ reputation for brutal executions, use of suicide bombers and fierce tactics have made many enemies cringe and withdraw in the face of IS fighters. “Thirty IS fighters won over four hundred Free Syrian Army fighters very easily in taking over the border gate across Akçakale,” Abu Jamal told us. Perhaps because there are few if any alternatives, after prison breaks, “Prisoners who were released by IS mostly join the group” (Abu Jamal).
Battlefield Administration of Psychopharmaca
Two of our informants discussed how drugs were used to motivate cadres. The child soldier who had served in a ‘Cubs of the Caliphate’ unit (Abu Shujaa) told us that children would be given drugs before they mounted their bomb-laden vehicles to conduct suicide attacks. Abu Said who had been an IS commander confirmed this.
Abu Said also detailed the battlefield use of a drug that appears to match the description of the amphetamine Captagon.[252] “When we were fighting against nizam in Ras al-Ayn, there were loud sounds of explosions all around me and I was very scared. There was this guy from IS, he looked at me and realized that I was scared. Asked if I was afraid, I said, ‘Yes I am really scared. He gave me a tablet. It was very bitter and brown in color. I swallowed it. In thirty minutes, I became a different man—as if I am a hero. I went into the battle very bravely to the very fronts alone. My friends told me to come back, but instead, I went forward, and said, ‘No, I want to die!’ I became so brave. I did not sleep afterward for three days. It gave me so much power. I felt as if I am indestructible and unbeatable. I went back home on the fourth day without sleeping-after having taken this tablet. I sat together with my family. Then I laid down for three to four minutes and I felt like I had not slept for years. At that moment, I could not move my arm and could not speak. I realized that it was because of the drug, so I did not take it again. They told me that I would not become addicted if I kept using this drug, but I didn’t. Many of the IS members use this drug. There are different varieties of it, some yellowish, some light brown.”
Foreign Fighters
ISIS currently attracts about one thousand new foreign fighters per month and already has a foreign fighter force estimated at twenty to thirty thousand-including some five thousand from Western Europe. Many of our informants had contacts with, and knowledge about, these foreign fighters. Abu Jamal, a former regional commander of IS, estimated that there are ten thousand IS fighters in Syria and twenty-five thousand in Iraq, with sixty percent of the fighters consisting of Iraqis and Syrians and the other forty percent being made up of foreign fighters.
The foreign fighters were seen as “true believers” by our informants who witness their dedication since they had given up everything to come and join IS. Abu Jamal recalls meeting one and hearing his story, “Once I took a French IS member to our truck while he was fleeing from the Kobani battle. The French IS fighter called the Arab IS fighters hypocrites and told me that they would not pray. ‘They are after money, not jihad,’ he said. He told me his story. After he converted to Islam, he flew with his wife and two children, to Istanbul as a tourist. From Istanbul he came to the border where he was instructed to meet his handler. The handler took him to a border village where they passed the border with the assistance of a smuggler. After their arrival and settling in, he was given Shariah courses for two months. His passport and phone were taken and destroyed. There was no Internet—it was not allowed. After Shariah training, he received military training for around a month and became a fighter” (Abu Jamal).
“The foreigners’ camp is located at the Tabqa Dam, which is around twenty-five miles away from Raqqa,” according to Abu Jamal. “ISIS has the control of this dam. All the foreigners arriving in Syria are transferred to the camp there. Based on the language of the foreigner fighter, IS sends sheikhs to their camp. After the ideological training, the trainees are then sent to military camp training for two months. The military camps training names are al-Hasakah Osama bin Laden Camp, al-Raqqa Zarqawi Camp, al-Raqqa 17th Battalion Camp and, for the boys between eight to seventeen, al-Shabaab Caliph Camp. The boys stay at this camp for three months for indoctrination. They mostly become preachers for IS. However, they also receive military training. In order to graduate from this camp, you have to cut the throat of a prisoner. The IS prisoners are kept in the Tabqa Dam area for this purpose” (Abu Jamal).
Many nationalities are represented among the foreign fighters. “I have seen people from the USA, the UK, Germany, France, Russia, Chechnya, China, Indonesia, Sri Lanka, Malaysia, Saudi Arabia, Tunisia, Algeria, Egypt, Palestine [limited numbers]), Lebanon, China, Azerbaijan and Uzbekistan,” Abu Jamal stated. He recalled that they were suspicious of the Russians. “We would consider them as agents because they were blonde, real Russian-blooded people and we would not trust them as they would mostly claim that they had been in the Russian Army and then converted to Islam and retired from their posts and came to fight for IS. They were also mostly military strategists and were making the plans for assaults and battles. They were effective on making strategic military decisions in IS.” Some of our informants wondered whether these Russians were plants (i.e. spies or agents), coordinating things with Assad’s forces.
Chechens and Kazaks are the battle-hardened fighters and thus form the elite special forces of IS, leading the regular cadres into battle. The two groups do not mix in battle. Many stories were told about Chechens executing prisoners in a very ruthless and brutal manner-seemingly numb to any feelings of horror.
One Serbian foreign fighter was pointed out by some of our informants as a particularly psychopathic executioner and more Serbians were seen as wanting to fulfill that role.
Regarding the Chinese foreign fighters, Abu Jamal recalls, “There is [a] Chinese village of IS fighters who speak fluent Qur’anic Arabic. There are around five hundred of them with their families. They are settled in a big village. I do not know how but they speak very fluent Arabic [Arabiyah al-fusha, according to him, which means, the most eloquent and Qur’anic Arabic language] as they are genuine Chinese people.” When asked if they could be Uyghur Turks, he said, “No, they are genuine Chinese people, I know Uyghurs”.
Each nationality has its particular reputation. Abu Jamal recalls that “the worst of IS are the Saudi fighters. They are very brutal and violent. Once during a campaign, there was a group of one hundred Saudi fighters. An American F-16 bombed them and around fifty died. They called for help, but were told to wait, and not to leave the stronghold. They however abandoned it. When their commander learned it he ordered that ten men be sent back to the IS command center. They were killed immediately as they had not listened to orders. The other forty Saudis, with their commanders, fled and joined al-Nusra.” Saudis and Jordanians tended to be well represented among the Shariah educators and judges. “The first judge of IS is from Saudi Arabia” (Abu Walid).
One informant told us a story that many of the others also referred to, “The foreign fighters are corrupt minded. For instance, one Tunisian guy wanted his two wives to be in bed with him together. His wives took him to court over this. He was sentenced and put in a truck for twenty days and paraded around.”
Many of our informants stated that Westerners who joined were already heavily indoctrinated in Salafi doctrine before arriving to IS. Unlike the Syrians, the Western cadres were, and generally remained throughout their time with IS, “true believers”. “They usually recruit from the West over the Internet,” Abu Jamal told us.
Western foreign fighters are kept separate from the ordinary Syrian fighters and given that they do not have a common language they cannot get to know each other well. However, our informants noted that Western recruits were obviously privileged in many ways above the regular Syrian cadres-often receiving homes, wives, female slaves and cars.
Porous Turkish Border
Turkey’s border with Syria runs as far as the Tigris. That the Turkish government illicitly if not openly supported the rebel movement in Syria is well known. Only recently has Turkey begun to control movement of IS cadres across its southern borders, following pressure from Western powers. Turkey is a member of both NATO and the OSCE and as such, its border forms an outer border of these two organizations. Likewise because of the highly porous boundary for people smuggling between Turkey and the Greek islands as well as between Syria and Turkey, Turkey has become a buffer zone for illegal migration into Europe. And as we saw in the November 13, 2015 terrorist attacks in Paris, Turkey has become important for controlling European IS fighters from moving freely back and forth between IS held territory and European capitals.
Along the southern border of Turkey, four cities—Sanliurfa, Gaziantep, Kilis, and Hatay—share this frontier. These towns have deep historical ties with Syria, and there are interactions with a spectrum of radical groups in Syria, including IS. The remaining border that southeastern Turkey shares with Syria faces down the cities of Mardin, Sirnak, Diyarbakir, and Hakkari. But this stretch is controlled by militants from the Kurdistan Worker’s Party (PKK) and the Kurdish Democratic Union Party (PYD).
The population of these four cities (i.e. Sanliurfa, Gaziantep, Kilis, and Hatay) is a blend of Kurdish and Arabic elements with local Turkmen populations inherited from the time when the Ottoman Empire ruled the entire region from Istanbul across Syria, Iraq, and Lebanon, and along the southern shore of the Mediterranean. Today, many Arabs and Kurds have relatives and family members across the border in Syria, and even today intermarriage across the border is still a common practice. So the historic and ongoing interaction of Arabs and Kurds across this often violent frontier stems not only from activities such as smuggling or illicit trafficking in drugs or refugees, but are also based on family ties, which may also be used to facilitate illegal activities along these routes. Lately, stretches of this border have also become a facilitator for the objectives of IS as well.
The financing that IS enjoys primarily from its sale of oil but also other “goods” means that the group is flush with cash which allows IS to pay smugglers and bribe border guards to gain easy entry into Turkey and to operate from there. “ISIS members have a lot of money, so they can rent a house in Turkey for operational purposes including to collect intelligence and use it for a maximum of ten days and then re-rent it again” (Abu Jamal).
“The smugglers do this for money. It usually costs two hundred US dollars per person to cross, depends on the situation. There is a coffee shop close to the border in Akçakale, anyone who wants to pass the border goes there to meet with the smugglers. You can see the PKK and IS members sitting there together. But for IS, the smugglers have to inform the IS handlers when they are assisting them passing the border from the other side. In the Akçakale at the Tell Abyad border gate, there is a middleman called the alligator. He handles everything in the name of IS. He is a very scary man. He works with the IS intelligence” (Abu Jamal).
With concerns that foreign fighters were using Turkey as route to slip into Syria and that extremist groups such as IS were using Turkey as a supply source and transit route, Turkish officials have in the past months cracked down on what previously was a relatively open border. The border has now been fortified with two hundred miles of trenches, fifty-five miles of barbed-wire fence. Armed Turkish troops who have been accused of shooting and killing at least thirty-one civilians who tried crossing into the country.[253] However, most of the fences or trenches have not arrived to Sanliurfa or mainly IS controlled parts of the border, making it quite possible for the IS members to still cross those sections of the frontier, although not as easily as during past years and until mid-2015.
Some of the cities in Northern Syria actually border twin cities in Turkey. For instance the Syrian city of Tel Abyad is directly across from the Turkish border city of Akçakale. Essentially the two run into each other. The division between them is a two-meter cyclone metal fence that smugglers can cut through or put blankets over the top late at night and thereby help people cross.
According to our informants, IS cadres still manage to penetrate the border. “Passing through the [Turkish] border is as easy as eating cheese,” one informant told us (Abu Jamal). IS illicit movement across the Turkish border is not limited to their cadres. According to Jamal, IS moved components for weapons from Turkey across the Akçakale border gate into Syria. “They acquired long, strong pipes along with a lot of fertilizer. The pipes and fertilizer along with LPG [liquid petroleum gas] tanks were used to make a kind of rocket in Raqqa. These rockets are named hell-fire balls and are more powerful than other rockets. We produced and used thousands of them. I know that the total is over eight thousand, as we had that many LPG tanks when we acquired the LPG tank factory. I do not know how they brought more tanks after that” (Abu Jamal).
Refugee Camp Involvement
Turkey currently has nearly two million Syrian refugees registered with UNHCR.[254] However the actual number of Syrian refugees in Turkey, according to many NGO’s, may be closer to three million as most of the Syrians entered Turkey illegally through borders that were open up until mid-2015.[255] Today, one can see Syrian panhandlers and beggars all around the country at any given time, especially in large cities like Istanbul, Ankara or Izmir but also in smaller cities in the West and central parts of Turkey.
Along the southern border of Turkey, a network of twenty-seven officially run refugee camps have been opened for Syrians and their population is growing rapidly according to the Deputy Prime Minister of Turkey.[256] There are five in Sanliurfa alone with around 150,000 refugees living in them. Some 25,000 Kurds also live in the Suruc refugee camp, almost all from Kobani. Another 30,000 refugees in the Akçakale refugee camp are mostly populated by Arabs, as the camp authorities carefully separate the two nationalities to avoid conflicts. As many as ten members of a family may live in a sixteen square meter tent, where meals, free medical service and medicine distribution, but also schooling are provided. Yet these camps may be serving more than one purpose.
Abu Jamal estimated that Akçakale Refugee Camp had approximately thirty thousand refugees, mostly Arabs. He said that in the Kobani battle it was found that many of the killed IS members were actually carrying Akçakale Camp ID’s on their body. He went on to state that there are around twenty quarters in the Akçakale Camp with each having it’s own mosque with its own Arabic imam or some other unofficial preacher. Jamal stated that some of them recruit for IS inside the camp. As a result young boys leave the camps to join IS. “These sheikhs preach that jihad is fard ayn [a mandatory individual responsibility] for every Syrian man according to Islam, as Syria is in war,” Abu Jamal declared. Likewise he insisted when we interviewed him that the IS recruiters pressure and threaten men to join without the camp authorities knowing they are doing so. “They ensure you that if you die in battle, that they will take care of your family. If you do not want to join IS then you have to flee the camp. They will not let you alone.”
Beyond their function of providing refuge for the people fleeing the violent battleground of Syria, the camps sadly, are also home to a contagious despair that can infect young boys in particular, those who prefer action to languishing unemployed, often fatherless, constantly looking back to Syria, while feeling devalued in a camp. Our informants told us several stories of young boys being talked into joining IS and then running away from their families. They all ended up dying- carrying out suicide missions. According to official Turkish policy, Syrians can remain in the camps as long as they do not cause trouble inside Turkey.
Including the camp population, over 467,000 Syrian refugees live in Sanliurfa according to records of the Turkish Ministry of the Interior [257]. Generally, those who are living outside of the camps are the more affluent ones as they have managed to flee with some resources or have relatives abroad, allowing them to rent houses and open businesses. In short, there is an already established population of Syrians in Sanliurfa, accounting now for a fifth of the population. This allows Syrian terrorists and criminals to blend in easily and to operate freely.
Humanitarian Aid
ISIS, like many other terrorist groups has figured out how to take advantage of humanitarian aid. One informant told us, “The humanitarian aid passing from Suruc to Kobani to aid the Kurdish people was mostly being sold to IS fighters, around two thousand truckloads. There are very few [civilian] people living in Kobani, as the people of Kobani did not go back. So, all those trucks loads of relief were mostly passed to IS. There were even explosives hid under the cement bags sent there,” (Abu Jamal).
Female Involvement
The Hisbah
According to information gained from our interviews, female members of IS do not become fighters. They can, however, join the hisbah (morality police), and many are quite brutal in this role. The female brigade of women in the hisbah was formed by IS in Raqqa after inhabitants there got fed up with male morality police beating and mistreating their women. At that time women were recruited into the hisbah to discipline and enforce morality rules for other women. This brigade is named al Ketibet-el Khansaa. There is also a foreigners’ hisbah formed of Western women. The Western group members carry AK-47s and they move around freely without taking orders from anyone and they have more power and authority than the regular women’s hisbah.
“The hisbah are like Shariah police. They steer people to mosques at prayer times” (Abu Jamal). “The al- Khansaa women [female morality police] go three at a time with a driver. They go into the market and into the village. They arrest and fine women who are out without niqaab and take some women even into the prison. [Niqaab is the Arabic style black dress now required for women under the control of IS where all parts of the body with the exception of the eyes are covered.] If there is a woman with no niqaab and no socks, or if a colorful garment under the niqaab is showing, they take her to court and she receives a sentence from ten to forty lashes” (Abu Walid). Most persons who fail to follow the strict rules of IS are punished in public, as an example to others. While males are lashed with their skin exposed, females are lashed through their clothing.
Marriage
ISIS uses the promise of marriage and female slaves as incentive for young men to join their ranks. One of our informants pointed out that marriage is a powerful inducement for some foreign fighters coming from poor regions of, for example Tunisia, a country that has had an inordinate number of foreign fighters joining IS. “The prospect of marriage also attracts youth. Turkish youth who are poor sometimes go to IS just to marry. They tell us, ‘I go there fight for them and get married’” (Abu Walid).
When IS controls all the jobs and resources in an area, the local Syrian young men can also be induced into joining IS simply by gaining the promise of marriage. Thus a very real reward of becoming an IS fighter is not only the imagined pleasure of the houris (virgins) in paradise if they are ‘martyred’ but the very real reward of ‘sex now’ with the wife he will be able to marry only if he has a salary-something IS membership makes possible. When an unmarried man takes his oath of allegiance to IS he is given a generous salary and a onetime marriage allowance. Foreign fighters who marry, or who are already married, are also provided with living quarters and in some cases a car, in addition to a fighter’s salary.
One informant told us how IS spoke in the first days of their arrival to the people in areas they conquered:, ‘All people come with us. We can give you a gun for fighting. Some people don’t have a wife—they can come with us. We will give you money, so you can marry. We will give you about two thousand dollars, so you can marry and a salary every month of two to three hundred US dollars per month. You need not be afraid. You are guaranteed if you die, we will take care of your family with money and food. ‘ They tell their recruits, ‘Come take our ten days Shariah course. After you can be in IS. You can have money, a gun, a car, after. Now you will be important’” (Abu Walid).
Our informants stated that Syrian women generally did not want to marry IS fighters but would when they believed that doing so would rescue their families from starvation. In this way Syrian women are enticed to marry local IS fighters by the money involved-to save their families.
Local women are also preyed upon by unscrupulous IS cadres who see them on the street and finding out where they live, go to put pressure upon their fathers to give them in marriage. One father was pressured in this manner and resisted it by quickly enlisting a cousin to marry his daughter—thereby taking her off the marriage market.[258]
Young women who come from abroad are expected to marry the IS cadres in a short span of time. These women are housed in a special “sisters house” and watched over by the hisbah until their marriages are arranged. According to one informant, “The hisbah has a hotel for the women who come as marriage partners, for the brides” (Abu Nasir).
Likewise there is, “a special marriage bureau that gives an order yes or no about marrying. A German for instance comes and says, ‘I want to get married.’ He goes first to the bureau to get permission. The women who come go to the Hizbah al-Khansaa and writes her name that she wants a husband. Then it is arranged between them. When they come to the marriage bureau it takes time. The young man is studied for four to six months by the bureau. They also make a study about the girl before they marry” (Abu Nasir). “There is a marriage bureau - services where they register the young women who come and match them with suitable IS cadres” (Abu Walid).
“There are many women coming from Tunis, Algeria etc. and they also want to marry. The Hisbah al- Khansaa arranges it. Many of the foreign girls don’t want to marry a Syrian fighter. They usually want to marry from their own group. For instance, the Europeans want to marry Europeans” (Abu Nasir).
Russia has been heavily involved in putting out pro-Assad and anti-rebel propaganda. One of their propaganda themes involved the spread of information about the supposed practice of “jihad al-nikah”, a practice which would be a total anathema to any Sunni Muslim, of a Sunni girl voluntarily offering herself to rebel fighters to be “married” repeatedly in a muta marriage (Shia temporary marriage)-essentially to serve as a prostitute. Our informants had also heard this piece of propaganda. They emphatically assured us that it is false before we even had a chance to ask about it. “We heard about jihad al-nikah - Muslim girls coming and giving their body as prostitutes for the mujahideen. It is absolutely not true’ (Abu Nisar).
In the case of widows of IS fighters up for remarriage, our informants stated that IS does not follow the normal Shariah practice of iddah—having the widow wait for a period of four months and ten days to ensure that she was not pregnant by her former husband. Instead IS widows are expected to remarry quickly, a practices that serve the needs of IS cadres who are often single and sexually motivated. When a fighter is killed in battle “his wife would wait for forty days and then get married to another fighter” (Abu Jamal).
It’s unclear how the women themselves feel about these practices. However, a Western woman writing under the pseudonym of Umm Layth, advises IS women to know their rights concerning widowhood-suggesting perhaps that rights that are not well known or if understood, are violated.[259]
One informant explains how the IS widows are cared for in the event of widowhood. “Under IS, women are kept very secluded. She can only see her husband or her brother. If her husband is killed as one of their fighters, a woman from IS comes to her after three days. For a widow they come bringing two hundred US dollars and they check on her regularly-to bring her money and ask whatever she needs” (Abu Walid).
One of our informants who had fought with Jabat al-Nusrah but was hiding that fact recalls that his wife was pressured the entire time he was held in interrogation (two weeks) and that IS cadres tried to get her to believe he was dead and to agree to marry them. “During this time while I was in prison, everyday they tell my wife I died” (Abu Walid).
Like the foreign fighters, IS women from the West are particularly privileged in IS and often live in nice homes and are given cars. They also are allowed more freedom.[260] A large group of western girls are, according to one of our informants, gathered each day in a big house in Raqqa, where they simply work on the Internet trying to recruit others. With their privileged lifestyles, these Western women seemed happy to the Syrian cadres who viewed them from afar. “Some Western women are very happy. They go and wander around outside with their weapons. After their husbands die, they remarry” (Nisar).
Female Slaves
ISIS has the practice of taking females captive-particularly the Yazidi women-and then selling or granting them as sexual slaves to IS cadres. IS ideologues argue that Islam allows for taking and distributing slaves as war booty, although many scholars would dispute this.[261]
While the press has reported on the practice of taking Yazidi women captive, our informants-one of them heavily involved-told us that it is not only Yazidi women who are preyed upon but also the Sunni and Shia wives of defeated enemy soldiers from the Iraqi army, the Free Syrian Army and from the Syrian regime forces.
“There are special places in Raqqa where they sell slaves,” one informant told us. “It is in the center of the city. It is only for Daesh. It’s in the building that was previously the government palace-the governor’s compound. Daesh took it over. There they have the hisbah al khansaa. They [female morality police] are in charge of everything about the slaves” (Abu Nasir).
The female slaves, known as “sabiyya”, are allowed only to the IS cadres. “Only a fighter can buy a slave woman. He needs documents from the emir or the governor of IS in that region granting permission to him to buy a slave and only after getting this permission he can go to hisbah and the slave market to buy slaves. They are sold by dollars. The minimum price is one thousand USD and the maximum is three thousand dollars. The slave girls can be sold between fighters, but only to the mujahideen, and there are rules, like you cannot take a mother and daughter slaves sexually at once, as you can only be with one of them [following Islamic incest rules]” (Abu Nasir).
Slaves are also given to the IS cadres as rewards-especially to the Westerners who do not have local wives. They reside with the fighter like a wife until he discards her, giving or selling her to another fighter. There are many rules governing the slave trade and how slaves ought to conduct themselves. For instance, “If the man wants to marry the slave he can. She can come in the presence of other men to serve chai [tea], coffee. She does not require a marham [male chaperone]. And the slave women have different rules in terms of covering themselves... When you have one, it’s like your wife. Although unlike wives, there is no limitation on the number you can have. If you are with her and have a child with her, and she becomes a Muslim, she can become your wife” (Abu Nasir). “The sheik had two slave girls,” one informant noted, indicating how higher social status conferred more rewards (Abu Jamal).
The Long Arm of IS
All of our informants feared discovery by active IS cadres and feared that IS could reach them inside Turkey and kill them for defecting-a fear greatly heightened after the double murder in Urfa, mentioned earlier.
Many had experiences of IS knowing about them inside Turkey. For instance Jamal reports, “ISIS has strong intel in Turkey as well. They knew whom I befriended while I was here in Akçakale.”
One subject reports that he only goes out to work in the field early and returns home after dark so that nobody sees him out. In this way he tries to ensure that he is not going to be caught by IS, and thereby ensure his own and his family’s safety. He also does not allow his child to play outside alone, fearing kidnap.
Disillusionment with IS
While most of our informants bought into the IS ideology either before or during their Shariah training and while they first had hopes that IS would bring about good for them, they became disillusioned when witnessing the mismatch between the words and deeds of IS. “In 2014, I realized that Daesh were liars. For instance, there was an IS guy who raped a woman, but got away with it” (Abu Walid).
Many were confused about how IS could sell oil to enemies such as the Assad regime, or why battles seemed to end suddenly with IS probably having made a behind the scenes deal with the other side. One former IS cadre reported about the confusion and disillusionment of his friend, Abdullah. “Once he told me, ‘I captured the Mursitpinar Border Gate several times [between Syrian Kobani and Turkish Suruc]; however, each time I was ordered to withdraw.’ He started to question IS in his mind, but not openly, otherwise they would kill him. Before he tried to flee, however, he was killed in an F-16 raid” (Abu Jamal).
One informant stated, “what I don’t like if someone did something wrong they tried to water board him, that I didn’t like.” He went on to add, “What I don’t like is that if they don’t like someone they just behead him. Or if a woman is not wearing hijab they bring someone to flog her, or if someone doesn’t believe they cut his ear” (Abu Shujaa).
All of our informants were tired of hypocrisy in IS noting that some were rapists, others themselves smoked, while punishing ordinary citizens for smoking, etc. “I have seen IS members go to pray without ablution” (Abu Jamal). Our informants found the IS cadres practice of quickly remarrying widows rather than allowing them to observe the normal Islamic interval before being re-married [iddah] both disgusting and wrong.
All our informants also grew disgusted by the constant stream of executions and the cruel pleasure that some IS cadres appeared to have when beheading and killing others. “There is a well by the name of Hute. There they cover the eyes of the prisoners and tell them, ‘You are free now, just walk now, but don’t open your eyes.’ They walk and fall into the well. It smells horrible because of all the corpses inside the well. I know that over three hundred people were thrown into that well.”
Our informants hoped that they could get rid of the Assad regime but now see all the death and destruction that came with IS. One informant noted that, “when you go around the country, you do not see youth in the villages. They are either fighting for IS, dead, or fled so as not to have to fight for IS.”
According to our informants, it is not only the defectors, but also ordinary Syrians as well who are disillusioned with the false claims and unfulfilled promises of IS. “Everybody in Syria doesn’t like IS now. When a fighter goes out to battle they say they hope he doesn’t come back” (Abu Walid).
One informant told us about how people began to understand that IS would not serve their needs, “But after some time, in 2014, people feel that IS is not good, but bad. Why? Because what they promised to the people, they did not keep. Where is this freedom they promised us?” (Abu Walid).
Our informants felt that many locals joined IS partly out of a hope in the proclaimed IS Caliphate and out of respect for their fighting power - they hoped that IS would help them achieve real freedom, but that as time wore on most joined IS out of desperation and hunger. One of those we interviewed stated that “now people join only for food” and that most have grown disillusioned with IS. “The few people who join now do so only because they need to eat. They are the ones who don’t have work. The rest try to escape to Turkey or Lebanon, or go by sea” (Abu Walid).
Defecting from IS
“If someone is caught fleeing from IS, he is killed immediately”, Abu Jamal stated. He mentioned the case of a fifteen-year-old Turkish fighter who wanted to quit serving IS. “He met with his father at the border gate in Akçakale. His father did not want to let him return [to the fighters] but the boy said through tears to his father, ‘They will kill me here right now, if I do not return with them now.’ Suddenly there were fifteen fighters who emerged out of the shadows around the young man to ensure that he wasn’t going to return home with his father.”
Most of our informants escaped IS by paying smugglers to get them across the Turkish border. Choice of one’s smuggler is of paramount importance as “all the smugglers are forced and paid to inform about IS members who are fleeing. The only way to ensure safe passage is to bribe the smuggler in high amounts, or he will inform IS and you will be killed instantly. Also there are several checkpoints. If you are caught by IS at the checkpoints, you also are immediately killed” (Abu Jamal).
Various authors have written about the importance of distinguishing between deradicalization and disengagement.[262] In the case of the defectors who spoke to us, all of them deradicalized, in the sense that they became totally and completely disaffected with IS and its extremist ideology. However, this process was not always completed at the moment they decided to leave IS behind-disengaging from the group. Abu Shujaa, for instance, told us that he continued to be a “true believer” in the Islamic State and its apocalyptic vision for more than one year, despite having deciding to escape from the ruthless terrorist regime which had fed him with End Times visions
Scott Atran writes about the confused state of “true believers” and their difficulty of leaving a group once one has bought into their version of sacred values which are not open to negotiation.[263] Indeed all of our informants felt that IS had deepened their understanding of Islam and they were grateful for having learned how to pray properly and were given a chance to learn more about Islam. For them giving up IS did not mean giving up their newfound deeper understanding of Islam and its practices. In fact, those things were sacred and non-negotiable for them. However, the deep hypocrisy of the IS cadres and their violent and brutal treatment of women, civilians and of other IS members convinced them that while they would not abandon their newly learned Islamic beliefs, they could walk away from IS.
In a study of open source reports of fifty-eight IS defectors, Peter Neumann, director of the International Centre for the Study of Radicalisation and Political Violence (ICSR) in London, teased out four themes among the reasons they gave for defecting.[264] One was the extent of fighting with other Sunni rebel groups and that “toppling the Assad regime didn’t seem to be a priority”. Our informants echoed the latter part of this concern. Neumann also referred to “the leadership’s obsession with ‘spies’ and ‘traitors’ as being a negative for them. This was true in our sample as well. A second theme was one of disillusionment and outrage with the group’s brutality, especially toward civilians. Our sample concurred on this as well, although our subjects-unlike Neumann’s media-based cases, showed compassion for the suffering of Yazidis and other minorities targeted by IS. The third narrative noted by Neumann was corruption in the group and special privileges granted to foreign fighters. Our sample also complained about corrupt and evil practices by IS members and noted that the foreign fighters were indeed privileged although the latter did not seem to cause them much concern. A fourth narrative identified by Neumann was that life under the Islamic State was harsh and disappointing. Our subjects were indeed disappointed that life in Syria did not improve and freedoms they had been willing to fight for did not materialize under IS.
Warnings to those Westerners Who Might be Attracted to IS
All of our informants felt very strongly that IS is an evil organization, one that others should not join. All of them were more than happy to make a strong statement to their own people-fellow Syrians-and to potential foreign fighters from the West, warning them about the evils of IS and telling them that under no circumstances should they join IS. They made statements such as “ISIS is not helping the Syrian people”, “Don’t come here, you won’t be able to leave,” “They are brutal, horrible rapists,” “This is not the true Islam and not the Islamic State,” “Don’t be fooled, they are liars.”
Referring to Islamic scriptures about a renegade tribe in the times of the Prophet that also practiced takfir [excommunication], Abu Walid stated, “They are the Khawarij tribe. I believed when they came to Raqqa that they are not good. They kill anybody from us, just like the Khawarij did. They existed during those times the same [in the times of the Prophet Mohammad]—with black clothes and black flags. Our scriptures warn us, ‘When you see them don’t follow them.’”
About the Authors: Anne Speckhard, Ph.D. is Director of the International Center for the Study of Violent Extremism (ICSVE) and also serves as Adjunct Associate Professor in the Department of Psychiatry, Georgetown University Medical School. She can be reached at at <Aspeckhard@AnneSpeckhard.com>.
Ahmet S. Yayla, Ph.D. is Professor and Chair of the Department of Sociology, Harran University, Osmanbey, Sanliurfa, Turkey. He is currently on leave as a Research Fellow at the ICSVE in Washington, D.C.and can be reached at <ahmetsyayla@gmail.com>.
Acknowledgment: The first author thanks Visiting Assistant Professor Allison McDowell Smith for her work in support of the project.
III. Resources
Bibliography: Homegrown Terrorism and Radicalisation
Compiled and selected by Judith Tinnes
[Bibliographic Series of Perspectives on Terrorism - BSPT-JT-2015-6]
Abstract
This bibliography contains journal articles, book chapters, books, edited volumes, theses, grey literature, bibliographies and other resources on homegrown terrorism and radicalisation. Though focusing on recent literature, the bibliography is not restricted to a particular time period and covers publications up to the middle of November 2015. The literature has been retrieved by manually browsing more than 200 core and periphery sources in the field of terrorism studies. Additionally, full-text and reference retrieval systems have been employed to expand the search.
Keywords: bibliography; resources; literature; homegrown terrorism; domestic terrorism; homegrown radicalisation; national security
NB: Publications focusing on Lone Wolf Terrorism have been largely excluded as the topic has been covered in a previous bibliography compiled by Eric Price. All websites were last visited on 21.11.2015. - See also Note for the Reader at the end of this literature list.
Bibliographies and other Resources
Andrusyszyn, Greta H. (2009, December): Domestic. In: Terrorism: A Selected Bibliography. Carlisle: U.S. Army War College Library, 17-18. URL: http://www.carlisle.army.mil/library/bibs/terror09.pdf
EurActiv (2015, February): From 9/11 to Charlie Hebdo: The EUs Response to Terrorism. URL: http://www. euractiv.com/sections/eu-priorities-2020/911-charlie-hebdo-eus-response-terrorism-311264
EUROPOL (2008, April-): EU Terrorism Situation & Trend Reports (TE-SAT). URL: https://www.europol. europa.eu/latest publications/37
Fairchild, Halford H. (2015, Fall): An Annotated Bibliography on Domestic Terrorism. URL: http://bernard. pitzer.edu/~hfairchi/courses/Fall%202015/Sem%20Social/Domestic%20Terrorism%20Bib%20090115.pdf
King’s College London (2015): Homegrown Radicalisation and Counter-Radicalisation in Western Europe and North America. (7SSWM053 Reading List). URL: https://kcl.rl.talis.com/lists/A176385C-490D-2FA1-3244- DB0AD8CEC082.html
Scheinfeldt, Tom et al. (2002-): The September 11 Digital Archive: Saving the Histories of September 11, 2001. URL: http://911digitalarchive.org
Stone, Amie (2014, July): Homeland Security: A Selected Bibliography. (U.S. Army War College Library Bibliography). URL: http://www.carlisle.army.mil/library/bibs/Homeland Security 2014.pdf
TSEC: The Terrorism and Security Experts of Canada Network (2014, May-): URL: http://tsecnetwork. blogspot.de
UK Web Archive (2005-): London Terrorist Attack 7th July 2005. URL: http://www.webarchive.org.uk/ukwa/ collection/100757/page/1
U.S. Department of State (2015): Country Reports on Terrorism 2014. URL: http://www.state.gOv/j/ct/rls/ crt/2014/index.htm
Books and Edited Volumes
Alexander, Yonah (2010): Terrorists in our Midst: Combating Foreign-Affinity Terrorism in America. Santa Barbara: Praeger Security International.
Alexander, Yonah; Myers, Kenneth A. (Eds.): Terrorism in Europe. (Routledge Library Editions: Terrorism and Insurgency). Abingdon: Routledge. (Original work published 1982)
Amghar, Samir; Boubekeur, Amel; Emerson, Michael (Eds.) (2007): European Islam: Challenges for Public Policy and Society. (e-Book). Brussels: Centre for European Policy Studies (CEPS). URL: http://www.ceps.eu/ publications/european-islam-challenges-society-and-public-policy
Argomaniz, Javier; Bures, Oldrich; Kaunert, Christian (Eds.) (2015): EU Counter-Terrorism and Intelligence: A Critical Assessment. Abingdon: Routledge.
Associated Press, The (2015): The Boston Marathon Bombing: The Long Run from Terror to Renewal. New York: Author.
Baker, Abdul Haqq (2011): Extremists in our Midst: Confronting Terror. (New Security Challenges).
Basingstoke: Palgrave Macmillan.
Beckman, James (2007): Comparative Legal Approaches to Homeland Security and Anti-Terrorism. (Homeland Security Series). Aldershot: Ashgate.
Bell, Stewart (2005): The Martyr’s Oath: The Apprenticeship of a Homegrown Terrorist. Mississauga: Wiley & Sons Canada.
Berger, J. M. (2011): Jihad Joe: Americans who Go to War in the Name of Islam. Washington, DC: Potomac Books.
Bleich, Erik (Ed.) (2010): Muslims and the State in the Post-9/11 West. Abingdon: Routledge.
Borgeson, Kevin; Valeri, Robin (2009): Terrorism in America. Sudbury: Jones and Bartlett.
Botha, Anneli (2008): Terrorism in the Maghreb: The Transnationalisation of Domestic Terrorism. Pretoria: Institute for Security Studies.
Charvat, J. P. I. A. G. (Ed.) (2012): Homeland Security Organization in Defence against Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 97). Amsterdam: IOS Press.
Chase, Alston (2003): Harvard and the Unabomber: The Education of an American Terrorist. New York: W. W. Norton.
Clarke, James W. (2012): Defining Danger: American Assassins and the New Domestic Terrorists. (New ed.). New Brunswick: Transaction Publishers.
Cook, Alethia (2009): Emergency Response to Domestic Terrorism: How Bureaucracies Reacted to the 1995 Oklahoma City Bombing. New York: Continuum.
Coolsaet, Rik (Ed.) (2011): Jihadi Terrorism and the Radicalisation Challenge: European and American
Experiences. (2nd ed.). Farnham: Ashgate.
de Koning, Martijn; Wagemakers, Joas; Becker, Carmen (2014): Salafisme: Utopische idealen in een weerbarstige praktijk. Almere: Parthenon.
Emerson, Steven; Investigative Project on Terrorism, The (2006): Jihad Incorporated: A Guide to Militant Islam in the US. New York: Prometheus Books.
Foley, Frank (2013): Countering Terrorism in Britain and France: Institutions, Norms and the Shadow of the Past. Cambridge: Cambridge University Press.
Forest, James J. F. (Ed.) (2015): Essentials of Counterterrorism. (Praeger Security International Textbooks).
Santa Barbara: Praeger Security International.
Forest, James J. F.; Howard, Russell D.; Moore, Joanne C. (2013): Homeland Security and Terrorism: Readings and Interpretations. (2nd ed.). New York: McGraw-Hill.
Gage, Beverly (2009): The Day Wall Street Exploded: A Story of America in its First Age of Terror. Oxford: Oxford University Press.
Gest, Justin (2010): Apart: Alienated and Engaged Muslims in the West. New York: Columbia University Press.
Gonzalez-Perez, Margaret (2008): Women and Terrorism: Female Activity in Domestic and International Terror Groups. (Contemporary Terrorism Studies). Abingdon: Routledge.
Gumbel, Andrew; Charles, Roger G. (2012): Oklahoma City: What the Investigation Missed - And why it still Matters. New York: William Morrow.
Haberfeld, M.R.; von Hassell, Agostino (Eds.) (2009): A New Understanding of Terrorism: Case Studies, Trajectories and Lessons Learned. New York: Springer. DOI: http://dx.doi.org/10.1007/978-1-4419-0115-6
Hassaine, Reda; Barling, Kurt (2014): Abu Hamza: Guilty: The Fight against Radical Islam. Faringdon: Redshank Books.
Hennebry, Jenna; Momani, Bessma (Eds.) (2013): Targeted Transnationals: The State, the Media, and Arab Canadians. Vancouver: UBC Press.
Herridge, Catherine (2011): The Next Wave: On the Hunt for Al Qaeda’s American Recruits. New York: Crown Forum.
Hesterman, Jennifer L. (2015): Soft Target Hardening: Protecting People from Attack. Boca Raton: CRC Press.
Hillebrand, Claudia (2012): Counter-Terrorism Networks in the European Union: Maintaining Democratic Legitimacy after 9/11. Oxford: Oxford University Press.
Hoffman, Bruce; Reinares, Fernando (Eds.) (2014): The Evolution of the Global Terrorist Threat: From 9/11 to Osama bin Laden’s Death. (Columbia Studies in Terrorism and Irregular Warfare). New York: Columbia University Press.
Husain, Ed (2007): The Islamist: Why I Joined Radical Islam in Britain, what I Saw Inside and why I Left.
London: Penguin Books.
Katz, Samuel M. (2005): Jihad in Brooklyn: The NYPD Raid that Stopped America’s First Suicide Bombers. New York: New American Library.
Kellner, Douglas (2008): Guys and Guns Amok: Domestic Terrorism and School Shootings from the Oklahoma City Bombing to the Virginia Tech Massacre. (Radical Imagination Series). Boulder: Paradigm Publishers.
LaFree, Gary; Dugan, Laura; Miller, Erin (2015): Putting Terrorism in Context: Lessons from the Global Terrorism Database. (Contemporary Terrorism Studies). Abingdon: Routledge.
Lambert, Robert (2011): Countering Al-Qaeda in London: Police and Muslims in Partnership. London: Hurst.
Leiken, Robert S. (2012): Europe’s Angry Muslims: The Revolt of the Second Generation. Oxford: Oxford University Press.
Levin, Jack (2006): Domestic Terrorism. (The Roots of Terrorism). New York: Chelsea House.
Marsh, Steve; Rees, Wyn (2012): The European Union in the Security of Europe: From Cold War to Terror War.
Abingdon: Routledge.
Morag, Nadav (2011): Comparative Homeland Security: Global Lessons. Hoboken: Wiley.
Neighbour, Sally (2009): The Mother of Mohammed: An Australian Woman’s Extraordinary Journey into Jihad.
Carlton: Melbourne University Press.
Nesser, Petter (2015): Islamist Terrorism in Europe. London: Hurst.
Neumann, Peter R. (2008): Joining al-Qaeda: Jihadist Recruitment in Europe. (The Adelphi Papers, Vol. 48, Iss.
399). Abingdon: Routledge.
Pantucci, Raffaello (2015): “We Love Death as You Love Life”: Britain’s Suburban Terrorists. London: Hurst.
Pargeter, Alison (2008): The New Frontiers of Jihad: Radical Islam in Europe. London: I.B. Tauris.
Pastor, James F. (2010): Terrorism and Public Safety Policing: Implications for the Obama Presidency. Boca Raton: CRC Press.
Pick, Thomas M.; Speckhard, Anne; Jacuch, Beatrice (2009) (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press.
Pisoiu, Daniela (2012): Islamist Radicalisation in Europe: An Occupational Change Process. (Political
Violence). Abingdon: Routledge.
Pisoiu, Daniela (Ed.) (2014): Arguing Counterterrorism: New Perspectives. (Routledge Critical Terrorism
Studies). Abingdon: Routledge.
Posiuszna, Elzbieta (2015): Environmental and Animal Rights Extremism, Terrorism, and National Security.
Waltham: Butterworth-Heinemann.
Post, Don E. (2005): A Patriotic Nightmare: A Tale of Domestic Terrorism. Santa Fe: Sunstone Press.
Poynting, Scott; Whyte, David (Eds.) (2012): Counter-Terrorism and State Political Violence: The “War on Terror” as Terror. (Critical Terrorism Studies). Abingdon: Routledge.
Rabasa, Angel; Benard, Cheryl (2015): Eurojihad: Patterns of Islamist Radicalization and Terrorism in Europe. New York: Cambridge University Press.
Radu, Michael (2009): Europe’s Ghost: Tolerance, Jihadism, and the Crisis in the West. New York: Encounter Books.
Ranstorp, Magnus (Ed.) (2010): Understanding Violent Radicalisation: Terrorist and Jihadist Movements in Europe. (Political Violence). Abingdon: Routledge.
Rapoport, David C. (Ed.) (2006): Terrorism: Critical Concepts in Political Science: Vol. 3: The Third or New Left Wave. Abingdon: Routledge.
Rapoport, David C. (Ed.) (2006): Terrorism: Critical Concepts in Political Science: Vol. 4: The Fourth or
Religious Wave. Abingdon: Routledge.
Sageman, Marc (2008): Leaderless Jihad: Terror Networks in the Twenty-First Century. Philadelphia: University of Pennsylvania Press.
Said, Behnam T.; Fouad, Hazim (Eds.) (2014): Salafismus: Auf der Suche nach dem wahren Islam. Freiburg im Breisgau: Herder.
Schauble, Martin (2011): Black Box Dschihad: Daniel und Saed auf ihrem Weg ins Paradies. Munchen: Carl Hanser.
Schauble, Martin (2011): Dschihadisten: Feldforschung in den Milieus: Die Analyse zu “Black Box Dschihad”. (Schriftenreihe Politik und Kultur, Vol. 12). Berlin: Hans Schiler.
Schirra, Bruno (2014): ISIS: Der globale Dschihad: Wie der „Islamische Staat“ den Terror nach Europa tragt.
Berlin: Econ.
Simcox, Robin et al. (2011): Islamist Terrorism: The British Connections. (Rev. ed.). London: Henry Jackson Society, Centre for Social Cohesion.
Southers, Erroll (2013): Homegrown Violent Extremism. Amsterdam: Anderson Publishing.
Speckhard, Anne; Shaikh, Mubin (2014): Undercover Jihadi: Inside the Toronto 18: Al Qaeda Inspired, Homegrown, Terrorism in the West. McLean: Advances Press.
Spencer, Robert (2014): Arab Winter Comes to America: The Truth about the War We’re in. Washington, DC: Regnery Publishing.
Storm; Morten; Cruickshank, Paul; Lister, Tim (2014): Agent Storm: My Life inside al-Qaeda. New York: Atlantic Monthly Press.
Temple-Raston, Dina (2007): The Jihad Next Door: The Lackawanna Six and Rough Justice in the Age of Terror. New York: PublicAffairs.
Thomson, David (2014): Les Frangais jihadistes. Paris: Les Arenes.
Vohryzek-Bolden, Miki; Olson-Raymer, Gayle; Whamond, Jeffrey O. (2001): Domestic Terrorism and Incident Management: Issues and Tactics. Springfield: Charles C. Thomas.
Waldmann, Peter (2009): Radikalisierung in der Diaspora: Wie Islamisten im Westen zu Terroristen werden.
Hamburg: Murmann.
Watts, Clint (2012, August): Radicalization in the U.S. beyond al Qaeda: Treating the Disease of the Disconnection. (FPRI E-Books). Philadelphia: Foreign Policy Research Institute (FPRI). URL: http://www. fpri.org/articles/2012/08/radicalization-us-beyond-al-qaeda
Welsh-Huggins, Andrew (2011): Hatred at Home: Al-Qaida on Trial in the American Midwest. Athens: Swallow Press.
Wiktorowicz, Quintan (2005): Radical Islam Rising: Muslim Extremism in the West. Lanham: Rowman & Littlefield.
Wright, Stuart A. (2007): Patriots, Politics, and the Oklahoma City Bombing. (Cambridge Studies in Contentious Politics). New York: Cambridge University Press.
Theses
Banez, Justin D. (2010, December): The Internet and Homegrown Jihadist Terrorism: Assessing U.S. Detection Techniques. (Master’s Thesis, Naval Postgraduate School, Monterey, United States). URL: http://www.dtic.mil/ cgi-bin/GetTRDoc?AD=ADA536371
Berkebile, Richard Evan (2012, December): Causes of Domestic Terrorism: 1970-2010. (Doctoral Thesis, University of Missouri-Columbia, Columbia, United States). URL: http://hdl.handle.net/10355/16521
Caraig, Joanna Marie C. (2010, May): The Human Security Act of 2007 of the Philippines: Assessing the Law’s Compliance with International Human Rights while Countering Terrorism. (Master’s Thesis, University of Oslo, Oslo, Norway). URL: https://www.duo.uio.no/handle/10852/22869
Chowanietz, Christophe (2009, June): Politics in Extraordinary Times: A Study of the Reaction of Political Parties and Elites to Terrorism. (Doctoral Thesis, University of Montreal, Montreal, Canada). URL: https:// papyrus.bib.umontreal.ca/xmlui/handle/1866/3716
Coar, Kristen Rose (2013, Summer): Islamist Radicalization in the United States and the Influence of Western Jihadist Ideologues. (Master’s Thesis, San Diego State University, San Diego, United States). URL: http://hdl. handle.net/10211.10/4763
DeFoster, Ruth Maku (2010, May): Domestic Terrorism on the Nightly News. (Master’s Thesis, University of Minnesota, Minneapolis, United States). URL: http://conservancy.umn.edu/bitstream/93028/1/DeFoster Ruth May2010.pdf
de Roy van Zuijdewijn, Jeanine H. (2014, January): Fearing the Western Muslim Foreign Fighter: The Connection between Fighting the Defensive Jihad and Terrorist Activity in the West. (Master’s Thesis, Utrecht University, Utrecht, The Netherlands). URL: http://dspace.library.uu.nl:8080/handle/1874/290146
Everly, Macklin Keith (2014): Multicultural Public Policy and Homegrown Terrorism in the European Union. (Master’s Thesis, Wright State University, Dayton, United States). URL: http://rave.ohiolink.edu/etdc/ view?acc num=wright1409088787
Frisk, Daniel (2014, May): Poor Choices: An Empirical Study of Terrorism in Europe during the Economic Crisis. (Master’s Thesis, Swedish National Defence College, Stockholm, Sweden). URL: http://fhs.diva- portal.org/smash/record.jsf;jsessionid=os-349ymycpqcY61vY w4dMUgUFPIlcSOWRSqAOk.diva2- search8?pid=diva2%3A732785&dswid=4309
Ghatak, Sambuddha (2014, May): Challenging the State: Evaluating the Effects of Uneven Distribution of Public Goods, Economic Globalization and Political Openness on Domestic Terrorism. (Doctoral Thesis, University of Tennessee, Knoxville, United States). URL: http://trace.tennessee.edu/utk graddiss/2692
Green, David Benjamin (2010, November): The Role of Local Law Enforcement in Counterterrorism. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: https://repository.library.georgetown. edu/handle/10822/553502
Hayne, Spencer O. (2010, November): Borderless World, Boundless Threat: Online Jihadists and Modern Terrorism. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://pqdtopen. proquest.com/pqdtopen/doc/818725727.html?FMT=ABS&pubnum=1483143
Heller, David E. (2010, September): Designating Domestic Terrorist Individuals or Groups. (Master’s
Thesis, Naval Postgraduate School, Monterey, United States). URL: http://calhoun.nps.edu/bitstream/ handle/10945/5213/10Sep Heller.pdf
Holtgraves, Lindsey (2012): The Politics of Identity: The Roots of Radicalization and Home-Grown Terrorism amongst Second and Third Generation Immigrants in Europe. (Master’s Thesis, University of North Carolina at Chapel Hill, Chapel Hill, United States). URL: https://cdr.lib.unc.edu/record/uuid:65b0a5f0-3ba1-4a2e-ab4a- 0f7ac37ecc41
Huffman, Alexia O. (2011, April): Homegrown Terrorism in the United States: Comparing Radicalization Trajectories in Britain and America. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://hdl.handle.net/10822/553516
Irwin, Travis Shane (2010, August): Social Structure and Culture: Applying Cross-National Indicators of Criminal Violence to Domestic Terrorism. (Master’s Thesis, Southern Illinois University Carbondale, Carbondale, United States). URL: http://opensiuc.lib.siu.edu/theses/333
Kabatoff, Mathew Alexander Yuri (2010): Subject to Predicate Risk, Governance and the Event of Terrorism within Post-9/11 U.S. Border Security. (Doctoral Thesis, London School of Economics and Political Science, London, United Kingdom). URL: http://etheses.lse.ac.uk/496
Kagioglidis, Ioannis (2009, September): Religious Education and the Prevention of Islamic Radicalization: Albania, Britain, France and the Former Yugoslav Republic of Macedonia. (Master’s Thesis, Naval Postgraduate School, Monterey, California). URL: https://calhoun.nps.edu/handle/10945/4561
Kaupa, Clemens (2009, December): The Multi-Causal and Asynchronous Development of Terrorism Laws in Germany from the 1970 s to the Present. (Diploma Thesis, University of Vienna, Vienna, Austria). URL: http:// othes.univie.ac.at/7963
King, Michael (2012, May): The Radicalization of Homegrown Terrorists: A Social-Personality Model.
(Doctoral Thesis, McGill University, Montreal, Canada). URL: http://digitool.library.mcgill.ca/R/?func=dbin- jump-full&object id=110446&local base=GEN01-MCG02
Lee, Belinda Yee-Wah (2012, April): Homegrown Islamic Extremism: Three Indicators of a U.S.- Targeted Attack. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://hdl.handle. net/10822/557664
Love, Karen (2009, April): From Deprivation to Detonation: Identity, Political Deprivation and Homegrown Terrorism in the United Kingdom. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://hdl.handle.net/10822/553267
Lundestad, Ingrid (2008, Spring): Strategies of Engagement: A Study of U.S. National Security Strategies from the End of the Cold War to the War on Terrorism and their Implications for the Role of NATO. (Master’s Thesis, University of Oslo, Oslo, Norway). URL: http://urn.nb.no/URN:NBN:no-19686
Lypka, Andrea (2011, June): Framing 10/12 and 3/11 in American and European News. (Master’s Thesis, University of South Florida, Tampa, United States). URL: http://scholarcommons.usf.edu/etd/3222
Mabe, Matthew Steven (2013, April): Inciting Violent Jihad: Understanding the Impact and Appeal of EnglishSpeaking Radical Islamic Ideologues on International Terrorism. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://hdl.handle.net/10822/558337
Mah, Richard (2014, Fall-Winter): Information-Sharing for Counter-Terrorism in Canada after 9/11: Issues in the Administrative Coordination of Multi-Agency Intelligence: A Comparative Study between Canada, the UK and Australia. (Master’s Thesis, University of Victoria, Victoria, Canada). URL: http://hdl.handle. net/1828/5862
Mason, Jonathan D. (2007): The Influence of the European Commission Data Privacy Directive on Third Countries and the Passenger Name Record Controversy. (Master’s Thesis, University of Florida, Gainesville, United States). URL: http://ufdc.ufl.edu/UFE0021477/00001
Mayer, Tamara M. (2009, December): Islam in America: Why U.S. Muslims are less Likely to Radicalize than their European Counterparts. (Master’s Thesis, Naval Postgraduate School, Monterey, United States). URL: http://hdl.handle.net/10945/4487
McCallum, Neil J. (2012, March): The Justification of Anti-Terrorism Legislation in Australia and Canada between September 17, 2001 and March 31, 2003. (Doctoral Thesis, RMIT University, Melbourne, Australia).
URL: http://researchbank.rmit.edu.au/view/rmit:160327
Miller, Warwick S. (2012, February): Homegrown Terrorism inside of Democratic States. (Master’s
Thesis, University of New South Wales, Canberra, Australia). URL: http://oai.dtic.mil/oai/ oai?verb=getRecord&metadataPrefix=html&identifier=ADA569742
Murthy, Arvind (2012, May): Protecting New York City from Homegrown Terrorism: The City’s Role in Radicalization and Counter- Radicalization. (Master’s Thesis, Columbia University, New York, United States). URL: http://hdl.handle.net/10022/AC:P:13385
Myers, Matthew Kendall (2010, March): A Tale of Two Countries: Why some British Muslims Turned to Terrorism and French Muslims Did not. (Master’s Thesis, Naval Postgraduate School, Monterey, United States). URL: http://hdl.handle.net/10945/5428
Nesser, Petter (2004): Jihad in Europe: Exploring the Sources of Motivations for Salafi-Jihadi Terrorism in Europe Post-Millennium. (Master’s Thesis, University of Oslo, Oslo, Norway).
Nesser, Petter (2011): Jihad in Europe: Patterns in Islamist Terrorist Cell Formation and Behaviour, 1995-2010. (Doctoral Thesis, University of Oslo, Oslo, Norway).
Peery, William Joseph, III (2012, December): Lone Wolves: An Assessment of the Ideology behind Homegrown Islamist Individual Terrorists. (Master’s Thesis, Baylor University, Waco, United States). URL: http://hdl. handle.net/2104/8590
Robert, Emilie (2012, February): LEtat de droit et la lutte contre le terrorisme dans lUnion europeenne: Mesures europeennes de lutte contre le terrorisme suite aux attentats du 11 septembre 2001. (Doctoral Thesis, University of Lille Nord de France, Lille, France). URL: http://www.theses.fr/2012LIL20001/document
Schlagheck, Heidi Michelle (2006, December): The Importance of International Law in Counter-Terrorism: The Need for New Guidelines in International Law to Assist States Responding to Terrorist Attacks. (Master’s Thesis, Virginia Polytechnic Institute and State University, Cape Canaveral, United States). URL: http://scholar.lib. vt.edu/theses/available/etd-12212006-142205
Simpson, Matthew Aaron (2014, August): Reanchoring Terrorism Studies: An Application of Social Movement Theory to the Concept of Domestic Terrorism. (Doctoral Thesis, University of Utah, Salt Lake City, United States). URL: http://content.lib.utah.edu/cdm/singleitem/collection/etd3/id/3209/rec/1683
Southers, Erroll Gregory (2013, December): Homegrown Violent Extremism: Designing a CommunityBased Model to Reduce the Risk of Recruitment and Radicalization. (Doctoral Thesis, University of Southern California, Los Angeles, United States). URL: http://digitallibrary.usc.edu/cdm/compoundobj ect/collection/ p15799coll3/id/328935/rec/2849
Springer, Nathan R. (2009, December): Patterns of Radicalization: Identifying the Markers and Warning Signs of Domestic Lone Wolf Terrorists in our Midst. (Master’s Thesis, Naval Postgraduate School, Monterey, United States). URL: http://www.hsdl.org/?view&did=29620
Starr-Deelen, Donna G. (2012): United States Use of Force against Terrorism and the Threat of Terrorism: An Analysis of the Past Four U.S. Presidents’ Use of Force to Combat International Terrorism. (Doctoral Thesis, University of Bradford, Bradford, United Kingdom). URL: https://bradscholars.brad.ac.uk/ handle/10454/6309
Stott, Paul Vernon Angus (2015, April): British Jihadism: The Detail and the Denial. (Doctoral Thesis, University of East Anglia, Norwich, United Kingdom). URL: https://ueaeprints.uea.ac.uk/id/eprint/53460
Stottlemyre, Sonia M. (2014, April): The Effect of Country-Level Income on Domestic Terrorism: A Worldwide Analysis of the Difference between Lone-Wolf and Group Affiliated Domestic Terrorism. (Master’s Thesis, Georgetown University, Washington, DC, United States). URL: http://hdl.handle.net/10822/709882
Uhlig, Christina (2015, June): Moving towards Securitization: How the Paris Attacks were Used to Justify Extraordinary Measures. (Master’s Thesis, Linnaeus University, Vaxjb/Kalmar, Sweden). URL: http://lnu. diva-portal.org/smash/record.jsf;jsessionid=CHAjXQ9cuncS55p7B5eijw8G9pTjo5eWuVB9bQ2u.diva2- search1?pid=diva2%3A824877&dswid=370
Vargas, Alejandro, Jr. (2011, June): Applying Psychosocial Theories of Terrorism to the Radicalization Process: A Mapping of De La Corte’s Seven Principles to Homegrown Radicals. (Master’s Thesis, Naval Postgraduate School, Monterey, United States). URL: http://hdl.handle.net/10945/5619
Wesseling, Mara (2013, September): The European Fight against Terrorism Financing: Professional Fields and New Governing Practices. (Doctoral Thesis, University of Amsterdam, Amsterdam, The Netherlands). URL: http://hdl.handle.net/11245/1.397292
Westerhout, Thomas (2015, January): When Citizens Become Terrorists: A Within-Case Analysis of the Link between Democracy and Domestic Terrorist Activity in Greece after Metapolitefsi. (Master’s Thesis, Leiden University, Leiden, The Netherlands). URL: http://hdl.handle.net/1887/32862
Wolfberg, William Seth (2012, October): The Homegrown Jihad: A Comparative Study of Youth Radicalization in the United States and Europe. (Master’s Thesis, University of South Florida, Tampa, United States). URL: http://scholarcommons.usf.edu/etd/4421
Zimmermann, Katie (2014, December): Terrorist Group Efforts in the Homeland and the Strategy to Combat them. (Master’s Thesis, Johns Hopkins University, Baltimore, United States). URL: http://jhir.library.jhu.edu/ handle/1774.2/37312
Journal Articles and Book Chapters
Abbas, Tahir (2015): Muslim Political Radicalization in the West. In: Roberto Tottoli (Ed.): Routledge Handbook of Islam in the West. (Routledge Handbooks). Abingdon: Routledge, 272-286.
Acharya, Arabinda (2013): Group, Network or Leaderless Jihad? In: Ten Years after 9/11: Rethinking the Jihadist Threat. (Routledge Security in Asia Pacific Series, Vol. 23). Abingdon: Routledge, 40-49.
Alexander, Dean C. (2012, Spring-Fall): Al-Qaeda and al-Qaeda in the Arabian Peninsula-Inspired, Homegrown Terrorism in the United States. Defence Against Terrorism Review, 4(1), 31-46. URL: http://www. coedat.nato.int/publication/datr/volume7/03-Al-Qaeda and al-QaedaintheArabian Peninsula.pdf
Allan, Stuart (2014, August): Witnessing in Crisis: Photo-Reportage of Terror Attacks in Boston and London. Media, War & Conflict, 7(2), 133-151. DOI: http://dx.doi.org/10.1177/1750635214531110
Alschuler, Lawrence (2014): The Life Cycle of a British Islamist: A Jungian Perspective. Journal of Social and Political Psychology, 2(1), 31-42. DOI: http://dx.doi.org/10.5964/jspp.v2i1.272
Aly, Anne (2013): The Policy Response to Home-Grown Terrorism: Reconceptualising Prevent and Resilience as Collective Resistance. Journal of Policing, Intelligence and Counter Terrorism, 8(1), 2-18. DOI: http://dx.doi. org/10.1080/18335330.2013.789594
Andre, Virginie (2015): Merah and Breivik: A Reflection of the European Identity Crisis. Islam and Christian-Muslim Relations, 26(2), 183-204. DOI: http://dx.doi.org/10.1080/09596410.2015.1015246
Andre, Virginie; Harris-Hogan, Shandon (2013): Mohamed Merah: From Petty Criminal to Neojihadist. Politics, Religion & Ideology, 14(2), 307-319. DOI: http://dx.doi.org/10.1080/21567689.2013.792655
Andre, Virginie; Mansouri, Fethi; Lobo, Michele (2015): A Fragmented Discourse of Religious Leadership in France: Muslim Youth between Citizenship and Radicalization. Journal of Muslim Minority Affairs, 35(2), 296-313. DOI: http://dx.doi.org/10.1080/13602004.2015.1046743
Antonius Rachad (2013): A Mediated Relationship: Media Representations of Arabs and Muslims as a Political Process. In: Jenna Hennebry; Bessma Momani (Eds.): Targeted Transnationals: The State, the Media, and Arab Canadians. Vancouver: UBC Press, 110-128.
Antonius, Rachad (2015): National and Transnational Security Regimes: Canada. In: Suad Joseph (Ed.): Encyclopedia of Women & Islamic Cultures. (Brill Online Edition). Leiden, The Netherlands: Brill. Available from: http://referenceworks.brillonline.com/entries/encyclopedia-of-women-and-islamic-cultures/national- and-transnational-security-regimes-canada-EWICCOM 0686
Antonius Rachad; Labelle Micheline; Rocher, Francois (2013): Multiculturalism and Discrimination in Canada and Quebec: The Case of Arabs and Muslims. In: Jenna Hennebry; Bessma Momani (Eds.): Targeted Transnationals: The State, the Media, and Arab Canadians. Vancouver: UBC Press, 89-109.
Archer, Emerald M. (2014): Crossing the Rubicon: Understanding Cyber Terrorism in the European Context. The European Legacy: Toward New Paradigms, 19(5), 606-621. DOI: http://dx.doi.org/10.1080/10848770.2014 .943495
Argomaniz, Javier (2015, June): European Union Responses to Terrorist Use of the Internet. Cooperation and Conflict, 50(2), 250-268. DOI: http://dx.doi.org/10.1177/0010836714545690
Avella, Valerie (2006): The Domestic War on Terrorism: Fighting the Roots of Jihadist Extremism in the United States. Defense Intelligence Journal, 15(1), 13-24.
Azzam, Maha (2007, Spring-Summer): The Radicalization of Muslim Communities in Europe: Local and Global Dimensions. The Brown Journal of World Affairs, 13(2), 123-134.
Bandyopadhyaya, Subhayu; Sandler, Todd (2014, February): Immigration Policy and Counterterrorism. Journal of Public Economics, 110, 112-123. DOI: http://dx.doi.org/10.1016Zj.jpubeco.2013.12.013URL: http:// create.usc.edu/sites/default/files/publications//immigrationpolicyandcounterterrorism.pdf
Barbieri, Eliane Tschaen; Klausen, Jytte (2012): Al Qaeda’s London Branch: Patterns of Domestic and Transnational Network Integration. Studies in Conflict & Terrorism, 35(6), 411-431. DOI: http://dx.doi.org/1 0.1080/1057610X.2012.675551
Bartolo, Romain (2011): Decentralised Leadership in Contemporary Jihadism: Towards a Global Social Movement. Journal of Terrorism Research, 2(1). DOI: http://doi.org/10.15664/jtr.173
Bartoszewicz, Monika G. (2013, June): Controversies of Conversions: The Potential Terrorist Threat of European Converts to Islam. Perspectives on Terrorism, 7(3), 17-29. URL: http://www.terrorismanalysts.com/ pt/index.php/pot/article/view/265
Beebe, Sarah Miller; Pherson, Randolph H. (2012): Colombia’s FARC Attacks the US Homeland. In: Cases in Intelligence Analysis: Structured Analytic Techniques in Action. Thousand Oaks: CQ Press, 155-178.
Beebe, Sarah Miller; Pherson, Randolph H. (2012): The Atlanta Olympics Bombing. In: Cases in Intelligence Analysis: Structured Analytic Techniques in Action. Thousand Oaks: CQ Press, 119-136.
Belarouci, Latefa (2009): Islamism: The Process of Identity Formation. In: Thomas M. Pick; Anne Speckhard;
Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 3-17. DOI: http://dx.doi.org/10.3233/978-1-60750- 075-9-3
Berczyk, Julia (2013): Community-Based Counter-Terrorism and Anti-Extremism Policies and the ZDK’s “Community Coaching”. JEX, 2/2013, 100-122. URL: http://journals.sfu.ca/jed/index.php/jex/article/view/25
Bergen, Peter; Hoffman, Bruce; Tiedemann, Katherine (2011): Assessing the Jihadist Terrorist Threat to America and American Interests. Studies in Conflict & Terrorism, 34(2), 65-101. DOI: http://dx.doi.org/10.10 80/1057610X.2011.538830
Beyler, Clara (2006): The Jihadist Threat in France. Current Trends in Islamist Ideology, 3, 89-113. URL: http:// www.hudson.org/content/researchattachments/attachment/1357/current trends vol 3.pdf
Blackwood, Leda; Hopkins, Nick; Reicher, Stephen D. (2015, October): “Flying while Muslim”: Citizenship and Misrecognition in the Airport. Journal of Social and Political Psychology, 3(2), 148-170. DOI: http:// dx.doi.org/10.5964/jspp.v3i2.375
Blumenau, Bernhard (2015): Taming the Beast: West Germany, the Political Offence Exception, and the Council of Europe Convention on the Suppression of Terrorism. Terrorism and Political Violence, 27(2), 310330. DOI: http://dx.doi.org/10.1080/09546553.2013.806912
Brachman, Jarret M.; Levine, Alix N. (2011, Winter): You Too Can Be Awlaki! The Fletcher Forum of World Affairs, 35(1), 25-46. URL: http://fletcher.tufts.edU/Fletcher-Forum/Archives/~/media/Fletcher/Microsites/
Fletcher%20Forum/PDFs/2011winter/Brachman-Levine.pdf
Brandon, James (2015, August): Rise of Islamic State Reignites British Radicalization Threat. Terrorism Monitor, 13(17), 7-10. URL: http://www.jamestown.org/uploads/media/TerrorismMonitorVol13Issue17 03. pdf
Brinson, Mary E.; Stohl, Michael (2012): Media Framing of Terrorism: Implications for Public Opinion, Civil Liberties, and Counterterrorism Policies. Journal of International and Intercultural Communication, 5(4), 270290. DOI: http://dx.doi.org/10.1080/17513057.2012.713973
Brockhoff, Sarah; Krieger, Tim; Meierrieks, Daniel (2015, October): Great Expectations and Hard Times: The (Nontrivial) Impact of Education on Domestic Terrorism. Journal of Conflict Resolution, 59(7), 1186-1215.
DOI: http://dx.doi.org/10.1177/0022002713520589
Brooks, Risa A. (2011, Fall): Muslim “Homegrown” Terrorism in the United States: How Serious Is the Threat? International Security, 36(2), 7-47. DOI: http://dx.doi.org/10.1162/ISEC a 00055URL: http:// belfercenter.ksg.harvard.edu/files/Muslim%20Homegrown%20Terrorism%20in%20the%20United%20States. pdf
Brown, Katherine E.; Saeed, Tania (2015): Radicalization and Counter-Radicalization at British Universities: Muslim Encounters and Alternatives. Ethnic and Racial Studies, 38(11), 1952-1968. DOI: http://dx.doi.org/1 0.1080/01419870.2014.911343
Bures, Oldrich (2010): EU’s Fight against Terrorist Finances: Internal Shortcomings and Unsuitable External Models. Terrorism and Political Violence, 22(3), 418-437. DOI: http://dx.doi.org/10.1080/09546550903463434
Capellan, Joel A. (2015): Lone Wolf Terrorist or Deranged Shooter? A Study of Ideological Active Shooter Events in the United States, 1970-2014. Studies in Conflict & Terrorism, 38(6), 395-413. DOI: http://dx.doi.or g/10.1080/1057610X.2015.1008341
Carter, Jeremy G.; Carter, David L. (2012): Law Enforcement Intelligence: Implications for Self-Radicalized Terrorism. Police Practice and Research: An International Journal, 13(2), 138-154. DOI: http://dx.doi.org/10.1 080/15614263.2011.596685URL: https://scholarworks.iupui.edu/bitstream/handle/1805/3857/Carter-2012- Law-Enforcement-Intelligence.p df
Celso, Anthony (2014): Al-Qaeda Plots and Attacks against the United States after 9/11. In: Al-Qaeda’s Post-9/11 Devolution: The Failed Jihadist Struggle against the Near and Far Enemy. New York: Bloomsbury Academic, 159-180.
Celso, Anthony (2014): Al-Qaeda’s Role in the Madrid and London Bombings. In: Al-Qaeda’s Post-9/11 Devolution: The Failed Jihadist Struggle against the Near and Far Enemy. New York: Bloomsbury Academic, 81-104.
Celso, Anthony (2014): Introduction: Al-Qaeda’s Post 9-11 Devolution and its Diffuse Network of “Associates”, “Affiliates”, Insurgents, and “Homegrown” Terrorists. In: Al-Qaeda’s Post-9/11 Devolution: The Failed Jihadist Struggle against the Near and Far Enemy. New York: Bloomsbury Academic, 1-14.
Charles, Christopher A. D.; Maras, Marie-Helen (2015): Strengthening Counterterrorism from the Information of a Successful Terrorist Attack and Failed Missions in the United States. Journal of Applied Security Research, 10(2), 155-180. DOI: http://dx.doi.org/10.1080/19361610.2015.1004513
Chermak, Steven; Gruenewald, Jeffrey A. (2015): Laying a Foundation for the Criminological Examination of Right-Wing, Left-Wing, and Al Qaeda-Inspired Extremism in the United States. Terrorism and Political Violence, 27(1), 133-159. DOI: http://dx.doi.org/10.1080/09546553.2014.975646
Chin, Warren (2013): The War on the Home Front: Al Qaeda and Terrorism in the UK. In: Britain and the War on Terror: Policy, Strategy and Operations. (Military Strategy and Operational Art). Farnham: Ashgate, 177-206.
Choi, Seung-Whan (2015): Economic Growth and Terrorism: Domestic, International, and Suicide. Oxford Economic Papers, 67(1), 157-181. DOI: http://dx.doi.org/10.1093/oep/gpu036
Chuang, Angie; Roemer, Robin Chin (2013, March): The Immigrant Muslim American at the Boundary of Insider and Outsider: Representations of Faisal Shahzad as “Homegrown” Terrorist. Journalism & Mass Communication Quarterly, 90(1), 89-107. DOI: http://dx.doi.org/10.1177/1077699012468740
Cilluffo, Frank J.; Cardash, Sharon L.; Whitehead, Andrew J. (2007, Spring-Summer): Radicalization: Behind Bars and beyond Borders. The Brown Journal of World Affairs, 13(2), 113-122. URL: http://cchs.gwu.edu/ sites/cchs.gwu.edu/files/downloads/HSPI Journal 11.pdf
Crenshaw, Emlyn (2014): American and Foreign Terrorists: An Analysis of Divergent Portrayals in US Newspaper Coverage. Critical Studies on Terrorism, 7(3), 363-378. DOI: http://dx.doi.org/10.1080/17539153.2 014.953306
Croft, Stuart; Moore, Cerwyn (2010, July): The Evolution of Threat Narratives in the Age of Terror: Understanding Terrorist Threats in Britain. International Affairs, 86(4), 821-835. DOI: http://dx.doi.
org/10.1111/j.1468-2346.2010.00914.x URL: http://wrap.warwick.ac.uk/5571/1/WRAP Croft Evolution threat narratives.pdf
Crone, Manni; Harrow, Martin (2011): Homegrown Terrorism in the West. Terrorism and Political Violence, 23(4), 521-536. DOI: http://dx.doi.org/10.1080/09546553.2011.571556
Dahl, Erik J. (2014): Local Approaches to Counterterrorism: The New York Police Department Model. Journal of Policing, Intelligence and Counter Terrorism, 9(2), 81-97. DOI: http://dx.doi.org/10.1080/18335330. 2014.940815
Dalgaard-Nielsen, Anja (2010): Violent Radicalization in Europe: What we Know and what we do not Know. Studies in Conflict & Terrorism, 33(9), 797-814. DOI: http://dx.doi.org/10.1080/1057610X.2010.501423
Daly, John C. K. (2014, November): Spain Grapples with Growing Islamic State Threat. Terrorism Monitor, 12(22), 7-9. URL: http://www.jamestown.org/uploads/media/TerrorismMonitorVol12Issue22 03.pdf
Daly, John C. K. (2015, February): Sweden Grapples with Rising Extremism. Terrorism Monitor, 13(3), 5-7.
URL: http://www.jamestown.org/uploads/media/TerrorismMonitorVol13Issue3 01.pdf
Dechesne, Mark; Meines, Marije (2012): What’s New about Radicalization in the Netherlands? The Rise of Individualized Radicalization and its Policy Challenge. Dynamics of Asymmetric Conflict: Pathways toward terrorism and genocide, 5(1), 55-59. DOI: http://dx.doi.org/10.1080/17467586.2012.699083
Delia Deckard, Natalie; Jacobson, David (2015, September): The Prosperous Hardliner: Affluence, Fundamentalism, and Radicalization in Western European Muslim Communities. Social Compass, 62(3), 412-433. DOI: http://dx.doi.org/10.1177/0037768615587827 URL: http://www.academia.edu/15151488/ The prosperous hardliner Affluence fundamentalism and radicalization in Western European Muslim communities
Dienstbuhl, Dorothee (2010, September): Jugendliche im Visier terroristischer Rekrutierungsarbeit: „Homegrown-Terrorism“ und der Mythos Gottesstaat. Die Kriminalpolizei, 9/2010. URL: http://www.
kriminalpolizei.de/ausgaben/2010/september/detailansicht-september/artikel/iugendliche-im-visier- terroristischer-rekrutierungsarbeit.html
Edwards, Aaron (2011): When Terrorism as Strategy Fails: Dissident Irish Republicans and the Threat to British Security. Studies in Conflict & Terrorism, 34(4), 318-336. DOI: http://dx.doi.org/10.1080/105761 0X.2011.551720
Edwards, Jonathan J. (2015, March): Figuring Radicalization: Congressional Narratives of Homeland Security and American Muslim Communities. Communication and Critical/Cultural Studies, 12(1), 102-120. DOI: http://dx.doi.org/10.1080/14791420.2014.996168
Eiikman, Quirine (2014, August): The German Sauerland Cell Reconsidered. Perspectives on Terrorism, 8(4), 82-90. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/view/363
Enders, Walter; Sandler, Todd; Gaibulloev, Khusrav (2011, May): Domestic versus Transnational Terrorism: Data, Decomposition, and Dynamics. Journal of Peace Research, 48(3), 319-337. DOI: http://dx.doi.
org/10.1177/0022343311398926URL: http://wenders.people.ua.edu/uploads/2/6/3/8/26382715/domestic trans ms final.pdf
Eroukhmanoff, Clara (2015): The Remote Securitisation of Islam in the US Post-9/11: Euphemisation, Metaphors and the “Logic of Expected Consequences” in Counter-Radicalisation Discourse. Critical Studies on Terrorism, 8(2), 246-265. DOI: http://dx.doi.org/10.1080/17539153.2015.1053747
Fahmy, Shahira; Johnson, Thomas J. (2007): Mediating the Anthrax Attacks: Media Accuracy and Agenda Setting during a Time of Moral Panic. Atlantic Journal of Communication, 15 (1), 19-40. DOI: http://dx.doi. org/10.1080/15456870701212583
Farrell, Laura C.; Littlefield, Robert S. (2012, June): Identifying Communication Strategies in Cases of Domestic Terrorism: Applying Cultural Context to the Fort Hood Shooting. Journal of Homeland Security and Emergency Management, 9(1). DOI: http://dx.doi.org/10.1515/1547-7355.1949
Field, Clive D. (2011): Young British Muslims since 9/11: A Composite Attitudinal Profile. Religion, State and Society, 39(2-3), 159-175. DOI: http://dx.doi.org/10.1080/09637494.2011.577201
Fodeman, Ari David (2015): Safety and Danger Valves: Functional Displacement in American Anti-Abortion Terrorism. Behavioral Sciences of Terrorism and Political Aggression, 7(3), 169-183. DOI: http://dx.doi.org/10 .1080/19434472.2015.1021828
Freilich, Joshua D.; Chermak, Steven M.; Belli, Roberta (2014): Homegrown Terrorism in the United States. In: Gerben Bruinsma; David Weisburd (Eds.): Encyclopedia of Criminology and Criminal Justice. New York: Springer, 2336-2345.
Freilich, Joshua D. et al. (2015, September): Investigating the Applicability of Macro-Level Criminology Theory to Terrorism: A County-Level Analysis. Journal of Quantitative Criminology, 31(3), 383-411. DOI: http://dx.doi.org/10.1007/s10940-014-9239-0
Gad, Ulrik Pram (2012): Preventing Radicalisation through Dialogue? Self-Securitising Narratives versus Reflexive Conflict Dynamics. Critical Studies on Terrorism, 5(3), 391-407. DOI: http://dx.doi.org/10.1080/175 39153.2012.723449URL: http://curis.ku.dk/ws/files/128738210/2012b Gad CST 5 3 391 407 Preventing radicalization FINAL DRAFT.pdf
Gaibulloev; Khusrav; Sandler, Todd (2008, August): Growth Consequences of Terrorism in Western Europe. Kyklos, 61 (3), 411-424. DOI: http://dx.doi.org/10.1111/j.1467-6435.2008.00409.x URL: http://create.usc.edu/ sites/default/files/publications/growthconsequencesofterrorisminwesterneurope.pdf
Gallaher, Carolyn (2015): Contemporary Domestic Terrorism in the United States. In: Randall D. Law (Ed.): The Routledge History of Terrorism. (The Routledge Histories). Abingdon: Routledge, 317-332.
Ganor, Boaz (2011): An Intifada in Europe? A Comparative Analysis of Radicalization Processes among Palestinians in the West Bank and Gaza versus Muslim Immigrants in Europe. Studies in Conflict & Terrorism, 34(8), 587-599. DOI: http://dx.doi.org/10.1080/1057610X.2011.582629
Ghatak, Sambuddha (2014, August): Willingness and Opportunity: A Study of Domestic Terrorism in PostCold War South Asia. Terrorism and Political Violence. Advance Online Publication. DOI: http://dx.doi.or g/10.1080/09546553.2014.902813URL: http://www.sambuddhaghatak.com/wp-content/uploads/2015/06/
Willingness-and-Opportunity-A-Study-of-Domestic-Terrorism-in-post-Cold-War-South-Asia.pdf
Giesecke, James et al. (2014): Regional Dynamics under Adverse Physical and Behavioral Shocks: The Economic Consequences of a Chlorine Terrorist Attack in the Los Angeles Financial District. In: Peter Nijkamp; Adam Rose; Karima Kourtit (Eds.): Regional Science Matters: Studies Dedicated to Walter Isard.
Cham: Springer, 319-350. DOI: http://dx.doi.org/10.1007/978-3-319-07305-7 16
Gonzalez, Alessandra L.; Freilich, Joshua D.; Chermak, Steven M. (2014, October): How Women
Engage Homegrown Terrorism. Feminist Criminology, 9(4), 344-366. DOI: http://dx.doi. org/10.1177/1557085114529809
Grewal, Harjeet (2013): Regarding the Face of Hatred: On Visions of Homegrown and Domestic Terror. Sikh Formations: Religion, Culture, 'Theory, 9(3), 409-416. DOI: http://dx.doi.org/10.1080/17448727.2013.828859
Gruenewald, Jeff; Chermak, Steven; Freilich, Joshua D. (2013, February): Distinguishing “Loner” Attacks from other Domestic Extremist Violence: A Comparison of Far-Right Homicide Incident and Offender Characteristics. Criminology & Public Policy, 12(1), 65-91. DOI: http://dx.doi.org/10.1111/1745-9133.12008
URL: http://criminology.fsu.edu/wp-content/uploads/volume-12-issue-1.pdf
Gunaratna, Rohan; Haynal, Cleo (2013, June): Current and Emerging Threats of Homegrown Terrorism: The Case of the Boston Bombings. Perspectives on Terrorism, 7(3), 44-63. URL: http://www.terrorismanalysts. com/pt/index.php/pot/article/view/267
Hafez, Mohammed; Mullins, Creighton (2015): The Radicalization Puzzle: A Theoretical Synthesis of Empirical Approaches to Homegrown Extremism. Studies in Conflict & Terrorism, 38(11), 958-975. DOI: http://dx.doi.org/10.1080/1057610X.2015.1051375
Haglund, David G. (2012): Orders and Borders: Unipolarity and the Issue of Homeland Security. Canadian Foreign Policy Journal, 18(1), 9-25. DOI: http://dx.doi.org/10.1080/11926422.2012.674383
Haglund, David G.; Lauzon, Dru (2014): “Homegrowns” in North America: The Changing Face of Radical Islamism, and its Implications for Canada-United States Relations. Canadian Foreign Policy Journal, 20(3), 305-319. DOI: http://dx.doi.org/10.1080/11926422.2014.982671
Harris-Hogan, Shandon (2013): Anatomy of a Terrorist Cell: A Study of the Network Uncovered in Sydney in 2005. Behavioral Sciences of Terrorism and Political Aggression, 5(2), 137-154. DOI: http://dx.doi.org/10.1080/ 19434472.2012.727096
Harris-Hogan, Shandon (2014): The Importance of Family: The Key to Understanding the Evolution of Jihadism in Australia. Security Challenges, 10(1), 31-49. URL: http://www.securitychallenges.org.au/
ArticlePages/vol10no1Harris-Hogan.html
Hegghammer, Thomas (2013, February): Should I Stay or Should I Go? Explaining Variation in Western Jihadists’ Choice between Domestic and Foreign Fighting. American Political Science Review, 107(1), 1-15.
DOI: http://dx.doi.org/10.1017/S0003055412000615URL: http://hegghammer.com/ files/Hegghammer - Should I stay or should I go.pdf
Hegghammer, Thomas; Nesser, Petter (2015, August): Assessing the Islamic State’s Commitment to Attacking the West. Perspectives on Terrorism, 9(4), 14-30. URL: http://www.terrorismanalysts.com/pt/index.php/pot/ article/view/440
Hellmich, Christina (2014): Reply to Christine Sylvester, “Terrorwars: Boston, Iraq”: An Examination of Differences between Counter-Terrorism and War as Seen through the Iraqi Experience of Occupation.
Critical Studies on Terrorism, 7(3), 472-478. DOI: http://dx.doi.org/10.1080/17539153.2014.953307
Hellmuth, Dorle (2015, August): Countering Jihadi Terrorists and Radicals the French Way. Studies in Conflict & Terrorism. Advance Online Publication. DOI: http://dx.doi.org/10.1080/1057610X.2015.1076277
Hellmuth, Dorle (2015, Fall): Countering Jihadi Radicals and Foreign Fighters in the United States and France: Tres Similaire. Journal for Deradicalization, 4, 1-43. URL: http://j ournals.sfu.ca/j d/index.php/j d/ article/view/24/
Hemmingsen, Ann-Sophie (2015): Viewing Jihadism as a Counterculture: Potential and Limitations. Behavioral Sciences of Terrorism and Political Aggression, 7(1), 3-17. DOI: http://dx.doi.org/10.1080/19434472 .2014.977326URL: https://counterideology2.files.wordpress.com/2014/11/jihadism-as-counter-culture.pdf
Henderson, James R. (2009, Winter): Home-Grown Jihadism and the Factors of Terror.
Yale Journal of International Affairs, 4(1), 59-71. URL: http://yalejournal.org/wp-content/ uploads/2011/01/094105henderson.pdf
Herrington, Lewis (2015, January): British Islamic Extremist Terrorism: The Declining Significance of Al- Qaeda and Pakistan. International Affairs, 91 (1), 17-35. DOI: http://dx.doi.org/10.1111/1468-2346.12184
Hesterman, Jennifer L. (2013): Domestic Terrorism and the Homegrown Threat. In: The Terrorist-Criminal Nexus: An Alliance of International Drug Cartels, Organized Crime, and Terror Groups. Boca Raton: CRC Press, 93-132.
Hildebrand, Sean (2015, May): Coerced Confusion? Local Emergency Policy Implementation after September 11. Journal of Homeland Security and Emergency Management, 12(2), 273-298. DOI: http://dx.doi. org/10.1515/jhsem-2014-0054
Hinkkainen, Kaisa (2013, August): Homegrown Terrorism: The Known Unknown. Peace Economics, Peace Science and Public Policy, 19(2), 157-182. DOI: http://dx.doi.org/10.1515/peps-2012-0001
Hinkkainen, Kaisa (2014): A Comparative Analysis of Homegrown Terrorism. In: Raul Caruso; Andrea Locatelli (Eds.): Understanding Terrorism: A Socio-Economic Perspective. (Contributions to Conflict Management, Peace Economics and Development, Vol. 22). Bingley: Emerald, 193-216.
Hirschmann, Kai (2010, August): Fanatiker in unserer Mitte: Das Phanomen der “Homegrown Jihadsts”. KAS Auslandsinformationen, 8/2010, 21-43. URL: http://www.kas.de/wf/de/33.20257
Hoffman, Bruce (2007, Spring-Summer): Terrorism in the West: Al-Qaeda’s Role in “Homegrown” Terror. The Brown Journal of World Affairs, 13(2), 91-99.
Hoffman, Bruce (2009, June): Covering the Waterfront: The Continuing, Myriad Threats from both Leader- Led and Leader-Less Terrorism. inSITE, 2(6), 3-6. URL: http://sitemultimedia.org/docs/inSITE June 2009. pdf
Hoffman, Bruce (2010, April): Connecting the Dots of Americans Joining the Jihad. inSITE, 2(11), 6-10.
URL: http://sitemultimedia.org/docs/inSITE April 2010.pdf
Hoffman, Bruce (2010, July): Al-Qaeda’s Continuing Threat to the Homeland: “Diversity Is Definitely the Word”. inSITE, 2(12), 6-9. URL: http://sitemultimedia.org/docs/inSITE July 2010.pdf
Hornqvist, Magnus; Flyghed, Janne (2012): Exclusion or Culture? The Rise and the Ambiguity of the Radicalisation Debate. Critical Studies on Terrorism, 5(3), 319-334. DOI: http://dx.doi.org/10.1080/17539153. 2012.717788
Jongman, Albert J. (Berto) (2009): Radicalisation and Deradicalisation: Dutch Experiences. In: Thomas
M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 32-50. DOI: http:// dx.doi.org/10.3233/978-1-60750-075-9-32
Jordan, Javier (2014): The Evolution of the Structure of Jihadist Terrorism in Western Europe: The Case of Spain. Studies in Conflict & Terrorism, 37(8), 654-673. DOI: http://dx.doi.org/10.1080/1057610X.2014.921770 URL: http://www.ugr.es/~jjordan/Jihadist-Terrorism-Spain.pdf
Kamolnick, Paul (2014, December): Has Adam Gadahn Forsaken the Lawful Jihad for Anti-Americanism?
A Case Study of Ideological Contradictions. Perspectives on Terrorism, 8(6), 36-62. URL: http://www.
terrorismanalysts.com/pt/index.php/pot/article/view/390
Kana, Rozila; Dore, Rupert (2014-15, Winter): Countering Radicalisation across Europe: The Pioneering ISDEP Project. Journal for Deradicalization, 1, 23-25. URL: http://journals.sfu.ca/jd/index.php/jd/article/ view/3
Karagiannis, Emmanuel; McCauley, Clark (2006): Hizb ut-Tahrir al-Islami: Evaluating the Threat Posed by a
Radical Islamic Group that Remains Nonviolent. Terrorism and Political Violence, 18(2), 315-334. DOI: http:// dx.doi.org/10.1080/09546550600570168
Kaunert, Christian; Leonard, Sarah (2011): EU Counterterrorism and the European Neighbourhood Policy: An Appraisal of the Southern Dimension. Terrorism and Political Violence, 23(2), 286-309. DOI: http://dx.doi. org/10.1080/09546553.2010.538276
Khosrokhavar, Farhad (2013): Radicalization in Prison: The French Case. Politics, Religion & Ideology, 14(2), 284-306. DOI: http://dx.doi.org/10.1080/21567689.2013.792654
Kim, MoonSun; de Guzman, Melchor C. (2012): Police Paradigm Shift after the 9/11 Terrorist Attacks: The Empirical Evidence from the United States Municipal Police Departments. Criminal Justice Studies: A Critical Journal of Crime, Law and Society, 25(4), 323-342. DOI: http://dx.doi.org/10.1080/1478601X.2012.707014
King, Michael; Taylor, Donald M. (2011): The Radicalization of Homegrown Jihadists: A Review of Theoretical Models and Social Psychological Evidence. Terrorism and Political Violence, 23(4), 602-622. DOI: http://dx.doi.org/10.1080/09546553.2011.587064
Kirby, Aidan (2007): The London Bombers as “Self-Starters”: A Case Study in Indigenous Radicalization and the Emergence of Autonomous Cliques. Studies in Conflict & Terrorism, 30(5), 415-428. DOI: http://dx.doi. org/10.1080/10576100701258619
Kitchen, Veronica M.; Molnar, Adam (2015): The Promise and Perils of Integrated Models of Public Safety in Canada. In: Martin Bouchard (Ed.): Social Networks, Terrorism and Counter-Terrorism: Radical and Connected. (Contemporary Terrorism Studies). Abingdon: Routledge, 175-195.
Kleinmann, Scott Matthew (2012): Radicalization of Homegrown Sunni Militants in the United States: Comparing Converts and Non-Converts. Studies in Conflict & Terrorism, 35(4), 278-297. DOI: http://dx.doi. org/10.1080/1057610X.2012.656299
Knapton, Holly Melissa (2014, March): The Recruitment and Radicalisation of Western Citizens: Does Ostracism Have a Role in Homegrown Terrorism? [Literature Review] Journal of European Psychology
Students, 5(1), 38-48. DOI: http://doi.org/10.5334/jeps.bo
Kohlmann, Evan F. (2008, July): “Homegrown” Terrorists: Theory and Cases in the War on Terror’s Newest Front. The ANNALS of the American Academy of Political and Social Science, 618(1), 95-109. DOI: http:// dx.doi.org/10.1177/0002716208317203
Komen, Maria M. (2014, Spring): Homegrown Muslim Extremism in the Netherlands: An Exploratory Note.
Journal of Strategic Security, 7(1), 47-53. URL: http://scholarcommons.usf.edu/jss/vol7/iss1/5/
Kowalski, Jeremy D. (2013): “Framing” the Toronto 18: Government Experts, Corporate Media, and the Orientalizing of the Other. In: Jenna Hennebry; Bessma Momani (Eds.): Targeted Transnationals: The State, the Media, and Arab Canadians. Vancouver: UBC Press, 129-156.
Krueger, Alan B. (2008, December): What Makes a Homegrown Terrorist? Human Capital and Participation in Domestic Islamic Terrorist Groups in the U.S.A. Economics Letters, 101 (3), 293-296. DOI: http://doi. orgZ10.1016Zj.econlet.2008.09.008
LaFree, Gary; Bersani, Bianca E. (2014, August): County-Level Correlates of Terrorist Attacks in the United States. Criminology & Public Policy, 13(3), 455-481. DOI: http://dx.doi.org/10.1111/1745-9133.12092URL: http://criminology.fsu.edu/wp-content/uploads/Volume-13-Issue-3.pdf
LaFree, Gary; Dugan, Laura; Miller, Erin (2015): International and Domestic Terrorism. In: Putting Terrorism in Context: Lessons from the Global Terrorism Database. (Contemporary Terrorism Studies). Abingdon: Routledge, 146-172.
LaFree, Gary; Dugan, Laura; Miller, Erin (2015): The Spatial Distribution of Terrorism around the World and in the United States. In: Putting Terrorism in Context: Lessons from the Global Terrorism Database. (Contemporary Terrorism Studies). Abingdon: Routledge, 49-69.
Lambert, Robert (2008, January): Empowering Salafis and Islamists against Al-Qaeda: A London Counterterrorism Case Study. PS: Political Science & Politics, 41 (1), 31-35. DOI: http://dx.doi.org/10.1017/ S1049096508080049
Lambert, Robert (2009): Police and Muslim Communities in London: Countering Al-Qaida Influence and Islamophobia. In: Thomas M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 51-73. DOI: http://dx.doi.org/10.3233/978-1-60750-075-9-51
Lebl, Leslie (2014, Summer): The Islamist Threat to European Security. Middle East Quarterly, 21(3). URL: http://www.meforum.org/3837/the-islamist-threat-to-european-security
Lehrke, Jesse Paul; Schomaker, Rahel (2014): Mechanisms of Convergence in Domestic Counterterrorism Regulations: American Influence, Domestic Needs, and International Networks. Studies in Conflict & Terrorism, 37(8), 689-712. DOI: http://dx.doi.org/10.1080/1057610X.2014.921769
Leuprecht, Christian; Hataley, Todd; Skillicorn, David B. (2013): Cross-Border Terror Networks: A Social Network Analysis of the Canada-US Border. Behavioral Sciences of Terrorism and Political Aggression, 5(2), 155-175. DOI: http://dx.doi.org/10.1080/19434472.2012.760105
Levin, Brian (2015, November): The Original Web of Hate: Revolution Muslim and American Homegrown Extremists. American Behavioral Scientist, 59(12), 1609-1630. DOI: http://dx.doi. org/10.1177/0002764215588815
Lindekilde, Lasse (2012): Introduction: Assessing the Effectiveness of Counter-Radicalisation Policies in Northwestern Europe. Critical Studies on Terrorism, 5(3), 335-344. DOI: http://dx.doi.org/10.1080/17539153. 2012.723522
Lindner, Evelin G. (2009): The Relevance of Humiliation Studies for the Prevention of Terrorism. In: Thomas M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 163-188. DOI: http:// dx.doi.org/10.3233/978-1-60750-075-9-163URL: http://www.humiliationstudies.org/documents/evelin/ PreventionofTerrorismBudapest08.pdf
Lischin, Luke (2013, Spring): Assessing the Terrorist Threat: The Primacy of Domestic Terrorism. The Journal on Terrorism and Security Analysis, 8, 46-59. URL: http://satsa.syr.edu/wp-content/uploads/2013/10/2013- Journal-on-Terrorism-and-Security-Analysis.pdf
Lombardi, Marco (2015): Violent Radicalization Concerns in the Euro-Mediterranean Region. In: Marco Lombardi et al. (Eds.): Countering Radicalisation and Violent Extremism among Youth to Prevent Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 118). Amsterdam: IOS Press, 83-100. DOI: http://dx.doi.org/10.3233/978-1-61499-470-1-83
Malmstrom, Cecilia (2013): EU versus Extremism: Europe must Respond to the Threat of Radicalisation, before it Turns even more Violent. JEX, 2/2013, 1-3. URL: http://j ournals.sfu.ca/j ed/index.php/j ex/article/ view/17
Malreddy, Pavan Kumar (2014): Domesticating the “New Terrorism”: The Case of the Maoist Insurgency in India. The European Legacy: Toward New Paradigms, 19(5), 590-605. DOI: http://dx.doi.org/10.1080/1084877 0.2014.943529
Malthaner, Stefan (2014): Contextualizing Radicalization: The Emergence of the “Sauerland-Group” from Radical Networks and the Salafist Movement. Studies in Conflict & Terrorism, 37(8), 638-653. DOI: http:// dx.doi.org/10.1080/1057610X.2014.921767
Maras, Marie-Helen (2014): Homeland Security. In: The CRC Press Terrorism Reader. Boca Raton: CRC Press, 123-134.
Maras, Marie-Helen (2014): International and Domestic Terrorism. In: The CRC Press Terrorism Reader. Boca Raton: CRC Press, 27-46.
Maras, Marie-Helen (2014): Regional Focus on Terrorism. In: The CRC Press Terrorism Reader. Boca Raton: CRC Press, 181-244.
Martin, C. (Clarence) Augustus (Gus) (2014): Domestic Terrorism in the United States. In: Essentials of Terrorism: Concepts and Controversies. (3rd ed.). Thousand Oaks: SAGE, 181-206.
Martin, C. (Clarence) Augustus (Gus) (2014): Homeland Security. In: Essentials of Terrorism: Concepts and Controversies. (3rd ed.). Thousand Oaks: SAGE, 233-260.
McCoy, John; Knight, W. Andy (2015): Homegrown Terrorism in Canada: Local Patterns, Global Trends. Studies in Conflict & Terrorism, 38(4), 253-274. DOI: http://dx.doi.org/10.1080/1057610X.2014.994349
Mcdonald, Laura Zahra (2011): Securing Identities, Resisting Terror: Muslim Youth Work in the UK and its Implications for Security. Religion, State and Society, 39(2-3), 177-189. DOI: http://dx.doi.org/10.1080/09637494.2011.584712
McGilloway, Angela; Ghosh, Priyo; Bhui, Kamaldeep (2015): A Systematic Review of Pathways to and Processes Associated with Radicalization and Extremism amongst Muslims in Western Societies. [Literature Review]. International Review of Psychiatry, 27(1), 39-50. DOI: http://dx.doi.org/10.3109/09540261.2014.992008
Mellen, Cyndi (2012): When Harry Met Salafi: Literature Review of Homegrown Jihadi Terrorism. [Literature Review]. Journal of Applied Security Research, 7(2), 239-252. DOI: http://dx.doi.org/10.1080/19361610.2012.656257
Michael, Lucy (2011): Islam as Rebellion and Conformity: How Young British Pakistani Muslims in the UK Negotiate Space for and against Radical Ideologies. Religion, State and Society, 39(2-3), 209-227. DOI: http:// dx.doi.org/10.1080/09637494.20n.584752
Michaelsen, Christopher (2010): Australia and the Threat of Terrorism in the Decade after 9/11. Asian Journal of Political Science, 18(3), 248-268. DOI: http://dx.doi.org/10.1080/02185377.2010.527212
Mohamed, Feisal G. (2007, Winter): The Globe of Villages: Digital Media and the Rise of Homegrown Terrorism. Dissent, 54(1), 61-64. DOI: http://dx.doi.org/10.1353/dss.2007.0033
Mueller, John; Stewart, Mark G. (2015): Terrorism, Counterterrorism, and the Internet: The American Cases. Dynamics of Asymmetric Conflict: Pathways toward terrorism and genocide, 8(2), 176-190. DOI: http://dx.doi.org/10.1080/17467586.2015.1065077
Mullins, Sam (2007): Home-Grown Terrorism: Issues and Implications. Perspectives on Terrorism, 1(3). URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/view/12
Mullins, Sam (2011): Islamist Terrorism and Australia: An Empirical Examination of the “Home-Grown” Threat. Terrorism and Political Violence, 23(2), 254-285. DOI: http://dx.doi.org/10.1080/09546553.2010.535717
Mullins, Sam (2013): “Global Jihad”: The Canadian Experience. Terrorism and Political Violence, 25(5), 734776. DOI: http://dx.doi.org/10.1080/09546553.2012.693552
Mythen, Gabe (2012): “No one Speaks for us”: Security Policy, Suspected Communities and the Problem of Voice. Critical Studies on Terrorism, 5(3), 409-424. DOI: http://dx.doi.org/10.1080/17539153.2012.723519
Napps, Cameron; Enders, Walter (2015): A Regional Investigation of the Interrelationships between Domestic and Transnational Terrorism: A Time Series Analysis. Defence and Peace Economics, 26(2), 133151. DOI: http://dx.doi.org/10.1080/10242694.2014.893705URL: http://time-series.net/yahoo site admin/ assets/docs/NappsEnders01282014.4175604.pdf
Nash, Rebecca; Bouchard, Martin (2015): Travel Broadens the Network: Turning Points in the Network Trajectory of an American Jihadi. In: Martin Bouchard (Ed.): Social Networks, Terrorism and CounterTerrorism: Radical and Connected. (Contemporary Terrorism Studies). Abingdon: Routledge, 61-81.
Nesser, Petter (2008): Chronology of Jihadism in Western Europe 1994-2007: Planned, Prepared, and Executed Terrorist Attacks. Studies in Conflict & Terrorism, 31 (10), 924-946. DOI: http://dx.doi. org/10.1080/10576100802339185URL: http://www.ps.au.dk/fileadmin/site files/filer statskundskab/ subsites/cir/pdf-filer/chronology.pdf
Nesser, Petter (2011): Ideologies of Jihad in Europe. Terrorism and Political Violence, 23(2), 173-200. DOI: http://dx.doi.org/10.1080/09546553.2010.537587
Nesser, Petter (2014): Toward an Increasingly Heterogeneous Threat: A Chronology of Jihadist Terrorism in Europe 2008-2013. Studies in Conflict & Terrorism, 37(5), 440-456. DOI: http://dx.doi.org/10.1080/105761 0X.2014.893405
Nesser, Petter (2015): Appendix: Chronology of Jihadism in Europe 1994-2015. In: Islamist Terrorism in Europe. London: Hurst. URL: http://www.hurstpublishers.com/wp-content/uploads/2015/11/Islamist- Terrorism-in-Europe-Appendix-1.pdf
Nesser, Petter; Stenersen, Anne (2014, December): The Modus Operandi of Jihadi Terrorists in Europe.
Perspectives on Terrorism, 8(6), 2-24. URL: http://www.terrorismanalysts.eom/pt/index.php/pot/article/ view/388
Neumann, Peter R. (2006): Europe’s Jihadist Dilemma. Survival, 48(2), 71-84. DOI: http://dx.doi. org/10.1080/00396330600765518
Neumann, Peter R. (2013): Options and Strategies for Countering Online Radicalization in the United States. Studies in Conflict & Terrorism, 36(6), 431-459. DOI: http://dx.doi.org/10.1080/1057610X.2013.784568
URL: https://counterideology2.files.wordpress.com/2013/06/options-n-strategies-for-countering-online- radicalization-in-the-us.pdf
Nischler, Christiane (2009, June): „Home-Grown“: Terrorismus und Radikalisierungspotenziale in
Deutschland: Hintergrunde und preventive Ansatze aus polizeilicher Sicht. Die Kriminalpolizei, 9/2009. URL:
http://www.kriminalpolizei.de/ausgaben/2009/juni/detailansicht-juni/artikel/home-grown.html
Olsson, Peter A. (2013, Summer): Homegrown Terrorists, Rebels in Search of a Cause. Middle East Quarterly, 20 (3), 3-10. URL: http://www.meforum.org/3539/homegrown-terrorists
O’Toole, Therese; DeHanas, Daniel Nilsson; Modood, Tariq (2012): Balancing Tolerance, Security and Muslim Engagement in the United Kingdom: The Impact of the “Prevent” Agenda. Critical Studies on Terrorism, 5(3), 373-389. DOI: http://dx.doi.org/10.1080/17539153.2012.725570
Qvortrup, Matt; Lijphart, Arend (2013): Domestic Terrorism and Democratic Regime Types. Civil Wars, 15(4), 471-485. DOI: http://dx.doi.org/10.1080/13698249.2013.853415
Pantucci, Raffaello (2008, October): Operation Praline: The Realization of Al-Suri’s Nizam, la Tanzim?
Perspectives on Terrorism, 2(12), 11-16. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/59
Pantucci, Raffaello (2015): Innovation and Learning in the British Jihad. In: Magnus Ranstorp; Magnus Normark (Eds.): Understanding Terrorism Innovation and Learning: Al-Qaeda and beyond. (Political Violence). Abingdon: Routledge, 213-231.
Pantucci, Raffaello (2015, January): Britain’s Terror Threat from the Levant. CTC Sentinel, 8(1), 14-17. URL: https://www.ctc.usma.edu/v2/wp-content/uploads/2015/01/Sentinel-Tanuary-2015-vol-8-issue-116.pdf
Pantucci, Raffaello (2015, August): Al-Muhajiroun’s European Recruiting Pipeline. CTC Sentinel, 8(8), 21-24.
URL: https://www.ctc.usma.edu/v2/wp-content/uploads/2015/08/CTCSentinel-Vol8Issue811.pdf
Pearson, Elizabeth (2015, September): The Case of Roshonara Choudhry: Implications for Theory on Online Radicalization, ISIS Women, and the Gendered Jihad. Policy & Internet. Advance Online Publication. DOI: http://dx.doi.org/10.1002/poi3.101
per Concordiam Staff (2015): The Risk from Returnees. per Concordiam, 6(2), 60-63. URL: http:// perconcordiam.com/perCon V6N2 Eng.pdf
Perkins, Brian M. (2015, March): Following the Peshawar School Attack, Pakistan Moves against
Domestic Terrorism. Terrorism Monitor, 13(5), 5-7. URL: http://www.jamestown.org/uploads/media/
TerrorismMonitorVol13Issue5 02.pdf
Perlmutter, Dawn (2004): Domestic Terrorist Religions. In: Investigating Religious Terrorism and Ritualistic Crimes. Boca Raton: CRC Press, 45-82.
Pick, Thomas M. (2009): Societal Fit and Radicalisation: Poorly Managed Absorption of Immigrants and Poor Fit between the Society of Origin and the Host Society as Predisposing Factors to Radicalisation. In: Thomas M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 207-226. DOI: http://dx.doi.org/10.3233/978-1-60750-075-9-207
Pisoiu, Daniela (2013): Coming to Believe “Truths” about Islamist Radicalization in Europe. Terrorism and Political Violence, 25(2), 246-263. DOI: http://dx.doi.org/10.1080/09546553.2012.659361
Pitcavage, Mark (2015, November): Cerberus Unleashed: The Three Faces of the Lone Wolf Terrorist. American Behavioral Scientist, 59(13), 1655-1680. DOI: http://dx.doi.org/10.1177/0002764215588817
Post, Jerrold M.; Sheffer, Gabriel (2007, Spring-Summer): The Risk of Radicalization and Terrorism in U.S. Muslim Communities. Brown Journal of World Affairs, 13, 101-112.
Powers, Samuel Tyler (2015, January): Expanding the Paradigm: Countering Violent Extremism in Britain and the Need for a Youth Centric Community Based Approach. Journal of Terrorism Research, 6(1), 19-26. DOI: http://doi.org/10.15664/jtr.1074
Prager, Fynnwin et al. (2011): Exploring Reductions in London Underground Passenger
Journeys Following the July 2005 Bombings. Risk Analysis, 31 (5), 773-786. DOI: http://dx.doi. org/10.1111/j.1539-6924.2010.01555.x URL: http://create.usc.edu/sites/default/files/publications/ exploringreductionsinlondonundergroundpassengerjourneysfollowingthejuly2005bombings 0.pdf
Pratt, Douglas (2015): Islamophobia as Reactive Co-Radicalization. Islam and Christian-Muslim Relations, 26(2), 205-218. DOI: http://dx.doi.org/10.1080/09596410.2014.1000025
Pratt, Douglas (2015): Reactive Co-Radicalization: Religious Extremism as Mutual Discontent. Journal for the Academic Study of Religion, 28(1), 3-23. DOI: http://dx.doi.org/10.1558/jasr.v28i1.26800
Probst, Peter S. (2009): Political Warfare, the Muslim Brotherhood, and the Targeting of America. In: Thomas M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 127-133. DOI: http:// dx.doi.org/10.3233/978-1-60750-075-9-127
Ramsay, Gilbert A.; Marsden, Sarah V. (2015): Leaderless Global Jihadism: The Paradox of Discriminate Violence. The Journal of Strategic Studies, 38(5), 579-601. DOI: http://dx.doi.org/10.1080/01402390.2015.1032 408
Reinares, Fernando (2010): The Madrid Bombings and Global Jihadism. Survival, 52(2), 83-104. DOI: http://dx.doi.org/10.1080/00396331003764629URL: http://www.ict.org.il/Article/1073/The%20Madrid%20 Bombings%20and%20Global%20Jihadism
Roex, Ineke (2014, June): Should we be Scared of all Salafists in Europe? A Dutch Case Study. Perspectives on Terrorism, 8 (3), 51-63. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/view/346
Roy, Abhra; Paul, Jomon Aliyas (2013, December): Terrorism Deterrence in a Two Country Framework: Strategic Interactions between R&D, Defense and Pre-Emption. Annals of Operations Research, 211(1), 399432. DOI: http://dx.doi.org/10.1007/s10479-013-1431-3
Sanchez-Cuenca, Ignacio; de la Calle, Luis (2013): Domestic Terrorism: The Hidden Side of Political Violence. Annual Review of Political Science, 12, 31-49. DOI: http://dx.doi.org/10.1146/annurev. polisci.12.031607.094133
Sandler, Todd (2010): Terrorism Shocks: Domestic versus Transnational Responses. Studies in Conflict & Terrorism, 33(10), 893-910. DOI: http://dx.doi.org/10.1080/1057610X.2010.508485URL: http://create.usc. edu/sites/default/files/publications//terrorismshocks-domesticversustransnationalresponses.pdf
Santifort, Charlinda; Sandler, Todd; Brandt, Patrick T. (2013, January): Terrorist Attack and Target Diversity: Changepoints and their Drivers. Journal of Peace Research, 50(1), 75-90. DOI: http://dx.doi. org/10.1177/0022343312445651URL: http://create.usc.edu/sites/default/files/publications//terroristattackand targetdiversity-changepointsandtheirdrivers.pdf
Scahill, Timothy (2006, Spring): The Domestic Security Enhancement Act of 2003: A Glimpse into a PostPATRIOT Act Approach to Combating Domestic Terrorism. CR: The New Centennial Review, 6(1), 69-94. DOI: http://dx.doi.org/10.1353/ncr.2006.0024
Schuurman, Bart; Eijkman, Quirine; Bakker, Edwin (2014, June): The Hofstadgroup Revisited: Questioning its Status as a “Quintessential” Homegrown Jihadist Network. Terrorism and Political Violence. Advance Online Publication. DOI: http://dx.doi.org/10.1080/09546553.2013.873719
Schuurman, Bart; Eijkman, Quirine; Bakker, Edwin (2014, August): A History of the Hofstadgroup.
Perspectives on Terrorism, 8(4), 65-81. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/362
Schuurman, Bart et al. (2014, August): Operation Pendennis: A Case Study of an Australian Terrorist Plot. Perspectives on Terrorism, 8(4), 91-99. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/364
Sedgwick, Mark (2012, December): Jihadist Ideology, Western Counter-Ideology, and the ABC Model. Critical Studies on Terrorism, 5(3), 359-372. DOI: http://dx.doi.org/10.1080/17539153.2012.723520
Shipler, David K. (1988): Future Domestic and International Terrorism: Media Perspective. Terrorism, 11(6), 543-545. DOI: http://dx.doi.org/10.1080/10576108808435752
Shterin, Marat; Spalek, Basia (2011): Muslim Young People in Britain and Russia: Intersections of Biography, Faith and History. Religion, State and Society, 39(2-3), 145-154. DOI: http://dx.doi.org/10.1080/09637494.201 1.605926
Simcox, Robin; Dyer, Emily (2013, March): The Role of Converts in Al-Qa'ida-Related Terrorism
Offenses in the United States. CTC Sentinel, 6(3), 20-24. URL: https://www.ctc.usma.edu/v2/wp-content/ uploads/2013/03/CTCSentinel-Vol6Iss32.pdf
Skillicorn, David B.; Leuprecht, Christian; Winn, Conrad (2012, December): Homegrown Islamist Radicalization in Canada: Process Insights from an Attitudinal Survey. Canadian Journal of Political Science, 45(4), 929-956. DOI: http://dx.doi.org/10.1017/S0008423912001023URL: http://post.queensu.ca/~leuprech/ docs/articles/Skillicorn Leuprecht %20Winn 2012 Homegrown%20Islamist%20Radicalization%20in%20 Canada Process%20Insights%20from%20an%20Attitudinal%20Survey Canadian%20Journal%20of%20 Political%20Science.pdf
Skjoldager, Morten (2015): Terrorists Lack Imagination when Choosing Targets in Denmark. In: Magnus Ranstorp; Magnus Normark (Eds.): Understanding Terrorism Innovation and Learning: Al-Qaeda and beyond. (Political Violence). Abingdon: Routledge, 232-250.
Sole, Jeff (2015, June): Under the Microscope: Abuse of Canada’s Immigration and Refugee Determination System. Counter Terrorist Trends and Analysis, 7(5), 4-9. URL: http://www.rsis.edu.sg/wp-content/ uploads/2015/06/CTTA-June-2015.pdf
Sorell, Tom (2011): Preventive Policing, Surveillance, and European Counter-Terrorism. Criminal Justice Ethics, 30(1), 1-22. DOI: http://dx.doi.org/10.1080/0731129X.2011.559057
Southers, Erroll G. (2015): Homegrown Violent Extremism. In: Robert J. Bunker et al. (Eds.): Counterterrorism: Bridging Operations and Theory. (Terrorism Research Center Book). (e-Book). Bloomington: iUniverse.
Spalek, Basia (2011): “New Terrorism” and Crime Prevention Initiatives Involving Muslim Young People in the UK: Research and Policy Contexts. Religion, State and Society, 39(2-3), 191-207. DOI: http://dx.doi.org/1 0.1080/09637494.2011.577202
Speckhard, Anne (2009): The Militant Jihad in Europe: Fighting Home-Grown Terrorism. In: Thomas
M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 143-160. DOI: http:// dx.doi.org/10.3233/978-1-60750-075-9-143
Stan, Mariana (2010): Islamic Terrorism in Europe. In: Hans-Liudger Dienel et al. (Eds.): Terrorism and the Internet: 'Threats - Target Groups - Deradicalisation Strategies. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 67). Amsterdam: IOS Press, 41-52. DOI: http://dx.doi. org/10.3233/978-1-60750-537-2-41
Sylvester, Christine (2014): Let’s not Jump (over) the Guns: Response to Christina Hellmich. Critical Studies on Terrorism, 7(3), 479-483. DOI: http://dx.doi.org/10.1080/17539153.2014.960212
Sylvester, Christine (2014): TerrorWars: Boston, Iraq. Critical Studies on Terrorism, 7(1), 11-23. DOI: http:// dx.doi.org/10.1080/17539153.2014.881202
Taarnby, Michael (2007): Understanding Recruitment of Islamist Terrorists in Europe. In: Magnus Ranstorp (Ed.): Mapping Terrorism Research: State of the Art, Gaps and Future Direction. (Political Violence). Abingdon Routledge, 164-186.
Torelli, Stefano Maria (2015, May): The Jihadist Threat in Italy. Terrorism Monitor, 13(11), 6-7. URL: http:// www.jamestown.org/uploads/media/TerrorismMonitorVol13Issue11 02.pdf
Torok, Robyn (2010): “Make a Bomb in your Mums Kitchen”: Cyber Recruiting and Socialisation of “White Moors” and Home Grown Jihadists. In: Security Research Centre, Edith Cowan University (Ed.): Proceedings of the 1st Australian Counter Terrorism Conference, Edith Cowan University, Duxton Hotel, Perth, Western Australia, November 30-December 2, 2010, 54-61. URL: http://igneous.scis.ecu.edu.au/proceedings/2010/ actc/torok.pdf
van Buuren, Jelle; de Graaf, Beatrice (2014): Hatred of the System: Menacing Loners and Autonomous Cells in the Netherlands. Terrorism and Political Violence, 26(1), 156-184. DOI: http://dx.doi.org/10.1080/09546553 .2014.849932
Van San, Marion (2015): Striving in the Way of God: Justifying Jihad by Young Belgian and Dutch Muslims. Studies in Conflict & Terrorism, 38(5), 328-342. DOI: http://dx.doi.org/10.1080/1057610X.2015.1013776
Veldhuis, Tinka M.; Lindenberg, Siegwart (2012): Limits of Tolerance under Pressure: A Case Study of
Dutch Terrorist Detention Policy. Critical Studies on Terrorism, 5(3), 425-443. DOI: http://dx.doi.org/10.108 0/17539153.2012.723518URL: http://lindenberg.academiaworks.com/articles/2012%20Veldhuis%20&%20 Lindenberg%20Limits%20of%20tolerance%20under%20pressure.pdf
Vermeulen, Floris (2014): Suspect Communities—Targeting Violent Extremism at the Local Level: Policies of Engagement in Amsterdam, Berlin, and London. Terrorism and Political Violence, 26(2), 286-306. DOI: http://dx.doi.org/10.1080/09546553.2012.705254 URL: http://www.wageningenur.nl/upload mm/b/0/ b/4e8bcaed-f74d-41a5-b4e3-d5d41effd102 4d162e2c-9f13-483f-998f-fb1874bb82e0 Understanding%20 radicalisation%20%28III%29%20-%20Floris%20Vermeulen%2024%20march%202015.pdf
Viano, Emilio C. (2015): Investigating and Preventing Terrorism in Multicultural Urban Settings: Is a Balanced Approach Possible? In: Marco Lombardi et al. (Eds.): Countering Radicalisation and Violent Extremism among Youth to Prevent Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 118). Amsterdam: IOS Press, 1-10. DOI: http://dx.doi.org/10.3233/978-1-61499-470- 1-1
Vidino, Lorenzo (2007): The Hofstad Group: The New Face of Terrorist Networks in Europe. Studies in Conflict & Terrorism, 30(7), 579-592. DOI: http://dx.doi.org/10.1080/10576100701385933
Vidino, Lorenzo (2008, August): A Preliminary Assessment of Counter-Radicalization in the Netherlands. CTC Sentinel, 1 (9), 12-16. URL: https://www.ctc.usma.edu/v2/wp-content/uploads/2010/07/CTCSentinel- Vol1Iss9.pdf
Vidino, Lorenzo (2009): Europe’s New Security Dilemma. The Washington Quarterly, 32(4), 61-75. DOI: http://dx.doi.org/10.1080/01636600903224100URL: http://csis.org/files/publication/twq09octobervidino.pdf
Vidino, Lorenzo (2009): Homegrown Jihadist Terrorism in the United States: A New and Occasional Phenomenon? Studies in Conflict & Terrorism, 32(1), 1-17. DOI: http://dx.doi. org/10.1080/10576100802564022
Vidino, Lorenzo (2012): Homegrown Jihadist Terrorism in the United States: A New and Occasional Phenomenon? In: John Horgan; Kurt Braddock (Eds.): Terrorism Studies: A Reader. Abingdon: Routledge, 469-484.
Vidino, Lorenzo (2013, November): The Evolution of Jihadism in Italy: Rise in Homegrown Radicals. CTC Sentinel, 6 (11-12), 17-20. URL: https://www.ctc.usma.edu/v2/wp-content/uploads/2013/11/CTCSentinel- Vol6Iss11-12.pdf
Vidino, Lorenzo (2015, April): Sharia4: From Confrontational Activism to Militancy. Perspectives on Terrorism, 9 (2), 2-16. URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/view/415
Wallace, Don, Jr. et al. (2015, March): Europe: Quo Vadis? Political, Legal, and Security Perspectives.
Terrorism: An Electronic Journal and Knowledge Base, 4(2). URL: http://www.terrorismelectronicjournal.org/ seminar-reports/europe-quo-vadis
Weinberg, Leonard (2014): The Islamic State and American National Security. Democracy and Security, 10(4), 335-342. DOI: http://dx.doi.org/10.1080/17419166.2014.983391
Weine, Stevan et al. (2013): Building Community Resilience to Counter Violent Extremism. Democracy and
Security, 9(4), 327-333. DOI: http://dx.doi.org/10.1080/17419166.2013.766131
Weinhauer, Klaus (2012): Religios motivierter Terrorismus in der europaischen Diaspora: Transnationale Netzwerke, lokale Kleingruppen, Medienkommunikation. In: Klaus Weinhauer; Jorg Requate (Eds.): Gewalt ohne Ausweg? Terrorismus als Kommunikationsprozess in Europa seit dem 19. Jahrhundert. Frankfurt am Main: Campus, 301-316.
Wilner, Alex S.; Dubouloz, Claire-Jehanne (2010, February): Homegrown Terrorism and Transformative Learning: An Interdisciplinary Approach to Understanding Radicalization. Global Change, Peace & Security, 22(1), 33-51. DOI: http://dx.doi.org/10.1080/14781150903487956
Youngs, Gillian (2010, July): The “New Home Front” and the War on Terror: Ethical and Political Reframing of National and International Politics. International Affairs, 86(4), 925-937. DOI: http://dx.doi.org/10.1111/ j.1468-2346.2010.00920.x URL: https://www.e-education.psu.edu/drupal6/files/sgam/virtual space/ thenewhomefront.pdf
Zammit, Andrew (2013): Explaining a Turning Point in Australian Jihadism. Studies in Conflict & Terrorism, 36(9), 739-755. DOI: http://dx.doi.org/10.1080/1057610X.2013.813264
Zegart, Amy (2015, Summer): Insider Threats and Organizational Root Causes: The 2009 Fort Hood Terrorist Attack. Parameters, 45(2), 35-46. URL: http://strategicstudiesinstitute.army.mil/pubs/parameters/Issues/ Summer 2015/7 Zegart.pdf
Zelin, Aaron Y. (2015, March-April): New Zealand’s Jihadis. New Zealand International Review, 40(2), 13-17. URL: https://azelin.files.wordpress.com/2015/03/nziemarch-april2015-new-zealands-jihadis-by-aaron-zelin. pdf
Zhou, Yilu et al. (2005): US Domestic Extremist Groups on the Web: Link and Content Analysis. IEEE Intelligent Systems, 20(5), 44-51. DOI: http://dx.doi.org/10.1109/MIS.2005.96
Zuhur, Sherifa (2009): Decreasing Violence in Saudi Arabia and beyond. In: Thomas M. Pick; Anne Speckhard; Beatrice Jacuch (Eds.): Home-Grown Terrorism. (NATO Science for Peace and Security Series - E: Human and Societal Dynamics, Vol. 60). Amsterdam: IOS Press, 74-98. DOI: http://dx.doi.org/10.3233/978- 1-60750-075-9-74
Grey Literature
Algemene Inlichtingen- en Veiligheidsdienst (AIVD) (2014, September): The Transformation of Jihadism in the Netherlands: Swarm Dynamics and New Strength. (Report). URL: https://www.aivd.nl/binaries/aivd nl/ documenten/publicaties/2014/06/30/the-transformation-of-jihadism-in-the-netherlands/jihadisme eng definitief b5 formaat webversie.pdf
Antonius, Rachad (2009): The Perceptions in Arab and Muslim Communities of Security Trials in Canada. (Research Report for the Ministry of Justice Canada). URL: http://www.ieim.uqam.ca/spip.php?article9444
Atran, Scott et al. (2009, August): Theoretical Frames on Pathways to Violent Radicalization: Understanding the Evolution of Ideas and Behaviors, how they Interact and how they Describe Pathways to Violence in Marginalized Diaspora. (ARTIS Case Studies). URL: http://www.artisresearch.com/articles/ARTIS Theoretical Frames August 2009.pdf
Bakker, Edwin; de Roy van Zuijdewijn, Jeanine (2015, October): Jihadist Foreign Fighter Phenomenon in Western Europe: A Low-Probability, High-Impact Threat. (ICCT Research Paper). URL: http://icct.nl/ publication/jihadist-foreign-fighter-phenomenon-in-western-europe-a-low-probability-high-impact-threat
Bakker, Edwin; Donker, Teije Hidde (2006, December): Jihadi Terrorists in Europe: Their Characteristics and the Circumstances in which they Joined the Jihad: An Exploratory Study. (Clingendael Security Paper). URL: http://www.clingendael.nl/publication/jihadi-terrorists-europe-their-characteristics-and-circumstances- which-they-joined-jihad
Bergen, Peter et al. (2014, September): 2014: Jihadist Terrorism and other Unconventional Threats. (Bipartisan Policy Center Report). URL: http://bipartisanpolicy.org/library/2014-jihadist-terrorism-and-other- unconventional-threats
Bigo, Didier et al. (2014, April): Preventing and Countering Youth Radicalisation in the EU. (Study for the LIBE Committee, PE 509.977). URL: http://www.europarl.europa.eu/RegData/etudes/etudes/ join/2014/509977/IPOL-LIBE ET%282014%29509977 EN.pdf
Bjelopera, Jerome P. (2011, June): Terrorism Information Sharing and the Nationwide Suspicious Activity Report Initiative: Background and Issues for Congress. (CRS Report for Congress R40901). URL: http://fpc. state.gov/documents/organization/166837.pdf
Bjelopera, Jerome P. (2013, January): American Jihadist Terrorism: Combating a Complex Threat. (CRS Report for Congress R41416). URL: https://www.fas.org/sgp/crs/terror/R41416.pdf
Bjelopera, Jerome P. (2014, February): Countering Violent Extremism in the United States. (CRS Report for Congress R42553). URL: https://www.fas.org/sgp/crs/homesec/R42553.pdf
Bjelopera, Jerome P. (2015, June): Sifting Domestic Terrorism from other Illegal Activity. (CRS Insights IN10299). URL: https://www.fas.org/sgp/crs/terror/IN10299.pdf
Briggs, Rachel; Fieschi, Catherine; Lownsbrough, Hannah (2006): Bringing it Home: Community-Based
Approaches to Counter-Terrorism. (Demos Report). URL: http://www.demos.co.uk/files/Bringing%20it%20 Home%20-%20web.pdf
Briggs, Rachel; Silverman, Tanya (2014, December): Western Foreign Fighters: Innovations in Responding to the Threat. (ISD Research Paper). URL: http://www.strategicdialogue.org/ISDJ2784 Western foreign fighters V7 WEB.pdf
Centre of Excellence - Defence Against Terrorism (2014, June): Homegrown Terrorism: Causes and Dimensions. (COE-DAT Activity Report). URL: http://www.coedat.nato.int/publication/workshop reports/02-Homegrown Terrorism Workshop Report.pdf
Cohen, J. Richard (2015, July): The Rise of Radicalization: Is the U.S. Government Failing to Counter International and Domestic Terrorism? Testimony presented before the Committee on Homeland Security, United States House of Representatives, 1st Session, 114th Congress. URL: http://docs.house.gov/meetings/ HM/HM00/20150715/103739/HHRG-114-HM00-Wstate-CohenJ-20150715.pdf
Cooper, Barry (2013, February): Homegrown Jihadists and the Evolution of al-Qaeda. (CDFAI Policy Paper).
URL: http://www.cdfai.org.previewmysite.com/idevicepapers/HomegrownJihadists.htm
Crone, Manni; Harrow, Martin (2010): Homegrown Terrorism in the West, 1989-2008. (DIIS Working Paper 2010:30). URL: http://pure.diis.dk/ws/files/56264/WP2010 30 homegrown terrorism web.pdf
Engebrethsen Smith, Tuva Julie (2015, Spring): Islamic Radicalization in Norway: Preventative Actions. (ICT Articles). URL: http://www.ict.org.il/Article/1339/Islamic-Radicalization-in-Norway
Fenstermacher, Laurie et al. (Eds.) (2010, January): Protecting the Homeland from International and Domestic Terrorism Threats: Current Multi-Disciplinary Perspectives on Root Causes, the Role of Ideology, and Programs for Counter-Radicalization and Disengagement. (Topical Strategic Multi-Layer Assessment [SMA] MultiAgency / Air Force Research Laboratory Multi-Disciplinary White Papers in Support of Counter-Terrorism and Counter-WMD). URL: http://www.start.umd.edU/sites/default/files/files/publications/U Counter Terrorism White Paper Final January 2010.pdf
Fleisher, Blake (2015, Spring): Islamic Radicalization in New Jersey. (ICT Articles). URL: http://www.ict.org.il/ Article/1369/Islamic-Radicalization-in-New-Jersey
Frampton, Martyn (2010): The Return of the Militants: Violent Dissident Republicanism. (ICSR Policy Report). URL: http://icsr.info/2010/11/return-of-the-militants-violent-dissident-republicanism
Gartenstein-Ross, Daveed; Grossman, Laura (2009, April): Homegrown Terrorists in the U.S. and U.K.: An Empirical Examination of the Radicalization Process. (FDD Study). URL: http://www.defenddemocracy.org/ media-hit/homegrown-terrorists-in-the-us-and-uk/
General Intelligence and Security Service (AIVD) ; National Coordinator for Security and Counterterrorism (NCTV) (2015, September): Salafism in the Netherlands: Diversity and Dynamics. (Report). URL: https:// english.aivd.nl/publications/publications/2015/09/24/salafism-in-the-netherlands-diversity-and-dynamics
Gill, Paul et al. (2015, November): What Are the Roles of the Internet in Terrorism? Measuring Online Behaviours of Convicted UK Terrorists. (VOX-Pol Report). URL: http://voxpol.eu/wp-content/ uploads/2015/11/DCUJ3518 VOX Lone Actors report 02.11.15 WEB.pdf
Global Center on Cooperative Security; Human Security Collective (HSC); International Centre for CounterTerrorism (ICCT) (2014, December): Addressing the Foreign Terrorist Fighters Phenomenon from a European Union Perspective. (ICCT Policy Brief). URL: http://www.globalcenter.org/publications/addressing-the- foreign-terrorist-fighters-phenomenon-from-a-european-union-perspective
Gruenewald, Jeff et al. (2014, June): Violence Perpetrated by Supporters of al-Qa’ida and Affiliated Movements (AQAM): Fatal Attacks and Violent Plots in the United States. (START Report to the U.S. Department of Homeland Security). URL: http://www.start.umd.edu/publication/violence-perpetrated-supporters-al-qa- ida-and-affiliated-movements-aqam-fatal-attacks-0
Gruenewald, Jeff et al. (2015, February): Validation of the Nationwide Suspicious Activity Reporting (SAR) Initiative: Identifying Suspicious Activities from the Extremist Crime Database (ECDB) and the American Terrorism Study (ATS). (START Report to the U.S. Department of Homeland Security). URL: http://www. start.umd.edu/publication/validation-nationwide-suspicious-activity-reporting-sar-initiative-identifying
Hahn, Gordon M. (2014, April): Assessing Terrorism in the Caucasus and the Threat to the Homeland. Testimony presented before the House Committee on Homeland Security’s Subcommittee on Counterterrorism and Intelligence, U.S. Congress, on April 3, 2014. URL: http://docs.house.gov/meetings/ HM/HM05/20140403/102041/HHRG-113-HM05-Wstate-HahnG-20140403.pdf
Hasan, Usama (2014, April): USA vs. Babar Ahmad. USA vs. Syed Talha Ahsan. (Quilliam Expert Witness & Personal Testimony). URL: http://www.quilliamfoundation.org/wp/wp-content/uploads/publications/free/ expert-witness-statement-usama-hasan-150414.pdf
Hedayah et al. (2015): Guidelines and Good Practices for Developing National CVE Strategies. URL: http:// www.hedayah.ae/pdf/guidelines-and-good-practices-for-developing-national-cve-strategies.pdf
Jenkins, Brian Michael (2010): Would-Be Warriors: Incidents of Jihadist Terrorist Radicalization in the United States since September 11,2001. (RAND Occasional Papers, OP-292-RC). URL: http://www.rand.org/pubs/ occasional papers/OP292.html
Jenkins, Brian Michael (2014): When Jihadis Come Marching Home: The Terrorist Threat Posed by Westerners Returning from Syria and Iraq. (RAND Perspectives, PE-130-1-RC). URL: http://www.rand.org/pubs/ perspectives/PE130-1.html
Jenkins, Brian Michael (2015, March): Containing Middle East Terror: Measures to Reduce the Threat Posed by Foreign Fighters Returning from Syria and Iraq. (RAND Testimonies, CT-427). URL: http://www.rand.org/ pubs/testimonies/CT427.html
Jenkins, Brian Michael (2015, March): There Will Be Battles in the Heart ofyour Abode: The Threat Posed by Foreign Fighters Returning from Syria and Iraq. (RAND Testimonies, CT-426). URL: http://www.rand.org/ pubs/testimonies/CT426.html
Kean, Thomas H. et al. (2014, July): Today’s Rising Terrorist Threat and the Danger to the United States:
Reflections on the Tenth Anniversary of The 9/11 Commission Report. (Bipartisan Policy Center Report). URL: http://bipartisanpolicy.org/library/rising-terrorist-threat-9-11-commission
Kis-Katos, Krisztina; Liebert, Helge; Schulze, Gunther G. (2010, September): On the Origin of Domestic and International Terrorism. (University of Freiburg, Department of International Economic Policy, Discussion Paper Series, No. 12). URL: ftp://ftp.repec.org/opt/ReDIF/RePEc/fre/wpaper/DP12 kiskatos-liebert-schulze dom-intl-terror.pdf
Klausen, Jytte (2010, September): Al Qaeda-Affiliated and “Homegrown” Jihadism in the United Kingdom, 1999-2010. (ISD Research Report). London: Institute for Strategic Dialogue (ISD).
Kuchins, Andrew C. (2014, April): Terrorism in the Caucasus. Testimony presented before the House Committee on Homeland Security’s Subcommittee on Counterterrorism and Intelligence, U.S. Congress, on April 3, 2014. URL: http://docs.house.gov/meetings/HM/HM05/20140403/102041/HHRG-113-HM05- Wstate-KuchinsA-20140403.pdf
Kuhle, Lene; Lindekilde, Lasse (2010, January): Radicalization among Young Muslims in Aarhus. (CIR Research Report). URL: http://cir.au.dk/fileadmin/site files/filer statskundskab/subsites/cir/radicalization aarhus FINAL.pdf
Kurzman, Charles (2013, February): Muslim-American Terrorism: Declining further. (Triangle Center on Terrorism and Homeland Security Report). URL: http://sites.duke.edu/tcths/files/2013/11/Kurzman Muslim-American Terrorism final2013.pdf
Kurzman, Charles (2014, February): Muslim-American Terrorism in 2013. (Triangle Center on Terrorism and Homeland Security Report). URL: http://sites.duke.edu/tcths/files/2013/06/Kurzman Muslim-American Terrorism in 20131.pdf
Kurzman, Charles (2015, February): Terrorism Cases Involving Muslim-Americans, 2014. (Triangle Center on Terrorism and Homeland Security Report). URL: http://sites.duke.edu/tcths/files/2013/06/Kurzman Terrorism Cases Involving Muslim-Americans 2014.pdf
Landau, Edan (2012, May): “And Inspire The Believers”. (ICT Articles). URL: http://www.ict.org.il/Articles/ tabid/66/Articlsid/1074/currentpage/1/Default.aspx
Leahy, Peter (2014, October): Another Century, another Long War. (ASPI Strategic Insights, No. 75). URL: https://www.aspi.org.au/publications/another-century,-another-long-war
Lebl, Leslie S. (2014, May): Islamism and Security in Bosnia-Herzegovina. (SSI Monographs). URL: http:// www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=1206
Levitt, Matthew (Ed.) (2015, April): From the Boston Marathon to the Islamic State: Countering Violent Extremism. (The Washington Institute for Near East Policy, Policy Focus, No. 139; Stein Counterterrorism Lectures, Vol. 6). URL: http://www.washingtoninstitute.org/policy-analysis/view/from-the-boston-marathon- to-the-islamic-state-countering-violent-extremism
Maher, Shiraz; Frampton, Martyn (2009, March): Choosing our Friends Wisely: Criteria for Engagement with Muslim Groups. (Policy Exchange Report). URL: http://www.policyexchange.org.uk/publications/category/ item/choosing-our-friends-wisely-criteria-for-engagement-with-muslim-groups?category id=24
Malet, David (2015, July): What does the Evidence Tell us about the Impact of Foreign Fighters on Home-Grown Radicalisation? (PACCS Briefing). URL: http://www.radicalisationresearch.org/debate/malet-foreign-fighters- home-grown-radicalization
Manning, Ruth; La Bau, Courtney (2015, August): “In and Out of Extremism”: How Quilliam Helped 10 Former Far-Right and Islamists Change. (Quilliam Report). URL: http://www.quilliamfoundation.org/wp/wp- content/uploads/publications/free/in-and-out-of-extremism.pdf
Margolin, Ephraim (2015, Summer): Islamic Radicalization in California. (ICT Articles). URL: http://www.ict. org.il/Article/1444/Islamic-Radicalization-in-California
Meleagrou-Hitchens, Alexander (2011, September): As American as Apple Pie: How Anwar al-Awlaki Became the Face of Western Jihad. (ICSR Policy Report). URL: http://icsr.info/2011/09/as-american-as-apple-pie- how-anwar-al-awlaki-became-the-face-of-western-jihad
Miller, Erin; Kammerer, William (2015, July): Use of Firearms in Terrorist Attacks in the United States 19702014. (START Background Report). URL: http://www.start.umd.edu/publication/use-firearms-terrorist- attacks-united-states-1970-2014
Miller, Erin; Smarick, Kathleen (2014, July): Profiles of Perpetrators of Terrorism in the United States. (START Research Highlight). URL: http://www.start.umd.edu/publication/profiles-perpetrators-terrorism-united- states-research-highlight
Mulligan, John (2015, June): n.t. Testimony presented at the Hearing before the House Homeland Security Committee “Terrorism Gone Viral: The Attack in Garland, Texas and Beyond”, June 3, 2015. URL: http:// docs.house.gov/meetings/HM/HM00/20150603/103513/HHRG-114-HM00-Wstate-MulliganJ-20150603.pdf
National Coordinator for Security and Counterterrorism (NCTV) (2014, December): Global Jihadism: Analysis of the Phenomenon and Reflections on Radicalisation. (Report). URL: https://english.nctv.nl/Images/ globaljihadism-uk-webversie tcm92-575175.pdf
Nelson, Rick “Ozzie”; Bodurian, Ben (2010, March): A Growing Terrorist Threat? Assessing “Homegrown” Extremism in the United States. (CSIS Report). URL: http://csis.org/files/publication/100304 Nelson GrowingTerroristThreat Web.pdf
Nesser, Petter (2004, April): Jihad in Europe: A Survey of the Motivations for Sunni Islamist Terrorism in PostMillennium Europe. (FFI/RAPPORT-2004/01146). URL: http://www.ffi.no/no/Rapporter/04-01146.pdf
Neumann, Peter R. (2011, June): Preventing Violent Radicalization in America. (Bipartisan Policy Center Report). URL: http://bipartisanpolicy.org/wp-content/uploads/sites/default/files/NSPG.pdf
Neumann, Peter R. et al. (2007, December): Recruitment and Mobilisation for the Islamist Militant Movement in Europe. (King’s College London Study carried out for the European Commission). URL: http://ec.europa. eu/home-affairs/doc centre/terrorism/docs/ec radicalisation study on mobilisation tactics en.pdf
Oftedal, Emilie (2015, January): The Financing of Jihadi Terrorist Cells in Europe. (FFI-rapport 2014/02234). URL: http://www.ffi.no/no/Rapporter/14-02234.pdf
O’Neil, Siobhan (2007, May): Terrorist Precursor Crimes: Issues and Options for Congress. (CRS Report for Congress, RL34014). URL: https://www.fas.org/sgp/crs/terror/RL34014.pdf
Page, Jacqueline (2014, September): The “Home Game”: Countering Violent Extremism within NATO. (NATO Research Paper No. 104). URL: http://www.ndc.nato.int/news/news.php?icode=711
Pandith, Farah (2015, July): The Rise of Radicalization: Is the U.S. Government Failing to Counter International and Domestic Terrorism? Testimony presented before the Committee on Homeland Security, United
States House of Representatives, 1st Session, 114th Congress. URL: http://docs.house.gov/meetings/HM/
HM00Z20150715Z103739ZHHRG-114-HM00-Wstate-PandithF-20150715.pdf
Peil, Florian (2012, October): “Inspire”: Das Jihad-Magazin fur die Diaspora. In: Guido Steinberg (Ed.): Jihadismus und Internet: Eine deutsche Perspektive. (SWP-Studien, 2012/S 23). Berlin: Stiftung Wissenschaft und Politik, 32-44. URL: http://www.swp-berlin.org/de/publikationen/swp-studien-de/swp-studien-detail/ article/jihadismus und internet.html
Phillips, Peter J. (2014, December): Terrorism Perpetrated by Individuals in the United States and Canada. URL: http://papers.ssrn.com/sol3/papers.cfm?abstract id=2262106
Precht, Tomas (2007, December): Home Grown Terrorism and Islamist Radicalisation in Europe: From Conversion to Terrorism. (Research Report Funded by the Danish Ministry of Justice). URL: http://www. justitsministeriet.dk/sites/default/files/media/Arbejdsomraader/Forskning/Forskningspuljen/2011/2007/ Home grown terrorism and Islamist radicalisation in Europe - an assessment of influencing factors 2 .pdf
Pregulman, Ally; Burke, Emily (2012, April): Homegrown Terrorism. (CSIS AQAM Futures Project Case Study Series, No. 7). URL: http://csis.org/publication/homegrown-terrorism
Quiggin, Tom (2014, May): The Muslim Brotherhood in North America (Canada/USA): Version 1.0. (TSEC Network Report). URL: https://docs.google.com/file/d/0B6tM70447biiTmotZUF0MWV0Nnc/edit
Quilliam Foundation (2010, October): Radicalisation on British University Campuses: A Case Study. (Quilliam Briefing Paper). URL: http://www.quilliamfoundation.org/wp/wp-content/uploads/publications/free/ radicalisation-on-british-university-campuses.pdf
Quilliam Foundation (2014, August): The Muslim Brotherhood in the UK. (Quilliam Submission to the National Security Secretariat, United Kingdom). URL: http://www.quilliamfoundation.org/wp/wp-content/ uploads/publications/free/the-muslim-brotherhood-in-the-uk2.pdf
Rasmussen, Nicholas J. (2015, February): Countering Violent Islamist Extremism: The Urgent Threat of Foreign Fighters and Homegrown Terror. Testimony presented before the House Committee on Homeland Security, February 11, 2015. URL: http://www.nctc.gov/docs/Countering Violent Islamist Extremism.pdf
Roggio, Bill (2014, April): Assessing Terrorism in the Caucasus and the Threat to the Homeland. Testimony presented before the House Committee on Homeland Security’s Subcommittee on Counterterrorism
and Intelligence, U.S. Congress, on April 3, 2014. URL: http://docs.house.gov/meetings/HM/
HM05/20140403/102041/HHRG-113-HM05-Wstate-RoggioW-20140403.pdf
Russell, Jonathan; Theodosiou, Alex (2015, July): Counter-Extremism: A Decade on from 7/7. (Quilliam Report). URL: http://www.quilliamfoundation.org/wp/wp-content/uploads/publications/free/counter- extremism-a-decade-on-from-7-7.pdf
Schanzer, David; Kurzman, Charles; Moosa, Ebrahim (2010, January): Anti-Terror Lessons of Muslim- Americans. (Duke University / University of North Carolina at Chapel Hill Research Project Report). URL: https://fds.duke.edu/db/attachment/1255
Schmid, Alex P. (2013, March): Radicalisation, De-Radicalisation, Counter-Radicalisation: A Conceptual Discussion and Literature Review. (ICCT Research Paper). URL: http://icct.nl/publication/radicalisation-de- radicalisation-counter-radicalisation-a-conceptual-discussion-and-literature-review
Schmid, Alex P. (2015, October): Foreign (Terrorist) Fighter Estimates: Conceptual and Data Issues. (ICCT Policy Brief). URL: http://icct.nl/publication/foreign-terrorist-fighter-estimates-conceptual-and-data-issues
Silber, Mitchell D.; Bhatt, Arvin (2007): Radicalization in the West: The Homegrown Threat. (NYPD Report). URL: http://www.nypdshield.org/public/SiteFiles/documents/NYPD Report-Radicalization in the West. pdf
Simcox, Robin (2014, May): American Links to Jihadist Combat Abroad. (Henry Jackson Society Briefing). URL: http://henryjacksonsociety.org/2014/05/30/american-links-to-jihadist-combat-abroad
Simcox, Robin (2015, September): “We will Conquer your Rome”: A Study of Islamic State Terror Plots in the West. (The Henry Jackson Society Report). URL: http://henryjacksonsociety.org/2015/09/29/we-will- conquer-your-rome-a-study-of-islamic-state-terror-plots-in-the-west-2
Simcox, Robin; Dyer, Emily (2013): Al-Qaeda in the United States: A Complete Analysis of Terrorism Offenses. (Henry Jackson Society Report). URL: http://henryjacksonsociety.org/wp-content/uploads/2013/02/Al-
Qaeda-in-the-USAbridged-version-LOWRES-Final.pdf
Sinkkonen, Teemu (2015, January): War on Two Fronts: The EU Perspective on the Foreign Terrorist Fighters of ISIL. (FIIA Briefing Paper 166). URL: http://www.fiia.fi/en/publication/470/war on two fronts
Slootman, Marieke W.; Tillie, Jean N. (2006, October): Processes of Radicalisation: Why some Amsterdam Muslims become Radicals. (IMES Report). URL: http://hdl.handle.net/11245/2.80473
Steinbach, Michael B. (2015, June): n.t. Testimony presented at the Hearing before the House Homeland Security Committee “Terrorism Gone Viral: The Attack in Garland, Texas and Beyond”, June 3, 2015.
URL: http://docs.house.gov/meetings/HM/HM00/20150603/103513/HHRG-114-HM00-Wstate-
Stuart, Hannah (2014, September): British Jihadists: Preventing Travel Abroad and Stopping Attacks at Home.
(CRT Policy Paper No. 1). URL: http://henryjacksonsociety.org/2014/09/12/british-jihadists-preventing- travel-abroad-and-stopping-attacks-at-home
Stuart, Hannah (2014, September): Disrupting Extremists: More Effective Use of Existing Legislation. (CRT Policy Paper No. 3). URL: http://henryjacksonsociety.org/2014/09/25/disrupting-extremists-more-effective- use-of-existing-legislation
Taylor, Francis X. (2015, June): Statement for the Record. Testimony presented at the Hearing before the House Homeland Security Committee “Terrorism Gone Viral: The Attack in Garland, Texas and Beyond”, June 3, 2015. URL: http://docs.house.gov/meetings/HM/HM00/20150603/103513/HHRG-114-HM00- Wstate-TaylorF-20150603.pdf
Thachuk, Kimberley L.; Bowman, Marion E. “Spike”; Richardson, Courtney (2008, May): Homegrown Terrorism: The Threat within. (CTNSP Defense and Technology Papers). URL: http://handle.dtic.mil/100.2/ ADA482139
United States Senate Committee on Homeland Security and Governmental Affairs (HSGAC) (2008, May): Violent Islamist Extremism, the Internet, and the Homegrown Terrorist Threat. (HSGAC Majority & Minority Staff Report). URL: http://hsgac.senate.gov/public/ files/IslamistReport.pdf
United States Senate Committee on Homeland Security and Governmental Affairs (HSGAC) (2012, February): Zachary Chesser: A Case Study in Online Islamist Radicalization and its Meaning for the Threat of Homegrown Terrorism. (HSGAC Majority & Minority Staff Report). URL: http://www.hsgac.senate.gov/imo/ media/doc/CHESSER%20FINAL%20REPORT(1).pdf
Vidino, Lorenzo (2009, December): The Homegrown Terrorist Threat to the US Homeland. (ARI Paper 171/2009). URL: http://www.realinstitutoelcano.org/wps/portal/web/rielcano en/contenido?WCM GLOBAL CONTEXT=/elcano/Elcano in/Zonas in/ARI171-2009
Vidino, Lorenzo (2011): Radicalization, Linkage, and Diversity: Current Trends in Terrorism in Europe. (RAND Occasional Papers, OP-333-OSD). URL: http://www.rand.org/pubs/occasional papers/OP333.html
Vidino, Lorenzo (2013, November): Jihadist Radicalization in Switzerland. (CSS Study). URL: https://edit.
ethz.ch/fsk/publications/DetailansichtPubDB EN?rec id=2752
Vidino, Lorenzo; Hughes, Seamus (2015, June): Countering Violent Extremism in America. (Program
on Extremism Report). URL: https://cchs.gwu.edu/sites/cchs.gwu.edu/files/downloads/CVE%20in%20
Weine, Stevan; Ahmed, Osman (2012, August): Building Resilience to Violent Extremism
among Somali-Americans in Minneapolis-St. Paul. (START Report to the U.S. Department of
Homeland Security). URL: http://www.start.umd.edu/sites/default/files/files/publications/Weine
BuildingResiliencetoViolentExtremism SomaliAmericans.pdf
Wiktorowicz, Quintan (2004): Joining the Cause: Al-Muhajiroun and Radical Islam. (Rhodes College Research Paper). URL: http://insct.syr.edu/wp-content/uploads/2013/03/Wiktorowicz.Joining-the-Cause.pdf
Note
Whenever retrievable, URLs for freely available versions of subscription-based publications have been provided. Thanks to the Open Access movement, self-archiving of publications in institutional repositories or on author homepages for free public use (so-called Green Open Access) has become more common. Please note, that the content of Green Open Access documents is not necessarily identical to the officially published versions (e.g., in case of pre-prints); it might, therefore, not have passed through all editorial stages publishers employ to ensure quality control (peer review, copy and layout editing etc.). In some cases, articles may only be cited after getting consent by the author(s).
About the compiler: Judith Tinnes, Ph.D., studied Information Science and New German Literature and Linguistics at the Saarland University (Germany). Herdoctoral thesis dealt with Internet usage of Islamist terrorists and insurgents. Currently, she works in the research & development department of the Leibniz Institute for Psychology Information (ZPID). She also serves as an Editorial Assistant for Perspectives on Terrorism.
IV. Book Reviews
Counterterrorism Bookshelf: 40 Books on Terrorism & Counter-Terrorism-Related Subjects
Reviewed by Joshua Sinai
This column consists of capsule reviews of recent books from various publishers.
Rajeev Bhattacharyya, Rendezvous With Rebels: Journey to Meet India’s Most Wanted Man (Noida, Uttar Pradesh, India: Harper Collins Publishers India, 2014), 328 pp., US $ 5.80 - US $ 12.86 [Paperback], ISBN: 978-9351363163.
This is a fascinating and well-informed account by a prominent Indian journalist, of his several-months’ long risky journey (with another fellow journalist) to visit rebel bases in eastern Nagaland in Myanmar, from where Indian separatist insurgent groups such as the United Liberation Front of Assam (ULFA), the National Democratic Front of Bodoland (NDFB), the United People’s Party of Kangleipak (UPPK) and the People’s Liberation Army (PLA) launch their cross-border operations into India. These visits entailed extensive interviews with the leaders and operatives of these groups, especially those associated with the UPPK. The author concludes that prospects for peaceful resolution of these separatist insurgencies depend on improved cooperation between the Indian and Myanmar governments on these issues and increased acceptance of the primacy of the sovereignty of Assam within the context of the northeast “as the core issue” of such negotiations (p. 291).
Gerhard Bowering (Ed.) Islamic Political Thought: An Introduction (Princeton, NJ: Princeton University Press, 2015), 304 pp., US $ 24.95 [Paperback], ISBN: 9780691164823.
The contributors to this edited volume present a comprehensive overview of the origins and evolution of Islamic political thought from the birth and rise of Islam in the seventh century to the current period. Following the editor’s introductory overview, the chapters cover topics such as the role of authority and governance in Islam (particularly in the aftermath of the Prophet Muhammad’s life), for instance, as expressed in the concept of the Caliphate; the Quran as Islam’s ‘holy book’; the roles of Shari’a (religious law) and the ulama (the body of religious scholars) in society; how the religion views different forms of jihad (e.g., how they are expressed internally and externally); how Islam regards women and minorities; and the nature of the relations between Islamic fundamentalism, revival and reform, and modernity. As an overview of these components of Islamic political thought, most of the chapters are authoritatively and clearly written. The chapter on “Modernity” by Armando Salvatore, however, is one of the book’s weakest, as it is filled with academic jargon that makes little sense to those who understand the components of modernity, such as his conclusion that “the significance of Islamic globalism at the present stage of entanglement of multiple modernities might support the decoupling of modernization from Westernization and a reconstruction of modernity along specific civilizational paths conforming to their foundational images, symbols, and discursive patterns.. ..'the growing Islamic focus on transnational interconnectedness transcends a Eurocentric modernist approach to modernity confined within the rationale of nation-states or of new aggregations thereof, like the European Union” (p. 150).
James Defronzo, Revolutions and Revolutionary Movements [5th edition] (Boulder, CO: Westview Press, 2015), 520 pp., US $ 50.00 [Paperback], ISBN: 9780813349244.
This textbook is a comprehensive and interesting account of important political revolutions in the 20th and 21st centuries, based on a conceptual framework for each case that examines “the significance of factors that appear necessary to the success of all revolutions,” how individual revolutionary conflicts played out, and “the history and unique social characteristics generating the essential revolution-promoting factors.” (p. 5) Beginning with an introductory overview of social movements and revolutions, case studies are presented of the revolutions in Russia and Eastern Europe, China, Vietnam, Cuba, Nicaragua, Iran (and Islamic Fundamentalism), South Africa, what the author terms as ‘democratic revolutions’ in Venezuela and Bolivia, and the Arab revolutions in Middle Eastern countries such as Egypt, Libya, Syria and Tunisia. The concluding chapter presents comparisons between the case studies, a critique of certain prominent theories of revolution, and prospects for the future. Each case study concludes with references for further readings, including selected film documentaries.
Phil Gurski, The Threat From Within: Recognizing Al Qaeda-Inspired Radicalization and Terrorism In The West (Lanham, MD: Rowman & Littlefield, 2016), 162 pp., US $ 75.00 [Hardcover], US $ 32.00 [Paperback], ISBN: 978-1-4422-5560-9.
This is an interesting conceptual and empirical examination of the pathways of radicalization into terrorism in Western countries, with a special focus on al Qaida type groupings and the lone wolves they inspire, including those that operate in Canada. The author, a recently retired veteran analyst in Canadian intelligence, is well positioned to discuss these issues, including the application of practical methodologies to analyze them. The book is divided into five chapters: the first chapter examines the key conceptual drivers, ranging from socio-economic backgrounds and psychological characteristics to physical venues (such as religious institutions, schools, the Internet, and foreign conflict zones) that underlie radicalization into terrorism; the second chapter presents key concepts from Islam and Muslim history that characterize al Qaida-type narratives that help to shape an “extremist mindset”; the third chapter discusses what the author considers to be 12 key behaviors and attitudes that characterize those that embark on such violent radicalization (such as intolerant religiosity, rejection of Western ways and policies, and obsession with violent jihad and martyrdom); the fourth chapter summarizes major Canadian cases of al Qaida-inspired terrorism since 9/11 (including the “Toronto 18” and Canadian Somalis);while the fifth chapter discusses the author’s recommendations for effective counter-extremism and counter-terrorism strategies. Although the book was written before the emergence to prominence of the Islamic State (IS/ISIL) as the most lethal expression of al Qaida-type Jihadist terrorism facing Western countries, the author’s excellent analysis also can serve to understanding and countering it better.
Bill Harlow (Ed.), Rebuttal: The CIA Responds to the Senate Intelligence Committee’s Study of Its Detention and Interrogation Program (Annapolis, MD: Naval Institute Press, 2015), 392 pp., US $ 16.95 [Paperback], ISBN: 978-1-59114-587-5.
This book is a rebuttal by the Central Intelligence Agency (CIA) and its former top officials to what they considered to be inaccuracies in the 6,000-page report issued in December 2014 by the U.S. Senate Select Committee on Intelligence (SSCI), which was highly critical of the CIA’s detention and interrogation of al Qaida terrorists in the aftermath of 9/11. The volume is divided into three sections: short rebuttal articles by eight of the CIA’s former top officials, including George J. Tenet, Porter Goss and General (Retired) Michael
V. Hayden; the official CIA response (with classified details redacted); and the Minority Report issued by the SSCI’s Republican Senators. This volume is an important and indispensable contribution to understanding the factors underlying the detention and interrogation component in America’s counterterrorism campaign in response to al Qaida’s horrific attacks in 9/11 and its aftermath.
Larissa Van Den Herik and Nico Schrijver (Eds.), Counter-Terrorism Strategies in a Fragmented International Legal Order: Meeting the Challenges (New York, NY: Cambridge University Press, 2013), 798 pp., US $ 155.00 [Hardcover], US $ 49.99 [Paperback], ISBN: 978-1107025387.
The contributors to this edited volume, who are prominent legal scholars from around the world, examine the roles and applications of international legal instruments in enhancing the legal basis for governments’ counterterrorism measures. With acts of terrorism defined as “criminal” in nature, the book is divided into three parts: improving international cooperation in the investigation and prosecution of terrorist acts, the legal basis for the use of force against terrorists, and the intersection between international human rights law and international humanitarian law in counter-terrorism. An Annex provides the “Leiden Policy Recommendations on Counter-Terrorism and International Law.”
Institute for Economics & Peace, Global Terrorism Index 2015: Measuring and Understanding the Impact of Terrorism (New York, NY: Institute for Economics & Peace, 2015), 108 pp., www.economicsandpeace.org.
This third edition of the Global Terrorism Index provides a comprehensive summary of the key global trends and patterns in terrorism over the last 15 years, with a special emphasis on 2014. The monograph consists of key summary findings on terrorism trends, the economic cost of terrorism, and correlates and drivers of terrorism (such as the presence of political violence, the nature of a country’s safety and security environment, pervasive lack of respect for human rights, with different drivers operating in wealthier than in poorer countries). Among the report’s numerous findings is that terrorism has continued its escalatory trajectory, with the total number of fatalities from terrorism reaching 32, 685 in 2014, constituting an 80 percent increase from 18, 111 the previous year. The top ranked countries in terms of their fatalities from terrorism in 2014 are (in order): Iraq, Afghanistan, Nigeria, Pakistan, Syria, India, Yemen, Somalia, Libya, and Thailand. In another interesting ranking, the report finds that the most lethal terrorist groups during the period of 2010-2014 were Boko Haram, ISIL, the Taliban, al-Shabaab, and another Nigerian group, the Fulani militant group. In terms of the economic cost of countering terrorism, the report finds that the United States “accounts for 70 percent of total global spending on national security agencies.” (p. 64) The report also includes contributions from other experts, who discuss issues such as a portrait of the Islamic State (IS) and the challenges and opportunities of measuring terrorism. The Annex includes an explanation of the methodology used in formulating the Index. The report is produced by the Institute for Economics and Peace, based on data from the Global Terrorism Database (GTD), which is collected by the National Consortium for the Study of Terrorism and Responses to Terrorism (START), University of Maryland, College Park.
William McCants, The ISIS Apocalypse: The History, Strategy, and Doomsday Vision of the Islamic State (New York, NY: St. Martin’s Press, 2015), 256 pp., US $ 26.99 [Hardcover], ISBN: 978-1250080905.
This book examines the “religious fervor, strategic calculation, and doomsday prophesy” that play a role in shaping the Islamic State’s (also known as IS, ISIL or ISIS) terrorist warfare and global ambitions. Despite the book’s relatively short length: some 160 pages of text, 20 pages of appendices, and 50 pages of detailed footnotes, its use of primary sources in Arabic, such as ancient Islamic texts and al Qaida and Islamic State documents (some of which are included in the appendices) and the author’s expertise on these issues, make it a highly authoritative examination that will be indispensable to those interested in understanding the nature of this group and its ever widening areas of operation.
Farish A. Noor, The Malaysian Islamic Party PAS 1951-2013: Islamism in a Mottled Nation (Amsterdam, The Netherlands: Amsterdam University Press/Distributed by The University of Chicago Press, 2014), 280 pp., US $ 99.00 [Hardcover], ISBN: 978-90-8964-576-0.
This is a highly detailed and comprehensive examination of the origins and evolution of the Pan-Malaysian Islamic Party (PAS) from its establishment in 1951 until the current period. The author concludes that “the viability of the various discourses within PAS, and the viability of PAS itself as a party, depend on the structural-economic circumstances that may or may not allow Islamism to present itself as a genuine alternative to the dominant paradigms of capital-driven development and the modern postcolonial nationstate” (p. 239). Such insights also apply to other Islamist-based parties around the world that attempt to capture state power against their secular competitors through an electoral process.
Thomas Small and Jonathan Hacker, Path of Blood: The Story of Al Qaeda’s War on the House of Saud (New York, NY: The Overlook Press, 2015), 480 pp., US$ 32.50 [Hardcover], ISBN: 978-1468310603.
An interesting account, based on the authors’ investigative reporting, of al Qaida’s ambition to attack and undermine the Saudi Arabian regime, which it claims has no religious legitimacy to rule over Mecca and Medina, the two holiest places in Islam. Al Qaida also hopes that by conquering the birthplace of Islam, it would succeed in re-establishing a Muslim Caliphate (Empire) that would stretch worldwide. With al Qaida ‘Central’ and its affiliate Al Qaida in the Arabian Peninsula (AQAP) continuing to target Saudi Arabia, whether through cells in the Kingdom itself or from its bases in Yemen, and the Saudi-led military campaign against al Qaida’s forces and Shi’ite tribes in Yemen, the accounts presented in this book are especially pertinent. The authors are prominent British documentary producers and experts on the Middle East.
Brian Stewart and Samantha Newbery, Why Spy? The Art of Intelligence (London, England: Hurst & Company/New York, NY: Oxford University Press, 2015), 288 pp., US $ 29.95 [Hardcover], ISBN: 9781849045131.
This is a highly informative examination of why governments engage in espionage and how intelligence products impact on policy-making. The book is based primarily on Brian Stewart’s extensive practitioner work in British intelligence. Following an introductory overview that includes a definition of intelligence terms, the book is divided into four parts: case studies of British intelligence operations in which Mr. Stewart was involved such as the Malayan Emergency from 1948 to 1960, Vietnam, and China; a discussion of the organization and methodology of intelligence; prominent cases of intelligence failures, such as Pearl Harbor, Cuba (in terms of the Bay of Pigs and the Missile Crisis in the early 1960s), and Iraq (the intelligence imbroglio over the supposed weapons of mass destruction by Saddam Hussein’s regime); and the use of “noninformation” gathering intelligence operations in the form of special operations, deception operations and assassination.
Ioannis Tellidis and Harmonie Toros, (Eds.), Researching Terrorism, Peace and Conflict Studies (New York, NY: Routledge, 2015), 246 pp., US $ 155.00 [Hardcover], ISBN: 9781138018174.
The contributors to this edited volume, which is part of the discipline of “Critical Terrorism Studies,” examine the important topic of how the academic fields of terrorism and conflict resolution can be harnessed to inform each other to more effectively resolve terrorist conflicts rather than let them continue protracted and unresolved. This objective is attempted through the first part’s discussion of the theoretical underpinnings of both fields (chapters 2-5) and the second part’s case studies (chapters 6-11). As is the case with other volumes in “Critical Terrorism Studies”, this attempt is marred by the authors’ over-use of academic jargon in their writings. Examples include the following: “the ontological and epistemological status of security” “the dysfunctionality of the liberal peace and the opportunities offered by post-liberal... peacebuilding frameworks” (p. 2); “The lack of reflexivity on the ontological status of its central concepts and assumptions is a serious obstacle, and one that is largely the consequence of the domination of the field’s positivist orientation” (p. 8); and, rather astonishingly, arguing that, in terms of a supposed similarity between Islamist ‘networks and groups’ and their Western counterparts, “there is very little to separate neoMarxist, postmodern and post-Gramscian approaches from the ideological underpinnings of al-Qaeda and similar Islamist and jihadist groups.” (p. 8) For those inclined to follow such academic jargon, the volume’s conceptual chapters will be of interest, although some of the case studies on the conflicts in Colombia, the Basque region in Spain, and Northern Ireland, do provide insight that will benefit all readers.
Lorenzo Bosi, Charles Demetriou and Stefan Malthaner, Dynamics of Political Violence: A Process-Oriented Perspective on Radicalization and the Escalation of Political Conflict (Burlington, VT: Ashgate 2014), 320 pp., US$ 134.96 [Hardcover], ISBN: 978-1-4094-4351-3.
The contributors to this edited volume examine the processes in which terrorist type violence emerges, escalates, and, in some cases, declines, by focusing on “the recurring causal patterns that shape trajectories of radicalization.” (p. 2) The book is divided into four parts: the dynamics that lead to violent conflict in the interaction between oppositional movements/groups and the state; the dynamics that lead to conflictual intra-movement interactions (such as in the cases of Northern Ireland in 1968-1969 and the South African Liberation Movement); the dynamics that lead to the transformation of social movements (such as the Islamization of Palestinian nationalism); and the dynamics of transnational diffusion (such as the role of the Anarchist Diaspora in radicalizing the insurgent opposition in Franco’s Spain, and the diffusion of political violence in Europe in the 1968 protest revolts in Turkey, Paris, and elsewhere over the Arab-Israeli conflict). In an interesting chapter, Ekaterina Stepanova, of the Institute of the World Economy and International Relations (IMEMO), Moscow, Russia, discusses the evolution of al Qaida-type terrorism which makes possible a “post-Qaeda” configuration, since it is not dependent on ‘networks’ with its “actor-oriented approach and the mobilizing potential of its extremist ideology providing it with asymmetrical advantages over its more powerful state adversaries”. The concluding chapter by Martha Crenshaw, of Stanford University, provides an excellent discussion of the volume’s main findings.
Kathleen Gleeson, Australia’s ‘War on Terror’ Discourse (Burlington, VT: Ashgate, 2014), 286 pp, US$ 134.96 [Hardcover], ISBN: 978-1-4724-1985-9.
Using Australia as its primary case study, this book is an interesting textual examination of how politicians in such a representative democracy “justify their policy decisions” in countering terrorism. The post 9/11 period of 2001 until the end of Prime Minister John Howard’s government in November 2007 serves as the primary time period for the textual examination, although other relevant periods in Australian history are discussed as well. Expressions of dissent against government counter-terrorism policies are also examined. The concluding chapter summarizes the book’s key findings and argues for a “less dangerous path” in counterterrorism political discourse than the one employed by the Howard government, with a focus on why terrorist acts, such as 9/11 were committed, accompanied by increased use of “consultation and open dialogue between many nations” in crafting response measures, all the while respecting and preserving “civil, legal and human rights and uphold[ing] democratic principles” (pp. 231-232).
Rebecca Richards, Understanding Statebuilding: Traditional Governance and the Modern State in Somaliland (Burlington, VT: Ashgate Publishing Company, 2014), 228 pp., US $ 107.96 [Hardcover], ISBN: 978-1-47242589-8.
This book’s objective is to provide a framework for conceptualizing what the author terms “acceptable statehood” within the overall context of externally-led state-building in what are considered fragile and failing states. Using Somaliland as the primary case study, the author attempts to demonstrate that by assuming “local ownership and legitimacy” (especially through the incorporation of clan-based politics) Somaliland has succeeded, at least to a certain extent, along the path of a viable state-building process, while Somalia itself is riven by internal strife.
Joseph Cirincione, Nuclear Nightmares: Security the World Before It Is Too Late (New York, NY: Columbia University Press, 2013), 280 pp., US $ 26.95 [Hardcover], US $ 18.95 [Paperback], ISBN: 9780231164047.
This is a well-argued account of the threats presented, as the author explains, by “the current global arsenal of some 17,000 nuclear weapons and the risk of their use, whether by accident or design”(p. 1). Also discussed are issues such as the spread of nuclear proliferation and the cost of such weapons. The book discusses which countries possess the largest nuclear arsenals, and, among them, who poses the greatest danger. It also addresses future trends in nuclear proliferation, the damage caused by nuclear detonations, and international efforts to reduce and eliminate these threats. With regard to the possibility of a terrorist group’s acquisition of a nuclear weapon, the author writes that this is of major concern since “terrorists could acquire an assembled nuclear warhead or enough fissile material to construct a bomb,” and that militant groups in Pakistan “have staged major attacks on military bases, including ones suspected of housing nuclear weapons” (p. 121).
Charity Scribner, After the Red Army Faction: Gender, Culture, and Militancy (New York, NY: Columbia University Press, 2015), 312 pp., US $ 50.00 [Hardcover], ISBN: 9780231168649.
This is an interesting account of what the author terms “post-militant culture - the charged field of literature, art, and criticism that responds to militancy and political violence,” which, in this case, is applied to analyzing the long-lasting impact of the Red Army Faction during and following its period of operations in Germany from the 1970s to the 1990s.
M.L.R. Smith and David Martin Jones, The Political Impossibility of Modern Counterinsurgency: Strategic Problems, Puzzles, and Paradoxes (New York, NY: Columbia University Press, 2015), 272 pp., US $ 45.00 [Hardcover], ISBN: 9780231170000.
This is a provocative account of what the authors term “the ambiguities and dissonances - the puzzles and enigmas - in the contemporary appreciation and practices of counterinsurgency: an idea that in the first decade of the twenty-first century assumed a prominent position in Western military and strategic thought.” (pp. ix-x) Although one may argue that this discussion overlooks a large body of literature on counterinsurgency (COIN), the authors do make a valid point that some of the writings on COIN are “highly ideological in orientation,” and tend “to mythologize the past, distort historical understanding, ignore contingency, and obscure complexity...” (pp. 182-183).
Tal Jonathan-Zamir, David Weisburd and Badi Hasisi (Eds.), Policing in Israel: Studying Crime Control, Community Policing, and Counterterrorism (Boca Raton, FL: CRC Press, 2016), 263 pp., US $ 79.96 [Hardcover], ISBN: 9781498722568.
The contributors to this volume are prominent Israeli criminologists. They examine three significant aspects of policing in Israel: crime control (e.g., analyzing crime “hot spots”, measures to ensure road safety, and the impact of the organization of the criminal justice system on crime rates); police and community (e.g., the relationship between the police and minority communities, such as Israeli Arabs); and policing terrorism, with the Israeli police also responsible for maintaining internal security. Also discussed is media coverage of police performance, including in confronting terrorism. Although the Israeli police has recently experienced several high-profile scandals involving financial corruption and mismanagement of criminal cases, it is hoped that the installation of Roni Alsheikh, the former deputy head of the General Security Service (Shin Bet) as Police Commissioner, will restore the type of efficient policing that is so well discussed in this important volume.
David Lowe, Policing Terrorism: Research Studies into Police Counterterrorism Investigations (Boca Raton, FL: CRC Press, 2016), 203 pp., US $ 71.96 [Hardcover], ISBN: 9781482226836.
Written by a former British counterterrorism detective, this highly useful practitioner-focused book is divided into two sections on policing terrorism. The first section, “The Law Governing Terrorism Investigations,” addresses issues such as how terrorism is legally defined, government policies and statutory preventative measures against terrorism, the need to balance the interests of national security and individual civil liberties in conducting surveillance and information sharing on terrorist suspects and how terrorism is funded. The volume also includes a comparative study of how terrorism-related laws are applied in a number of states. The second section, “Investigating Terrorism,” discusses issues such as the need for police officers to understand the levels of legal powers granted them to track the radicalization of individuals into terrorism. The volume also discusses how to recruit and handle informants, including when it comes to court presentations.
Elena Mastors, Breaking Al-Qaeda: Psychological and Operational Techniques [2nd edition], (Boca Raton, FL: CRC Press, 2014), 241 pp., US $ 55.96 [Hardcover], ISBN: 9781482230116.
This book is a comprehensive examination of the types of psychological and operational techniques that are effective in countering and defeating the terrorist threats presented by al Qaida and its affiliates. The author, a former U.S. government intelligence analyst and currently an academic, is well positioned to analyze these issues. In this new edition (the 1st dates from 2010), the author discusses the magnitude of the threats presented by al Qaida, including its motivation and the socio-demographic background of its operatives; the measures introduced by the U.S. government after 9/11 to counter al Qaida in the form of the establishment of the Department of Homeland Security and the passage of the Patriot Act to upgrade surveillance and arrest capabilities. The remaining chapters discuss the nature of intelligence collection against terrorism; the use of psychological influence techniques to undermine terrorist propaganda; understanding the nature of terrorist leadership, including their personal characteristics, their operating environment, their reliance on “advisers”, and their “information” environment; how to break terrorist groups by identifying their fissure points, security vulnerabilities, competition over internal resources that can be exploited; and the use by governments of psychology-based information campaigns to weaken terrorist groups on the individual, group, and intra-terrorist group levels.
Malcolm W. Nance, The Terrorists of Iraq: Inside the Strategy and Tactics of the Iraqi Insurgency 2003-2014 (Boca Raton, FL: CRC Press, 2015), 404 pp., US $ 59.95 [Hardcover], ISBN: 978-1498706896.
With the resumption of the civil war in Iraq following the withdrawal of U.S. military forces in December 2011, this book is an important contribution to understanding the strategy and tactics being employed by the al Qaida/Islamic State insurgency and the measures required in response to defeat them. In this comprehensive and detailed account, the author discusses the nature of the insurgency; the groups that compose it (ranging from al Qaida to the Islamic State); their strategy, tactics, internal organization, and weaponry; and the nature of the foreign volunteers that have joined their forces - all the components that need to be considered in formulating effective countermeasures.
Scott Nicholas Romaniuk and Stewart Tristan Webb (Eds.) Insurgency and Counterinsurgency in Modern War (Boca Raton, FL: CRC Press, 2016), 312 pp., US $ 55.96 [Hardcover], ISBN: 978-1-4822-4765-7.
The contributors to this volume examine the nature of insurgency and counterinsurgency in all its dimensions. This ranges from a discussion of how to conceptualize insurgencies, counterterrorism and counterinsurgency, to analyzing case studies of insurgencies in Afghanistan, Pakistan, Syria, Indonesia, Mali, Burma, the Caucasus, and the Balkans. Also analyzed are various types of insurgencies such as those marked by a “nexus” between crime and terrorism, and global insurgencies by groups such as al Qaida and its affiliates. The volume’s chapters are accompanied by numerous illustrations, tables, and chronologies of incidents, making it a valuable textbook.
Arabinda Acharya, Whither Southeast Asia Terrorism? (London, England, UK: Imperial College Press, 2015), 312 pp., US $ 115.00 [Hardcover], ISBN: 978-1783263899.
This is a comprehensive and well-organized account of the evolution of terrorism in Southeast Asia since the October 2002 Bali bombings, which were carried out by Jemaah Islamiyah, al Qaida’s regional affiliate. Utilizing a differentiated approach to analyze the region’s terrorist-based conflicts, the book’s chapters examine topics such as the relationship between Islamist militancy and terrorism, the maritime dimensions of terrorism as well as the responses to terrorism by individual states and regional organizations. Among the author’s well-informed conclusions is the following insight: “the terrorist threat is neither uniform across the region nor an existential concern for all the concerned countries, despite the manner that it is framed in securatization scholarship. Such a discourse, moreover, fails to take into account the varied political cultural and historical contexts in which the conflicts themselves are embedded in the region” (p. 251).
Rohan Gunaratna and Mohamed Bin Ali (Eds.), Terrorist Rehabilitation: A New Frontier in Counter-terrorism (London, England, UK: Imperial College Press, 2015), 272 pp., US $ 95.00 [Hardcover], ISBN: 978-1-78326743-9.
The contributors to this volume examine the role of terrorist rehabilitation (which is also related to countering violent extremism and disengagement from terrorism), which constitutes, when applicable, an important tool in counterterrorism. Following an overview of the evolution and future direction of the practice of terrorist rehabilitation (and its related components), the chapters discuss rehabilitation programs in Indonesia, Saudi Arabia, Singapore and Sri Lanka, as well as more general approaches to counter al Qaida- type extremist religious beliefs such as Jihad, Salafism, and Takfir (the practice of excommunication) and the notion that “Islam is under attack.” The final chapter provides a useful assessment of the elements involved in tracking the outcome of terrorist rehabilitation programs and the steps that are necessary to implement best practices in regional contexts.
Rohan Gunaratna, Jolene Jerard and Salim Mohamed Nasir (Eds.) Countering Extremism: Building Social Resilience Through Community Engagement (London, England, UK: Imperial College Press, 2013), 228 pp., US $ 58.00 [Hardcover], ISBN: 978-1-908977-52-6.
A central theme running through this edited book is that with extremism constituting one of the precursors to terrorism and insurgency, it is essential to counter and moderate extremism at the local level in order to promote resilience in susceptible communities. Specific cases of community engagement and resilience building are discussed for Singapore, South Asia, the Middle East, and the United Kingdom, as well as on a general level, with accounts of countering extremism on the Internet. This book is the outcome of a conference held in Singapore in September 2011.
Muhammad Haniff Hassan, The Father of Jihad: Abd Allah Azam’s Jihad Ideas and Implications to National Security (London, England, UK: Imperial College Press, 2014), 368 p., US $ 125.00 [Hardcover], ISBN: 9781-78326-287-8.
This is a valuable account of the writings and life of Abdullah Yusuf Azzam, one of the iconic figures in shaping the Jihadi religious ideology of groups such as al Qaida, of which he was one of the founding members. Azzam, a Palestinian Islamic scholar and theologian, was subsequently assassinated under mysterious circumstances in Peshawar, Pakistan, in November 1989. The author’s utilization of a qualitative literature review to examine Azzam’s books, articles and transcripts of his sermons and speeches, makes this volume an important contribution to the scholarship on Jihadi theologians, as it also makes extensive reference to Azzam’s theological predecessors, such as the Egyptian Sayyid Qutb. One of Azzam’s theological innovations, according to the author, was his call for making it a “duty” for Muslims “to reclaim all past Muslim territories that are currently part of, or occupied by, non-Muslim states, and...to wage jihad al-talb (offensive jihad) against non-Muslim territories until they are either part of Dar Al-Islam or submit to the rule of Dar Al-Islam.” (p. 2) The author also discusses the implications of Azzam’s ideas for current national security and provides theologically-based recommendations for countering Jihadism.
Jolene Jerard and Salim Mohamed Nasir (Eds.), Resilience and Resolve: Communities Against Terrorism (London, England, UK: Imperial College Press, 2015), 180 pp., US $ 85.00 [Hardcover], ISBN: 978-1-78326773-6.
The contributors to this volume examine the role of local communities in mitigating the threat of terrorism, with a focus on countering al Qaida-type Islamist terrorism. To achieve community resilience against terrorism, the contributors propose countering and deconstructing extremist ideologies, promoting religious harmony, and ensuring that state agencies that counter terrorism, such as law enforcement, are used in ways that promote community resilience.
Muhammad Tito Karnavian, Explaining Islamist Insurgencies: The Case of al-Jamaah al-Islamiyya and the Radicalisation of the Poso Conflict, 2000-2007 (London, England, UK: Imperial College Press, 2015), 304 pp., US $ 105.00 [Hardcover], ISBN: 978-1-78326-485-8.
This is an examination of how the process of Islamist radicalization might eventually result in al-Jamaah al-Islamiyyah-type terrorism through a case study of how such processes played out in the town of Poso, in Indonesia, during the year 2000 to 2007. The author focuses on the causal factors that play out in the radicalization process: disaffected persons, an enabling group, and its legitimizing ideology. What is especially important about this study, as the author concludes (and which this reviewer concurs), is its usefulness in providing a theoretical framework for policy interventions that could be applied (once adjusted to the local context) to regions that “have become targets of Islamist radicalization, such as conflict areas like Maluku (Ambon),,the southern Philippines as well as non-conflict areas like Java” (p. 238) as well as other areas around the world.
Erik Nemeth, Cultural Security: Evaluating the Power of Culture in International Affairs (London, England, UK: Imperial College Press, 2015), 312 pp., US $ 110.00 [Hardcover], ISBN: 978-1783265480.
With the widespread plunder, illicit sales, and destruction of cultural and historical antiquities by terrorist groups ranging from the Afghan Taliban to the Islamic State, this book’s examination of this aspect of ‘cultural security’ is of great importance. The volume is divided into three sections: the history of cultural plunder and destruction (including by the Nazis in the Second World War), measures to counter such illicit activities through intelligence, including monitoring art sales around the world, and incorporating the securing of such cultural property into states’ foreign policies.
Maria A. Ressa, From Bin Laden to Facebook: 10 Days of Abduction, 10 Years of Terrorism (London, England, UK: Imperial College Press, 2013), 308 pp., US $ 35.00 [Hardcover], ISBN: 978-1908979537.
An interesting account by a veteran journalist of the role of the Internet’s social networks in radicalizing adherents and mobilizing them to engage in al Qaida-type Islamist terrorism around the world, with a special focus on the Philippines and Indonesia.
Albrecht Schnabel and Rohan Gunaratna, (Eds.), Wars From Within: Understanding and Managing Insurgent Movements [Second Edition] (London, England, UK: Imperial College Press, 2015), 496 pp., US $ 145.00 [Hardcover], ISBN: 978-1-78326-556-5.
This is a revised and updated edition of the editors’ 2006 volume Understanding and Managing Insurgents Movements (published by Marshall Cavendish Academic, Singapore). Following an introductory overview of challenges presented by contemporary insurgencies, the chapters are divided into two parts: first, a classification of insurgencies as ethnic, religious, ideological, as well as a discussion of the Internet as a force multiplier for modern insurgencies; and second, case studies of insurgencies in the Balkans, India, Sri Lanka, Indonesia, Lebanon (the case of Hizballah), as well as al Qaida as a global insurgency. In the concluding chapter, the editors discuss the challenges involved in addressing contemporary insurgencies.
Javier Argomaniz and Orla Lynch (Eds.) International Perspectives on Terrorist Victimisation: An Interdisciplinary Approach (New York, NY: Palgrave Macmillan, 2015), 288 pp., US $ 100.00 [Hardcover], ISBN: 9781137347107.
The contributors to this volume examine the diverse experiences of victims of terrorism and the types of responses by governments to their plight. The plight of victimhood is complex, according to the book’s preface, because it involves “the interactivity at times between victims and perpetrators, the potential for counter-terrorism measures to create victims and a complex lifestyle relationship between being victimized and the potential for politicization, media intrusion and re-traumatisation” (p. viii). To examine these issues, the book is divided into three parts: victims’ experiences (e.g., in general and in the cases of the victims of the Spanish ETA’s violence and the traumas experienced by child soldiers in Sri Lanka); support for victims (e.g., providing financial compensation and public health treatment for victims of terrorism); and victims of counter-terrorism campaigns (e.g., the victimization of some Muslim youth in Western countries, the impact of drone attacks and suicide bombings on their respective Pakistani victims, and the consequences of targeted policing by the New York Police Department against the city’s Muslim communities).
Colin Wight, Rethinking Terrorism: Terrorism, Violence and the State (New York, NY: Palgrave/Macmillan Education, 2015), 272 pp., US $ 95.00 [Hardcover], US$35.00 [Paperback], ISBN: 978-0-230-57376-5.
This is a theoretical account of contemporary types of terrorism and their impact on the international system. The author, a Professor of Government and International Relations at the University of Sydney, Australia, was part of a group that developed the sub-discipline of “Critical Terrorism Studies.” This book, which is clearly written and well-reasoned, presents a comprehensive overview of the interplay between terrorism, here interpreted as a violent form of protest, and its state adversary. These issues are covered through an examination of the historical development of the modern state, types of violent and non-violent protest against the state, the nature of terrorism and state-terrorism, how terrorist actors justify their use of violence as a form of political activity, how terrorist groups are organized and the tactics they employ in their warfare, and the nature of international terrorism and the counterterrorism responses by the threatened governments. The final chapter, entitled “Rethinking Terrorism,” presents the author’s conclusions and includes a discussion of recent terrorist attacks, including the nature of the Islamic State (IS), which “stands as the archetypical Islamic terrorist group” (p. 225).
David L. Altheide, Terror Post-911 and the Media (New York, NY: Peter Lang Publishing, Inc., 2009), US $ 111.95 [Hardcover], US $ 37.95 [Paperback], ISBN 978-1-4331-0366-7.
This is an interesting discussion of the logic, rhetoric, and discourse revolving around the issue of terrorism and how to counter it, especially since 9/11. A central theme is that public discourse on terrorism tends to be “more associated with victimization and fear, even surpassing linkages with crime” even when evidence may point to a diminished threat. The book’s chapters examine the relation between terrorism and propaganda, the politics of fear and moral panic, the problem of evidence in demonstrating the supposed severity of the threat. A separate chapter examines similarities and differences in the way the April 1999 school shootings at Columbine and terrorism are covered by American media.
Josef Schrofl, Sean Michael Cox, and Thomas Pankratz (Eds.) Winning the Asymmetric War: Political, Social and Military Responses (New York, NY: Peter Lang Publishing, Inc., 2009), 366 pp., US $ 83.95 [Paperback], ISBN: 978-3631572498.
The contributors to this volume examine the nature of asymmetric war and the comprehensive responses required to defeat asymmetric actors. The book is divided into four chapters: a theoretical analysis of asymmetric warfare, including in the form of a terrorist insurgency; cases of asymmetric conflicts in Africa, al Qaeda as an asymmetric group; and strategies to counter asymmetric threats.
Lori J. Underwood (Eds.) The Root of All Evil? Religious Perspectives on Terrorism (New York, NY: Peter Lang Publishing, Inc., 2013), 153 pp., US $ 72.95 [Hardcover], ISBN: 978-1-4331-1929-3.
The contributors to this volume examine the question of whether a causal relationship between organized religions and terrorism exists as a way to ascertain if “removing adherence to religion” might ameliorate the problem of terrorism. These issues are discussed in cases such as the Islamic context of global Jihadism, confronting Buddhist terrorism, the Japanese cult Aum Shinrikyo, and Hinduism and terrorism. In the concluding chapter, the volume’s editor writes that while “looking at the world unreflectively and being willing to objectify others for the sake of sanctifying one’s own personal causes” is one of the explanations of terrorism, “that process is psychologically independent from any psychological attachment to organized religion.” (p. 143) As a result, organized religion should not necessarily be blamed for what terrorists do, “bend and twist [such] religions into a weapon” in their warfare (p. 143).
Laurie R. Blank and Gregory P. Noone, International Law and Armed Conflict: Fundamental Princples and Contemporary Challenges in the Law of War (New York, NY: Wolters Kluwer Law & Business, 2013), 736 pp., US $ 106.00 [Paperback], ISBN: 978-1454817727.
This comprehensive textbook on international law and armed conflict (also known as Law of Armed Conflict - LOAC) is divided into five parts: basic principles of LOAC and the nature and classification of armed conflict; the designation of combatants, civilians and the nature of their battlefield status in armed conflict; identifying legitimate targets and protected objects, including designating weapons and tactics in attacks; and training military judge advocates and ensuring accountability for violations of LOAC. As a textbook, each chapter is accompanied by questions for discussion.
Geoffrey S. Corn, Victor Hansen, Richard B. Jackson, Chris Jens, Erik Talbot Jensen, and James A. Schoettler, Jr. (Eds.), The Law of Armed Conflict: An Operational Approach (New York, NY: Wolters Kluwer Law & Business, 2012), 648 pp., US $ 205.00 [Hardcover], ISBN: 978-1454806905.
This textbook on international humanitarian law is crucial, according to the editors, “to the planning, execution, and critique of military operations”(p. xxv). The volume’s chapters cover topics such as the legal basis and principles governing the use of force in armed conflict; how combatants, civilians and other belligerents are covered by the law of armed conflict (LOAC); the application of LOAC in targeting, weapons use, and tactics; the treatment of “wounded and sick” under LOAC; detention under LOAC; applying LOAC to military occupation, termination of hostilities and transition to other types of post-conflict situations; the application of LOAC to naval warfare, including neutrality; LOAC and war crimes; and military command responsibility and compliance mechanisms under LOAC. Each chapter includes a series of study questions for further discussion.
Stephen Dycus, William C. Banks, Peter Raven-Hansen, and Stephen L. Vladeck (Eds.), Counterterrorism Law [Second Edition] (New York, NY: Wolters Kluwer Law & Business, 2012), 912 pp., US $ 209.00 [Hardcover], ISBN: 9780735598638.
This textbook presents a comprehensive and detailed overview of counterterrorism law within the larger field of national security law. The book is divided into eight parts: an introduction, authority and its limits in the war on terrorism, detecting terrorist threats, detaining and interrogating terrorist suspects, criminalizing terrorists, prosecuting terrorists and their supporters, applying counterterrorism law in homeland security, and applying “noncriminal sanctions” against terrorists and their supporters by means of public sanctions and launching lawsuits against terrorists and their supporters. The textbook’s chapters are accompanied by excerpted sections from relevant criminal codes and criminal cases, including notes and questions for discussion.
About the Reviewer: Dr. Joshua Sinai is the Book Reviews Editor of ‘Perspectives on Terrorism’. He can be reached at: Joshua.sinai@comcast.net.
V. Notes from the Editor
A Word of Appreciation for Our External Peer Reviewers
from the Editorial Team
Perspectives on Terrorism is the product of volunteer efforts - academics, professionals and practitioners - who for nine consecutive years have been giving their time and providing their expertise to keep this free online journal alive and even increasing in circulation to more than 5,800 subscriptions. While the main burden of producing six issues per year rests on the shoulders of the Editorial Team and those of the Editorial Board members, there are many others who assist us in bringing out timely articles and research notes.
The seven Editorial Team members and the twenty Editorial Board members alone would not be able to handle and review the growing number of articles that reach us now on an almost daily basis. We could not deal with this volume of submissions without the selfless help of our esteemed external reviewers. Once a year we wish to thank them publicly by listing their names.
For reviewing article submitted to Perspectives on Terrorism in 2015, we wish to thank the individuals listed in the following table.
THANK YOU to our Peer Reviewers for Perspectives on Terrorism, 2015
| Wale Adeboye | Sajjan Gohel | Petter Nesser |
| Ehsan Ahrari | Muhammad Feyyaz | Brian Nussbaum |
| Omar Ashour | William Hansen | Allan Orr |
| Max Boon | Thomas Hegghammer | Anita Peresin |
| Frank Bovenkerk | Donald Holbrook | Nico Prucha |
| Michael Boyle | Jack Jarmon | Gilbert Ramsay |
| Tina Christensen | Paul Joosse | Don Rassler |
| David Cheney | Paul Kamolnick | Ineke Roex |
| Christina Cliff | Brynjar Lia | Jeanine de Roy van Zuijdewijn |
| Orville Shawn Cupp | Michael Loadenthal | Bart Schuurman |
| Joel Day | Miroslav Mares | Mubin Sheikh |
| Leah Farrall | Sarah Marsden | Haldun Yalcinkaya |
| Heather Gregg | Jonathan Matusitz | Ahmet S. Yayla |
| Aaron Hoffman | Assaf Moghadam |
We also wish to thank our regular members of the Editorial Board. They were approached most often and asked again and again to give us their professional assessment regarding the quality of the submissions reaching our journal.
Thank you all for making Perspectives on Terrorism a success!
Alex P. Schmid & James J.F. Forest (Editors)
Robert Wesley (Founding Editor)
Joseph J. Easson (Associate Editor for IT)
Joshua Sinai (Book Reviews Editor)
Jared Dmello (Editorial Assistant)
Eric Price (Editorial Assistant)
Judith Tinnes (Editorial Assistant)
TRI Award for Best PhD Thesis 2015: Call for Submissions
The Terrorism Research Initiative (TRI) seeks to enhance the quality of research in the field of Terrorism Studies. For this purpose it has established an Annual Award for the Best Doctoral Dissertation on Terrorism and Counter-Terrorism. The TRI Award jury identifies among the submissions three finalists and among them the winner. The Award for the best thesis submitted in 2013 went to Dr. Tricia Bacon (American University, Washington, D.C., USA) and the winner of the 2014 Award was Dr. Anneli Botha (Institute for Security Studies, Pretoria, South Africa).
With the present announcement, a call is being made for Ph.D. theses submitted or defended at an academic institution in the year 2015. Doctoral theses in the field of terrorism- and counter-terrorism studies can be submitted either by the author or by the academic supervisor, and should be submitted in electronic form to the chairman of the jury, Prof. em. Alex P. Schmid, at apschmid@terrorismanalysts.com, together with a cover letter (1-3 pp.), highlighting the merits of the submitted Ph.D. thesis. Submissions have to be in English (or translated into English)
The deadline for entries (in English, or with translation into English) is 31 March, 2016.
The TRI Award jury, consisting of the three directors of TRI (Robert Wesley, James Forest and Alex P. Schmid) will evaluate and compare the submissions in the months of April and May 2016 and inform the three finalists in the course of June 2016. The winner among them will be announced in the summer of 2016 and can expect an Award of US $1,000, plus a certificate of achievement signed by the President of the Terrorism Research Initiative, acknowledging the granting of the TRI thesis award. The other two finalists will receive a certificate of achievement. For all three finalist theses, TRI will assist the author in finding a publisher. The winner of the 2015 TRI Award will also be invited to submit an article for publication in Perspectives on Terrorism, summarizing the winning thesis’ main results.
TRI National/Regional TRI Networks (Partial) Inventory of Ph.D. Theses in the Making
by Alex P. Schmid (Network Coordinator)
The Terrorism Research Initiative (TRI) seeks to stimulate research in various ways, one being the annual competition for the best Ph.D. thesis in the field of terrorism and counter-terrorism. Another effort involves the organization of national or (sub-) regional networks of researchers engaged in writing a doctoral dissertation on (counter-) terrorism or a closely-related subject at a recognized academic institution. There are a dozen TRI Theses Writers Networks in existence, some functioning better than others. Below, the reader will find a list of two dozen doctoral theses in the making. In each case the (working) title of a thesis is given, followed by the name of the Ph.D. researcher and the one of the university where the thesis is being written. The expected date of completion is given at the end. In addition to the networks listed below, there are also (proto-) networks in existence in Australia, Canada, Greece, the Netherlands (incl. Flanders in Belgium), Nigeria, Pakistan, Russia and the United Kingdom.
Graduate students who wish to join a network should contact the network coordinator at <apschmid@ terrorismanalysts.com >.
Austrian-German-Swiss Network (Coordinator: Johannes Saal)
1. Les Femmes Musulmanes Occidentals dans le Jihad Contemporain: Une Armee de Roses entre Soutien Visible et Invisible d l’Utopie Jihadiste dans une Conception Feminine du Fard Al Ayn [Western Muslim Women in the Contemporary Jihad: An Army of Roses between Visible and Invisible Support for the Jihadist Utopia in a Feminine Conception of Fard Al Ayn]
Geraldine Casutt
University of Fribourg (CH) and EHESS-Paris
Expected date of completion: 2017.
2. Switzerland and the Origins of International Counterterrorism: Crisis Management, Multilateral Diplomacy, and Intelligence Cooperation (1969-1977)
Aviva Guttmann
University of Bern and Handa Centre for the Study of Terrorism and Political Violence (CSTPV), University St. Andrews
Expected date of completion: February 2016.
3. Policies of Tajikistan and Uzbekistan toward Afghanistan: Common Structures, Varying Outcomes
Azamjon Isabaev
Institute for Peace Research and Security Policy, University of Hamburg
Expected date of completion: September 2016.
4. The Dark Social Capital of Religious Terrorists: Analyzing Radicalization, Recruitment and Dynamics of Jihadist Networks in Europe
Johannes Saal
Graduate School of Humanities and Social Sciences (GSL),
University of Lucerne
Expected date of completion: Summer 2018.
5. Ermittlungen gegen Organisierte Kriminalitat: Ein Vergleich des deutschen und kolumbianischen Rechts [Investigations on Organized Crime: A Comparison between German and Colombian Law]
Angelica Romero Sanchez
University of Freiburg (D) and International Max Planck Research School for Comparative Criminal Law (IMPRS-CC)
Expected date of completion: December 2016.
6. The Military Organization of State Repression
Adam Scharpf
Graduate School of Economic and Social Sciences, University of Mannheim
Expected date of completion: Summer 2016.
7. The Illicit Business of Terrorism: Assessing the Resourcing of Terrorist Campaigns
Julia Sammelbeck
Graduate School of Economic and Social Sciences, University of Mannheim
Expected date of completion: Summer 2017.
8. Preemptive Self-Defense Aspect of the Laws of War: U.S. Drone Strikes Inside Pakistan
Imdad Ullah
Willy Brandt School of Public Policy, University of Erfurt.
Expected date of completion: not determined.
9. Filling the Gaps: Hamas and Hezbollah between Inclusion and Exclusion: A Multi-Dimensional Framework based on Sociological Systems Theory
Dennis Walkenhorst
Bielefeld Graduate School in History and Sociology, University of Bielefeld
Expected date of completion: Summer 2016.
South(ern) Africa Network (Coordinator: Petra Harvest)
10. The New Insurgencies and Mass Uprisings in Africa and International Involvement: Selected Case Studies.
Samuel Adotey Anum (Ghana).
University of Pretoria
Expected completion date is 2017.
11. Counter-terrorism and Civil Society in Nigeria
Emeka Thaddues Njoku
University of Ibadan, Nigeria
Expected completion date: 2016.
12. The Westphalian Model and Trans-Border Ethnic Identity: The Case of the Chewa Kingdom of Malawi, Mozambique and Zambia.
Happy Kayuni (Malawia)
University of the Western Cape
Expected completion: early 2016.
13. Nuclear Proliferation.
[Name cannot be released as author is government official]
University of Pretoria
Expected completion date: 2016.
Norwegian Network (Coordinator: Cato Hemmingby)
14. The Terrorist Target Selection Process: Influencing Factors with regard to Terrorists’ Choice of Targets.
Cato Hemmingby
Norwegian Police University College
Expected date of completion: 2016.
15. Helicopter Emergency Medical Services in Major Incidents: Patterns of Use and Influence on Outcome
Anne Siri Johnsen
University of Stavanger
Expected date of completion: 2019.
16. Far-Right Violence in Europe 1990-2012: Patterns and Processes.
Jacob Aasland Ravndal
Norwegian Defence Research Institute, Terrorism Research Group
Expected date of completion: 2016.
17. From the Extreme to the Mainstream: the Politics of Anti-Islamic Movements and their Rhetoric
Lars Erik Berntzen
Department of Political and Social Science, European University Institute Florence
Expected date of completion: Spring 2017.
United States Network (Coordinator: Matthew Sweeney)
18. Net-Nazis: Framing Hegemonic Ideologies of the White Power Movement through Racist Humor
Steven Windisch
University of Nebraska - Omaha
Expected date of completion: 2019.
19. Political Crimes and Responses to Them:Terrorism, Expectations of Interactions, and Trust
Erin Kearns
American University, Washington D.C.
Expected date of completion: 2017.
Brazilian Network (Coordinator: Prof. Jorge Lasmar)
20. The Pedagogy of Martyrdom in Shia Narratives
Patricia Prado
PUC Minas
Expected date of completion: December 2017.
21. Terrorism Risk Analysis: A Comparison of Different Risk Models
Suzane Vasconcelos
PUC Minas
Expected date of completion: December 2018.
22. Gender Issues and the Role of Women in Terrorism
Luisa Novaes Tolledo
PUC Minas
Expected date of completion: December 2016.
23. The Interplay Between Macro-, Meso- and Micro-Factors in the Decision of Becoming a Foreign Fighter: The Case of Syria
Guilherme Damasceno Fonseca
PUC Minas
Expected date of completion: 2015.
24. Cosmopolitan Uncivil Societies and the Problem of Terrorism
Adriana Neves Gomes de Azevedo
PUC Minas
Expected date of completion: August 2017.
Job Announcement: Open Rank Faculty Search at CTSS, UMass Lowell
The School of Criminology & Justice Studies at the University of Massachusetts Lowell seeks to fill one interdisciplinary position in Security Studies at the rank of Assistant/Associate/Full Professor for September, 2016. The candidate may be hired with tenure if he/she currently holds tenure at another institution. Applicants must hold a Ph.D. in Criminology, Criminal Justice, Political Science, International Relations, Psychology, or a field relevant to Security Studies.
Candidates must demonstrate a record of scholarship and publications in respected peer-reviewed journals, or evidence of future scholarly productivity, and expertise in advanced quantitative and/or qualitative research methods. Additionally, senior faculty hires (Associate or Full) are expected to come with a track record of procuring and serving as a lead investigator on externally funded research projects, and will be evaluated in part on this criterion. Assistant professor candidates would not have this requirement, but should have demonstrated capacity for such activity in the future.
Candidates with research specialization in mass atrocities, political violence, national security policy, cybersecurity or countering violent extremism are strongly encouraged to apply. Applicants must demonstrate the ability to teach courses and play a role in the university’s degree programs, including Security Studies, which offers concentrations in international security, homeland security, industrial & economic security, critical infrastructure protection, cybersecurity, and weapons of mass destruction. The successful applicant will also teach and mentor students in the Terrorism Studies Option track of the Ph.D. in Criminology & Criminal Justice. The successful applicant will be expected to play a major role in the Center for Terrorism & Security Studies at UMass Lowell, and may be eligible for joint faculty appointments in the Departments of Political Science, Psychology, or other academic unit within the University related to the candidate’s academic discipline.
School of Criminology and Justice Studies
The School enrolls over 1,200 students across its programs, and is the largest component of the College of Fine Arts, Humanities, and Social Sciences. The School has 16 tenured and tenure-track faculty with a blending of senior and junior colleagues. The faculty has expertise in a wide range of topics in criminology and criminal justice and extensive research and scholarly productivity. Faculty research is currently supported by several million dollars in external grants from the National Institute of Justice, the Department of Homeland Security, and other major funding agencies. We offer a Bachelor of Science, two Master’s degrees, graduate level certificates in six specialized areas, and a Ph.D. Our faculty lead several research centers and serve as editors of 3 top academic journals.
Center for Terrorism & Security Studies
The Center was established in 2013 in connection with the University’s growing academic enterprise in the field of terrorism and security studies. Concurrent with the Center’s growth in recent years, the College of Fine Arts, Humanities, and Social Sciences has established a terrorism studies option within the PhD program in Criminal Justice housed in the School of Criminology and Justice Studies, launched M.S. and M.A. degree programs in Security Studies, initiated a PhD program in Global Studies, and hired several new social science faculty with research programs in the areas of security, terrorism, and international conflict. Additionally, a significant number of faculty within both the University’s College of Engineering and its
College of Sciences are extensively engaged in funded research programs focused on matters of national and international security.
Salary commensurate with experience. Review of applications will begin February 1, 2016 and continue until the position is filled. The University is committed to increasing the gender and racial/ethnic diversity of its faculty to match that of our student body. Candidates who can contribute to that goal are strongly encouraged to apply, and should identify in their cover letter how their personal and professional experiences can help us achieve this goal.
Applications must be submitted online at: http://www.uml.edu/j obs
Please direct inquiries to the Chair of the Search Committee:
Professor James J.F. Forest
Director, Security Studies Program
University of Massachusetts Lowell
School of Criminology & Justice Studies
113 Wilder Street, Suite 400
Lowell, MA 01854-3060
Tel: 978-934-4337
Email: james forest@uml.edu
About Perspectives on Terrorism
Perspectives on Terrorism (PT) is a joint publication of the Terrorism Research Initiative (TRI), headquartered in Vienna, Austria, and the Center for Terrorism and Security Studies (CTSS), headquartered at the Lowell Campus of the University of Massachusetts, United States of America.
PT is published six times per year as a free peer-reviewed online journal available at www.terrorismanalysts. com. It seeks to provide a platform for established scholars as well as academics and professionals entering the interdisciplinary fields of Terrorism, Political Violence and Conflict Studies. The editors invite readers to:
-
present their perspectives on the prevention of, and response to, terrorism and related forms of violent conflict;
-
submit to the journal accounts of evidence-based, empirical scientific research and analyses;
-
use the journal as a forum for debate and commentary on issues related to the above.
Perspectives on Terrorism has sometimes been characterised as ‘nontraditional’ in that it dispenses with some of the traditional rigidities associated with commercial print journals. Topical articles can be published at short notice and reach, through the Internet, a much larger audience than subscription-fee based paper journals. Our free on-line journal also offers contributors a higher degree of flexibility in terms of content, style and length of articles - but without compromising professional scholarly standards.
The journal’s articles are peer-reviewed by members of the Editorial Board as well as outside experts. While aiming to be policy-relevant, PT does not support any partisan policies regarding (counter-) terrorism and conflict-waging. Impartiality, objectivity and accuracy are guiding principles that we require contributors to adhere to.
Editorial Team of Perspectives on Terrorism
Alex P. Schmid, Editor-in-Chief
James J.F. Forest, Co-Editor
Joseph J. Easson, Associate Editor
Joshua Sinai, Books Reviews Editor
Jared Dmello, Editorial Assistant
Eric Price, Editorial Assistant
Judith Tinnes, Editorial Assistant
[1] Picarelli, John T. “The Future of Terrorism.” NIJ Journal, no. 264 (n.d.). https://www.ncjrs.gov/pdffiles1/nij/228387.pdf.
[2] Sageman, Marc. Leaderless Jihad: Terror Networks in the Twenty-First Century. Philadelphia: University of Pennsylvania Press, 2008.
[3] Ryan, Michael W. S. Decoding Al-Qaeda’s Strategy: The Deep Battle against America. Columbia Studies in Terrorism and Irregular Warfare. New York: Columbia University Press, 2013, p. 227-229.
[4] Cozzens, Jeffery B. and Magnus Ranstorp, “The Enduring Al Qaeda Threat: A Network Perspective,” in Contemporary Debates on Terrorism, ed. Richard Jackson and Samuel Justin Sinclair, London: Routledge, 2012, 90-97; Thomas, Timothy L. “Al Qaeda and the Internet: The Danger of Cyberplanning” Parameters 23(1) 2003, p. 112-123; Cronin, Audrey Kurth. “Cyber Mobilization: The New Levee en Masse” Parameters 36(2), 2006 p. 77-87.
[5] Hoffman, Bruce. Inside Terrorism. Rev. and expanded ed. New York: Columbia University Press, 2006. 63-71
[6] Hoffman, Bruce, “Al Qaeda, Trends in Terrorism, and Future Potentialities: An Assessment,” Studies in Conflict & Terrorism, 26, (2003): 429-442; Mayntz, R., “Hierarchy or Network? On the Organizational Forms of Terrorism” Berliner Journal fur Soziologie 14 (2), 2004, p. 251; Raufer, Xavier, “Al Qaeda: A Different Diagnosis,” Studies in Conflict & Terrorism, 26 (2003): 391-398; Sageman, Marc, Understanding Terror Networks. Philadelphia: University of Pennsylvania Press (2004); Pedahzur, Ami and Perliger, Arie, “The Changing Nature of Suicide Attacks: A Social Network Perspective.” Social Forces 94 (4), 2006.
[7] Brams, J. Steven, Mutlu Hande, and S. Ling Ramirez, “Influence in Terrorist Networks: From Undirected to Directed Graphs,” Studies in Conflict & Terrorism 29, 2006, p. 703-718; Carley, M. Kathleen, Ju-Sung, Lee and Krackhardt, David, “Destabilizing Network,” Connections 24 (3), 2002, p. 79-92; Carley, M. Kathleen, Diesner Jana, Reminga Jeffrey and Tsvetovat Maksim, “Toward an Interoperable Dynamic Network Analysis Toolkit,” Decision Support System, 43, 2006, p. 1324-1347; Krebs, E. Valdis, “Mapping Networks of Terrorist Cells,” Connections 24 (3), 2002, p. 43-52; Koschade, Stuart, “A Social Network Analysis of Jemaah Islamiyah: The Applications to Counterterrorism and Intelligence,” Studies in Conflict & Terrorism 29 (6), 2006, p. 559-75; Perliger, Arie and Pedahzur, Ami, “Social Network Analysis in the Study of Terrorism and Political Violence,” Political Science and Politics, 44(1), 2011, p. 45-50.
[8] Carley et al. 2002; Pedahzur and Perliger, 2006
[9] Laszlo-Barabasi, Albert, and Eric Bonabeau, “Scale-Free Networks.” Scientific American 288(5), 2003, p.60-69.; Pedahzur, Ami and Perliger, Arie, Jewish Terrorism in Israel, New York: Columbia University Press (2009); Cozzens, Jeffrey B.. “Approaching Al-Qaeda’s Warfare: Function, Culture and Grand Strategy,” in Mapping Terrorism Research: State of the Art, Gaps and Future Directions, ed. Magnus Ranstorp, London: Routledge, 2007, p.127-64, 132; Atwan, Abdel Bari . The Secret History of Al-Qa’ida, London: Saqi Books, 2006, p.265-66.
[10] Jenkins, Brian Michael. “Statement on Terrorism: Current and Long-Term Threats”, Senate Armed Services Committee on Emerging Threats, November 15, 2001. RAND Testimony Series.
[11] Berger, J.M. “ISIS/The Islamic State.” Lecture at the Fletcher School of Law and Diplomacy, Medford, MA, February 17, 2015.
[12] Gunaratna, Rohan, “Al Qaeda’s Trajectory During and After Bin Laden,” in Howard and Hoffman (eds.) Terrorism and Counterterrorism, p. 206-237.
[13] Vennesson, Pascal. “Globalization and al Qaeda’s Challenge to American Unipolarity,” in Recalling September 11th: Is Everything Different Now? ed. James Burk, New York: Cambridge University Press, 2013, p. 232-261, 242.
[14] Hoffman, Bruce and Fernando Reinares, “Conclusion,” in The Evolution of the Global Terrorist Threat, p. 618-639
[15] Ibid.
[16] Sageman, Marc. Leaderless Jihad: Terror Networks in the Twenty-First Century. Philadelphia: University of Pennsylvania Press, 2008; Bruce Hoffman, “The Myth of Grass-Roots Terrorism,” Foreign Affairs 87(3), 2008, p.133-138; Sciolino, Elaine and Eric Schmitt, “A Not Very Private Feud over Terrorism,” New York Times, June 8, 2008.
[17] Gunaratna, Rohan. Inside Al Qaeda. Columbia University Press, 2002, p. 95-101.
[18] Berger, J.M. “ISIS/The Islamic State,” 2015; Bruce Hoffman, “The Myth of Grass-Roots Terrorism,” 2008, p. 133-138.
[19] Porter, Patrick. The Global Village Myth: Distance, War and the Limits of Power. Washington, DC: Georgetown University Press, 2015, p. 136.
[20] Laszlo-Barabasi, Albert, and Eric Bonabeau, “Scale-Free Networks.” Scientific American 288(5), 2003, p.60-69; Pedahzur, Ami and Perliger, Arie, Jewish Terrorism in Israel, New York: Columbia University Press (2009); Brams et al, “Influence in Terrorist Networks,” 2006; Carley et al, 2002, 2006; Helfstein, Scott and Wright, Dominic. “Covert or Convenient? Evolution of Terror Attack Networks,” Journal of Conflict Resolution, October 2011, pp. 785-813; Krebs, “Mapping Networks of Terrorist Cells,” 2002, p. 43-52; Koschade, “A Social Network Analysis of Jemaah Islamiyah,” 2006, p. 559-575; Perliger, Arie. “Terrorist Networks’ Productivity and Durability: A Comparative Multi-Level Analysis.” Perspectives on Terrorism 8(4), 2014. http://www.terrorismanalysts.com/pt/index.php/pot/ article/view/359/712; Perliger and Pedahzur, 2006, 2009, 2011.
[21] Arguments can certainly be made for the role of ISIS in fracturing the movement, but this piece will focus on the period before IS broke from Al Qaeda.
[22] Crenshaw, Martha. “Global Al-Qaeda.” Mapping Militant Organizations. Stanford University, n.d. Web. 12 Nov. 2014.
[23] National Consortium for the Study of Terrorism and Responses to Terrorism (START). (2014). Global Terrorism Database [GTD 1970-2013]. Retrieved from http://www.start.umd.edu/gtd
[24] Sources used for coding the groups can be found in the Bibliography section of this paper.
[25] This designation was reserved for groups that were concerned with the overthrow of a specific government (e.g. the TTP in Pakistan), rather than groups that were interested in the overthrow of apostate governments writ large.
[26] Al Qaeda Core’s organizational objectives, along with most other attribute data within the dataset, were taken from the Mapping Militants Project. In the interest of maintaining as much consistency in the dataset as possible, it was only on the occasions that sufficient data were not available in the MMP, typically because the group was not included within it, that outside sources were consulted.
[27] Hoffman, Bruce and Fernando Reinares, “Conclusion,” p. 618-639
[28] Tunnard, Christopher, “Consulting Firm-Analyzing” Lecture at the Fletcher School of Law and Diplomacy, Medford, MA, 30 September 2014.
[29] Ibid.
[30] Vidino, Lorenzo, “The Evolution of the Post-9/11 Threat to the U.S. Homeland,” in The Evolution of the Global Terrorist Threat, p. 3-28.
[31] Arquilla, John, David F. Ronfeldt, and United States, eds. Networks and Netwars: The Future of Terror, Crime, and Militancy. Santa Monica, CA: Rand, 2001.
[32] Berger, J.M. “ISIS/The Islamic State.” 2015.
[33] Again, one who is familiar with the case may note the positive high tie between AQC and Hamas as strange, given the public disputes that occurred between the two during this period. However, the public disputes did not appear within the MMP dataset, and yet the GTD did list a joint operation between the two in 2007. As joint operations are coded as a high positive weight, the relationship between the two is shown as a high positive tie.
[34] Leadership i.e. the top place in centrality measures.
[35] Cooperation with those with whom it shares organizational objectives
[36] A reader who is familiar with the case may note the lack of ties between Al Qaeda Core and many other groups with which it had relations through this time period, such as TTP, the Haqqani Network, and AQIM. However, there were no specific incidents linking Al Qaeda Core to any of these groups in either dataset from 2011 to 2013. As mentioned previously, this project was limited to the MMP and GTD data for reasons of feasibility.
[37] Hoffman and Reinares, “Conclusion,” p. 618-639.
[38] Once again, a follower of TTP and LeT may find it odd that the two groups have a positive high link, given their history of shared hostilities. However, as with the positive high tie between AQC and Hamas in the 2006-2010 interval, the MMP dataset did not include data points for the hostilities within this time period, although there were some previously. Rather, the GTD listed a joint operation in 2012, which gave it the positive high weight.
[39] Crenshaw, Martha. “Global Al-Qaeda.” 2014.
[40] Helen Pidd, “Neo-Nazi Terror Scandal Grows in Germany,” The Guardian, November 16 2011; Spiegel, “The Brown Army Faction: A Disturbing New Dimension of Far-Right Terror,” SpiegelOnline, http://www.spiegel.de/international/germany/the-brown-army-faction-a-disturbing-new-dimension-of-far-right- terror-a-797569-4.html; Quentin Peel, “The Faces of Neo-Nazism,” http://www.ft.com/cms/s/2/dfda3010-3438-11e2-9ae7-00144feabdc0.html#axzz2K6JSUB7i.
[41] Tom Sundermann, „Wer Doner Aft, Wurde Ausgepeitscht,“ Die Zeit, June 18 2013.
[42] Andreas Witzel and Herwig Reiter, The Problem-Centered Interview, vol. 1, 2000 (New York: Sage, 2012).vol. 1, 2000 (New York: Sage, 2012
[43] Tore Bj0rgo and John Horgan, Leaving Terrorism Behind: Individual and Collective Disengagement (London/New York: Routledge, 2009); Ineke van der Valk and Willem Wagenaar, “The Extreme Right: Entry and Exit,” in Racism & Extremism Monitor (Leiden: Anne Frank House/Leiden University, 2010); Mary Beth Altier, Christian N Thoroughgood, and John G Horgan, “Turning Away from Terrorism: Lessons from Psychology, Sociology, and Criminology,” Journal of Peace Research 51, no. 5 (2014).
[44] Tore Bj0rgo and Horgan, Leaving Terrorism Behind: Individual and Collective Disengagement; Darcy M.E. Noricks, “Disengagement and Deradicalization: Processes and Programs,” in Social Science for Counterterrorism. Putting the Pieces Together., ed. Paul K. Davis and Kim Cragin (Santa Monica: Rand Corporation, 2009); Chowdhury Naureen Fink and Ellie B. Haerne, “Beyond Terrorism: Deradicalization and Disengagement from Violent Extremism,” (International Peace Insitute, 2008); Renee Garfinkel, “Personal Transformations. Moving from Violence to Peace.,” in Special Report (United States Institute of Peace, 2007); van der Valk and Wagenaar, “The Extreme Right: Entry and Exit.”; Emma Disley et al., “Individual Disengagement from Al Qa’ida-Influenced Terrorist Groups: A Rapid Evidence Assessment to Inform Policy and Practice in Preventing Terrorism,” (Cambridge: RAND Europe, 2011).
[45] Tore Bj0rgo, Racist and Right-Wing Violence in Scandinavia: Patterns, Perpetrators, and Responses. (Oslo: Aschehoug, 1997); Bj0rgo and Horgan, Leaving Terrorism Behind: Individual and Collective Disengagement.
[46] Idem.
[47] John Horgan, Walking Away from Terrorism: Accounts of Disengagement from Radical and Extremist Movements (London/New York: Routledge, 2009), 47.2009
[48] James A. Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism,” Current Research on Peace and Violence 11, no. 4 (1988): 165.no. 4 (1988
[49] John Horgan, Walking Away from Terrorism: Accounts of Disengagement from Radical and Extremist Movements, 37.
[50] Idem., p. 93.
[51] Idem., p. 114.
[52] Tore Bj0rgo, Racist and Right-Wing Violence in Scandinavia: Patterns, Perpetrators, and Responses., 224.
[53] Tore Bj0rgo and Horgan, Leaving Terrorism Behind: Individual and Collective Disengagement.
[54] James A. Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism.”Current Research on Peace and Violence 11, no. 4 (1988), p. 165.
[55] Idem., p.163.
[56] Boaz Ganor and Ophir Falk, “De-Radicalization in Israel’s Prison System,” Studies in Conflict & Terrorism 36, no. 2 (2013): 125-26.
[57] Rodger A. Bates, “Terrorism within the Community Context,” The Journal of Public and Professional Sociology 3, no. 1 (2010).no. 1 (2010
[58] Idem., pp. 4-5.
[59] Idem, p. 11.
[60] Idem., p.12.
[61] For examples onE.g., ‘altruistic punishment’, see Robert Boyd et al., “The Evolution of Altruistic Punishment,” Proceedings of the National Academy of Sciences 100, no. 6 (2003); Arie W. Kruglanski and Donna M. Webster, “Group Members’ Reactions to Opinion Deviates and Conformists at Varying Degrees of Proximity to Decision Deadline and of Environmental Noise,” Journal of Personality and Social Psychology 61, no. 2 (1991); Donald Thomas Campbell, “Ethnocentric and Other Altruistic Motives,” in Nebraska Symposium on Motivation, ed. David Levine (Lincoln: University of Nebraska Press, 1965).
[62] Fabio Sani and John Todman, “Should We Stay or Should We Go? A Social Psychological Model of Schisms in Groups,” Personality and Social Psychology Bulletin 28, no. 12 (2002); E.g., group factionalism, fissions, shisms, see Fabio Sani, “When Subgroups Secede: Extending and Refining the Social Psychological Model of Schism in Groups,” ibid.31, no. 8 (2005); E. Burke Rochford, Jr., “Factionalism, Group Defection, and Schism in the Hare Krishna Movement,” Journal for the Scientific Study of Religion 28, no. 2 (1989); Claire M. Hart and Mark Van Vugt, “From Fault Line to Group Fission: Understanding Membership Changes in Small Groups,” Personality and Social Psychology Bulletin 32, no. 3 (2006).
[63] John M. Levine and Richard L. Moreland, “Group Reactions to Loyalty and Disloyalty.,” in Group Cohesion, Trust and Solidarity. Advances in Group Processes, ed. Shane R. Thye (Elsevier Science/JAI Press, 2002).
[64] Idem., p.211.
[65] Idem., p. 207.
[66] Idem., p. 219.
[67] Idem., p. 212-215.
[68] Barry M Staw, “The Consequences of Turnover,” Journal of occupational Behaviour (1980): 257.
[69] Herbert Riehl-Heyse, „Bilder Einer Schaurigen Traumwelt. Beobachtungen in Einem Prozess Gegen Junge Neonazis.,“ in Rechtsextremismus in Der Bundesrepublik. Vorrausstetzungen, Zusammenhange, Wirkungen., ed. Wolfgang Benz (Frankfurt am Main: 1984).
[70] Kluftmann, „Explosives Klima,“ http://www.spiegel.de/spiegel/print/d-8848666.html.
[71] Spiegel, „Verrater Verfallen Der Feme,“ ibid., May 13 1996.
[72] James A. Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism,” 163, 65.
[73] John M. Levine and Moreland, “Group Reactions to Loyalty and Disloyalty.,” 211.
[74] Tore Bj0rgo, Racist and Right-Wing Violence in Scandinavia: Patterns, Perpetrators, and Responses; Bj0rgo and Horgan, Leaving Terrorism Behind: Individual and Collective Disengagement.
[75] Ingo Hasselbach and Tom Reiss, Fuhrer-Ex: Memoirs of a Former Neo-Nazi, 1st ed. (New York: Random House, 1996).
[76] R. Mauer, „Violence Plagued Ex-Aryan Ally,“ Idaho Statesman, September 17 1980; Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism,” 160.
[77] See, for instance.g., Kate Barrelle, “Pro-Integration: Disengagement from and Life after Extremism,” Behavioral Sciences of Terrorism and Political Aggression 7, no. 2 (2015); Anja Dalgaard-Nielsen, “Promoting Exit from Violent Extremism: Themes and Approaches,” Studies in Conflict & Terrorism 36, no. 2 (2013); F. Demant et al., “Decline and Disengagement-an Analysis of Processes of Deradicalisation,” in IMES Report Series (Amsterdam: Institute for Migration and Ethnic Studies (IMES), 2008); van der Valk and Wagenaar, “The Extreme Right: Entry and Exit.”
[78] James A. Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism,” 160; Mauer, “Violence Plagued Ex-Aryan Ally.”, Idaho Statesman, September 17, 1980.
[79] Herbert Riehl-Heyse, “Bilder Einer Schaurigen Traumwelt. Beobachtungen in Einem Prozess Gegen Junge Neonazis..”
[80] Kluftmann, „Explosives Klima“.
[81] UPI, “Ex-Kkk and Neo-Nazi Leader Found Nailed to Board,” Los Angeles Times, August 11 1987.
[82] James A. Aho, “Out of Hate: A Sociology of Defection from Neo-Nazism,” 160.
[83] Idem, p. 163 & p. 165.
[84] Hasselbach and Reiss, Fuhrer-Ex : Memoirs of a Former Neo-Nazi.
[85] Spiegel, “Sachsen: Mogliche Nsu-Verbindung Zu Ungeklartem Doppelmord,” Der Spiegel, June 6 2014.
[86] „Verrater Verfallen Der Feme.“, Der Spiegel, May 13, 1996
[87] Rhein-Zeitung, “Neonazi-Prozess: Funf Rechte Schlager Mussen Ins Gefangnis” Rhein-Zeitung, October 30 2011.
[88] Gegenrede to gegenrede. Informationsportal gegen Rechtsextremismus fur Demokratie., 2011, http://www.gegenrede.info/news/2011/lesen. php?datei=110328_01.
[89] Theo Schneider to Stoerungsmelder, December 28, 2014, http://blog.zeit.de/stoerungsmelder/2014/07/16/blutiger-szenestreit-in-berlin_16704.
[90] Ted Robert Gurr and Will H. Moore, “Ethnopolitical Rebellion: A Cross-Sectional Analysis of the 1980s with Risk Assessments for the 1990s.” American Journal of Political Science, (1997), pp. 1079-1103; Patrick Regan and Daniel Norton, “Greed, Grievance, and Mobilization in Civil Wars,” Journal of Conflict Resolution, no. 49 (2005): pp. 319-36.
[91] Joe Eyerman. “Terrorism and Democratic States: Soft Targets or Accessible Systems,” International Interactions, no. 24 (1998), pp. 151-70.
[92] Martha Crewshaw, “The Causes of Terrorism,” Comparative Politics, no. 13 (1981), pp. 379-99.
[93] Ted Robert Gurr, Why Men Rebel (Princeton: Princeton University Press, 1970).
[94] Walter Enders and Todd Sandler, The Political Economy of Terrorism, New York: Cambridge University Press, 2006.
[95] Max Abrahms, “Why Democracies Make Superior Counterterrorists,” Security Studies, no. 16 (2007), pp. 223-53; James I. Walsh, and James A. Piazza, “Why Respecting Physical Integrity Rights Reduces Terrorism,” Comparative Political Studies, no. 43 (2010), pp. 551-77.
[96] Erica Chenoweth, “Democratic Competition and Terrorist Activity,” Journal of Politics, (2008), pp. 16-30.
[97] Alex P. Schmid, “Terrorism and Democracy,” Terrorism and Political Violence, no. 4 (1992), pp. 14-25; William Lee Eubank and Leonard Weinberg, “Does Democracy Encourage Terrorism?” Terrorism and Political Violence, no. 6 (1994), pp. 417-43; William Lee Eubank, and Leonard Weinberg. “Terrorism and Democracy: Perpetrators and Victims.” Terrorism and Political Violence, no. 13 (2001), pp. 155-64.; Quan Li. “Does Democracy Promote or Reduce Transnational Terrorist Incidents?” Journal of Conflict Resolution, no. 49 (2005), pp. 278-97; Ana Bela Santos Bravo and Carlos Manuel Mendes Dias, “An Empirical Analysis Of Terrorism: Deprivation, Islamism And Geopolitical Factors.” Defence and Peace Economics, 2006, pp. 329-41.
[98] Brigitte L. Nacos, Mass-mediated Terrorism: The Central Role of the Media in Terrorism and Counterterrorism (London: Rowman & Littlefield, 2002).
[99] Ibid.
[100] Sara Jackson Wade and Dan Reiter, “Does Democracy Matter?: Regime Type and Suicide Terrorism,” Journal of Conflict Resolution, no. 51 (2007), pp. 329-48.
[101] Erica Chenoweth, Why Democracy Encourages Terrorism (New York: Columbia University Press, forthcoming).
[102] Edward N. Muller and Erich Weede, “Cross-National Variation in Political Violence: A Rational Action Approach,” Journal of Conflict Resolution, vol.34, no.4 (1990), pp. 624-651; Eyerman. “Terrorism and Democratic States”; Eubank and Weinberg, “Terrorism and Democracy: Perpetrators and Victims”; Alberto Abadie, Poverty, Political Freedom, and the Roots of Terrorism (Cambridge, Mass.: National Bureau of Economic Research, 2004); Konstantinos Drakos and Andreas Gofas, “In Search Of The Average Transnational Terrorist Attack Venue,” Defence and Peace Economics, no. 17 (2006), pp. 73-93; Peter Kurrild-Klitgaard, Mogens K. Justesen, and Robert Klemmensen, “The Political Economy Of Freedom, Democracy And Transnational Terrorism,” Public Choice, no. 128 (2006), pp.289-315; James A. Piazza, “Regime Age and Terrorism: Are New Democracies Prone to Terrorism?” International Interactions, 2013, pp. 246-63.
[103] James A. Piazza, “Terrorism and Party Systems in the States of India,” Security Studies, no. 19 (2010), pp. 99-123.
[104] Alex P. Schmid, “Prevention of Terrorism: Towards a Multi-pronged Approach,” in Tore Bjorjo (Ed.), Root Causes of Terrorism (Oslo: Norwegian Institute of International Affairs, 2003), pp. 209-231.
[105] Quan Li,, op. cit. “Does Democracy Promote or Reduce Transnational Terrorist Incidents?”
[106] Deniz Aksoy and David Carter, “Electoral Institutions and the Emergence of Terrorist Groups,” British Journal of Political Science, no. 44, (2012), pp. 181-204.
[107] Tore Bjorjo, “Conclusions,” in Tore Bjorjo (ed.), Root Causes of Terrorism (Oslo: Norwegian Institute of International Affairs, (2003), p. 258.
[108] Bruce Hoffman, “Holy Terror”: The Implications Of Terrorism Motivated By A Religious Imperative,” Studies in Conflict & Terrorism, no. 18 (1995), pp. 271-84; Mark Juergensmeyer, Terror in the Mind of God: The Global Rise of Religious Violence (Berkeley: University of California Press, 2003); Magnus Ranstorp, Terrorism in the Name of Religion, Journal of International Affairs, no.50 (1996), pp. 41-62; Jessica Stern, Terror in the Name of God: Why Religious Militants Kill. New York: Harper Perennial.
[109] Ibid.
[110] Seth G. Jones and Martin C. Libicki, How Terrorist Groups End Lessons for Countering Al Qa’ida (Santa Monica, CA: Rand, 2008); Victor Asal and R. Karl Rethemeyer, “The Nature Of The Beast: Organizational Structures And The Lethality Of Terrorist Attacks,” Journal of Politics, vol. 70, no. 2 (2008), pp. 437-49; Bruce Hoffman, “The Confluence of International and Domestic Trends in Terrorism,” Terrorism and Political Violence vol. 9, no. 2 (1997), pp. 1-15; Jessica Stern, The Ultimate Terrorists (Cambridge: Harvard University Press, 2000); Walter Enders and Todd Sanders, “Is Transnational Terrorism Becoming More Threatening?: A Time Series Investigation,” Journal of Conflict Resolution vol. 44, no. 3 (2000), pp. 307-332.
[111] Assaf Moghadam, The Globalization of Martyrdom: Al Qaeda, Salafi Jihad, and the Diffusion of Suicide Attacks (Baltimore: Johns Hopkins University Press, 2008). Peter S. Henne, “The Ancient Fire: Religion and Suicide Terrorism,” Terrorism and Political Violence, no. 24 (2012), pp. 38-60.
[112] Freedom House assesses a country’s level of freedom along two different dimensions-political rights and civil liberties-on a scale of 1 (most free) to 7 (least free). Countries whose averaged scores fall between 1-3 are considered “free”; those scoring 3-5 are considered “partly free;” those scoring above 5 are considered “not free.”
[113] A list of organizations used in the analysis is available from the author.
[114] Each attack was coded as either “religious,” “non-religious,” or “unknown.” An attack was coded as “religious” if the following conditions were met: (a) it was carried out by a group or individual that conceives of itself as a predominantly religious actor; (b) that group frames its mission in religious terms, although it may have other goals as well; and (c) the attacker, although perhaps involved in a communitarian conflict that politicizes religious symbols, holds a discernible religious ideology or motivation that serves to animate its strategies and goals apart from or in addition to the mere utilization of religious objects or rhetoric.-See Bruce Hoffman, Inside Terrorism (New York: Columbia University Press), pp. 81-131.
[115] Ronald F. Inglehart, The Silent Revolution: Changing Values and Political Styles among Western Publics (Princeton, N.J.: Princeton University Press, 1977); Ronald F. Inglehart, Culture Shift in Advanced Industrial Society (Princeton, N.J.: Princeton University Press, 1990); Ronald F. Inglehart, Modernization and Postmodernization: Cultural, Economic, and Political Change in 43 Societies (Princeton, N.J.: Princeton University Press, 1997); Pippa Norris and Ronald F. Inglehart, Sacred and Secular: Religion and Politics Worldwide (Cambridge, UK: Cambridge University Press, 2004); Ronald F. Inglehart, and Christian Welzel, Modernization, Cultural Change, and Democracy: The Human Development Sequence (Cambridge, UK: Cambridge University Press, 2005).
[116] Ronald Inglehart, “Changing Values Among Western Publics From 1970 To 2006,” West European Politics, Vol. 31, No. 1-2 (2008), pp. 130-146.
[117] Nilay Saiya, “Explaining Religious Violence Across Countries: An Institutional Perspective,” in Kevin R. den Dulk and Elizabeth Oldmixon (eds.), Mediating Religion and Government: Political Institutions and the Policy Process (New York: Palgrave, 2014), pp. 209-240; Nilay Saiya and Anthony Scime, “Explaining Religious Terrorism: A Data-Mined Analysis,” Conflict Management and Peace Science, Vol. 35, No. 5 (2015), pp. 487-512; Nilay Saiya, “The Religious Freedom Peace,” International Journal of Human Rights, Vol. 19, No. 3 (2015), pp. 369-382.
[118] Brian J. Grim and Roger Finke, The Price of Freedom Denied: Religious Persecution and Conflict in the 21st Century (New York: Cambridge University Press, 2011).
[119] Risa Brooks, “Muslim ‘Homegrown’ Terrorism in the United States: How Serious is the Threat?,” International Security, Vol. 36, No. 2 (2012), pp. 7-47.
[120] Mark Juergensmeyer, The New Cold War? Religious Nationalism Confronts the Secular State (London: University of California Press, 1993); Walter Laqueur, The New Terrorism: Fanaticism and the Arms of Mass Destruction, (New York: Oxford University Press, 1999); David C. Rapoport, “The Four Waves of Modern Terrorism,” in Audrey Cronin and J. Ludes, eds., Attacking Terrorism: Elements of a Grand Strategy (Washington, DC: Georgetown University Press, 2004), pp. 46-73.
[121] Monica Duffy Toft, and Timothy Shah, “Why God is Winning”, Foreign Policy, (2006), pp. 39-43; Monica Duffy Toft, Daniel Philpott, and Timothy Shah, God’s Century: Resurgent Religion and Global Politics (New York: W.W. Norton, 2011); Gilles Kepel, The Revenge of God: The Resurgence of Islam, Christianity, and Judaism in the Modern World (University Park, Pa: Pennsylvania State University Press, 1994).
[122] Brian J. Grim and Roger Finke, The Price of Freedom Denied; ,Timothy Samuel Shah, Religious Freedom: Why Now?: Defending an Embattled Human Right (Princeton, NJ: The Witherspoon Institute, 2012); Alan Hertzke, (Ed.), The Future of Religious Freedom (New York: Oxford University Press, 2013); Pew Research Center, ‘Religious Hostilities Reach Six-Year High, Pew Forum on Religion in Public Life, http://www.pewforum.org/2014/01/14/religious-hostilities-reach-six-year- high/(accessed 1 June 2014).
[123] Edwin Bakker and Beatrice de Graaf, (2011), “Preventing Lone Wolf Terrorism: Some CT Approaches Addressed,” Perspectives on Terrorism, 5(5-6), pp.4350; Clark McCauley, Sophia Moskalenko & Benjamin Van Son, (2013), “Characteristics of Lone-Wolf Violent Offenders: A Comparison of Assassins and School Attackers,” Perspectives on Terrorism, 7(1), pp.4-24; Claire Wardle, (2003), “The ‘Unabomber’ vs. the ‘Nail Bomber’: A Cross-Cultural Comparison of Newspaper Coverage of Two Murder Trials,” Journalism Studies, 4(2), pp.239-251.
[124] Some researchers and law enforcement officials use the term “Unibomber” when referring to Kaczynski. However, “Unabomber,” the more commonly used term, more accurately accounts for the fact that Kaczynski sent bombs to persons affiliated with universities (“Un”) and airlines (“a”).
[125] Alston Chase, (2003), “Harvard and the Unabomber: The Education of an American Terrorist,” New York: W.W. Norton & Company.
[126] Theodore Kaczynski, “Industrial Society and Its Future” The Washington Post, September 19, 1995, available at http://www.washingtonpost.com/wp-srv/ national/longterm/unabomber/manifesto.text.htm, accessed December 10, 2015.
[127] Ron Arnold, (1997), “Ecoterror: The Violent Agenda to Save Nature, the World of the Unabomber,” Bellevue, WA: Free Enterprise Press.
[128] Ibid.
[129] Chase p.21 (See note 3); Robert Graysmith, (1997), “Unabomber: A Desire to Kill,” Washington, D.C.: Regnery Publishing.
[130] Ibid.
[131] Chase p.22 (See note 3).
[132] Paul Joosse, (2007), “Leaderless Resistance and Ideological Inclusion: The Case of the Earth Liberation Front.” Terrorism and Political Violence, 19(3), pp.351368.
[133] Kaczynski (See note 4). Kaczynski’s manifesto is divided into 28 sections. While environmentalism is not referenced in any of the section titles, Kaczynski discussed environmental issues at several points within the manifesto. Within the body (i.e. excluding footnotes) of the manifesto, individual paragraphs are designated by numbers listed in ascending order from 1 to 232. When information from the manifesto is quoted, the paragraph or paragraphs from which the quoted material was taken is cited in the endnotes.
[134] Herbert W. Simons, (1970), “Requirements, Problems, and Strategies: A Theory of Persuasion for Social Movements,” Quarterly Journal of Speech, 56 (1), pp.1-11.
[135] Kaczynski, paragraph 184 (See note 4).
[136] Kaczynski, paragraph 41 (See note 4).
[137] Kaczynski wrote his manifesto on an old-fashioned typewriter that did not allow him to italicize or boldface words.
[138] Kaczynski, paragraph 1 (See note 4).
[139] Kaczynski, paragraph 69 (See note 4).
[140] Kaczynski, paragraph 169 (See note 4). Kaczynski also discussed how he believed increasingly liberal (“leftist’) attitudes regarding the personal acquisition of consumer goods, coupled with higher population densities, were wreaking havoc on the environment. In essence, Kaczynski believed consumer demand for products had grown beyond environmental sustainability levels.
[141] Kaczynski’s use of “we,” “us,” and “our” could have also been intended to convince authorities he represented an actual multi-person group.
[142] Bron Taylor, (1998), “Religion, Violence and Radical Environmentalism: From Earth First! to the Unabomber Manifesto to the Earth Liberation Front,” Terrorism and Political Violence, 10(4), pp:1-42. Kaczynski inscribed “FC” on some of his bombs.
[143] Kaczynski, paragraph 4 (See note 4).
[144] Kaczynski, paragraph 3 (See note 4).
[145] Kaczynski, paragraph 4 (See note 4).
[146] Kaczynski, paragraph 4 (See note 4).
[147] Kaczynski, paragraph 2 (See note 4).
[148] Simons, p.4 (See note 10).
[149] Kaczynski, paragraph 166 (See note 4).
[150] Kaczynski, paragraph 183 (See note 4).
[151] Kaczynski, paragraph 188 (See note 4).
[152] Kaczynski, paragraphs 186-187 (See note 4).
[153] Kaczynski, paragraph 189 (See note 4).
[154] If that were not enough, Kaczynski’s manifesto is available in book form through several libraries.
[155] Simons, p.4 (See note 10).
[156] Simons, p.4 (See note 10).
[157] Kaczynski, paragraph 135 (See note 4).
[158] Kaczynski, paragraph 4 (See note 4).
[159] Kaczynski, paragraph 96 (See note 4).
[160] Kaczynski, paragraph 96 (See note 4).
[161] Simons, pp.4-7 (See note 10).
[162] Kaczynski, paragraph 200 (See note 4).
[163] Kaczynski, paragraph 202 (See note 4).
[164] Kaczynski, paragraphs 190-191 (See note 4).
[165] Simons, p.7 (See note 10).
[166] Simons, p.7 (See note 10).
[167] Simons, p.8 (See note 10).
[168] Simons, p.11 (See note 10).
[169] Chase p.77 (See note 3).
[170] Ibid.
[171] Ibid.
[172] Taylor p.2 (See note 20).
[173] Taylor p.7 (See note 20).
[174] Taylor p.7-8, 35 (See note 20).
[175] Taylor p.35 (See note 20).
[176] Michael Loadenthal, (2014), “Eco-Terrorism? Countering Dominant Narratives of Securitisation: A Critical, Quantitative History of the Earth Liberation Front (1996-2009),” Perspectives on Terrorism, 8(3), pp:16-50.
[177] Robin Simcox and Emily Dyer, “The Role of Converts in Al-Qa'ida-Related Terrorism Offenses in the United States” CTC Sentinel, 6 (3) (2013) https://www.ctc. usma.edu/posts/the-role-of-converts-in-al-qaida-related-terrorism-offenses-in-the-united-states. Accessed April 2, 2013.
[178] These data were collected and analyzed by the author over a period of approximately seven years (see Sam Mullins, ‘Home-Grown’ Jihad: Understanding Islamist Terrorism in the US and UK (London: Imperial College Press, forthcoming).
[179] After also dividing each sample into converts versus non-converts, this resulted in 8 different sub-samples: For the U.S., the pre-9/11 sample consisted of 143 individuals (25 converts, 118 non-converts) while the post-9/11 sample included 222 individuals (51 converts -1 of whom was a repeat offender from before 9/11- and 172 non-converts). By comparison, the U.K. pre-9/11 sample included 139 individuals (13 converts, 126 non-converts) and the post-9/11 sample included 288 (34 converts -including 1 repeat offender during the post-9/11 period- and 254 non-converts).
[180] Note that all percentages reported for the present study refer to the number of known individuals as a function of the respective sub-sample total.
[181] Note that the number of U.S. converts before and after 9/11 adds to 76, although the true number of individuals is 75. This is because one person (Daniel Boyd) committed separate offences in both time-periods. All other repeat offenders, both American and British, are excluded from the totals in order to show the actual number of people involved.
[182] This is consistent with research conducted by Kleinmann, who found that 19 of 32 American converts showed evidence of individual-level mechanisms of radicalization (including mental health problems), compared to just 5 of 51 non-converts (Scott Matthew Kleinmann, “Radicalization of Homegrown Sunni Militants in the United States: Comparing Converts and Non-Converts” Studies in Conflict and Terrorism, 35(4) (2012) 278-297.
[183] Regarding involvement in terrorism plots, Simcox and Dyer do not report provide clear, comparative figures.
[184] Including plots involving undercover operatives and excluding attacks that were actually completed.
[185] Defined here as lone, untrained individuals acting independently of any organization or group (also excluding terrorism offenders who were caught in sting operations where they plotted together with undercover operatives).
[186] “Leader of Revolution Muslim Pleads Guilty to Using Internet to Solicit Murder and Encourage Violent Extremism” US Department of Justice, February 9, 2012, http://www.justice.gov/usao/vae/news/2012/02/20120209mortonnr.html. Accessed February 10, 2012.
[187] Sara Carter, “Somalis in U.S. Draw FBI Attention” The Washington Times, December 29, 2008 http://www.washingtontimes.com/news/2008/dec/29/somalis-in- us-draw-fbi-attention/print/. Accessed June 13, 2010.
[188] Laura Yuen, “Sixth Minn. Man Reportedly Dies in Somalia” Minnesota Public Radio, September 11, 2009, http://minnesota.publicradio.org/display/ web/2009/09/11/somali-death/. Accessed June 27, 2011.
[189] “Jury Convicts Naser Jason Abdo on All Counts in Connection with Killeen Bomb Plot” US Department of Justice, May 24, 2012, http://www.justice.gov/usao/ txw/press releases/2012/Abdo conviction.pdf Accessed May 25, 2012.
[190] Sam Stanton and Denny Walsh, “Lodi-area Man Charged with Trying to Join Islamic State May Be Mentally Ill” The Sacramento Bee, December 2, 2014, http:// www.sacbee.com/news/local/crime/article4248423.html. Accessed December 2, 2014.
[191] Michael Schwirtz and William Rashbaum, “Attacker With Hatchet Is Said to Have Grown Radical on His Own” The New York Times, October 24, 2014, http:// www.nytimes.com/2014/10/25/nyregion/man-who-attacked-police-with-hatchet-ranted-about-us-officials-say.html?partner=rss&emc=rss&smid=tw-nytimes& r=0. Accessed October 26, 2014.
[192] “Mom: Son Arrested at O’Hare, Accused of Trying to Join Islamic State has Mental Illness” Chicago Tribune, April 8, 2015, http://www.chicagotribune.com/ news/nationworld/chi-wisconsin-islamic-state-20150411-story.html. Accessed April 9, 2015.
[193] Bob Dunn, “Alexander Ciccolo: Adams Man’s Path Divided Between Peace and Violence” The Berkshire Eagle, July 16, 2015, http://www.berkshireeagle.com/ local/ci 28496106/alexander-ciccolo-adams-mans-path-divided-between-peace. Accessed July 26, 2015.
[194] This is not to suggest that these are the only motives for converting to Islam and becoming involved in Islamist terrorism, or that converts’ expectations are always met. For more on these issues see: Jahangir E. Arasli, “Violent Converts to Islam: Growing Cluster and Rising Trend” Combating Terrorism Exchange, 1(1) (2011) https://globalecco.org/en GB/ctx-v1n1/violent-converts-to-islam. Accessed November 29, 2015; Monika Gabriela Bartoszewicz, Controversies of Conversions: The Potential Terrorist Threat of European Converts to Islam (University of St. Andrews: Unpublished doctoral thesis, 2013) https://research-repository. st-andrews.ac.uk/bitstream/10023/3676/3/MonikaGabrielaBartoszewiczPhDThesis.pdf. Accessed November 29, 2015; M.A. Kevin Brice, A Minority Within a Minority: A Report on Converts to Islam in the United Kingdom (Faith Matters: 2010) http://www.portmir.org.uk/assets/islam-and-muslims/a-minority-within- a-minority—a-report-on-converts-to-islam-in-the-uk—faith-matters.pdf. Accessed November 29, 2015; Matthew Kleinmann, “Radicalization of Homegrown Sunni Militants in the United States”; Leon Moosavi, “Are Converts More Likely to be Extremists than Other Muslims?” The Guardian, May 24, 2013, http://www. theguardian.com/commentisfree/belief/2013/may/24/islam-converts-woolwich-attackers-extremists. Accessed November 29, 2015; Milena Uhlmann, “European Converts to Terrorism” Middle East Quarterly, 15(3) (2008) http://www.meforum.org/1927/european-converts-to-terrorism. Accessed November 29, 2015.
[195] Sam Mullins, ‘Home-Grown’ Jihad.
[196] Ibid.
[197] Simcox and Dyer, “The Role of Converts in Al-Qa'ida-Related Terrorism Offenses in the United States”.
[198] Ibid.
[199] For a more detailed discussion relating to estimates of the number of converts to Islam in the U.K. see Brice, A Minority Within a Minority.
[200] Lorenzo Vidino and Seamus Hughes, ISIS in America: From Retweets to Raqqa (George Washington University: Program on Extremism, 2015) 7, https://cchs. gwu.edu/sites/cchs.gwu.edu/files/downloads/ISIS%20in%20America%20-%20Full%20Report.pdf. Accessed December 2, 2015.
[201] Martha Crenshaw, “The Causes of Terrorism” Comparative Politics 13, no. 4 (July 1981): 379-99; Andrew H. Kydd and Barbara F. Walter, “The Strategies of Terrorism” International Security 31, no. 1 (Summer 2006): 49-80; Robert Pape, Dying to Win: The Strategic Logic of Suicide Terrorism, Reprint edition (New York: Random House Trade Paperbacks, 2006).
[202] Max Abrahms, “What Terrorists Really Want,” International Security 32, no. 4 (Spring 2008): 78-105; Mark Juergensmeyer, Terror in the Mind of God: The Global Rise of Religious Violence, 3rd Edition, Third Edition, Completely Revised edition (Berkeley: University of California Press, 2003).
[203] For instance, in their 2014 study, Horowitz and Potter demonstrate that lethality and sophistication of domestic terror attacks increases after financial and tactical connections are forged with a larger transnational terror partner. Michael C. Horowitz and Philip B. K. Potter, “Allying to Kill Terrorist Intergroup Cooperation and the Consequences for Lethality,” Journal of Conflict Resolution 58, no. 2 (March 1, 2014): 199-225, doi:10.1177/0022002712468726.
[204] Ted Hopf, “The Logic of Habit in International Relations,” European Journal of International Relations 16 (2010): 539.
[205] For a comprehensive analysis of the “Practice Turn” literature, see Christian Bueger and Frank Gadinger, “The Play of International Practice,” International Studies Quarterly 59: no.3 (2015): 449-460.
[206] Thomas Hegghammer. “Why Terrorists Weep: The Socio-Cultural Practices of Jihadi Militants.” Paul Wilkinson Memorial Lecture, University of St. Andrews, 16 April 2015. There are important differences, however. Hegghammer’s work on “jihad culture” is concerned with “what terrorists do in their off time” while practice theory provides a focus on how meaning is created within jihadi culture, which integrates isolated activities like dressing together with violent practices like beheading. My argument is that practice offers observable, material points of identity formation, thus entirely related to preferences and passion creation that demonstrate in tactical choice and communication tactics. On the other hand, “culture” as conceived by Hegghammer seems to exist as a separate activity that jihadis engage in when not fighting. I argue that practice constructs actors in special ways that they take with them into fighting.
[207] Iver B. Neumann, “The Body of the Diplomat” European Journal of International Relations 14, no. 4 (December 1, 2008): 671-95, doi:10.1177/1354066108097557.
[208] Erik Voeten, “The Practice of Political Manipulation” in International Practices, ed. Emanuel Adler and Vincent Pouliot (Cambridge, Cambridge University Press, 2011).
[209] Emanuel Adler and Vincent Pouliot, International Practices (Cambridge, Cambridge University Press, 2011).
[210] Patrick Morgan, “The Practice of Deterrence,” in International Practices, ed. Emanuel Adler and Vincent Pouliot (Cambridge: Cambridge University Press, 2011).
[211] Severine Autesserre, Peaceland: Conflict Resolution and the Everyday Politics of International Intervention (Cambridge University Press, 2014).2014
[212] Iver B. Neumann, “Returning Practice to the Linguistic Turn: The Case of Diplomacy,” Millennium: Journal of International Studies 31, no. 3 (2002): 627-51.
[213] Mia Bloom, Dying to Kill: The Allure of Suicide Terror (New York: Columbia University Press, 2007).
[214] Monica Duffy Toft, Daniel Philpott, and Timothy Samuel Shah, God’s Century: Resurgent Religion and Global Politics (New York: W. W. Norton & Company, 2011); Isak Svensson, “Fighting with Faith Religion and Conflict Resolution in Civil Wars,” Journal of Conflict Resolution 51, no. 6 (December 2007).
[215] Adam B. Seligman et al., Ritual and Its Consequences: An Essay on the Limits of Sincerity (New York: Oxford University Press, 2008).
[216] Heather S. Gregg, “Defining and Distinguishing Secular and Religious Terrorism,” Perspectives on Terrorism 8, no. 2 (April 24, 2014), http://www. terrorismanalysts.com/pt/index.php/pot/article/view/336.
[217] Andreas Reckwick, “Toward a Theory of Social Practices: A Development in Culturalist Theorizing,” European Journal of Social Theory 5 (2002): 252.
[218] Alasdair MacIntyre, After Virtue (University of Notre Dame Press, 1981)..
[219] Adler and Pouliot, International Practices..
[220] The word used is phronesis. Otfried Hoffe, Aristotle’ “Nicomachean Ethics” (Brill, 2010).
[221] Pierre Bourdieu elaborates a compelling theory of practice which mirrors Aristotelian phronesis. Using the term habitus, Bourdieu refers to a set of habit-based dispositions (as opposed to thought-based propositions), where objective structures realize in prescribed actions of subjective agents.
[222] Vincent Pouliot, International Security in Practice: The Politics of NATO-Russia Diplomacy (Cambridge University Press, 2010), 38.
[223] Theodore R. Schatzki, The Site of the Social: A Philosophical Account of the Constitution of Social Life and Change (University Park, Pa: Pennsylvania State University Press, 2002), 177.
[224] Iain R. Edgar, “The Dreams of Islamic State,” Perspectives on Terrorism 9, no. 4 (July 31, 2015), http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/453.
[225] Pouliot, Vincent, “The Logic of Practicality,” International Organizations 54, no. 1 (2008): 257-88.
[226] Harvey Whitehouse and Jonathan Lanman, “The Ties That Bind Us: Ritual, Fusion, and Identification,” Current Anthropology 55, no. 6 (December 2014): 674-95.
[227] Vincent Pouliot, “Practice Tracing,” in Process Tracing: From Metaphor to Analytic Tool, ed. Andrew Bennet and Jeffrey Checkel (Cambridge, MA: Cambridge University Press, 2014).
[228] Ibid.
[229] Ibid., 252. According to Pouliot “practices are perfect units of analysis to travel up and down the ladder of abstraction.”
[230] Codebook, examples, and replication data are available at www.joelday.org
[231] Seligman et al., Ritual and Its Consequences. Religion is, as sociologist Riesebrodt argues, “a complex of religious practices.” Martin Riesebrodt, The Promise of Salvation: A Theory of Religion (Chicago: University of Chicago Press, 2010).
[232] “Extreme Rituals Forge Intense Social Bonds - Dimitris Xygalatas - Aeon” Aeon Magazine, January 21, 2015, http://aeon.co/magazine/society/how-extreme- rituals-bond-us-for-life/.
[233] Victor H. Asal and R. Karl Rethemeyer, “The Nature of the Beast: Terrorist Organizational Characteristics and Organizational Lethality,” Journal of Politics 70, no. 2 (2008): 437-49.
[234] Creating an index is helpful because the practices themselves are highly interdependent. The index is additive and unweighted for the sake of transparency and simplicity - no extant literature suggests a reason why one practice operates as more “rooting” than others, nor is there a natural hierarchy among practices.
[235] Ethnographic work may be less available for say, Jihadi poetry or beauty practices of NeoNazis. In those cases, it would not be possible to create larger datasets - it would be necessary to start with local ethnographic data collection, practice tracing, and participant observation.
[236] Thomas Riggs, ed., Worldmark Encyclopedia of Religious Practices, 3 vols. (Detroit: Gale, 2006).
[237] Ron Hassner, “‘Religion and International Affairs: The State of the Art,’” in Religion, Identity and Global Governance: Ideas, Evidence and Practice, ed. Steven Lamy and Patrick James (Toronto: University of Toronto Press, 2011), 37-56.
[238] Caner K. Dagli, “The Phony Islam of ISIS,” The Atlantic, February 27, 2015, http://www.theatlantic.com/international/archive/2015/02/what-muslims-really- want-isis-atlantic/386156/.
[239] Monica Duffy Toft, “Issue Indivisibility and Time Horizons as Rationalist Explanations for War,” Security Studies 15, no. 1 (2006): 34-69, doi:10.1080/09636410600666246.
[240] Again, the exclusivity measurement is helpful here since Unitarians may practice afterlife rituals, but have no limitations on the type of actions that gain access to that afterlife.
[241] Exclusivity is perhaps another way of talking about “otherization” but specified in material, physical manifestations. For the connection between “othering” and terrorist outcomes see Victor Asal and R. Karl Rethemeyer, “The Nature of the Beast: Organizational Structures and the Lethality of Terrorist Attacks,” Journal of Politics 70, no. 2 (2008): 437-449.
[242] See: Tim Mak, & Youssef, N. (March 3, 2015). IS ranks grow as fast as U.S. bombs can wipe them out. The Daily Beast. URL: http://www.thedailybeast.com/ articles/2015/02/03/isis-recruits-thousands-of-new-fighters-despite-u-s-bombs.html; Kirk, A. (August 12, 2015). Iraq and Syria: How many foreign fighters are fighting for Isil. The Telegraph. URL: http://www.telegraph.co.uk/news/worldnews/islamic-state/11770816/Iraq-and-Syria-How-many-foreign-fighters-are-fighting- for-Isil.html; Neumann, P. (January 26, 2015). Foreign fighter total in Syria/Iraq now exceeds 20,000; surpasses Afghanistan conflict in the 1980s. ISCR. URL: http:// icsr.info/2015/01/foreign-fighter-total-syriairaq-now-exceeds-20000-surpasses-afghanistan-conflict-1980s/ ; Schmid, Alex P.. Foreign (Terrorist) Fighter Estimates: Conceptual and Data Issues. The Hague: ICCT, 2015, p. 11.
[243] Ahmet Atasoy, Resat Gecen, & Huseyin Kormaz. (August 2015). Siyasi Coğrafya Açısından Türkiye (Hatay) - Suriye Siniri Turkey (Hatay) -Syrian border in terms of political geography. URL: http://www.mku.edu.tr/files/1_dosya_1355572531.pdf
[244] Cockburn, P. (November 16, 2014). War with IS: Islamic militants have army of 200,000, claims senior Kurdish leader. Independent. URL: http://www. independent.co.uk/news/world/middle-east/war-with-isis-islamic-militants-have-army-of-200000-claims-kurdish-leader-9863418.html
[245] See: Tim Mak, & Youssef, N. (March 3, 2015). IS ranks grow as fast as U.S. bombs can wipe them out. The Daily Beast. URL: http://www.thedailybeast.com/ articles/2015/02/03/isis-recruits-thousands-of-new-fighters-despite-u-s-bombs.html; Kirk, A. (August 12, 2015). Iraq and Syria: How many foreign fighters are fighting for Isil? The Telegraph. URL: http://www.telegraph.co.uk/news/worldnews/islamic-state/11770816/Iraq-and-Syria-How-many-foreign-fighters-are-fighting- for-Isil.html; Neumann, P. (January 26, 2015). Foreign fighter total in Syria/Iraq now exceeds 20,000; surpasses Afghanistan conflict in the 1980s. ISCR. URL: http:// icsr.info/2015/01/foreign-fighter-total-syriairaq-now-exceeds-20000-surpasses-afghanistan-conflict-1980s/
[246] Levitt, M. (November 18, 2015). How do IS terrorists finance their attacks. The Hill. URL:http://thehill.com/blogs/pundits-blog/homeland-security/260597-how- do-isis-terrorists-finance-their-attacks
[247] Jones, S. (October 30, 2015). IS beheads two Syrian activists who documented terror group’s crimes. The World Post. URL:http://www.huffingtonpost.com/entry/ syrian-activists-documenting-isis-crimes-beheaded-in-turkish-border-town_563383dae4b0c66bae5c148d
[248] For a report on the number of Syrian refugees see: Gurcanli, Z. (May 25, 2015). i§te 3 yil sonunda Turkiye’deki Suriyeliler’in durumu. Hurriyet. URL: http:// www.hurriyet.com.tr/iste-3-yil-sonunda-turkiyedeki-suriyelilerin-durumu- 29098215and Erdogan, M. M. (December 2014). Syrians in Turkey: Social acceptance and integration research. URL: http://www.hugo.hacettepe.edu.tr/TurkiyedekiSuriyeliler-Syrians%20in%20Turkey-Rapor-TR-EN-19022015.pdf
[249] Reuter, C. (April 18, 2015). The terror strategist: Secret files reveal the structure of Islamic State. Der Spiegel.URL: http://www.spiegel.de/international/world/ islamic-state-files-show-structure-of-islamist-terror-group-a-1029274.html
[250] Jam'iat Ihyaa’ Minhaaj al-Sunnah. (1993). A Brief Introduction to the Salafi Da'wah. Ipswich, UK.
[251] Dabiq. (September 2014). The revival of slavery before the hour. (4). URL:http://media.clarionproject.org/files/islamic-state/islamic-state-isis-magazine-Issue- 4-the-failed-crusade.pdf
[252] Lopez, G. (November 21, 2015). Captagon, IS’s favorite amphetamine, explained. Vox. URL: http://www.vox.com/world/2015/11/20/9769264/captagon-isis- drug
[253] Abdulrahim, R. (September 13, 2015). Syrians find it harder to flee country as Turkey tightens border control. The Wall Street Journal. URL: http://www.wsj. com/articles/syrians-find-it-harder-to-flee-country-as-turkey-tightens-border-control-1442176477 .
[254] Abdulrahim, R. (September 13, 2015). Syrians find it harder to flee country as Turkey tightens border control. The Wall Street Journal. URL: http://www.wsj. com/articles/syrians-find-it-harder-to-flee-country-as-turkey-tightens-border-control-1442176477
[255] Gurcanli, Z. (May 25, 2015). i§te 3 yil sonunda Turkiye’deki Suriyeliler’in durumu. Hurriyet. URL: http://www.hurriyet.com.tr/iste-3-yil-sonunda-turkiyedeki- suriyelilerin-durumu-29098215and Erdogan, M. M. (December 2014). Syrians in Turkey: Social acceptance and integration research. URL: http://www.hugo. hacettepe.edu.tr/TurkiyedekiSuriyeliler-Syrians%20in%20Turkey-Rapor-TR-EN-19022015.pdf
[256] Memurlar.net. (May 18, 2015). Kurtulmuş: Türkiye’de 27 multeci kampi var. URL: http://www.memurlar.net/haber/515446/
[257] Gurcanli, Z. (May 25, 2015). i§te 3 yil sonunda Turkiye’deki Suriyeliler’in durumu. Hurriyet. URL: http://www.hurriyet.com.tr/iste-3-yil-sonunda-turkiyedeki- suriyelilerin-durumu-29098215and Erdogan, M. M. (December 2014). Syrians in Turkey: Social acceptance and integration research. URL: http://www.hugo. hacettepe.edu.tr/TurkiyedekiSuriyeliler-Syrians%20in%20Turkey-Rapor-TR-EN-19022015.pdf
[258] (November 11, 2015). The true horrors of life under the Islamic State.URL:http://blogs.reuters.com/great-debate/2015/11/11/who-picks-up-your-trash-when- you-live-in-the-islamic-state/
[259] Layth, U. (2014). Diary of muhajirah. URL: http://fa-tubalilghuraba.tumblr.com/post/108838886229/diary-of-a-muhajirah-4
[260] Moaveni, A. (November 21, 2015). IS Women and Enforcers in Syria recount collaboration, anguish and escape. New York Times. URL: http://www.nytimes. com/2015/11/22/world/middleeast/isis-wives-and-enforcers-in-syria-recount-collaboration-anguish-and-escape.html?_r=0
[261] Dabiq. (September 2014). The revival of slavery before the hour. (4). URL: http://media.clarionproject.org/files/islamic-state/islamic-state-isis-magazine-Issue- 4-the-failed-crusade.pdf
[262] Horgan, J. (2008). Deradicalization or disengagement? Perspectives on Terrorism, 2(4). URL: http://www.terrorismanalysts.com/pt/index.php/pot/article/ view/32/html and Silke, A. (January 1, 2011). Disengagement or deradicalization: A look at prison programs for jailed terrorists. Combating Terrorism Center. URL: https://www.ctc.usma.edu/posts/disengagement-or-deradicalization-a-look-at-prison-programs-for-jailed-terrorists
[263] Scott Atran, & Axelrod, R. (July 2008). In theory: Reframing sacred values. Negotiation Journal. URL: http://www-personal.umich.edu/~axe/negj0708.pdf and Shiekh, H., Atran, S., Ginges, J., Wilson, L., Obeid, N., & Davis, R. (2014). The devoted actor as parochial altruist: sectarian morality, identity fusion, and support for costly sacrifices. Cliodynamics, 5(1).
[264] Neumann, P. (2015). Victims, perpetrators, assets: the narratives of Islamic State defectors. ICSR Report. URL: http://icsr.info/wp-content/uploads/2015/09/ ICSR-Report-Victims-Perpertrators-Assets-The-Narratives-of-Islamic-State-Defectors.pdf.